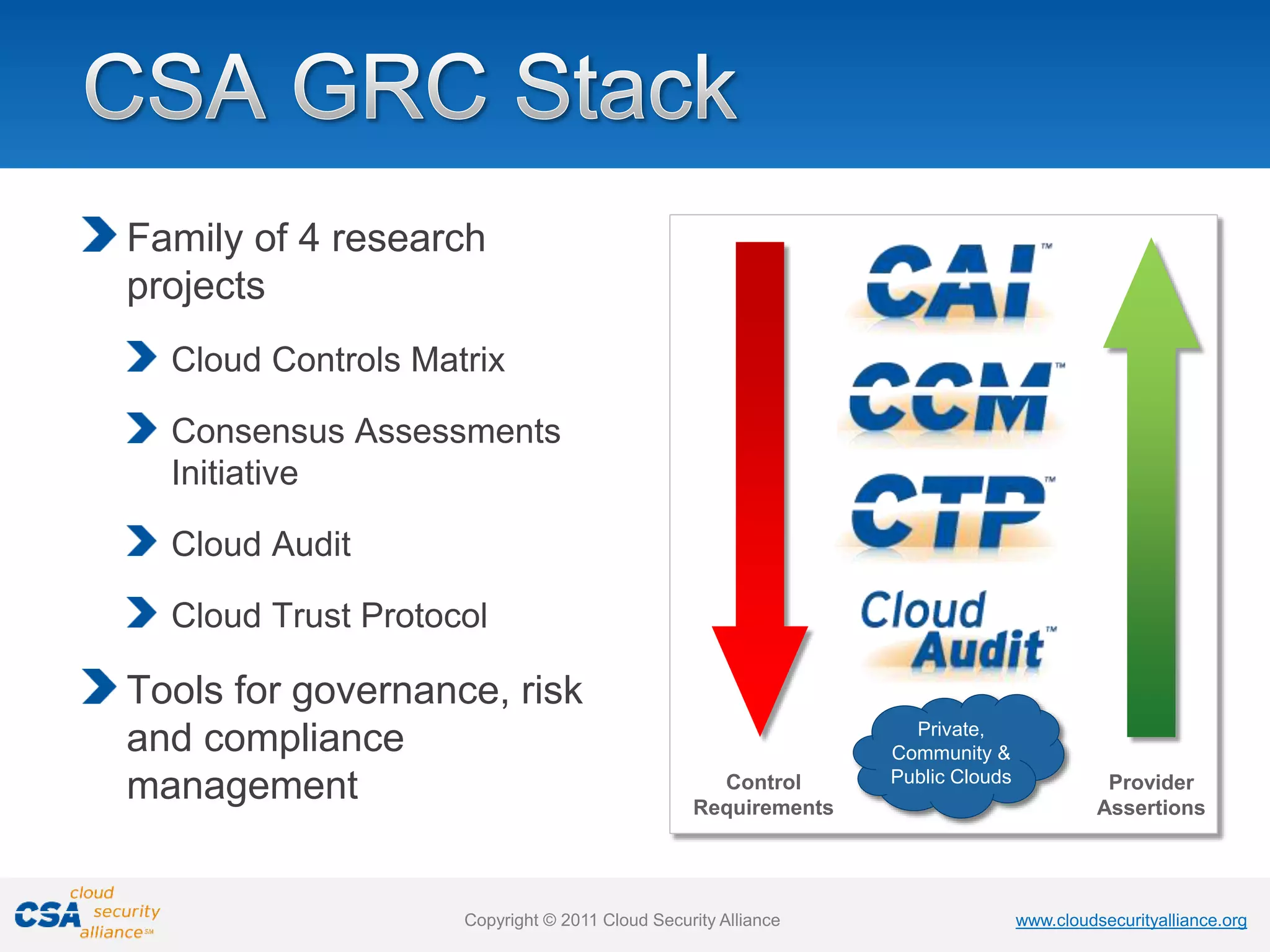
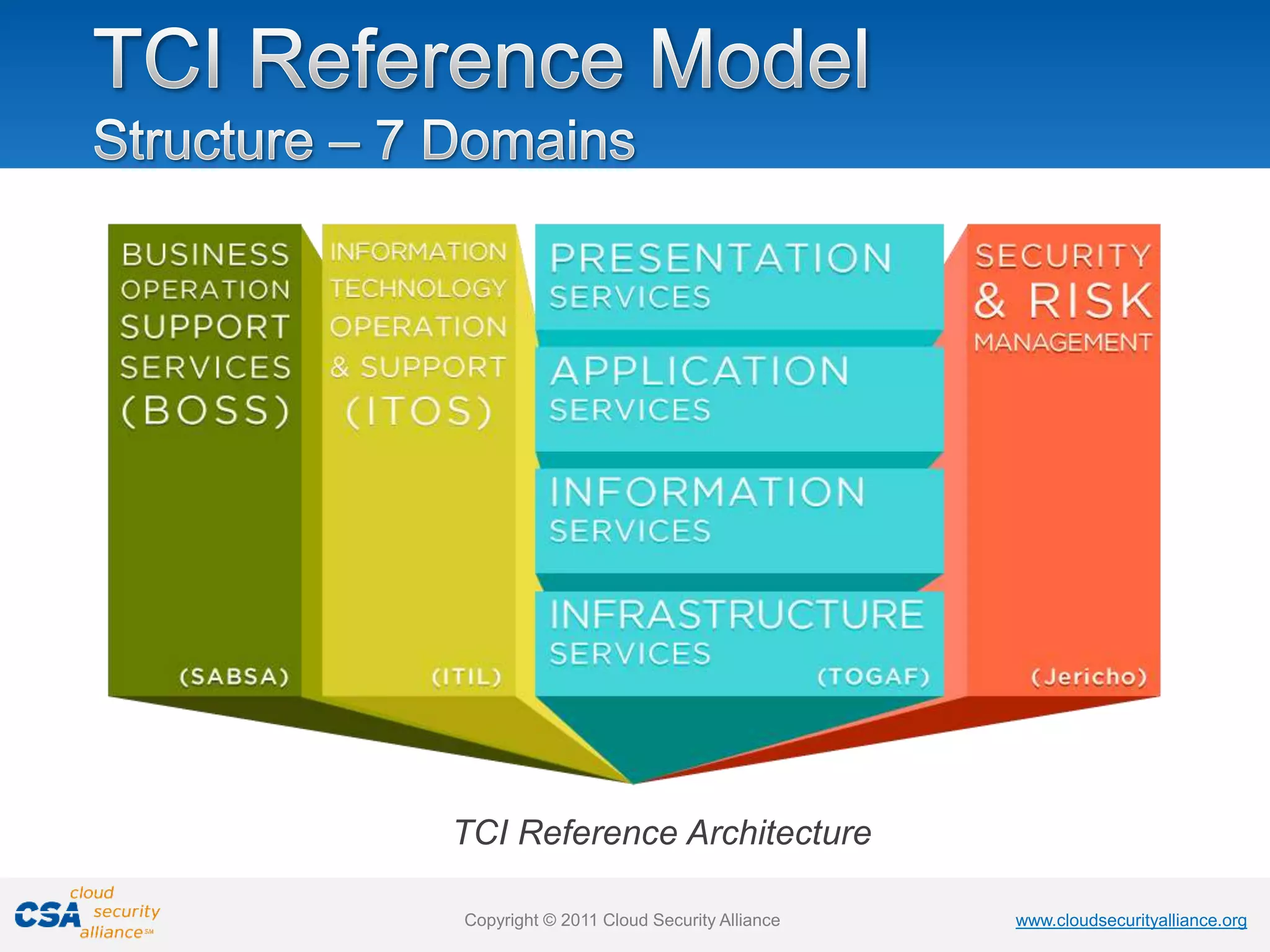
The document summarizes the research and work of the Cloud Security Alliance (CSA), a global non-profit organization focused on best practices for cloud security. It outlines that CSA has developed comprehensive best practices and tools for cloud security including the Cloud Controls Matrix, Consensus Assessments Initiative, Cloud Audit, and Cloud Trust Protocol. CSA also maintains the CSA STAR registry of cloud provider security assessments and conducts ongoing research to address emerging issues in cloud security, identity management, and other areas.