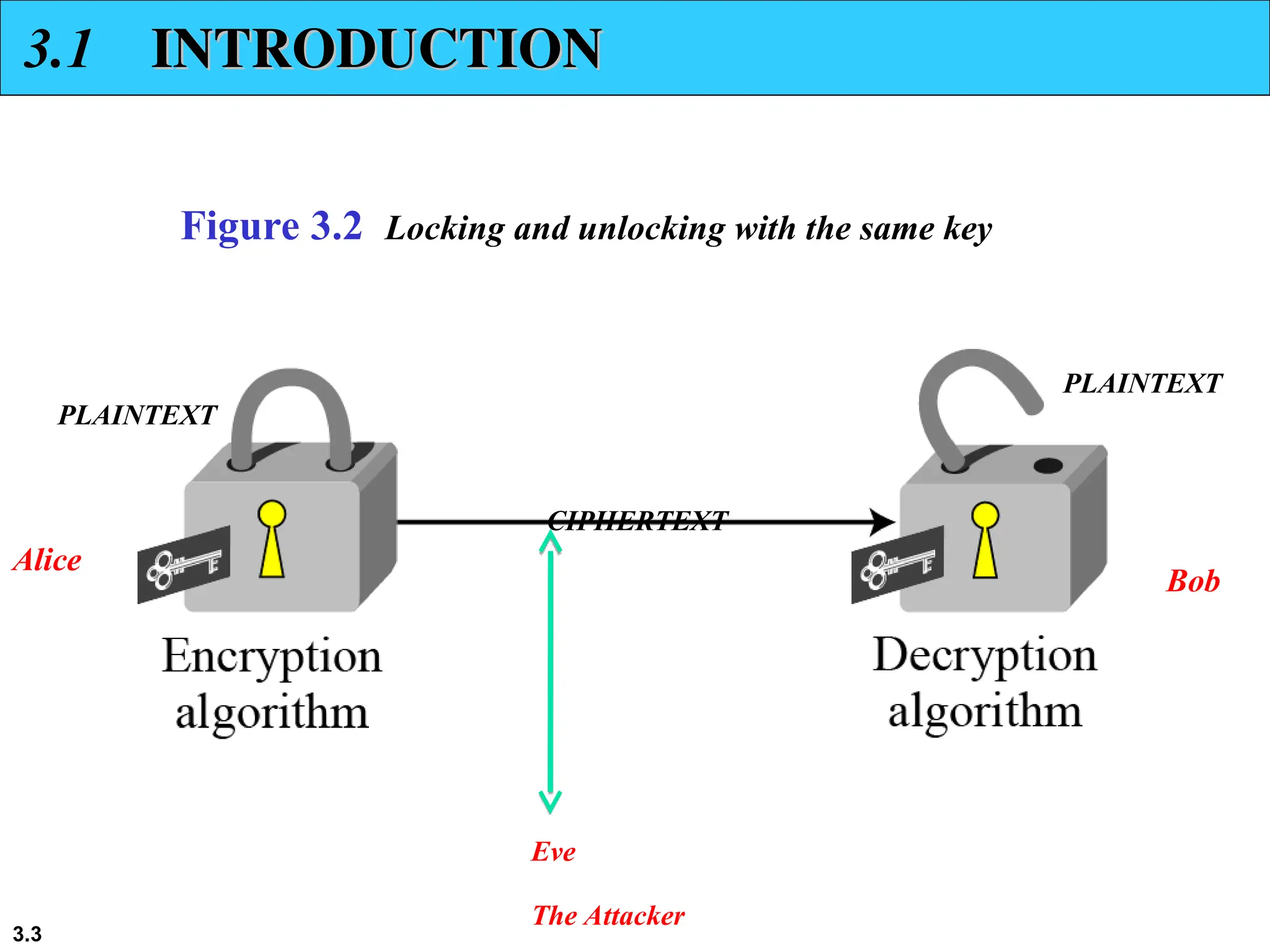
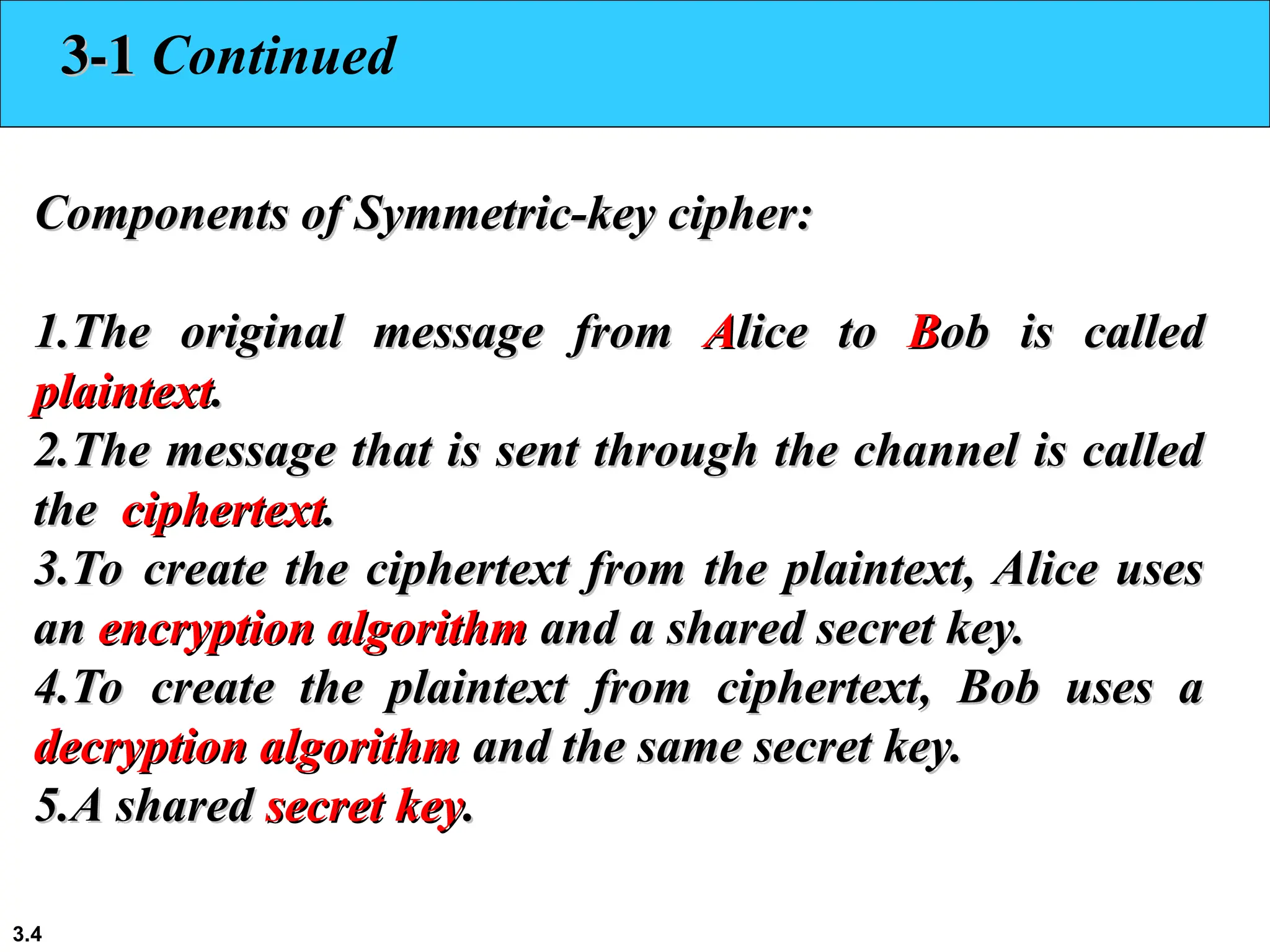
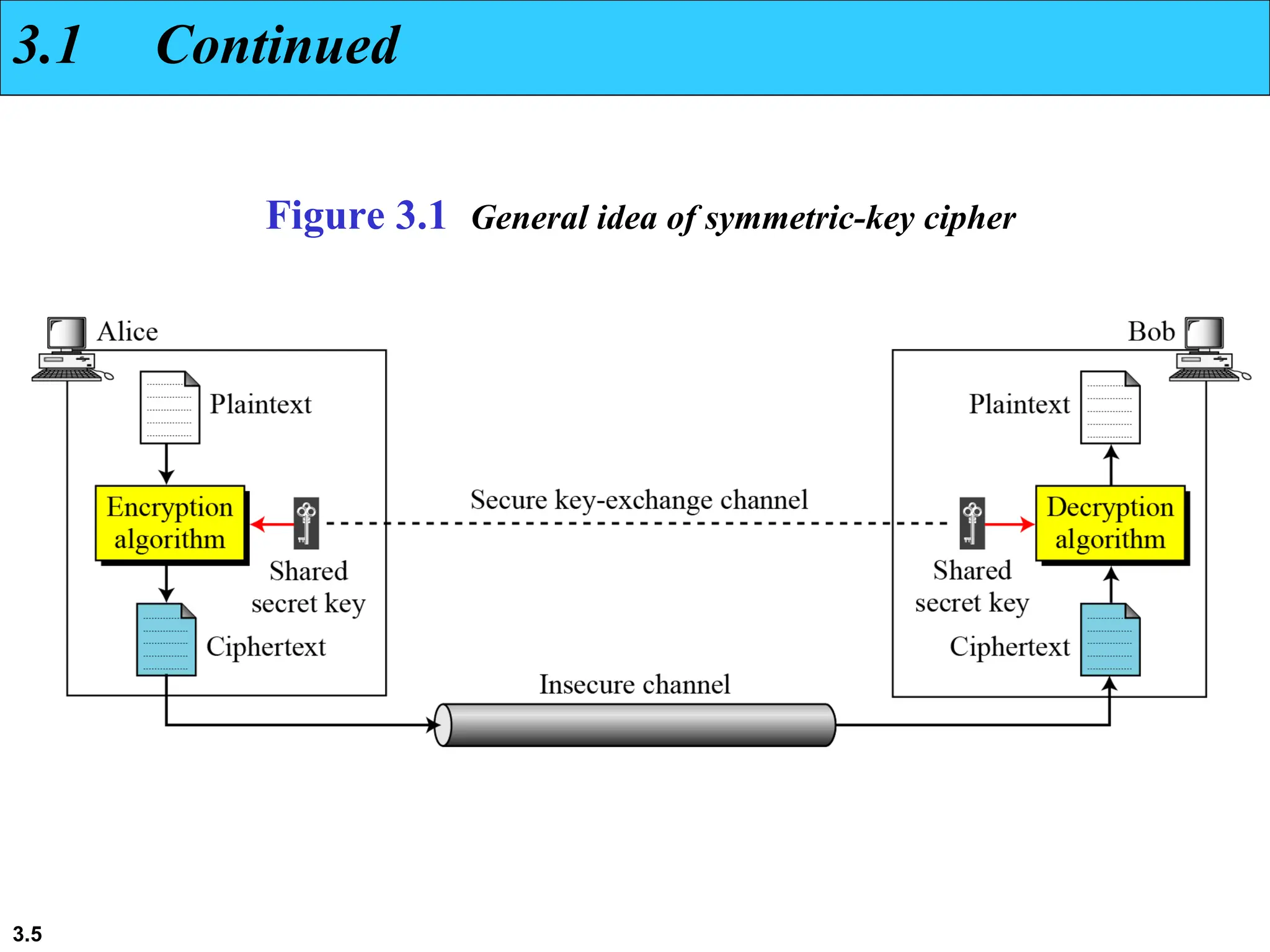
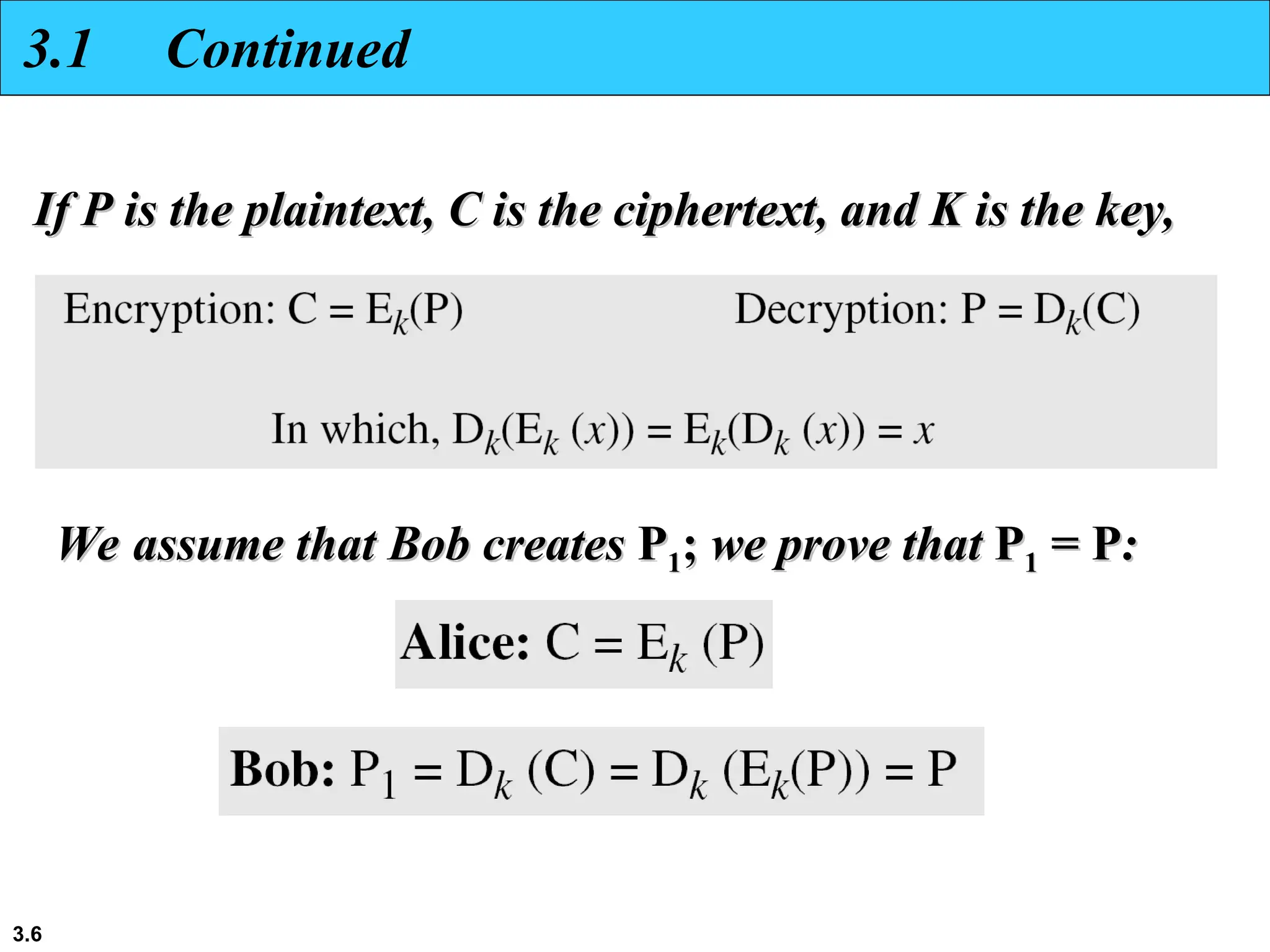
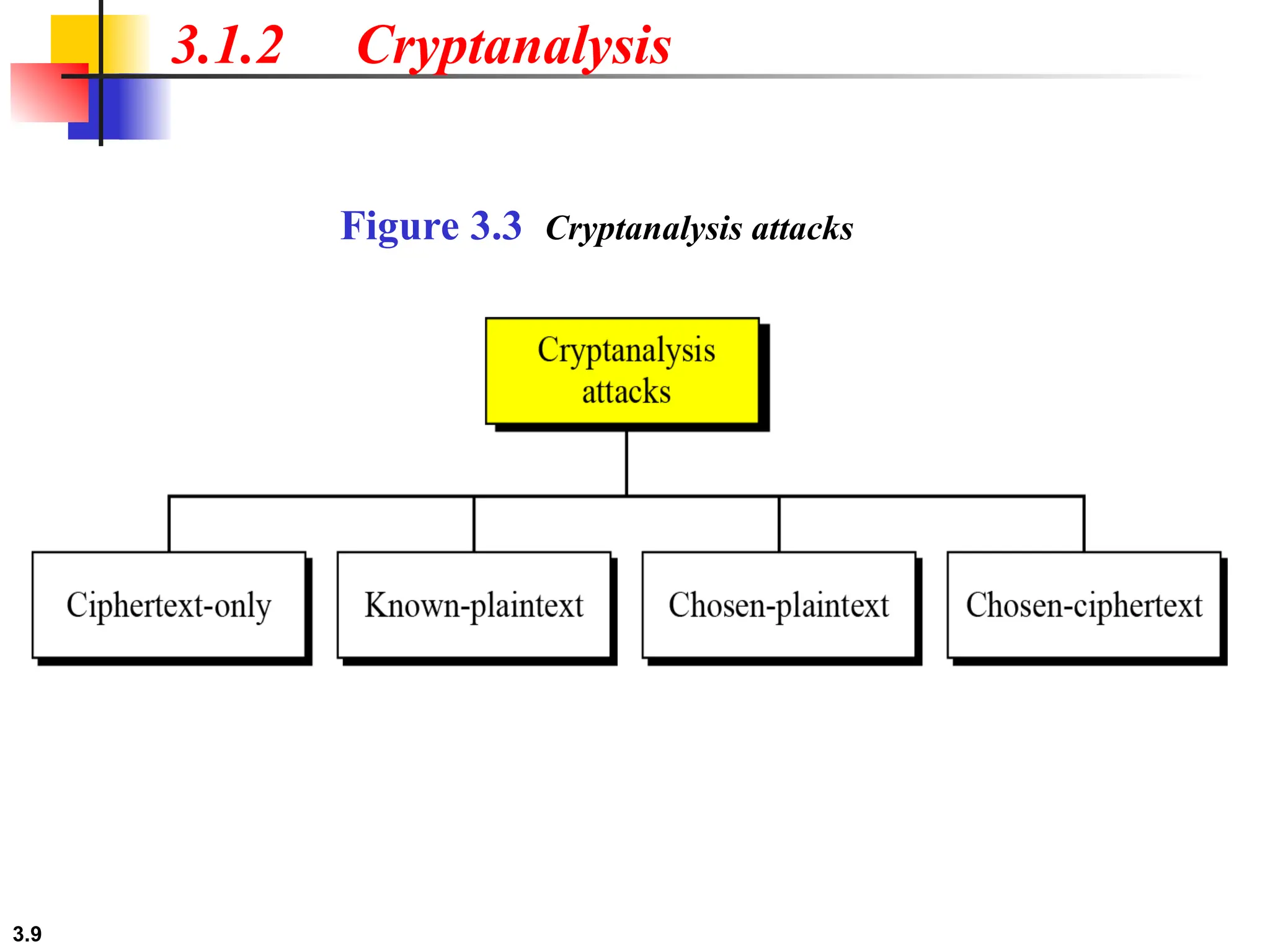
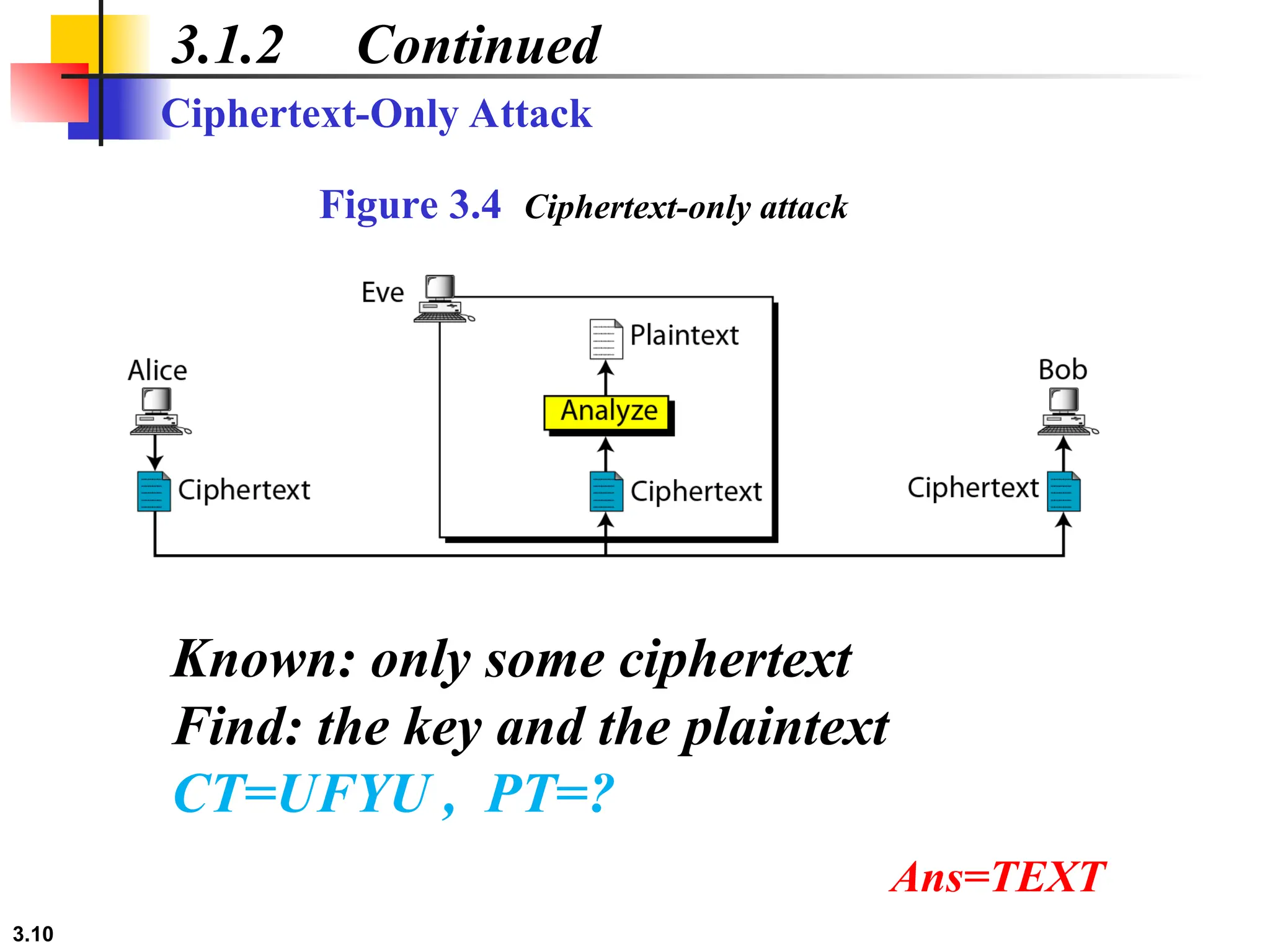
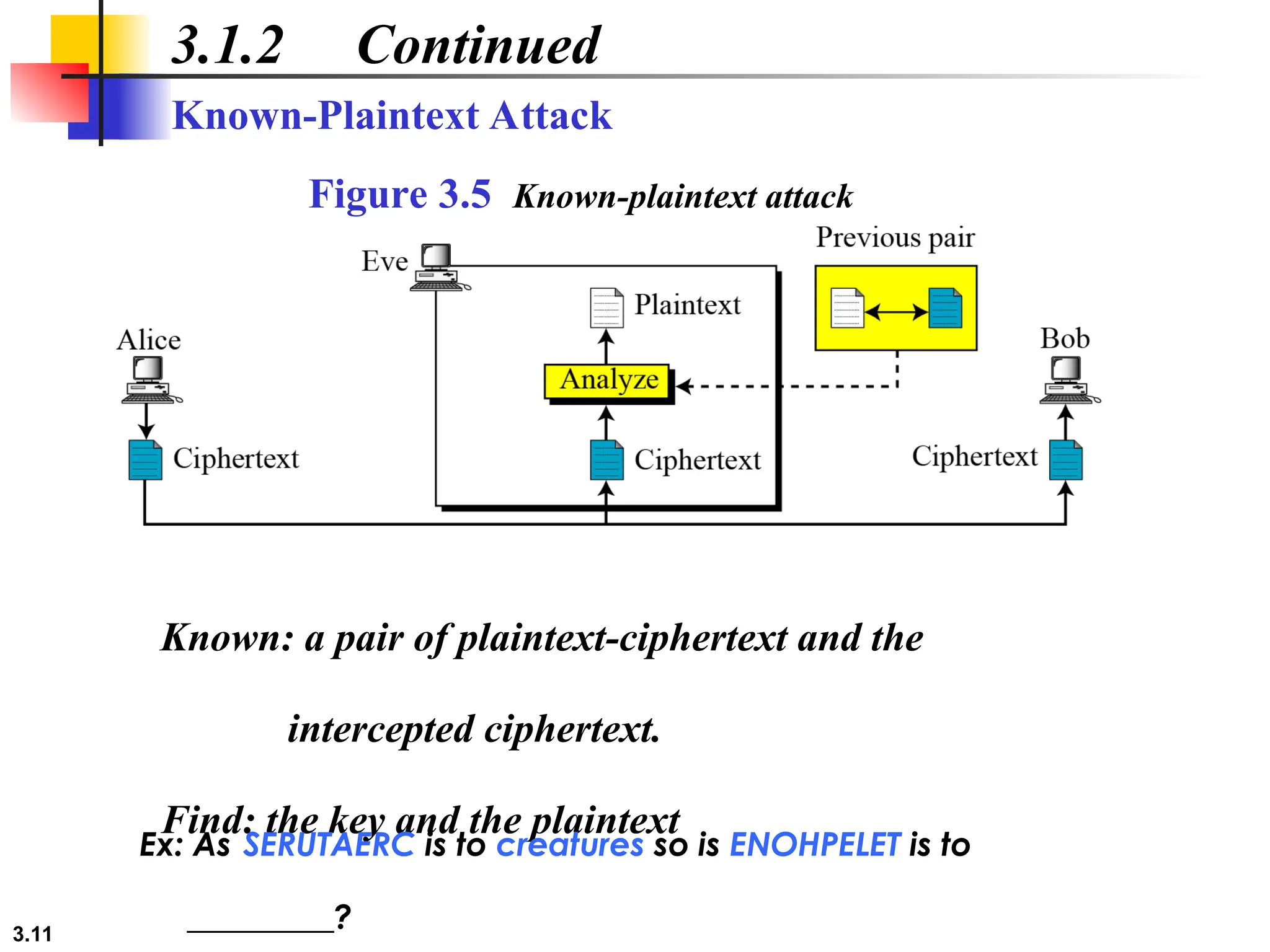
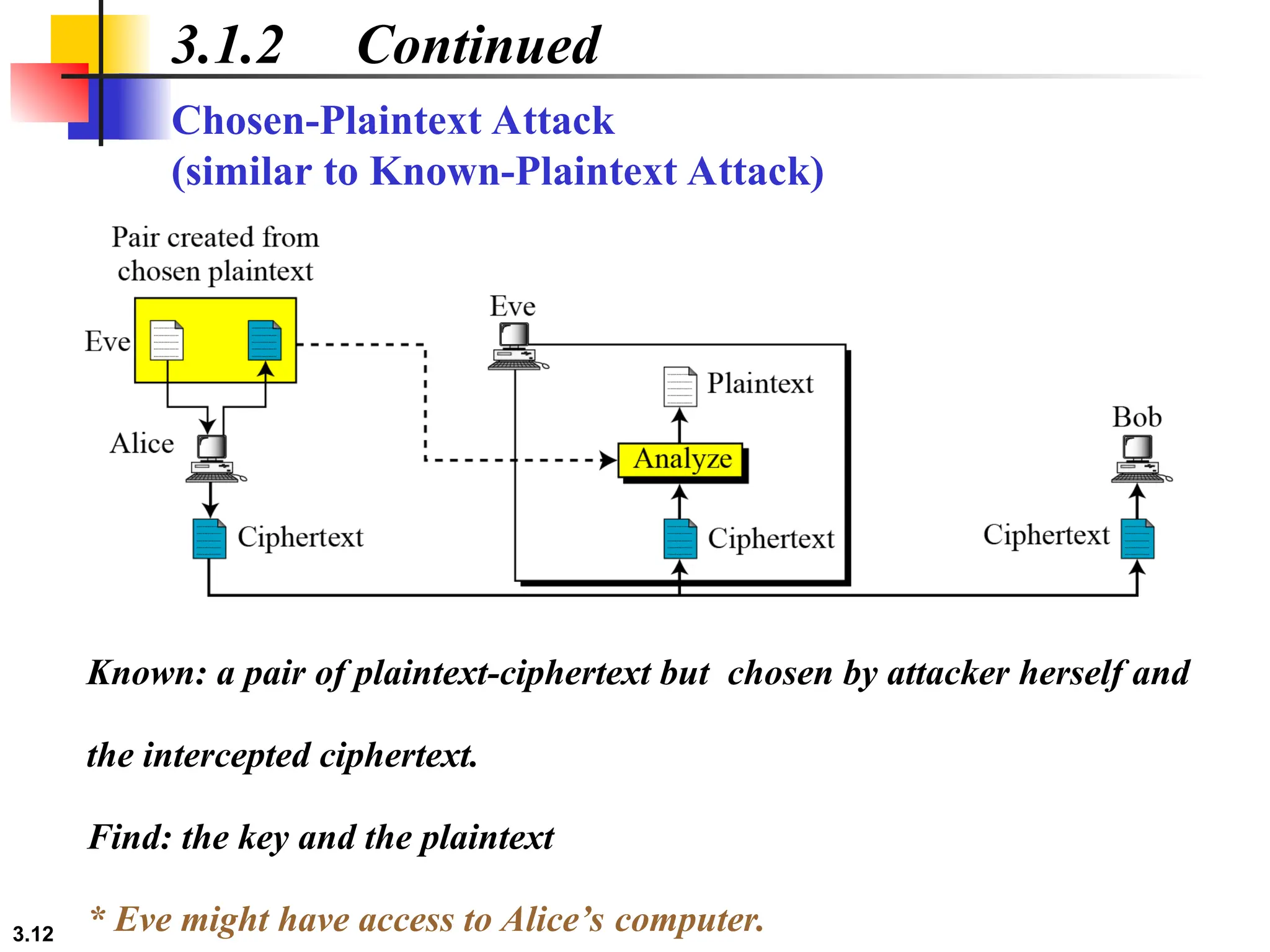
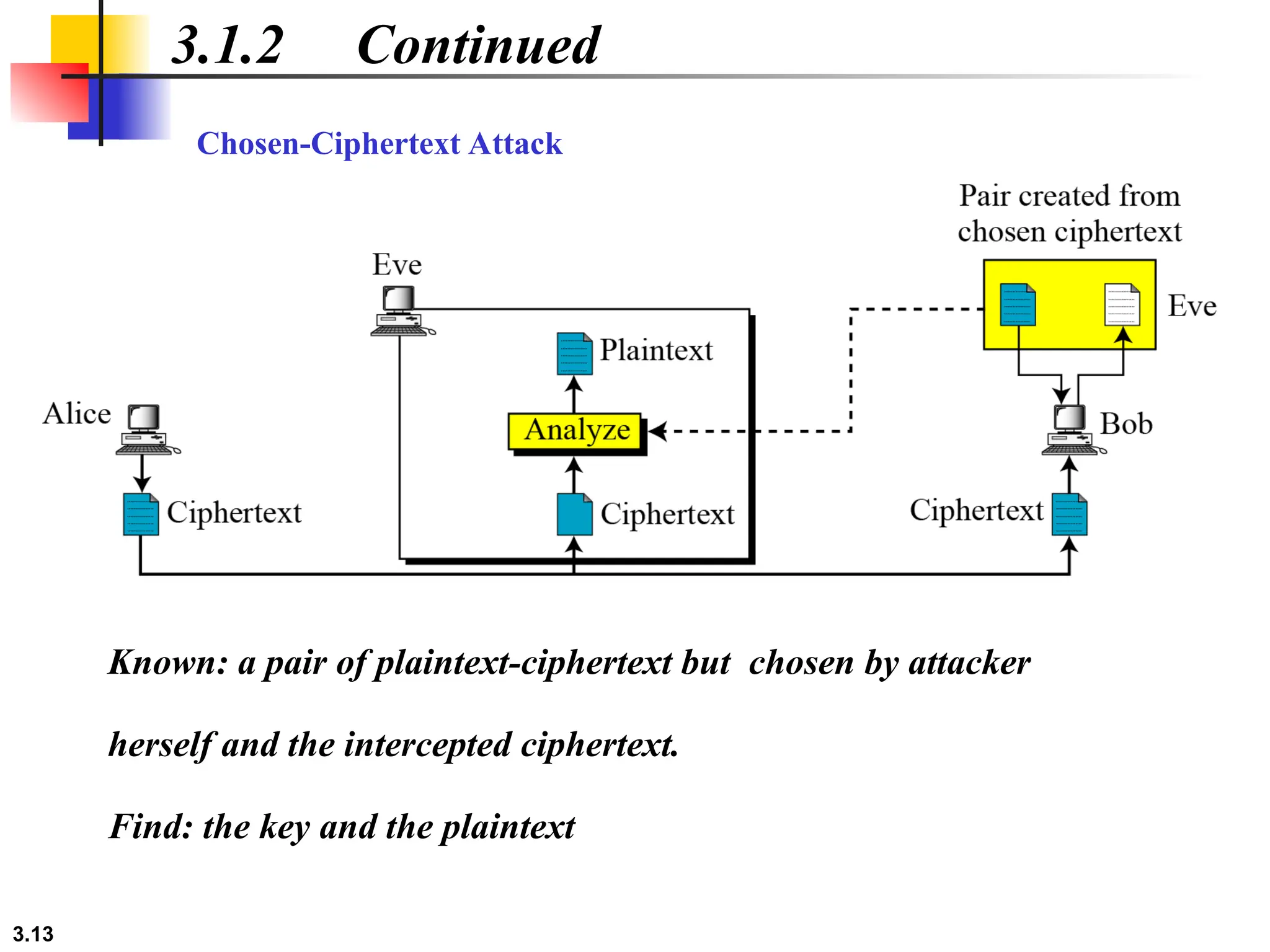
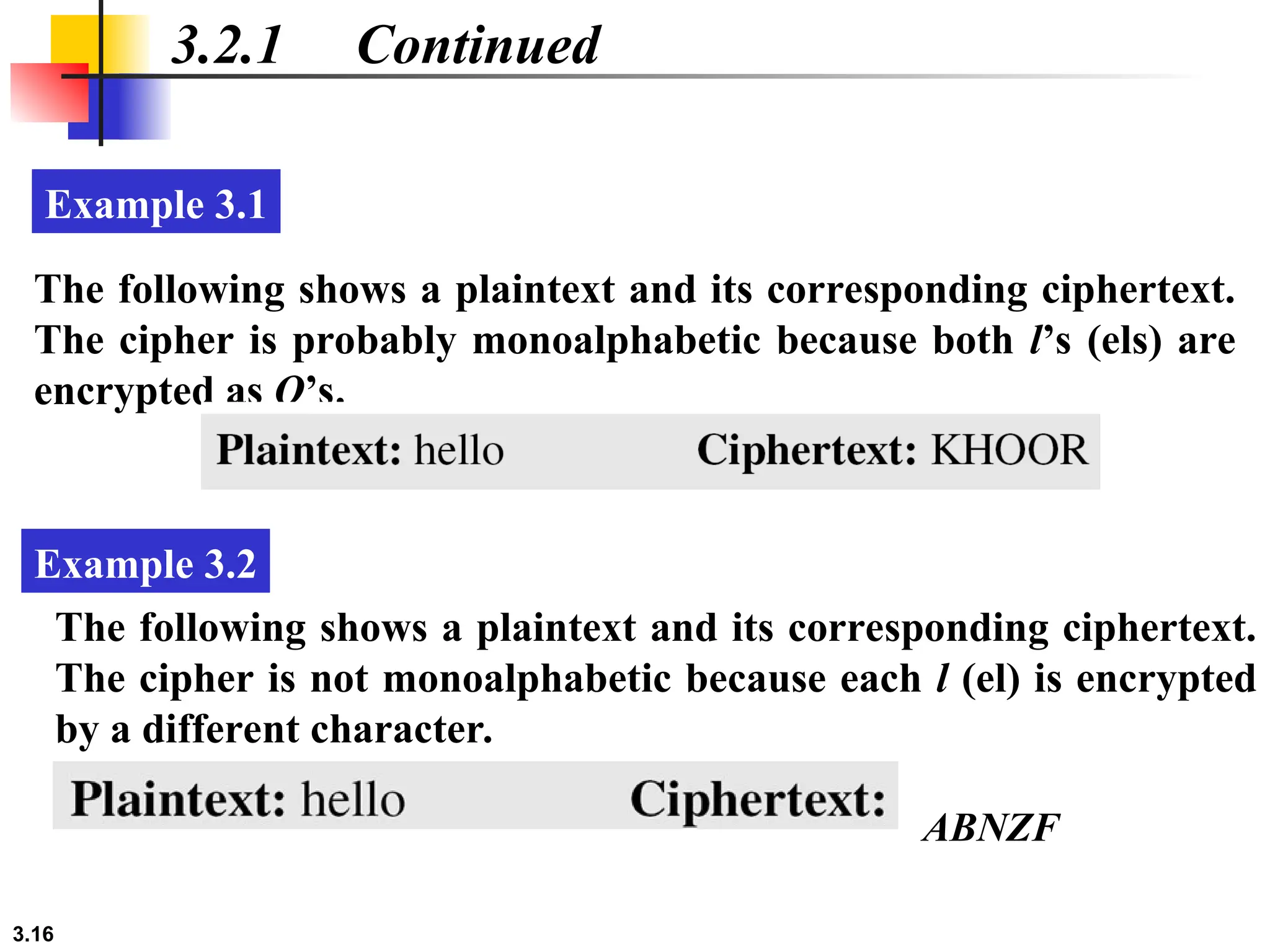
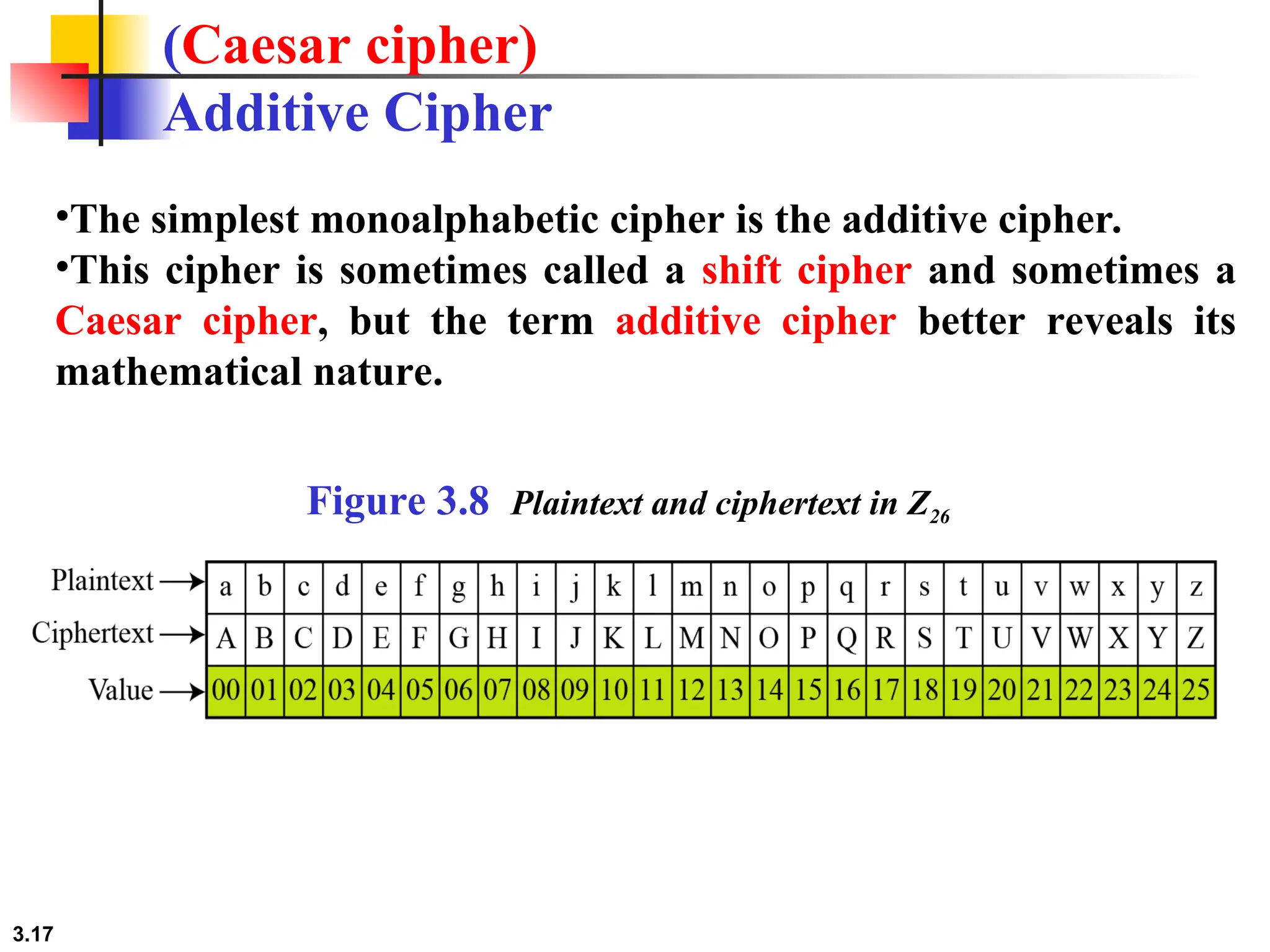
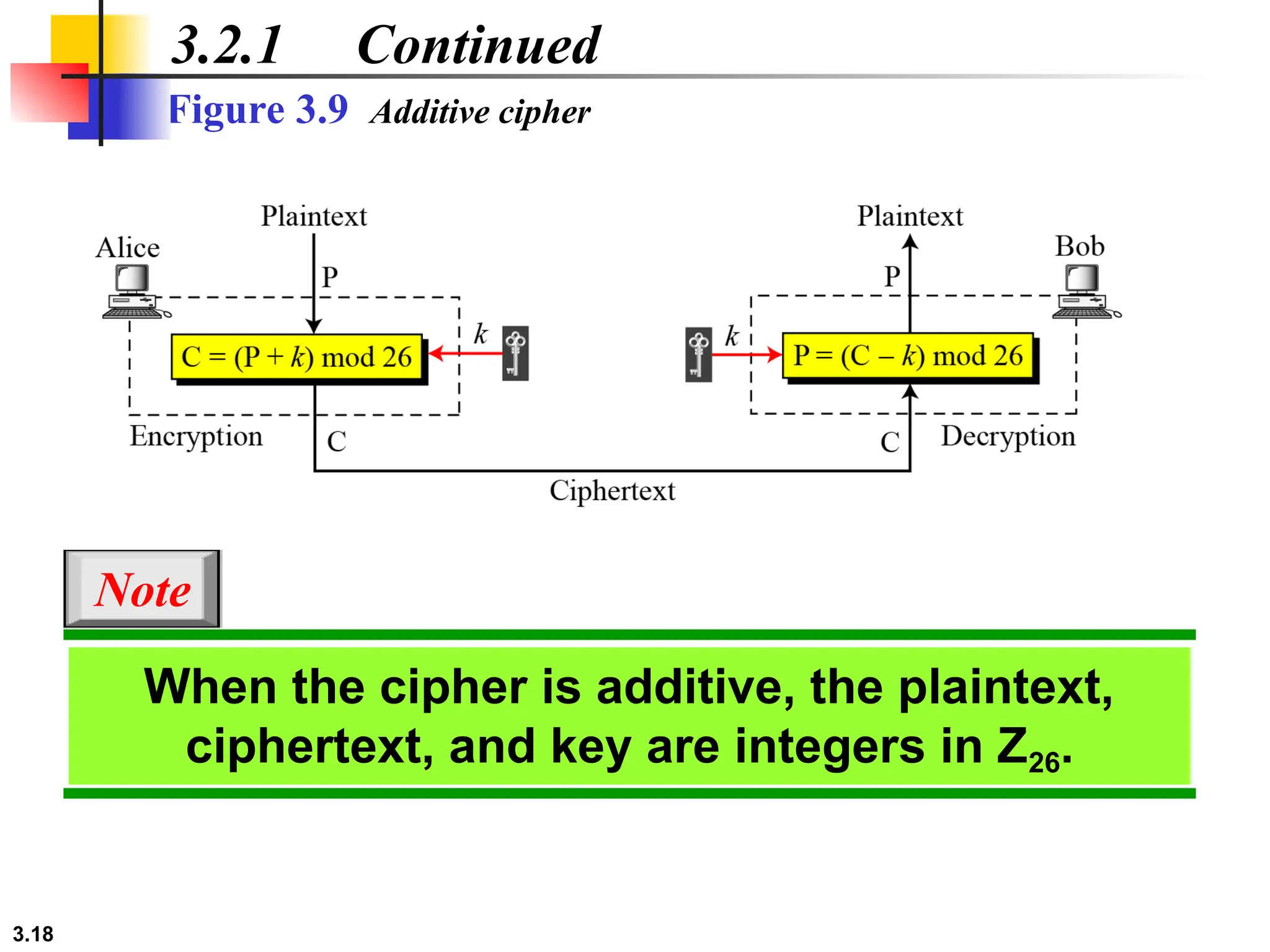
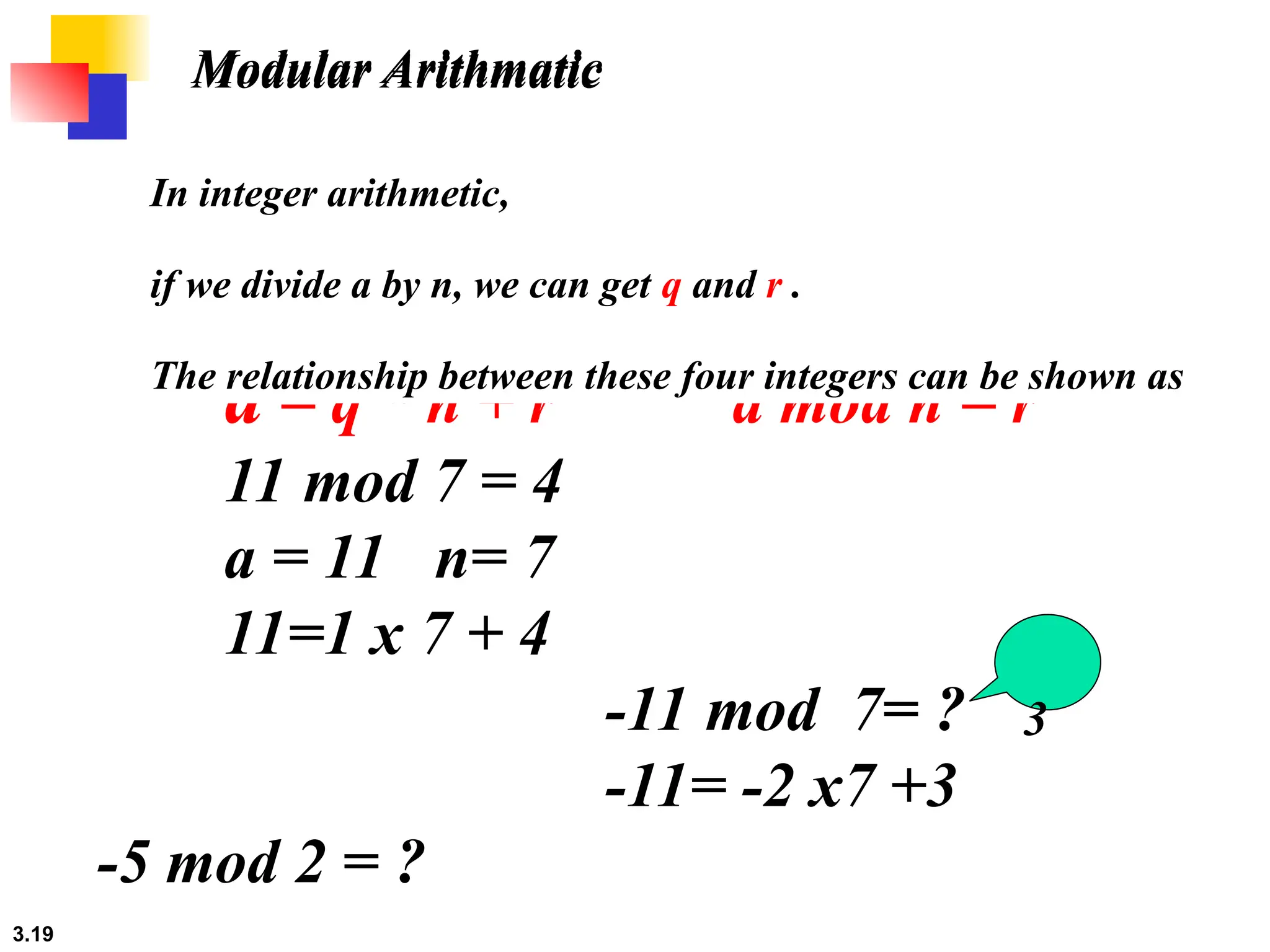
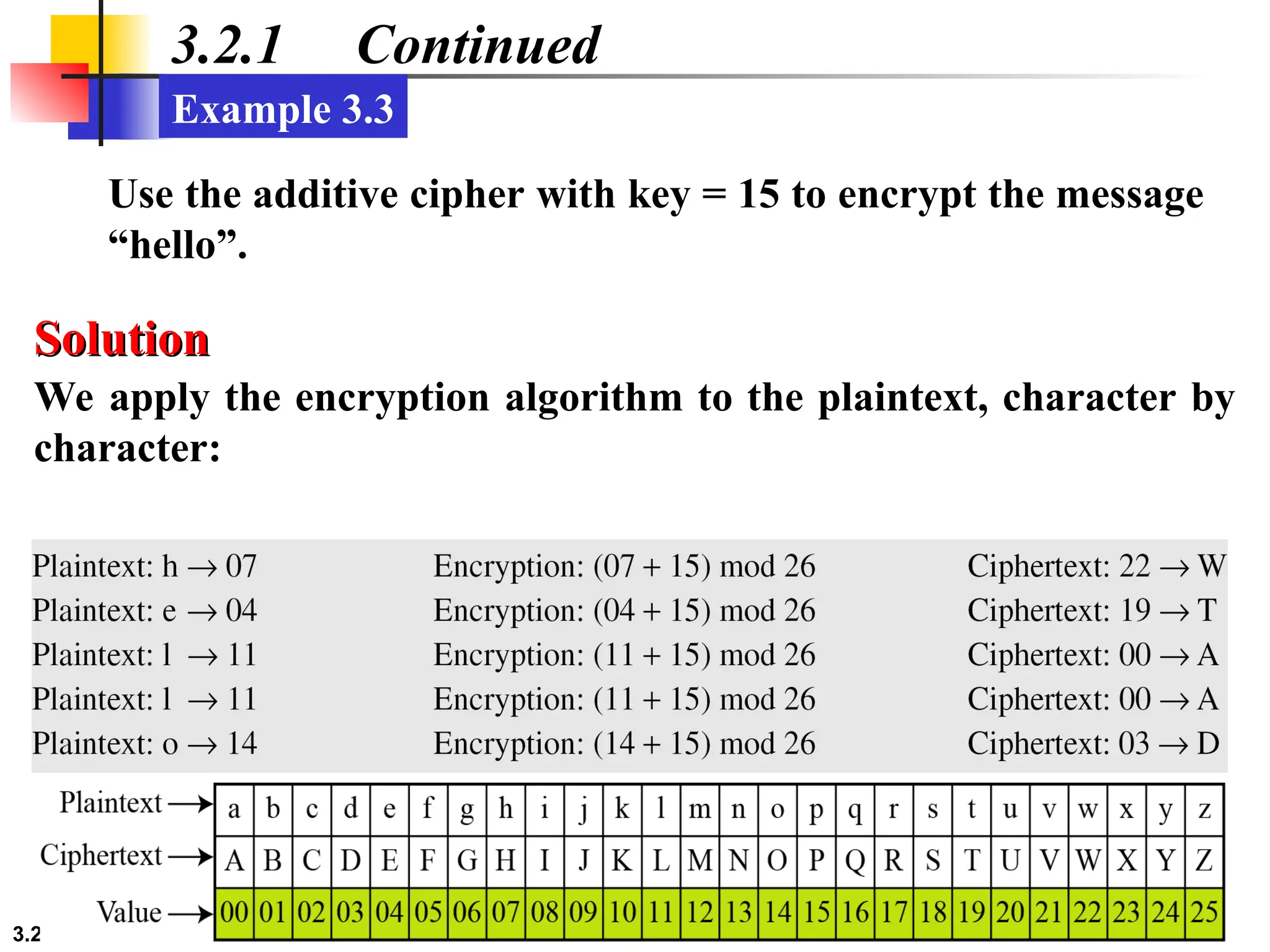
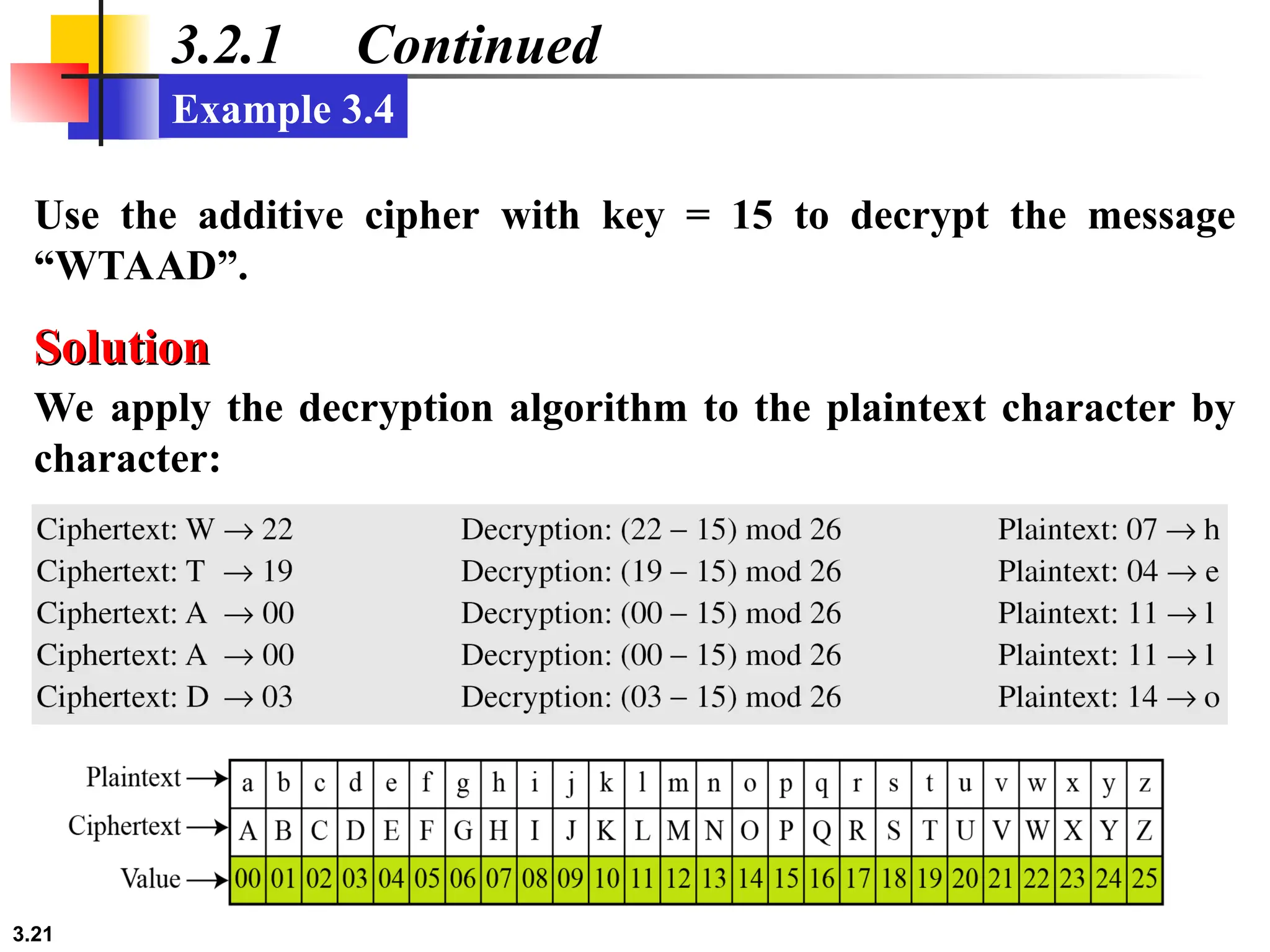
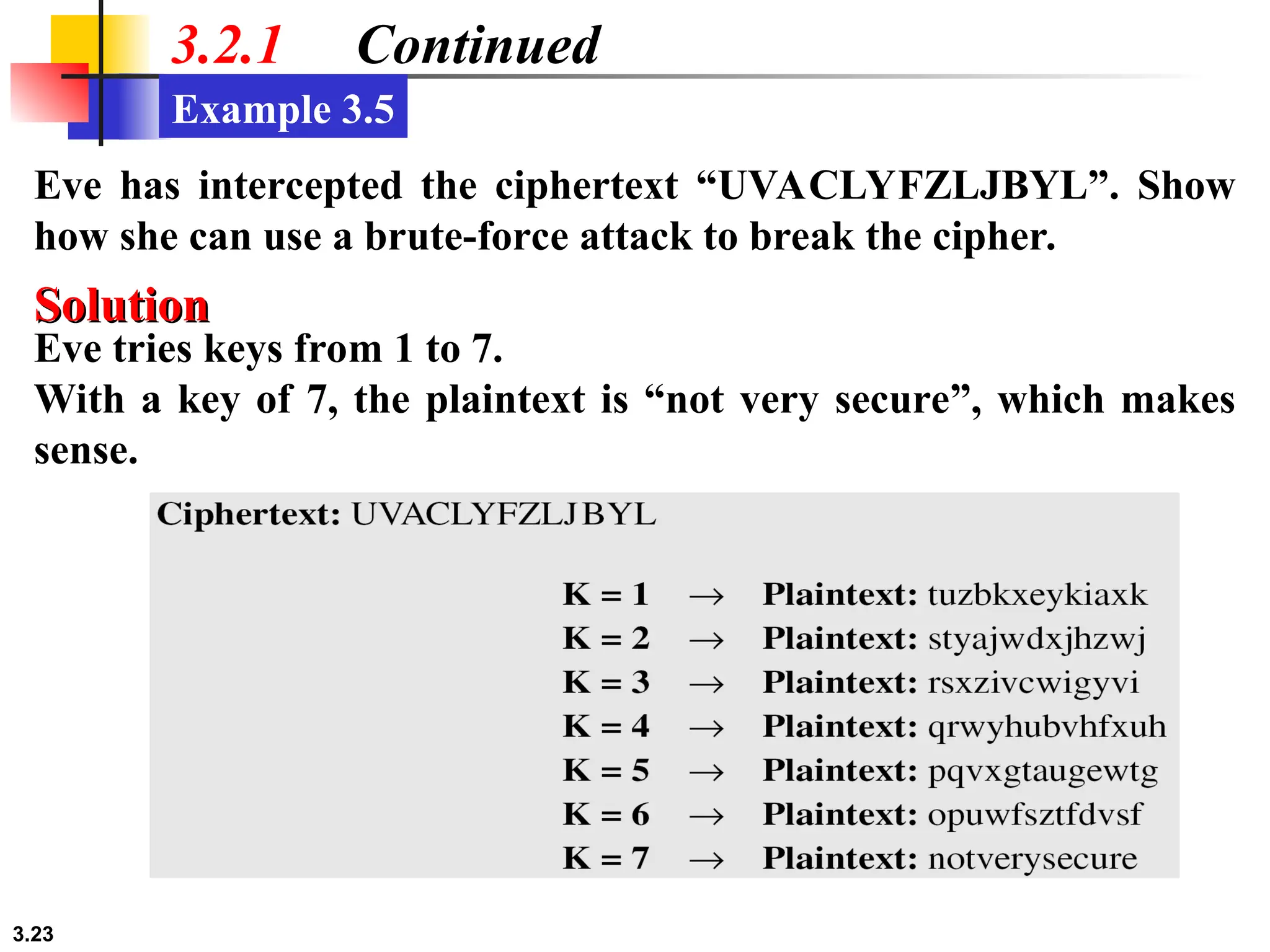
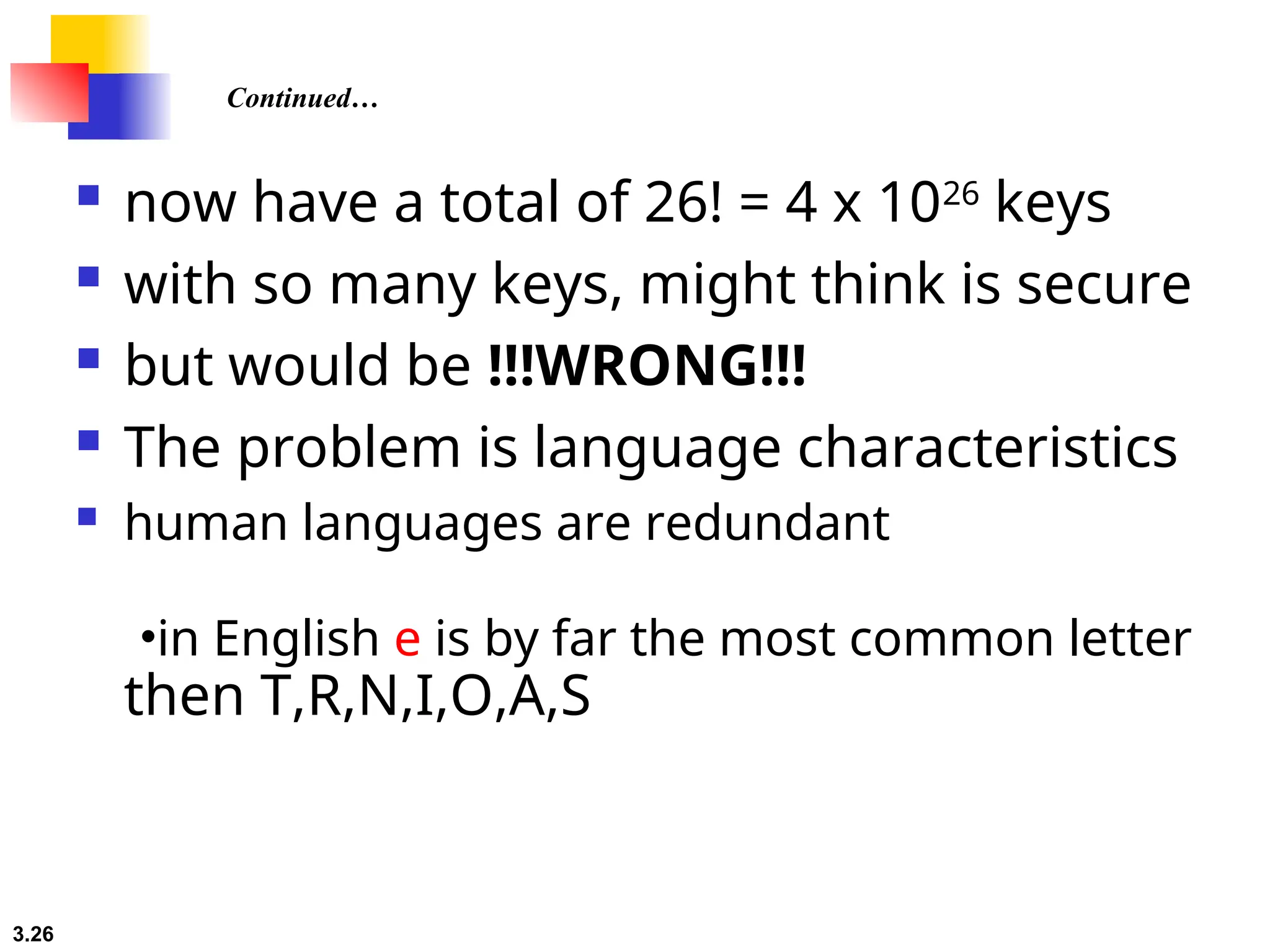
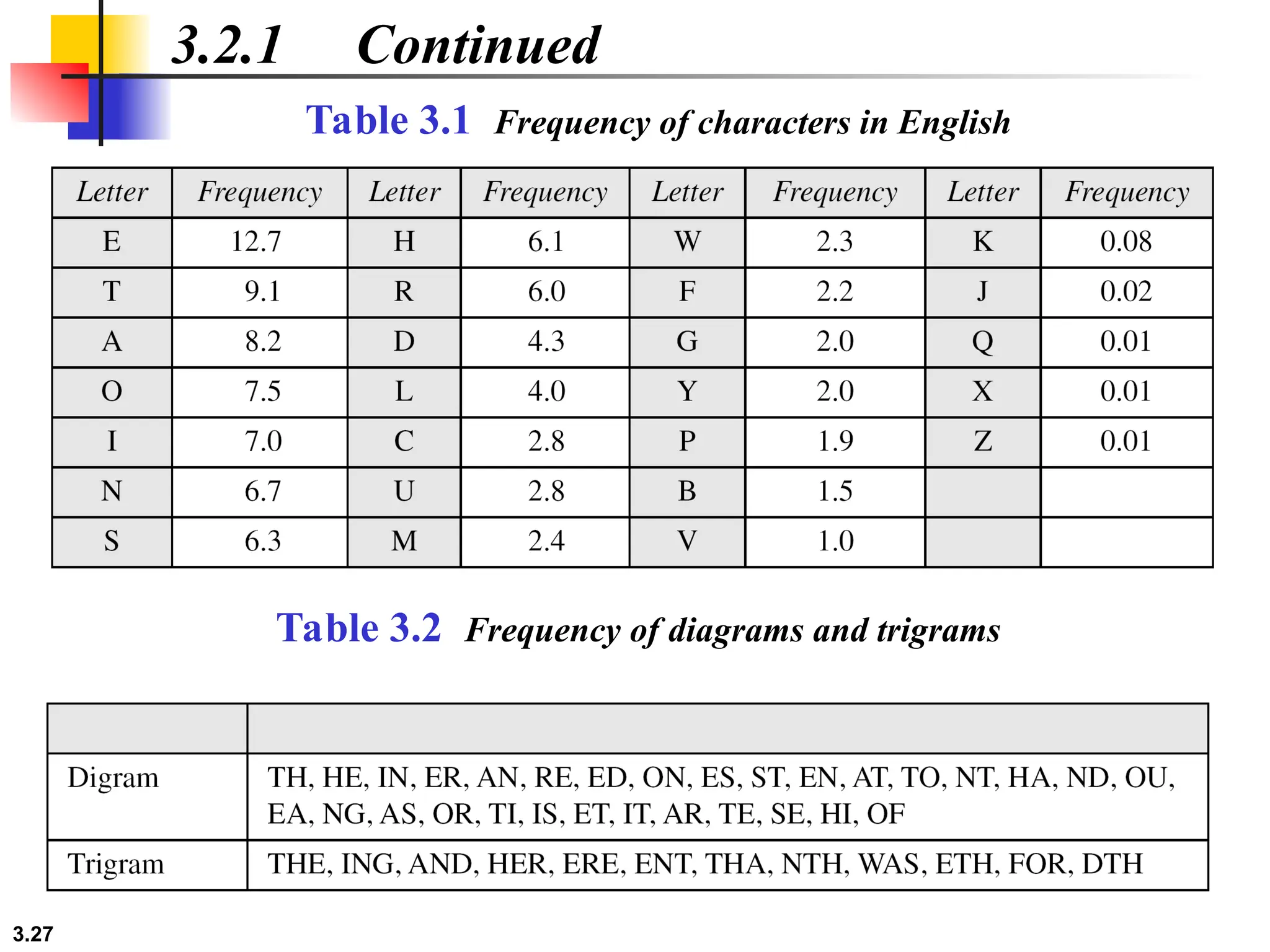
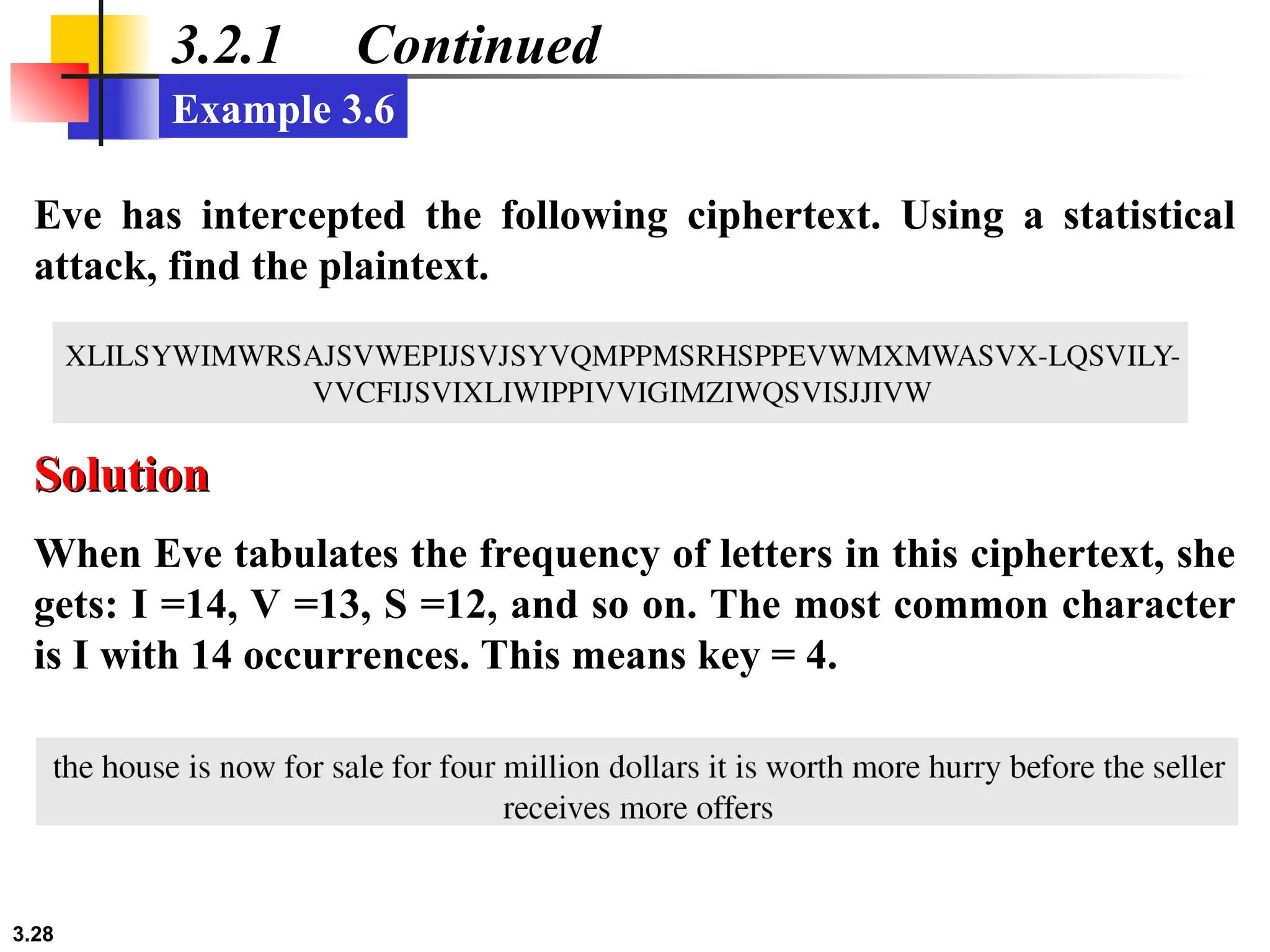
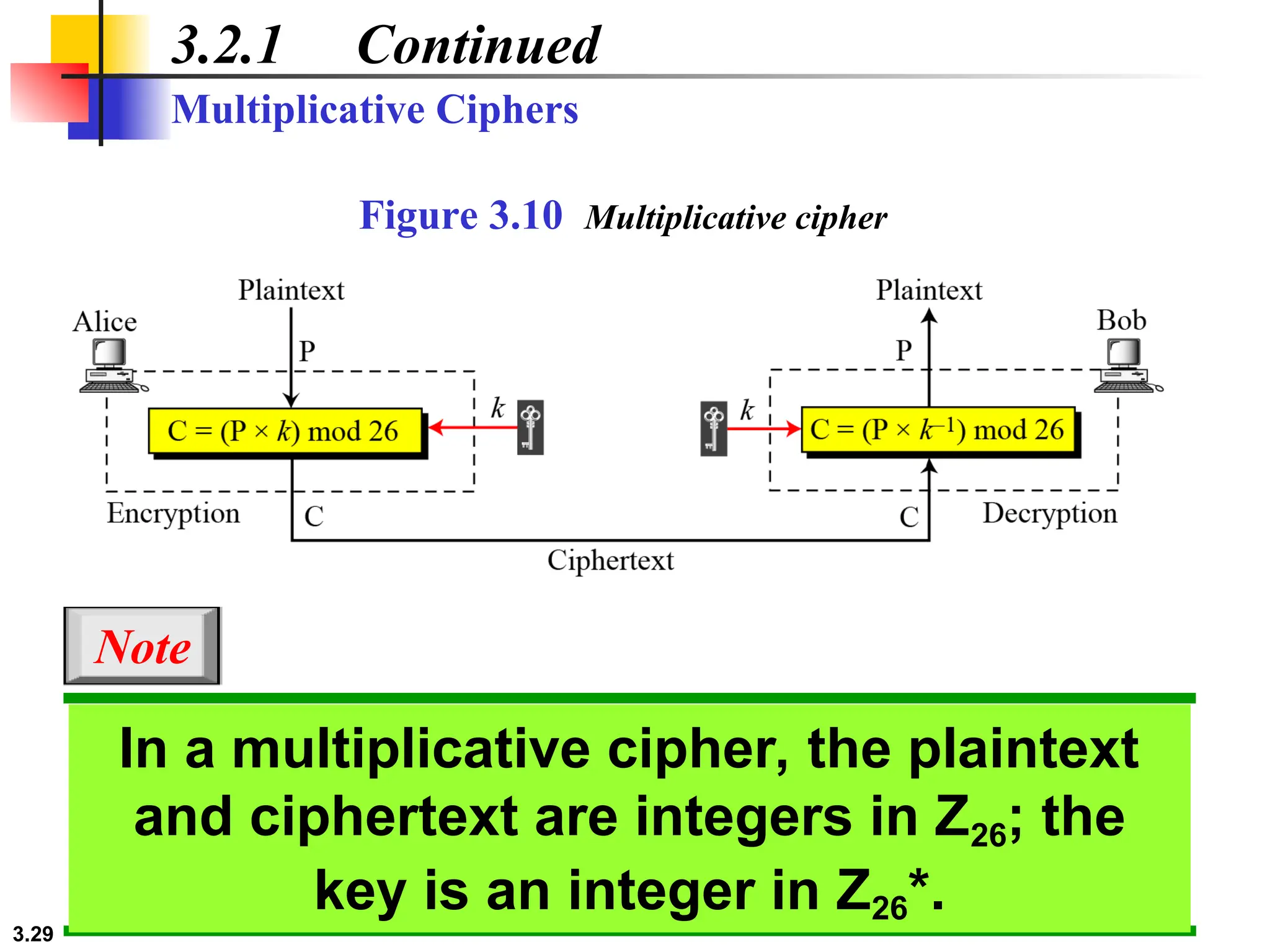
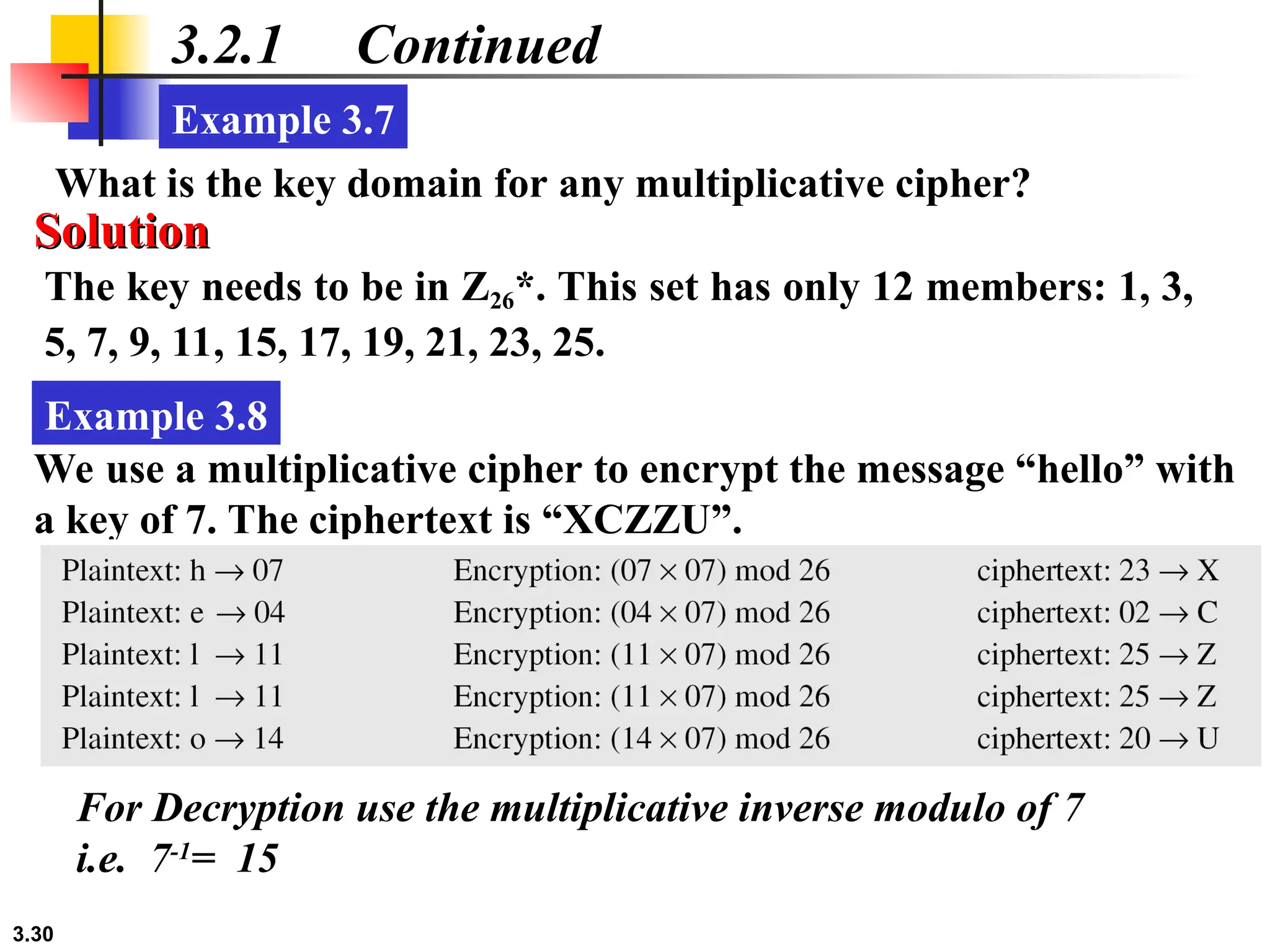
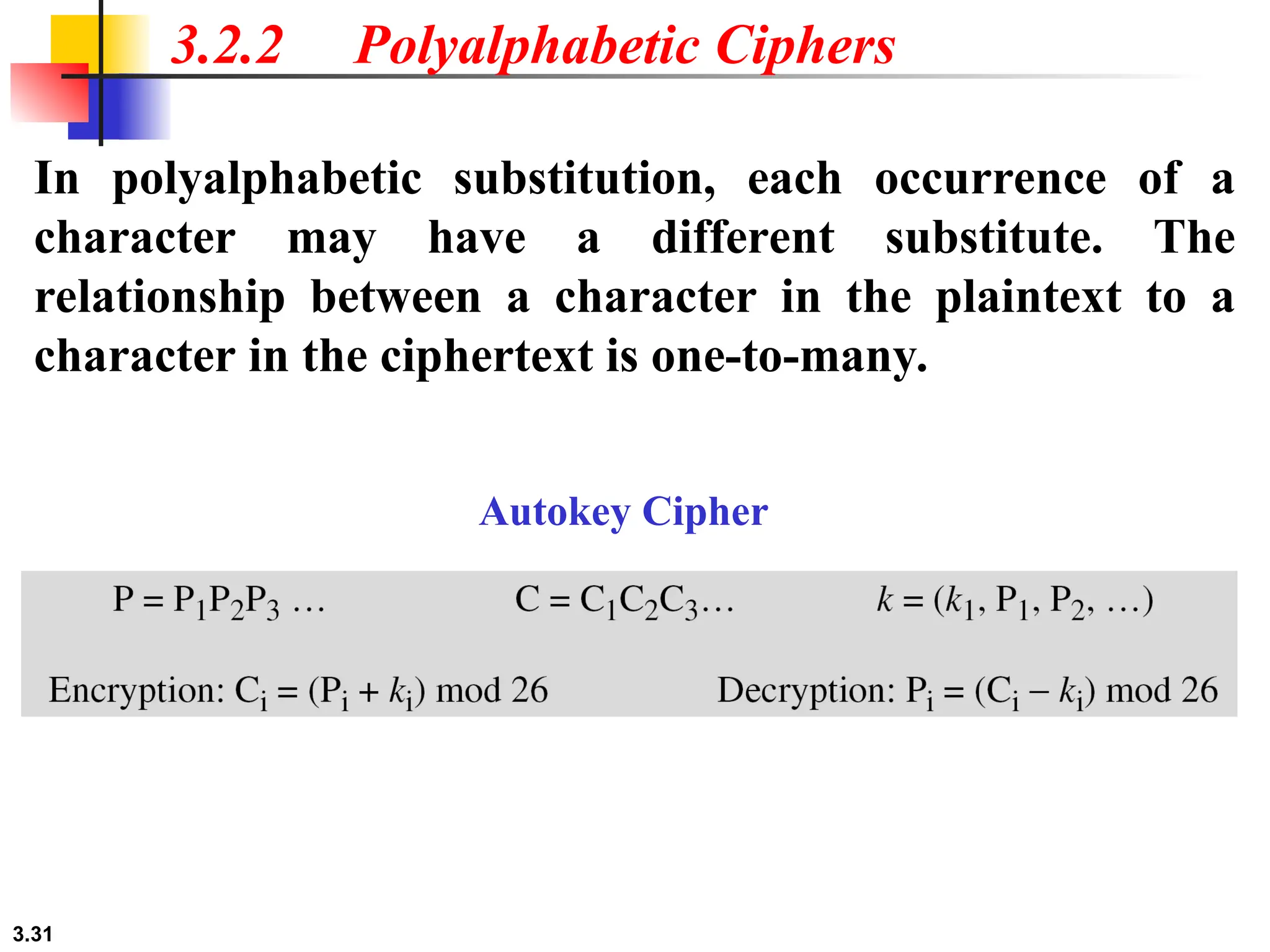
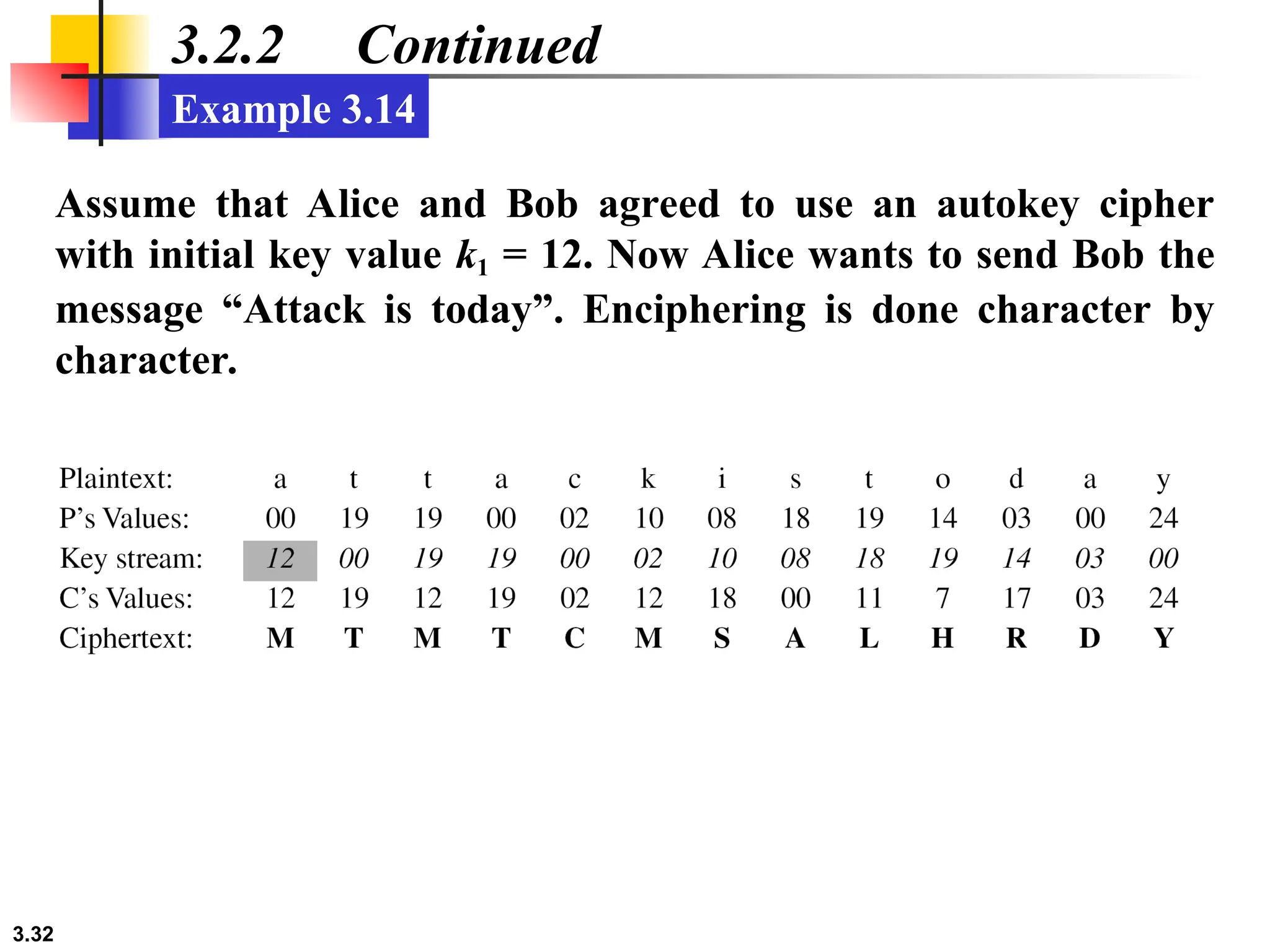
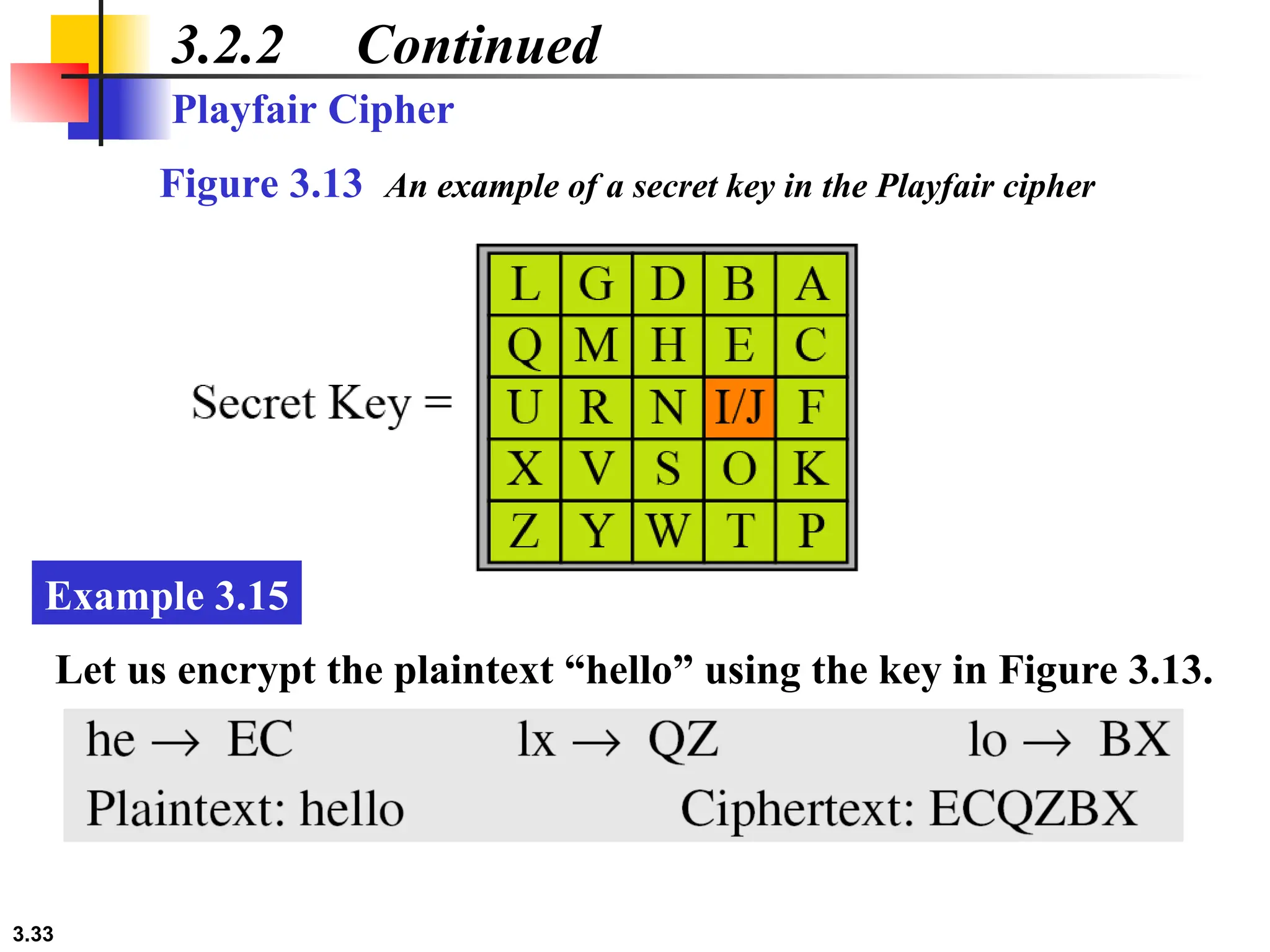
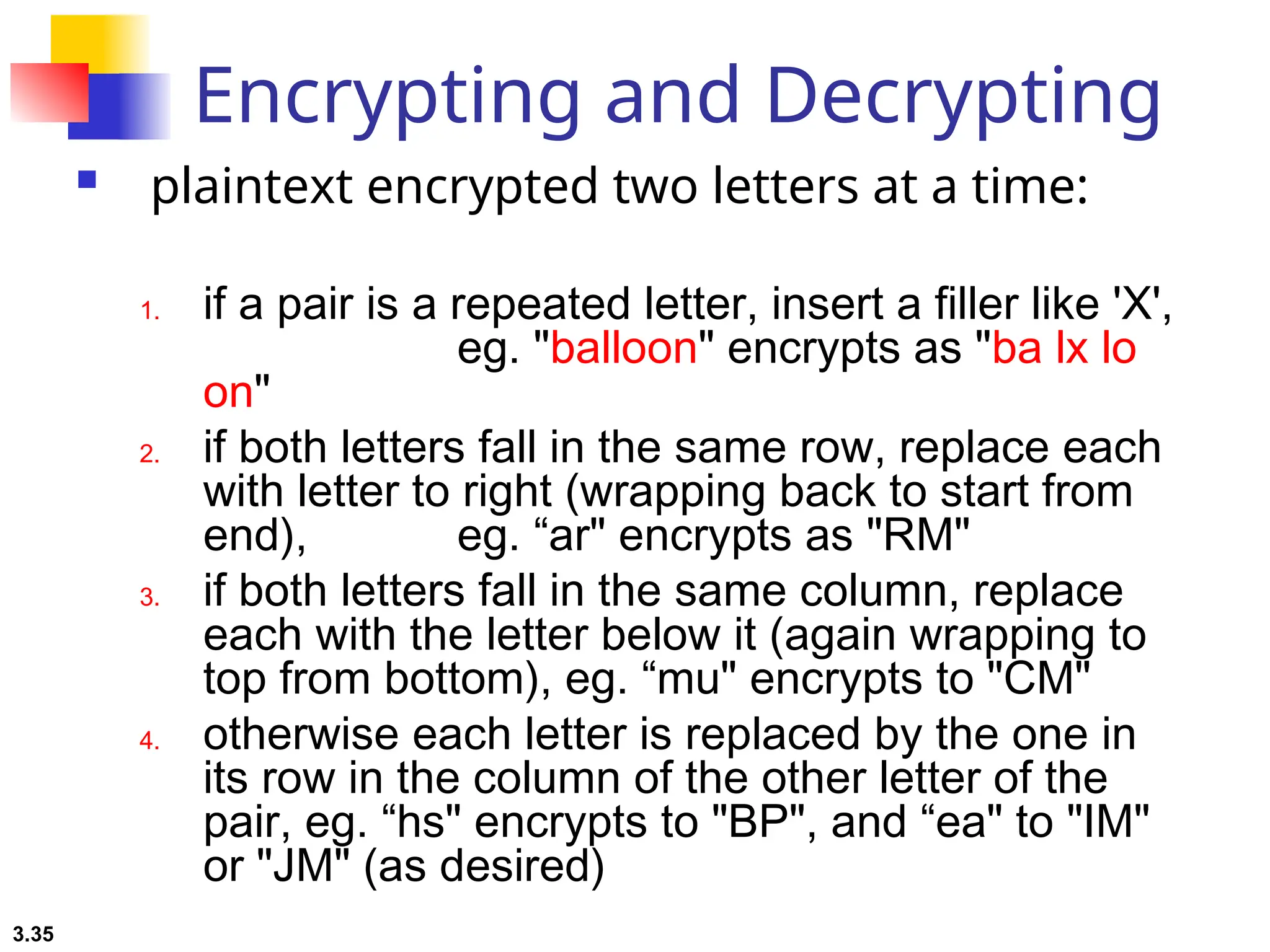
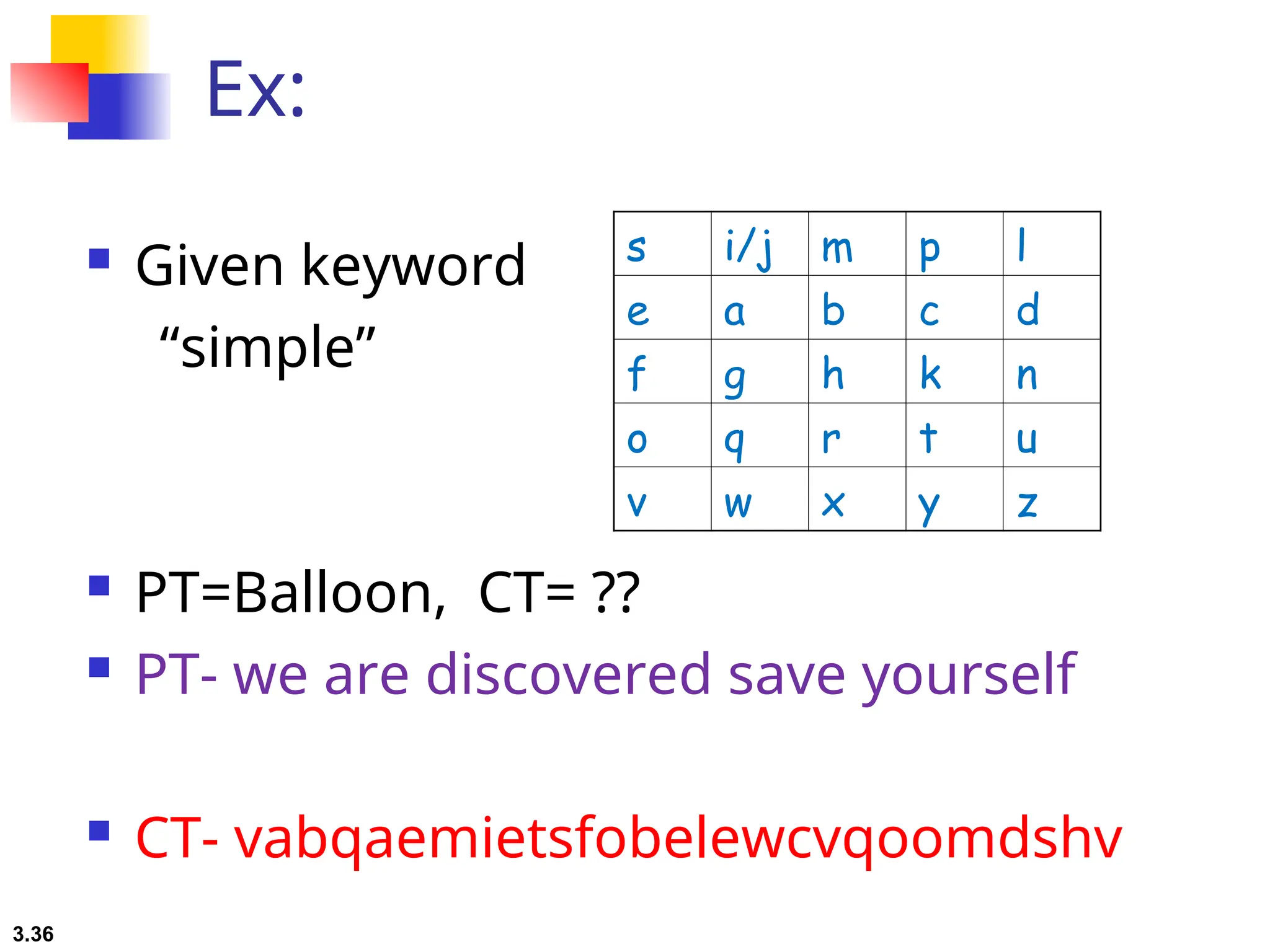
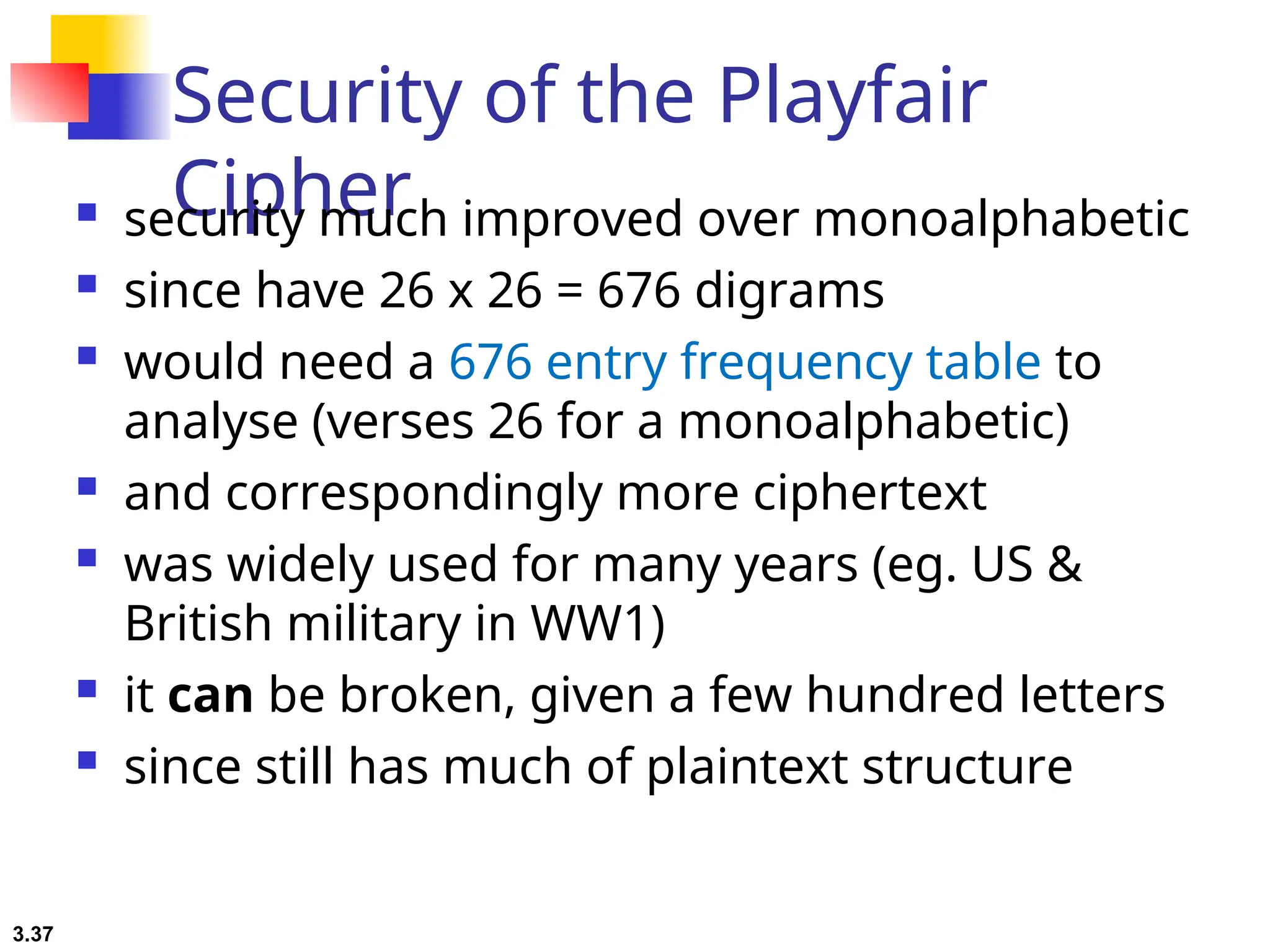
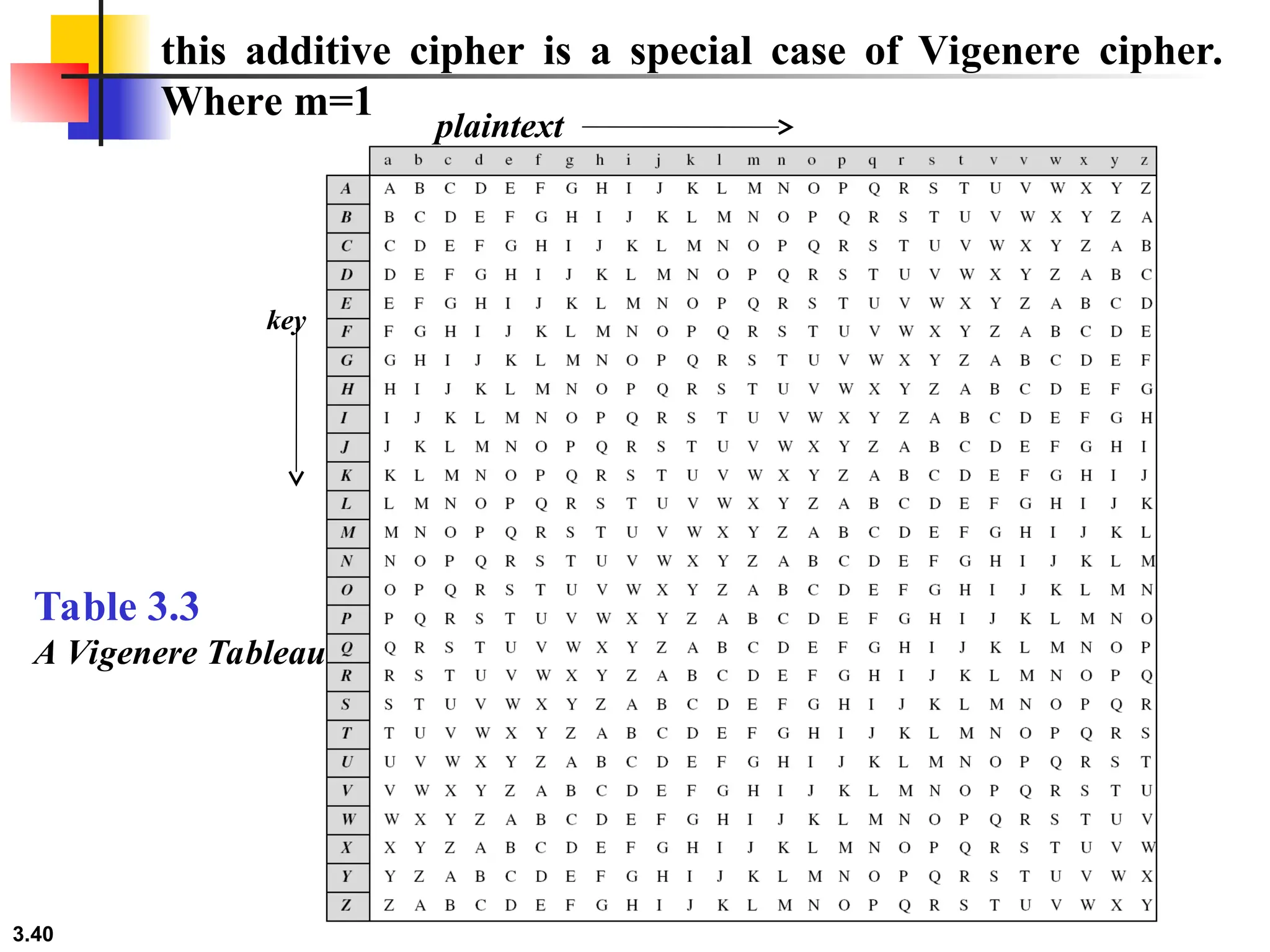
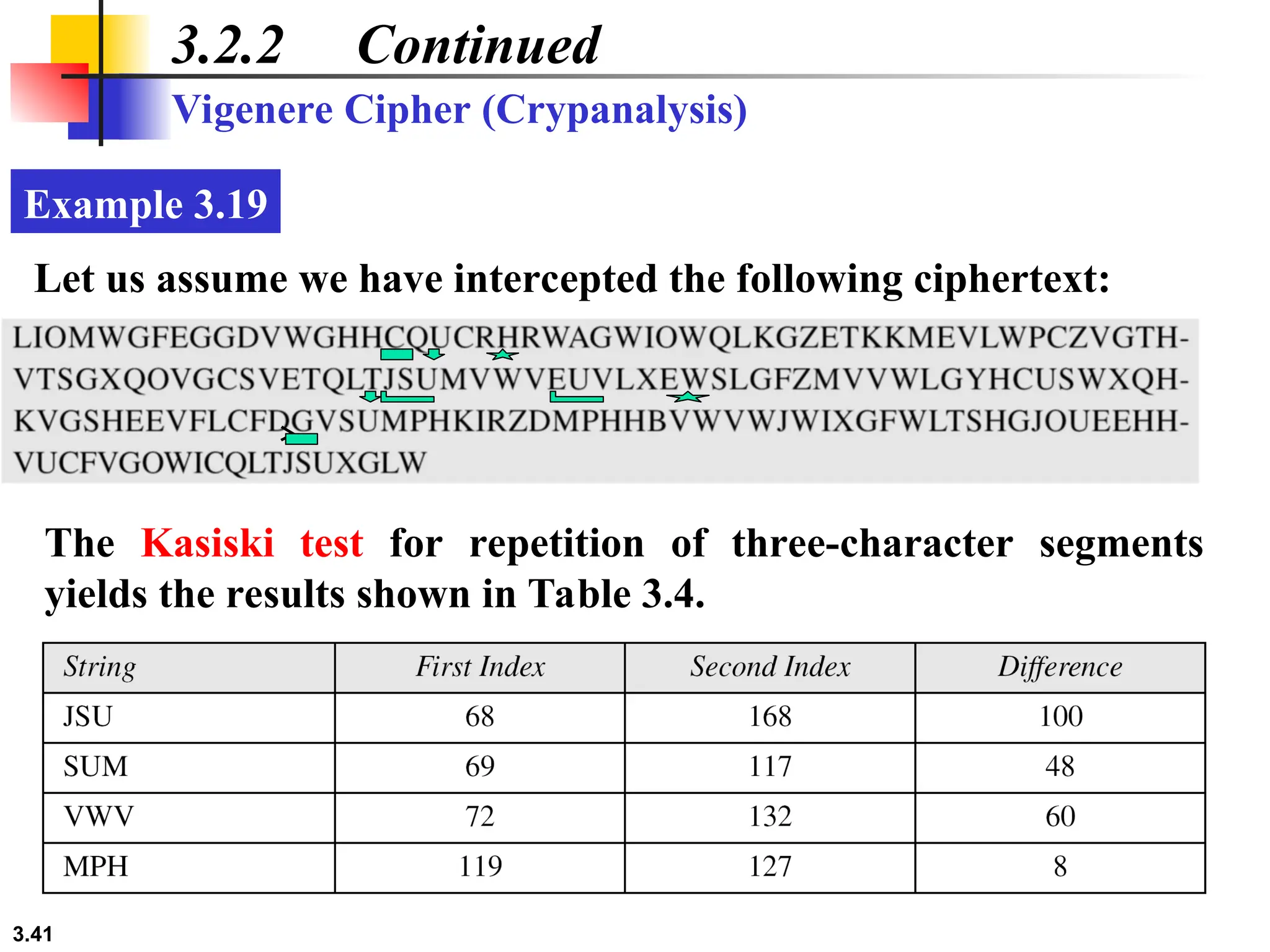
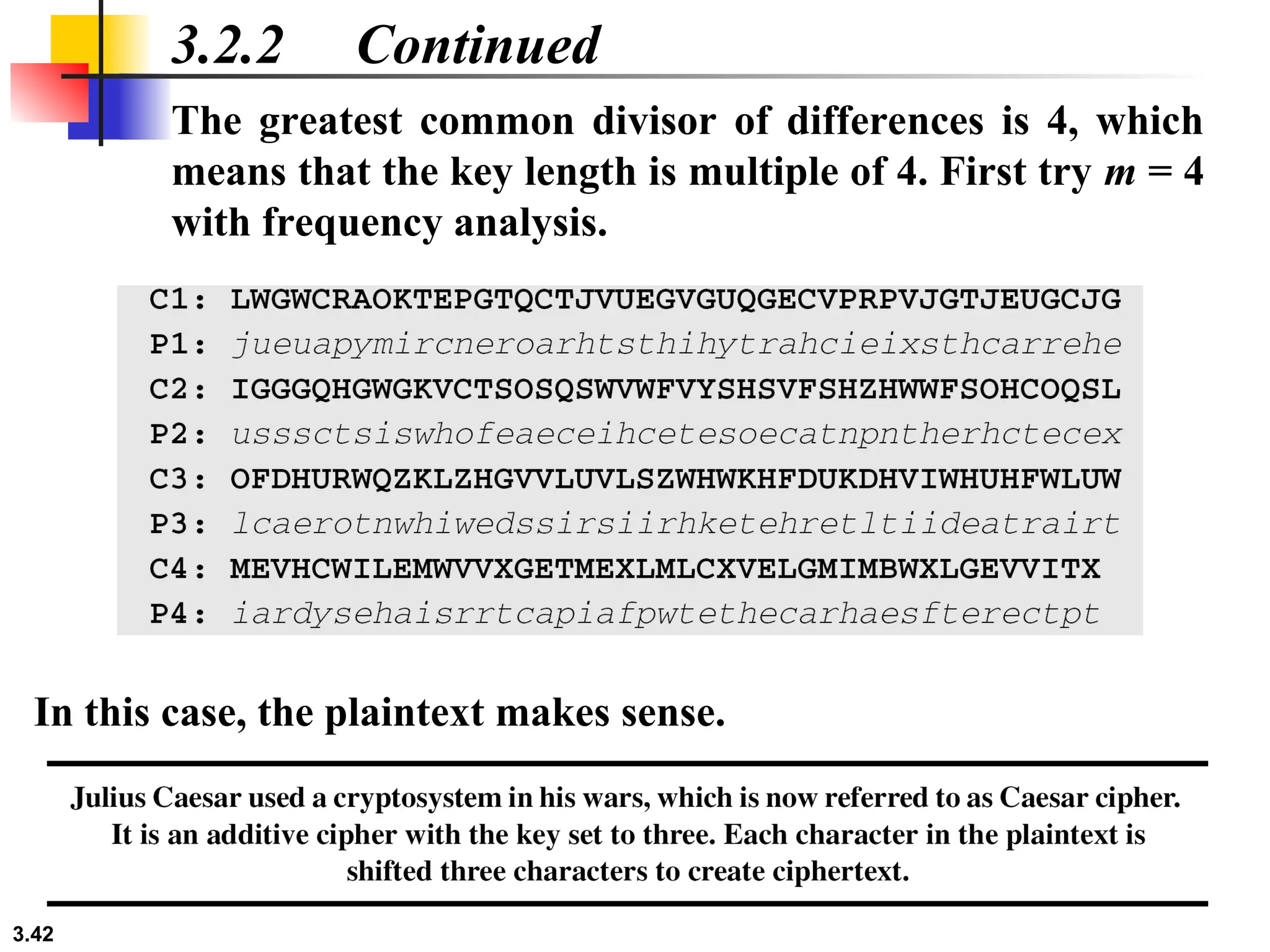
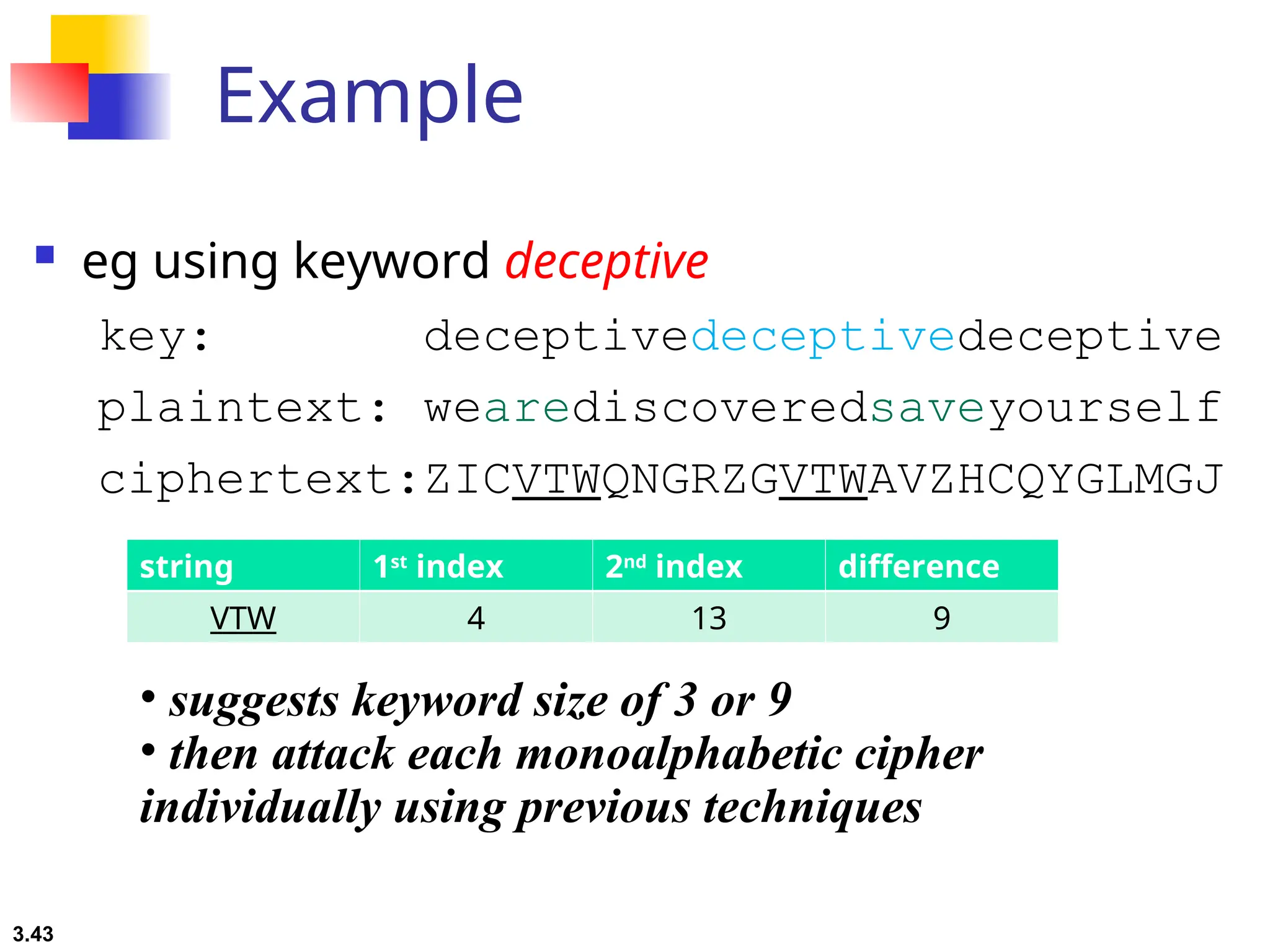
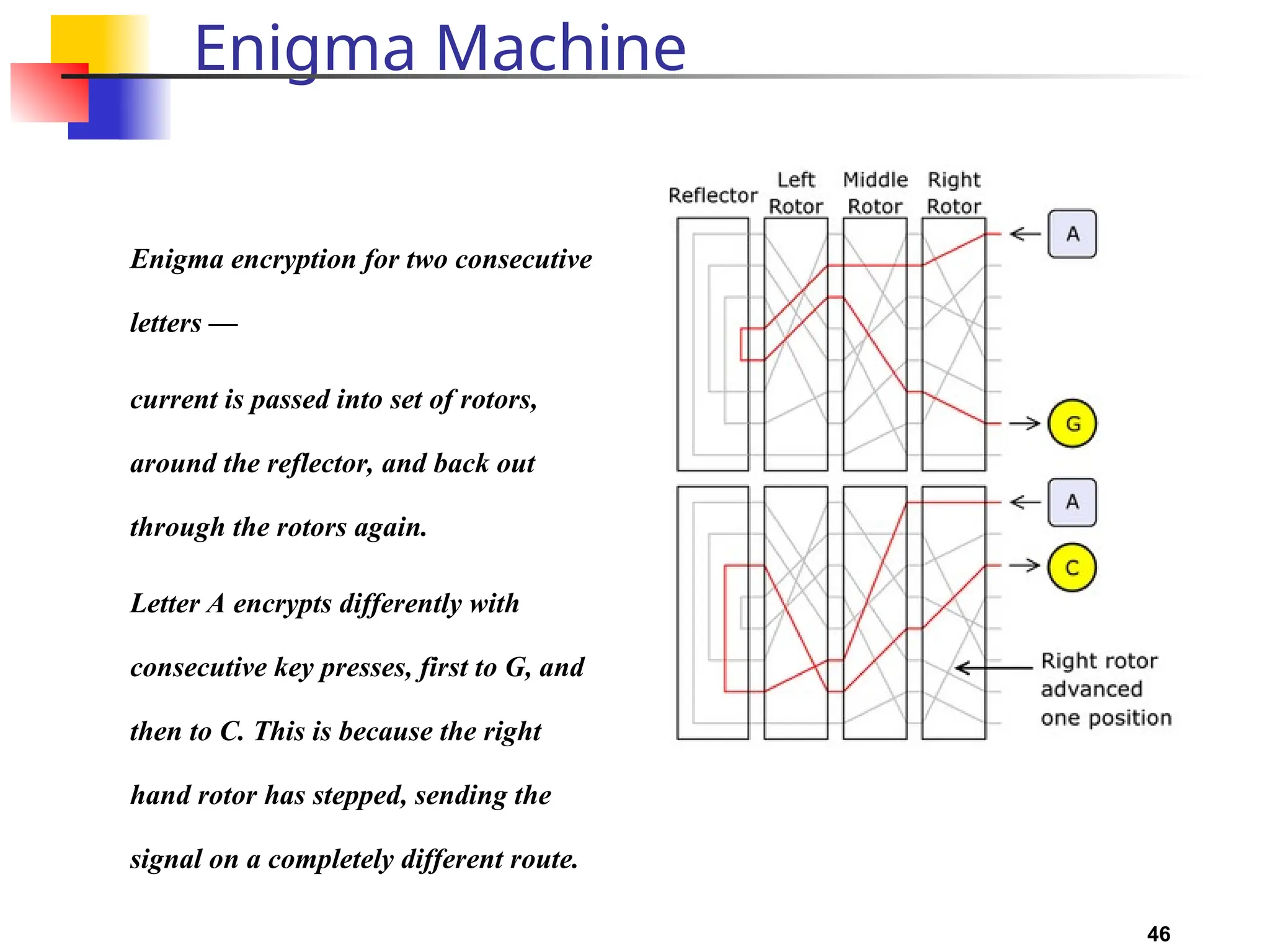
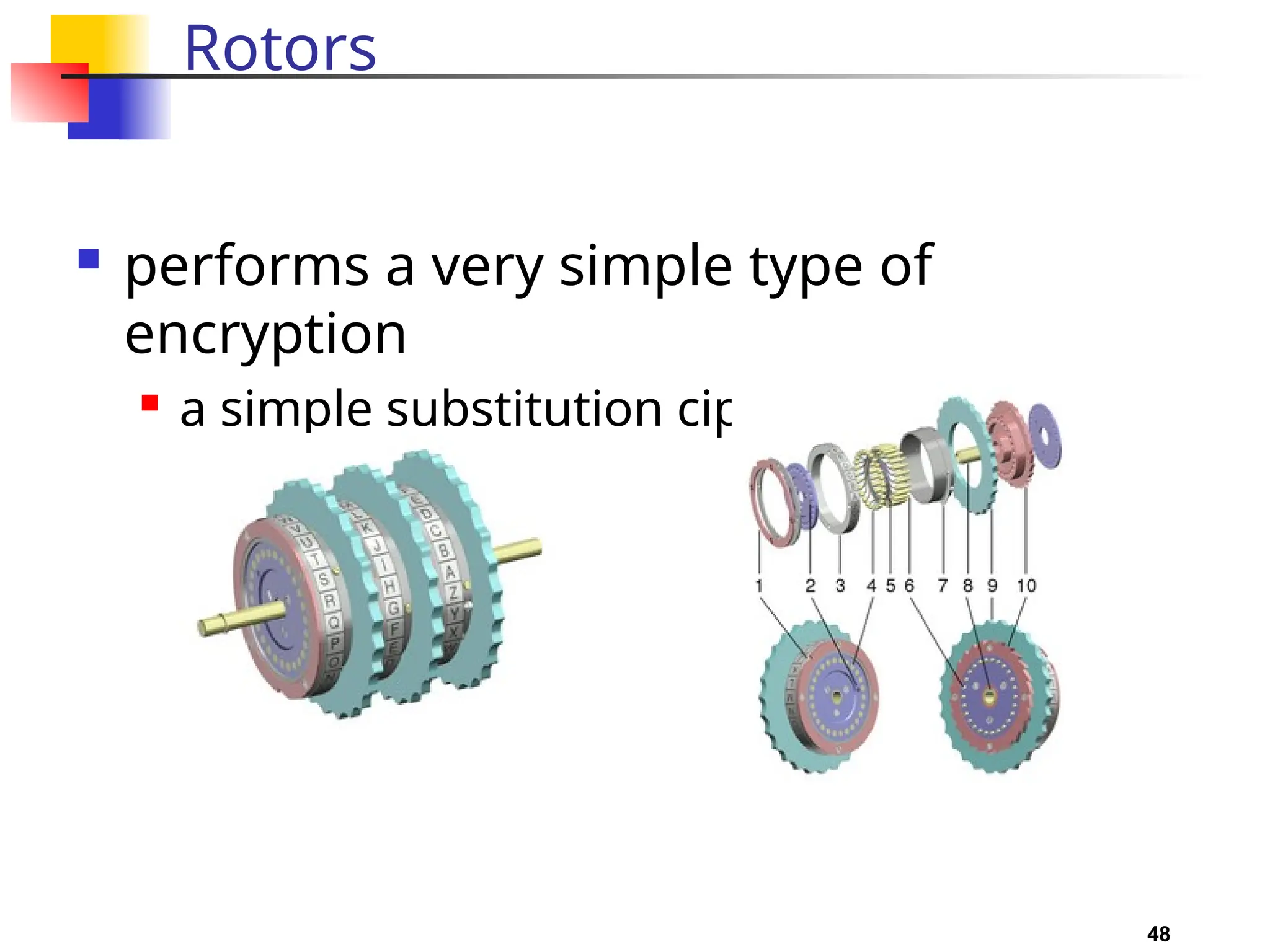
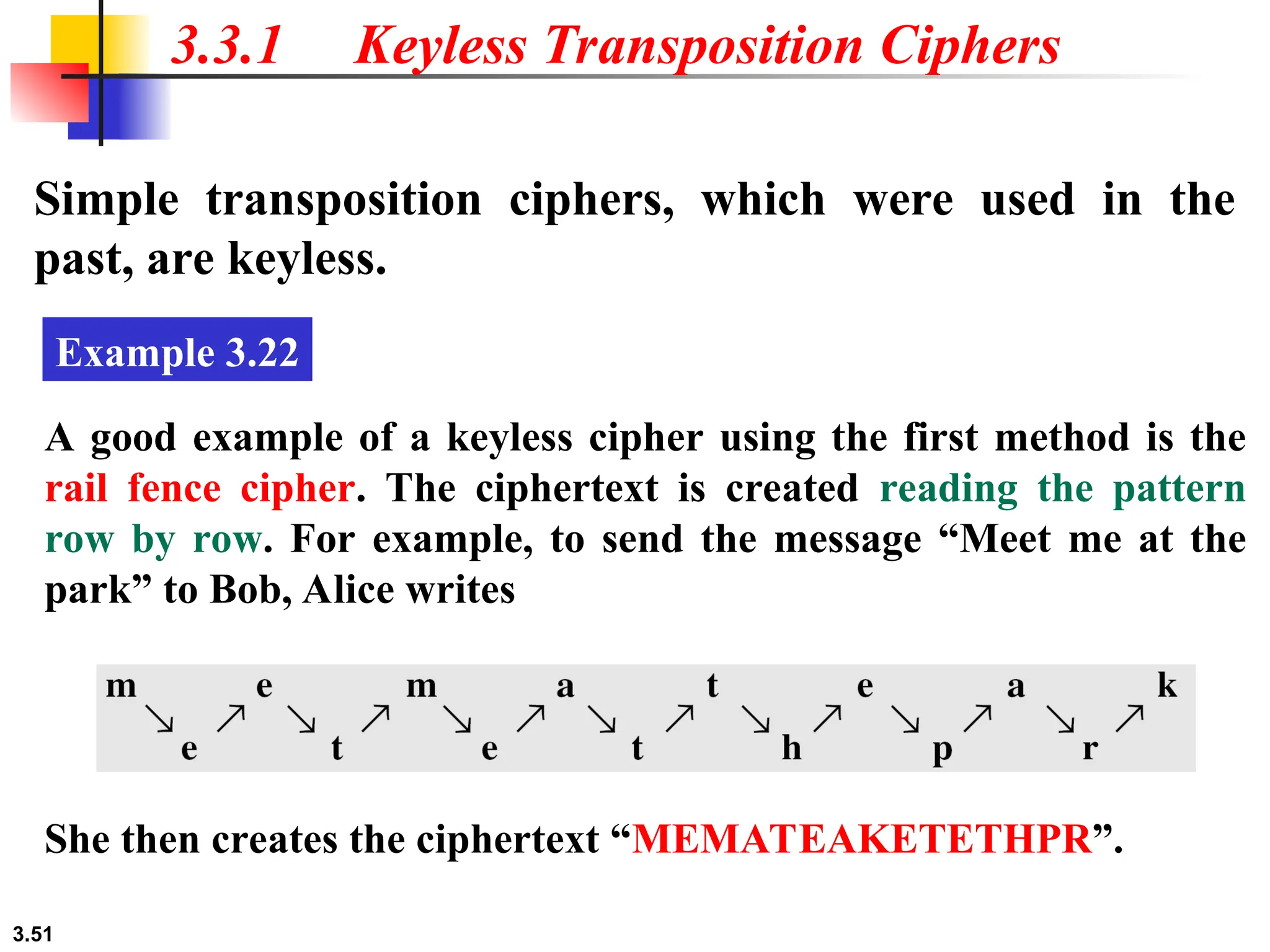
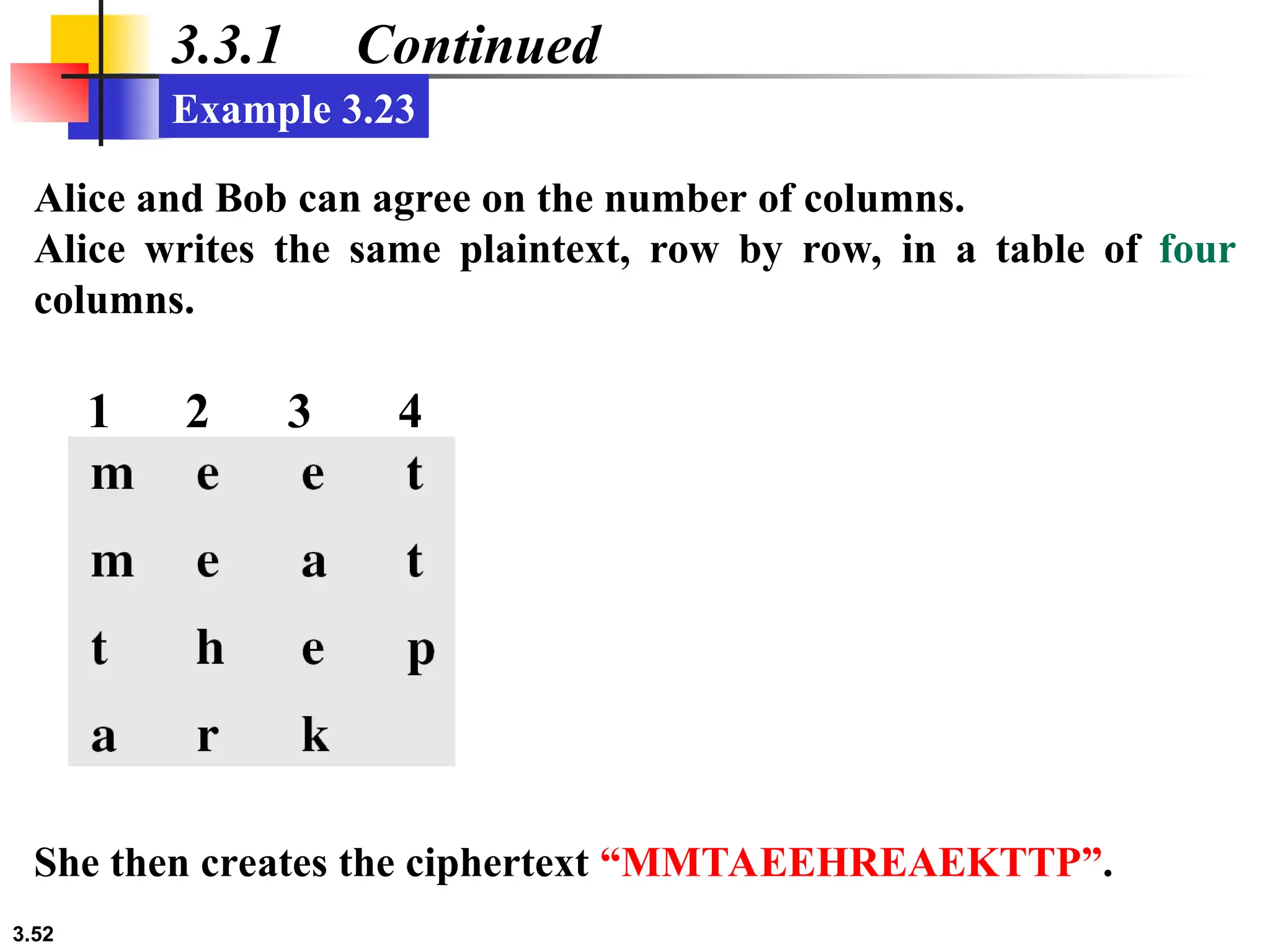
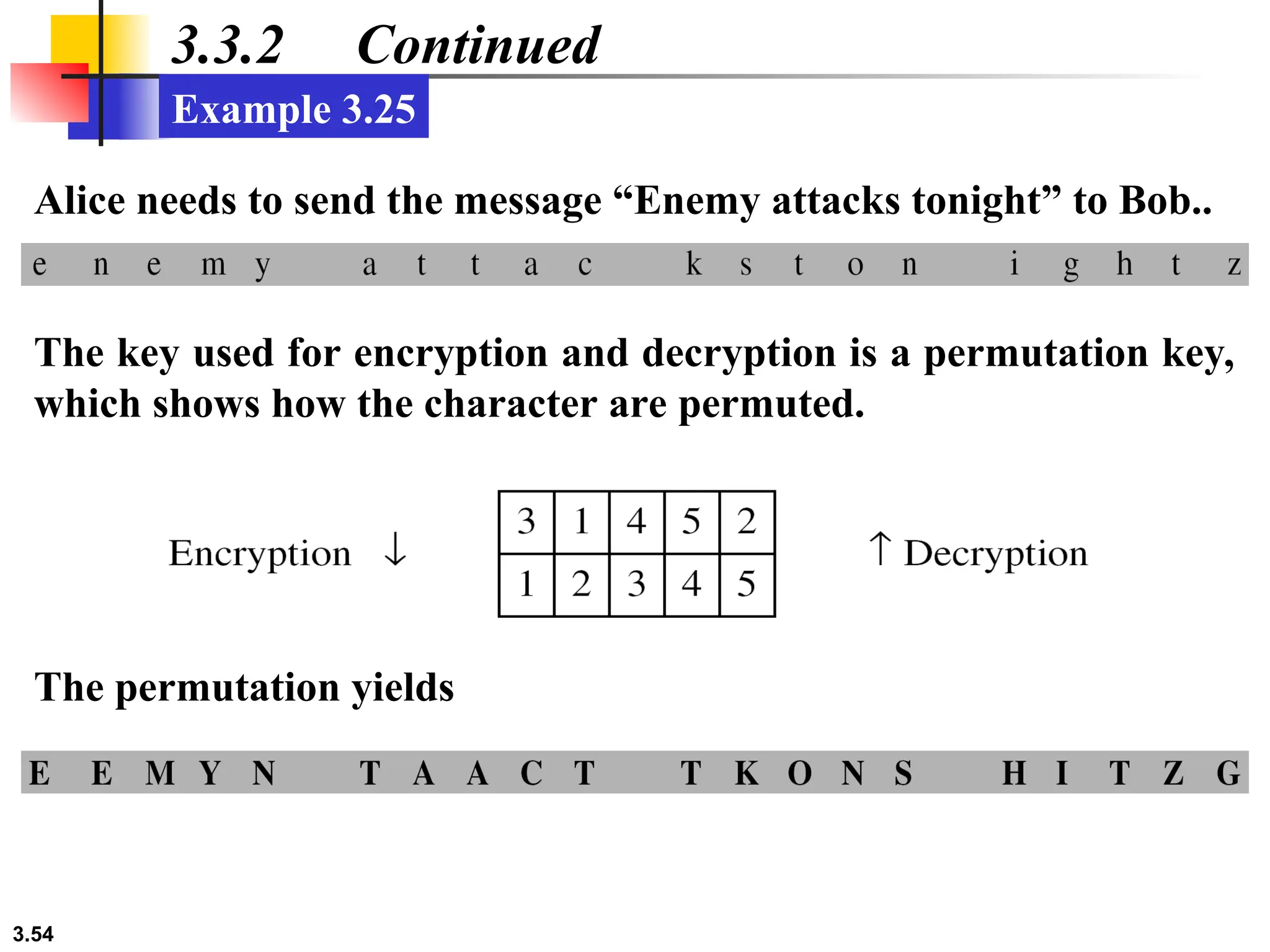
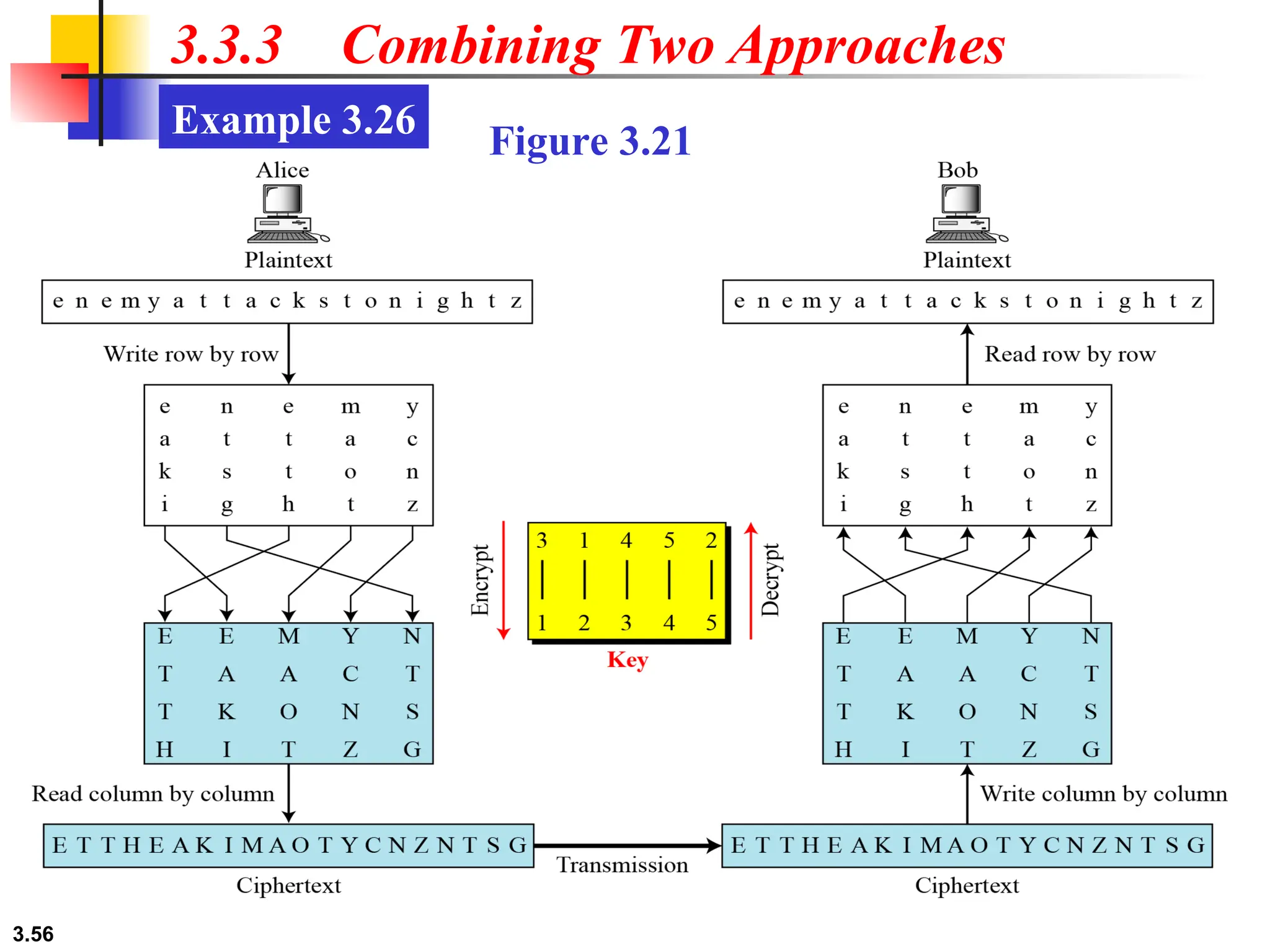
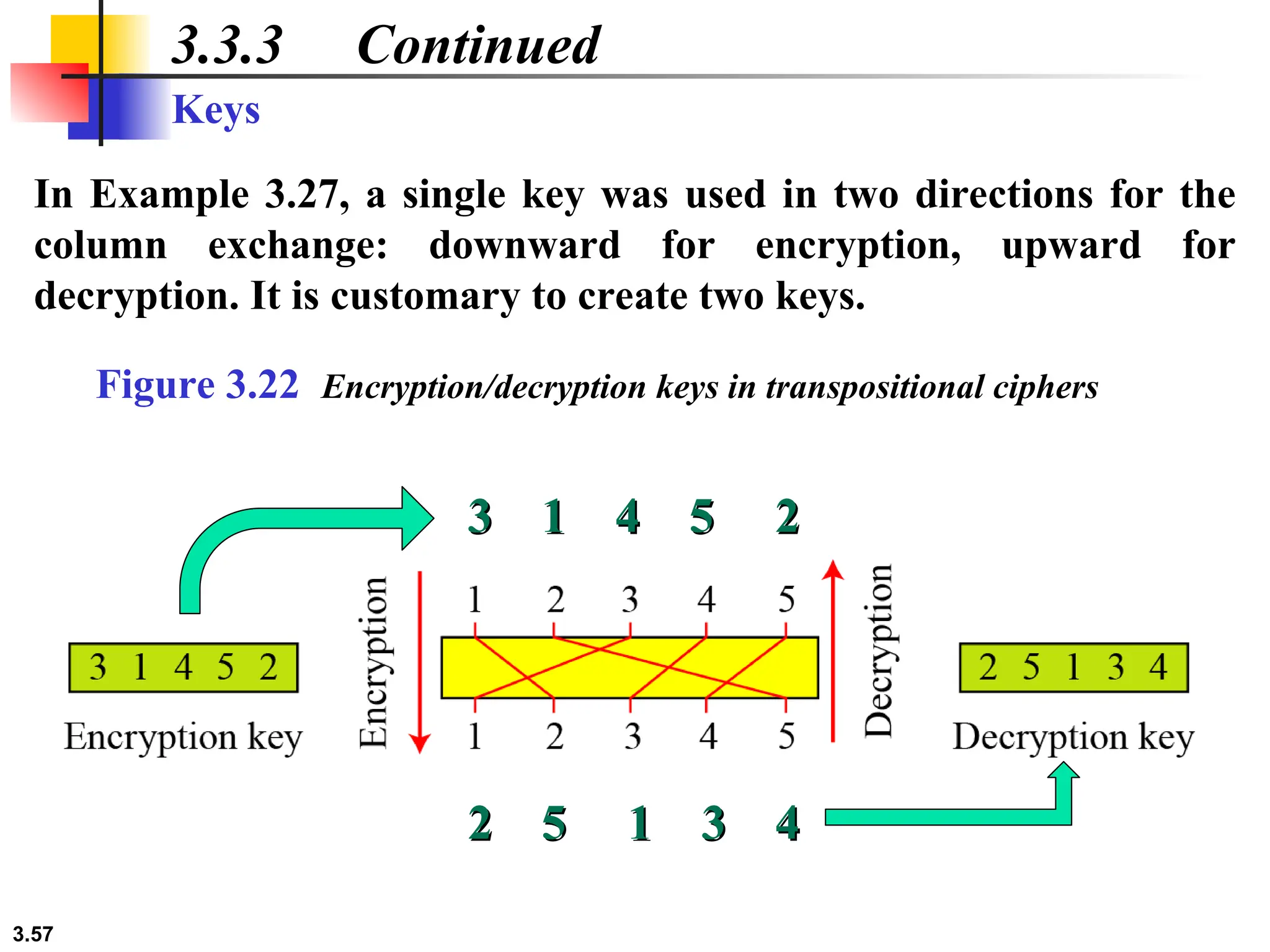
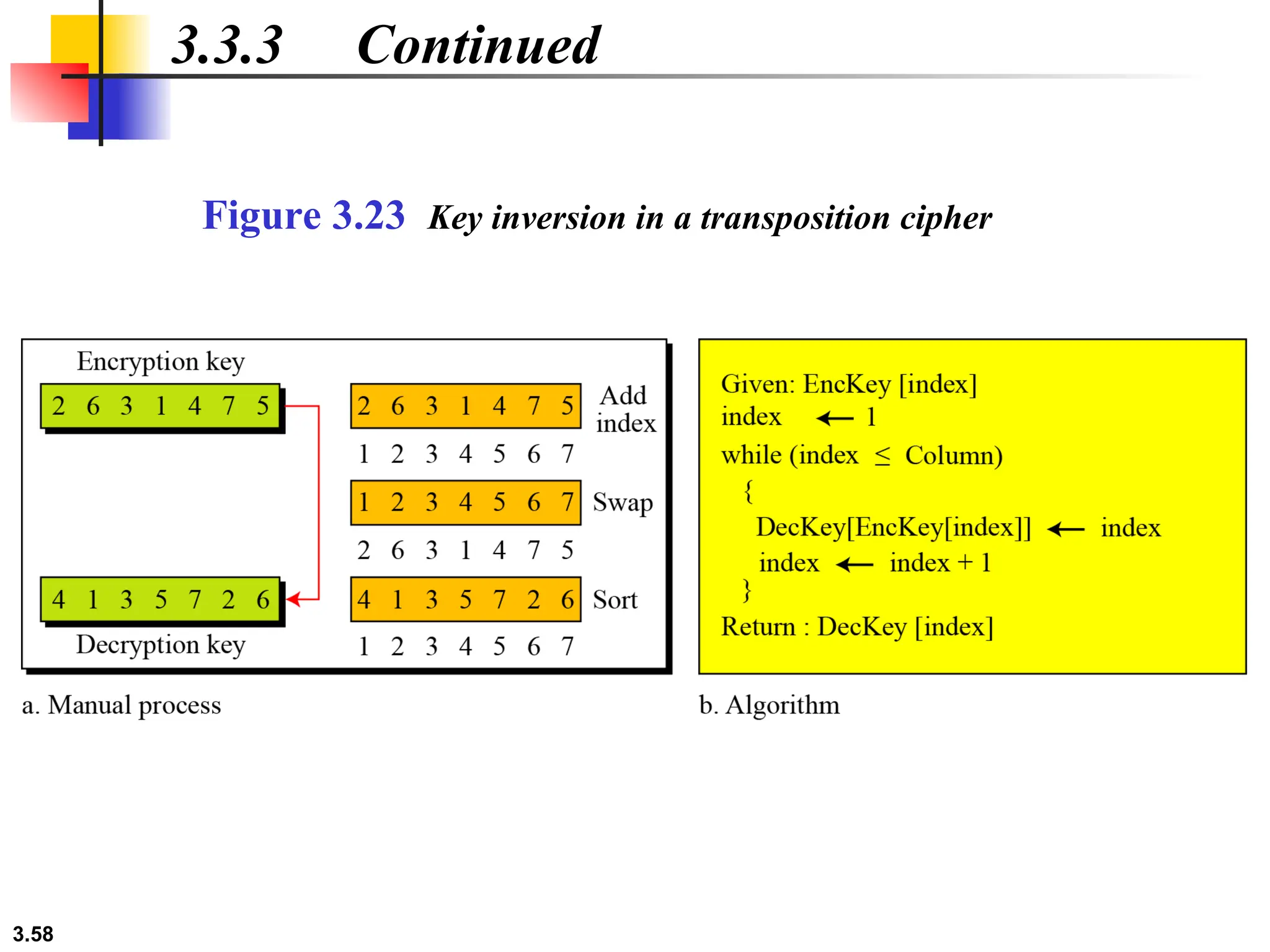
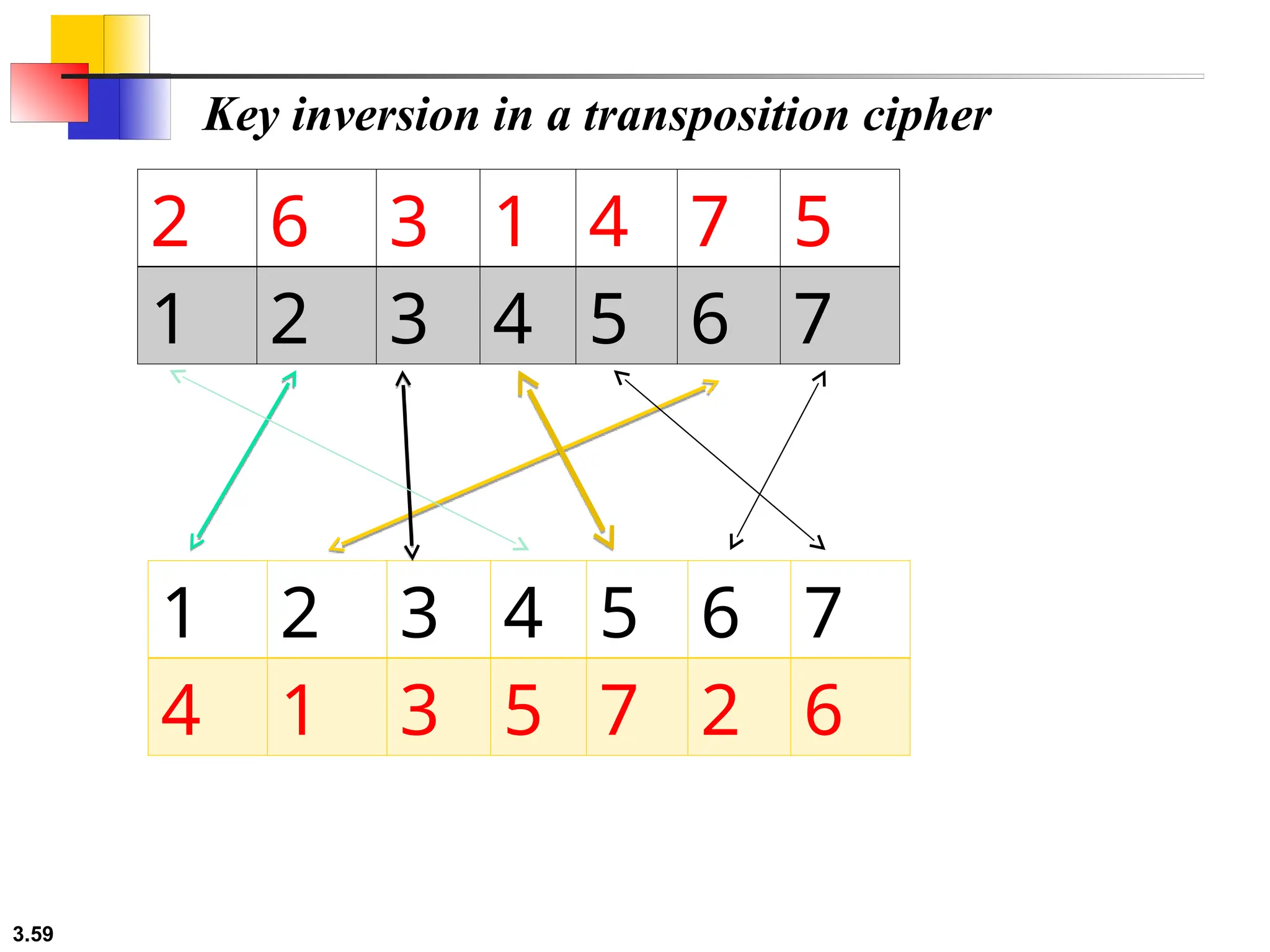
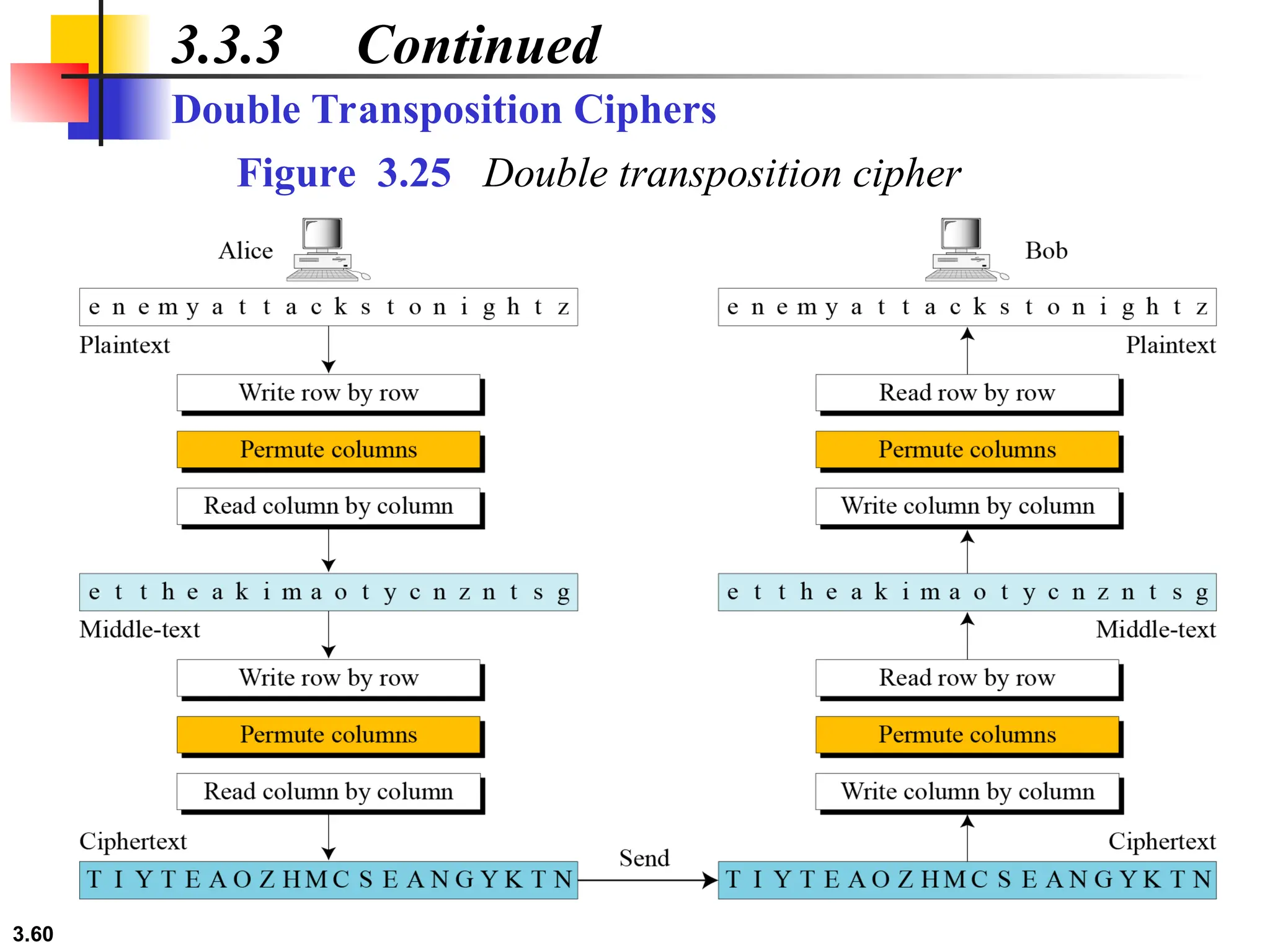
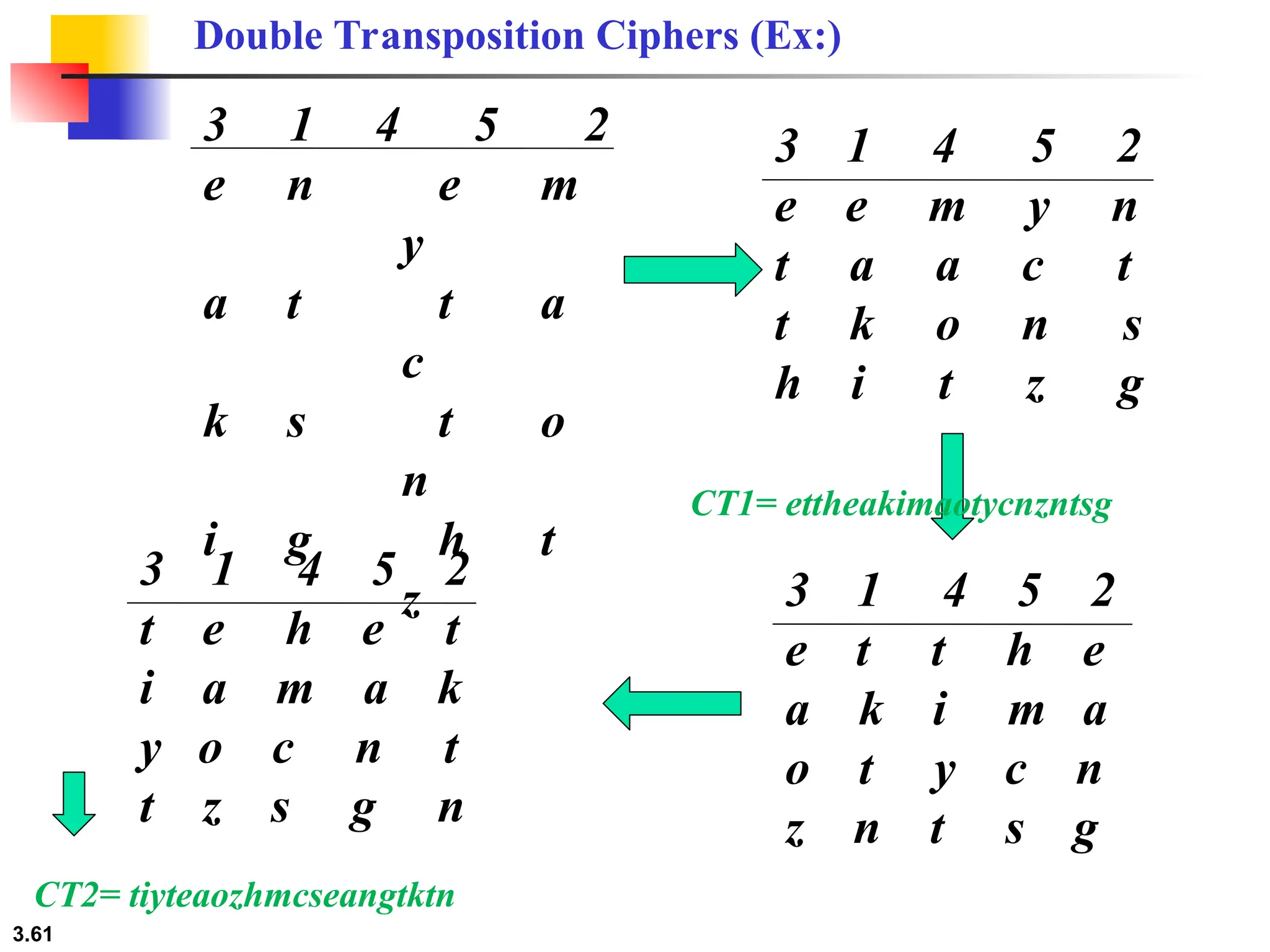
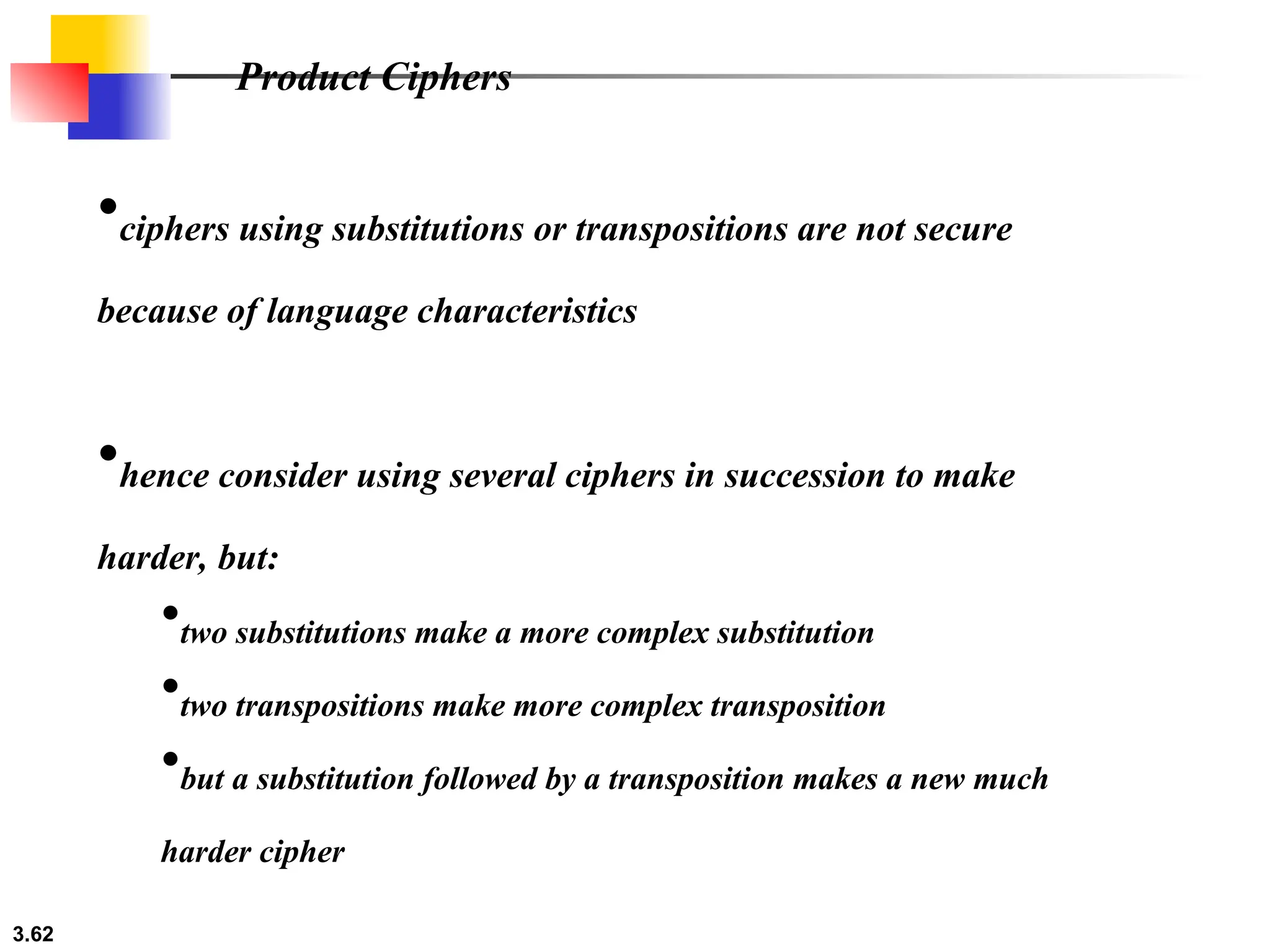
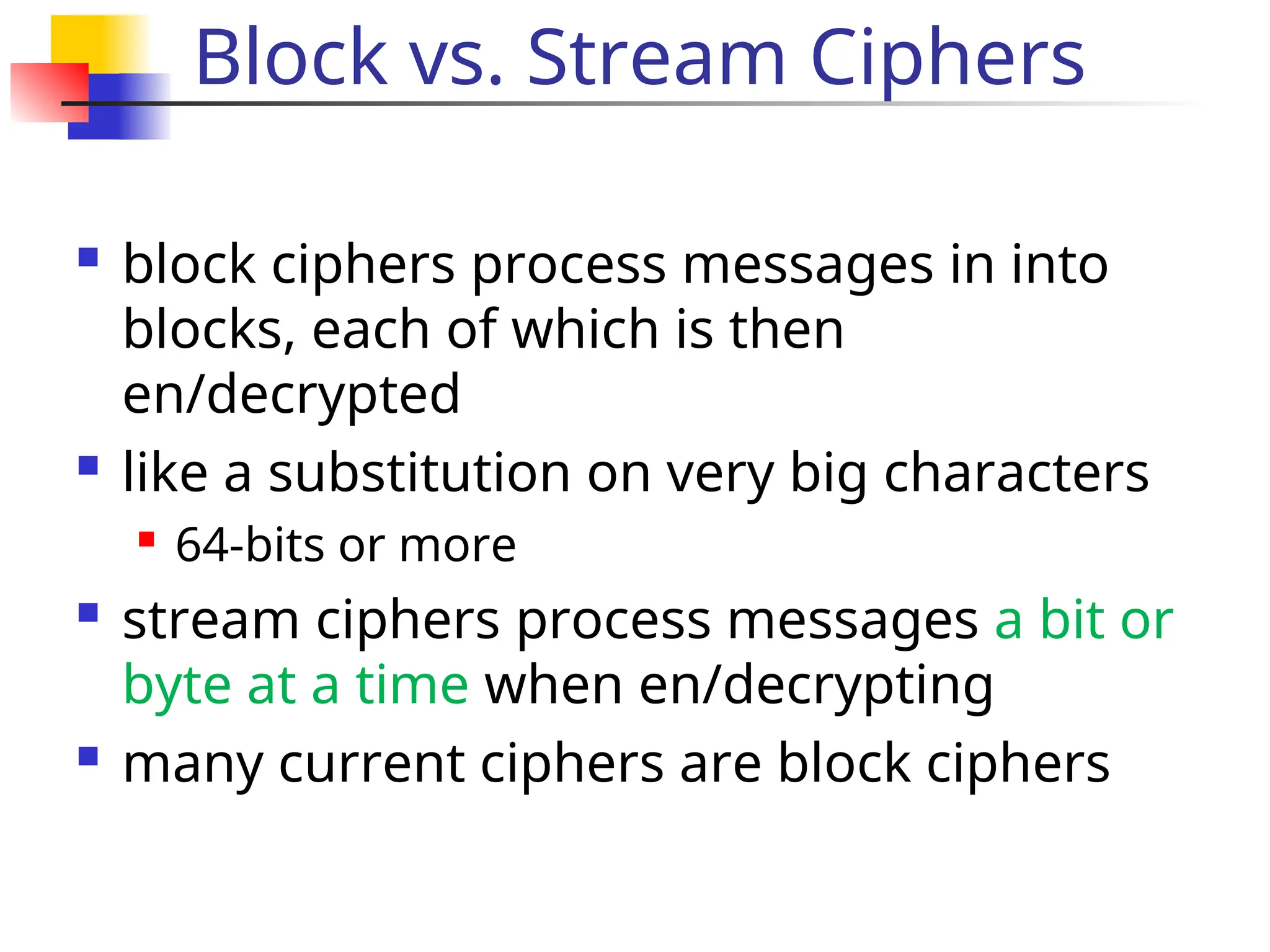
The document discusses traditional symmetric-key ciphers, highlighting key concepts such as substitution and transposition ciphers, as well as various types of cryptanalysis used to break these ciphers. It explains the components of symmetric-key systems, including the roles of plaintext, ciphertext, encryption, and decryption algorithms. Additionally, it covers specific ciphers like the additive and polyalphabetic ciphers, alongside historical examples such as the Enigma machine.