This document summarizes the evolution of cellular networks from 1G to 4G and discusses key concepts in mobile IP. It describes:
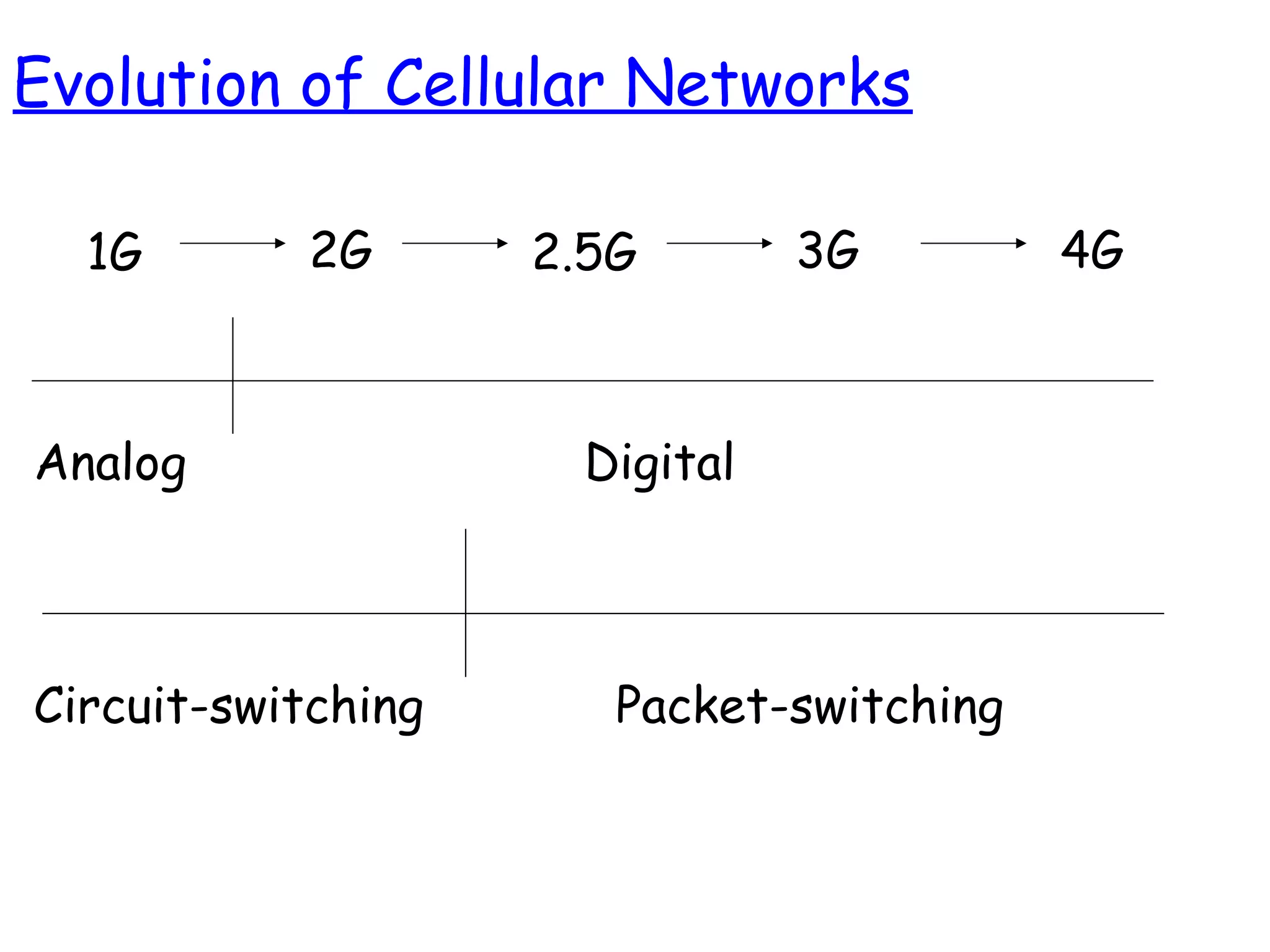
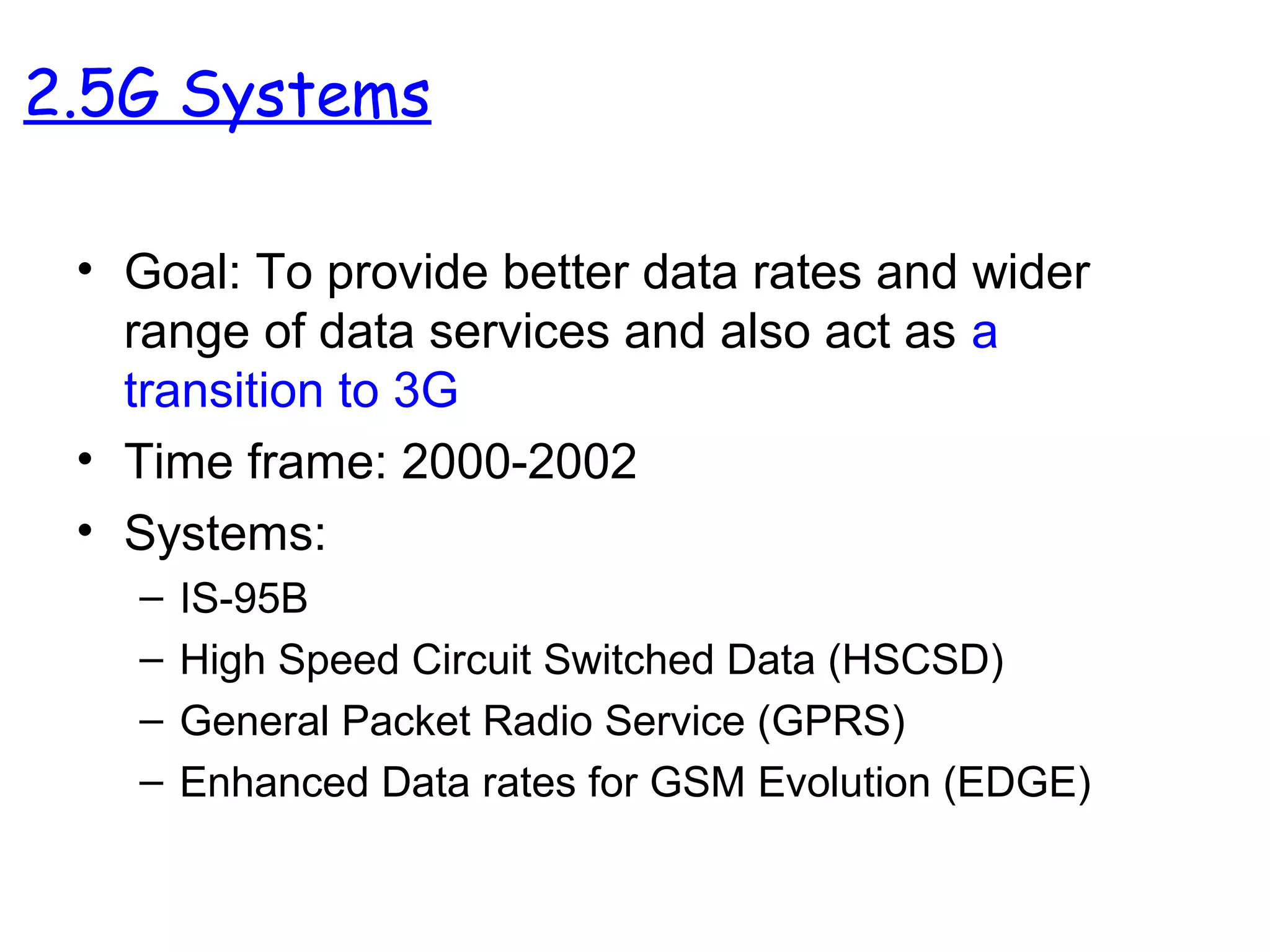
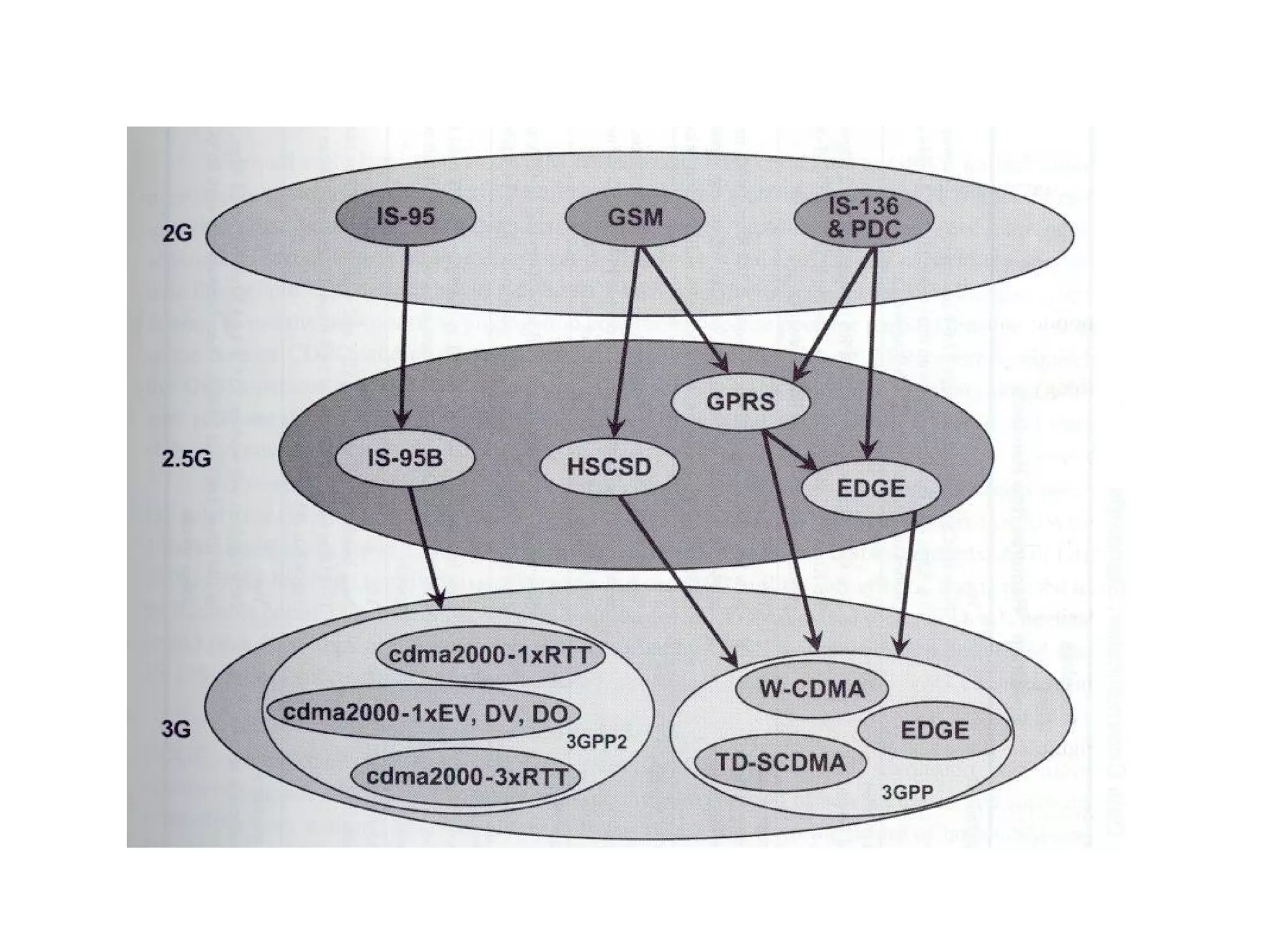
- The progression of cellular network standards from analog 1G networks to digital 2G/3G networks with improved voice quality and data services.
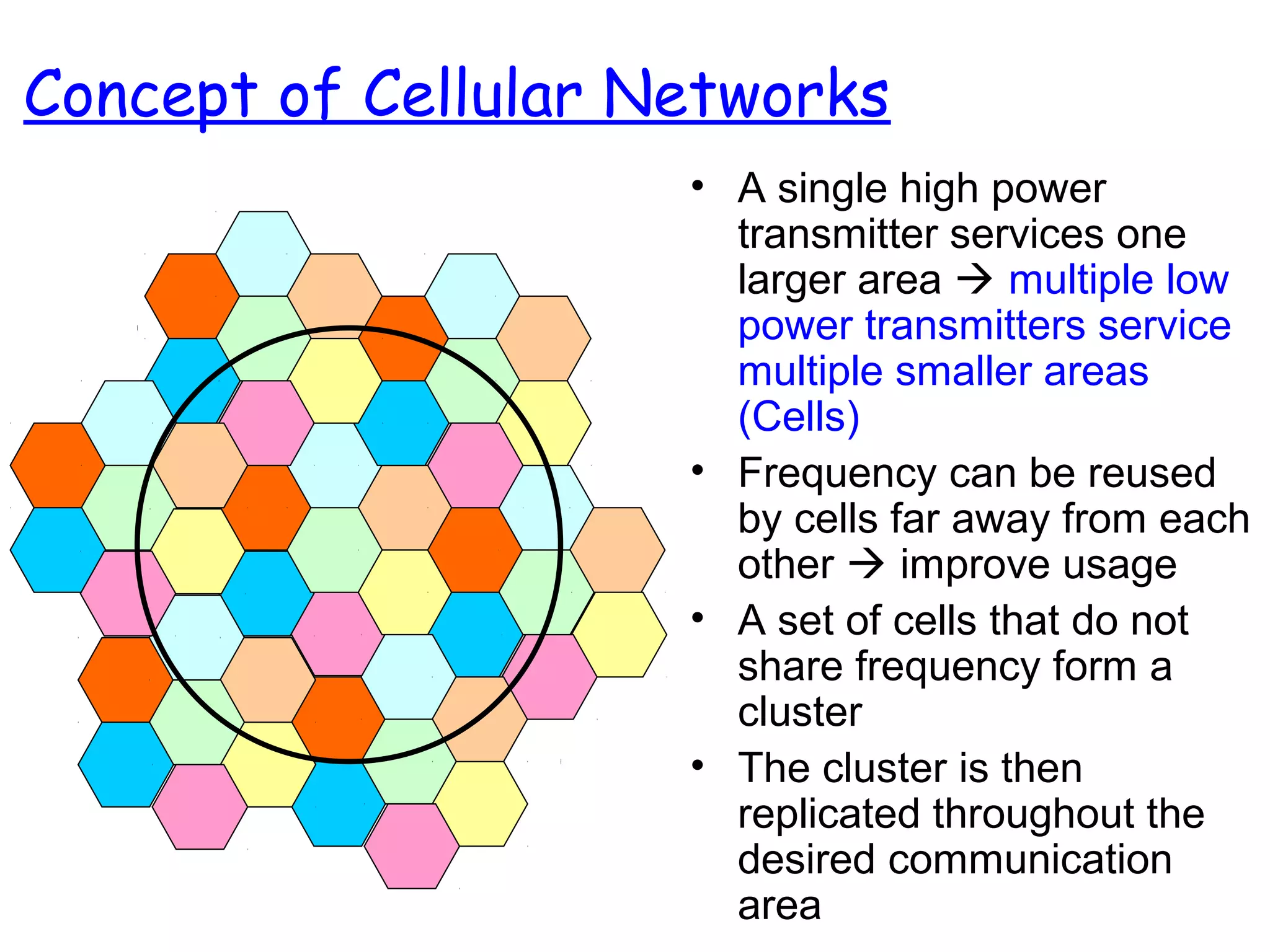
- The basic concept of cellular networks using low-power transmitters and frequency reuse to improve coverage and capacity compared to single high-power transmitters.
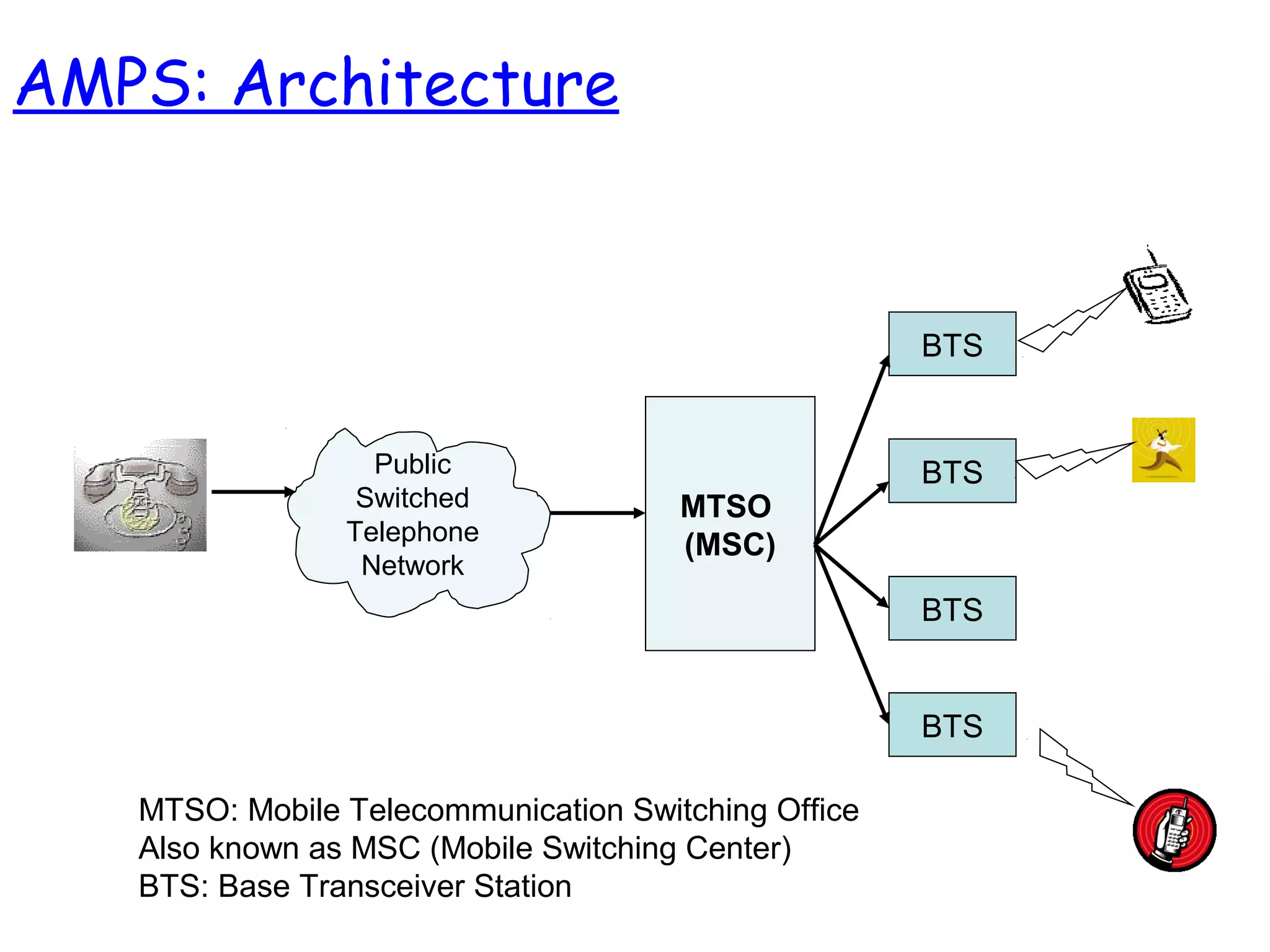
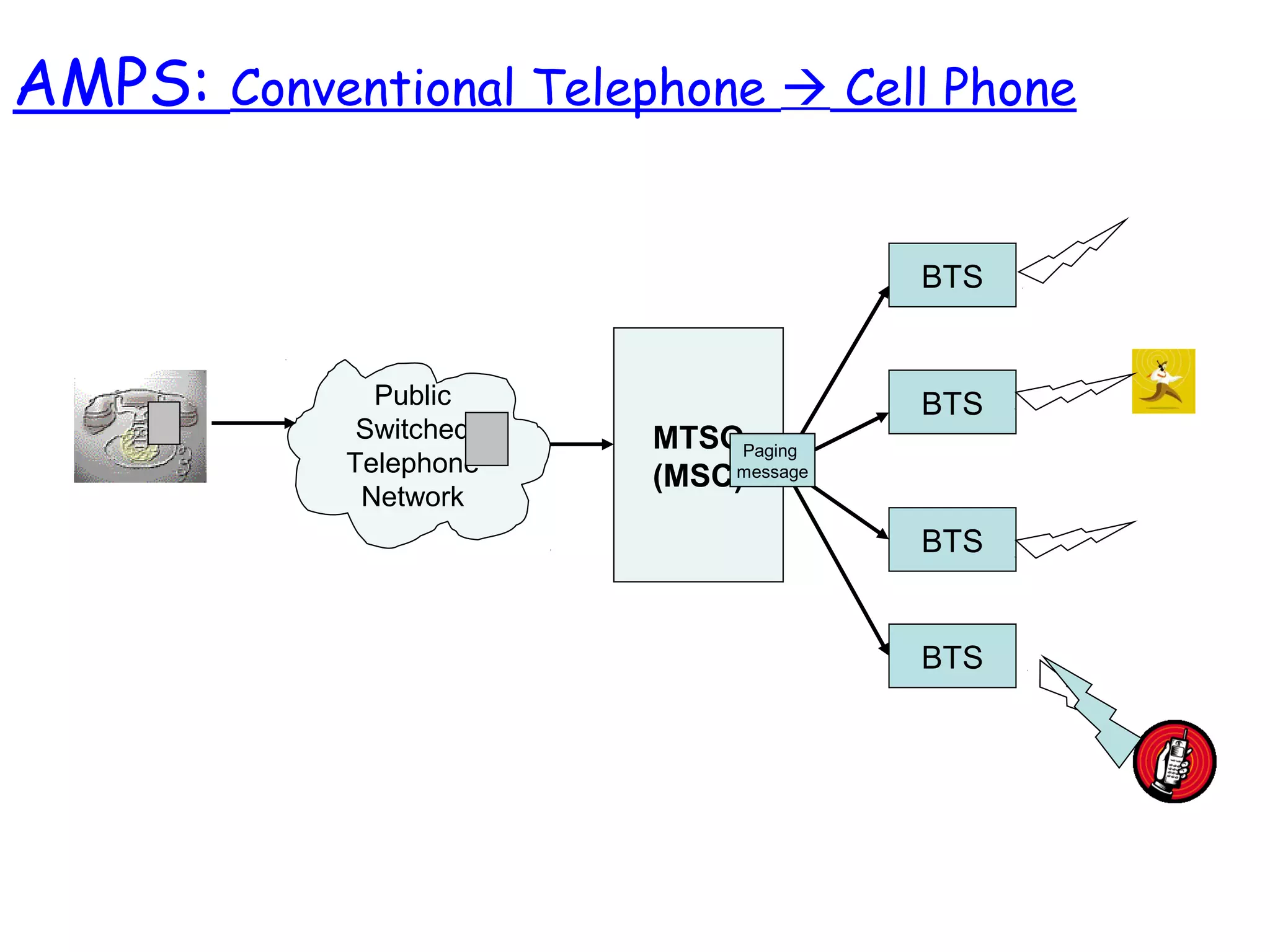
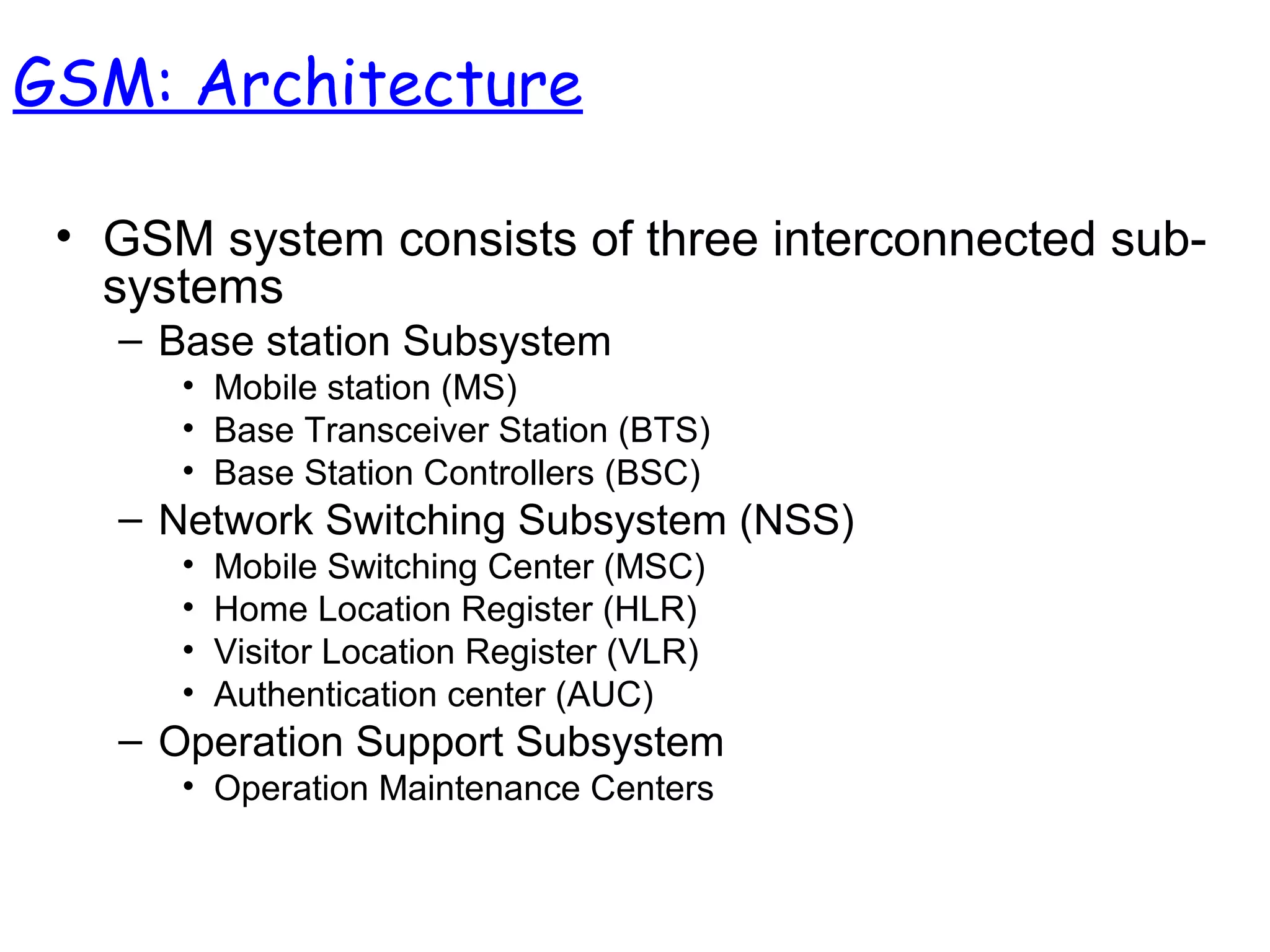
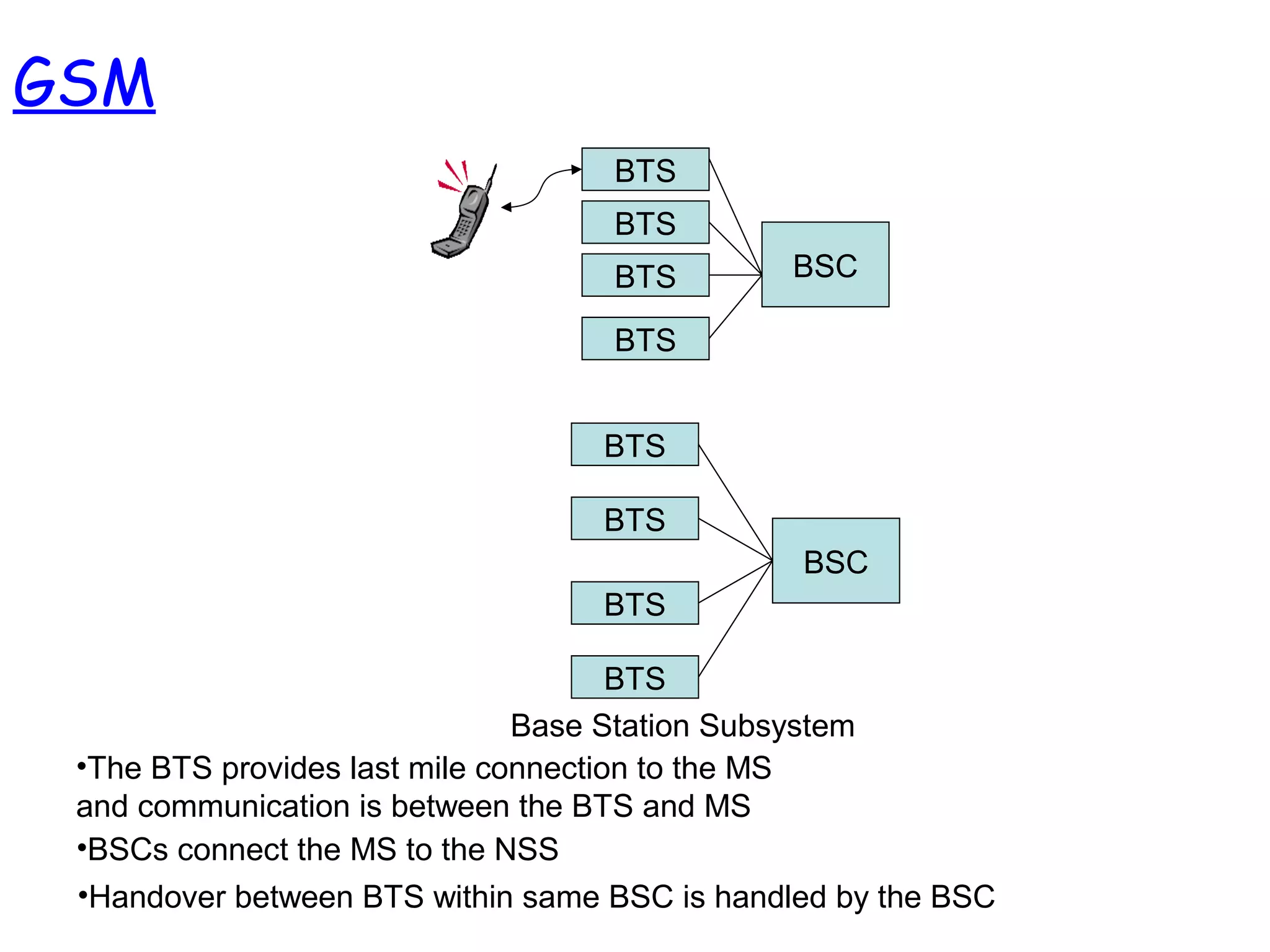
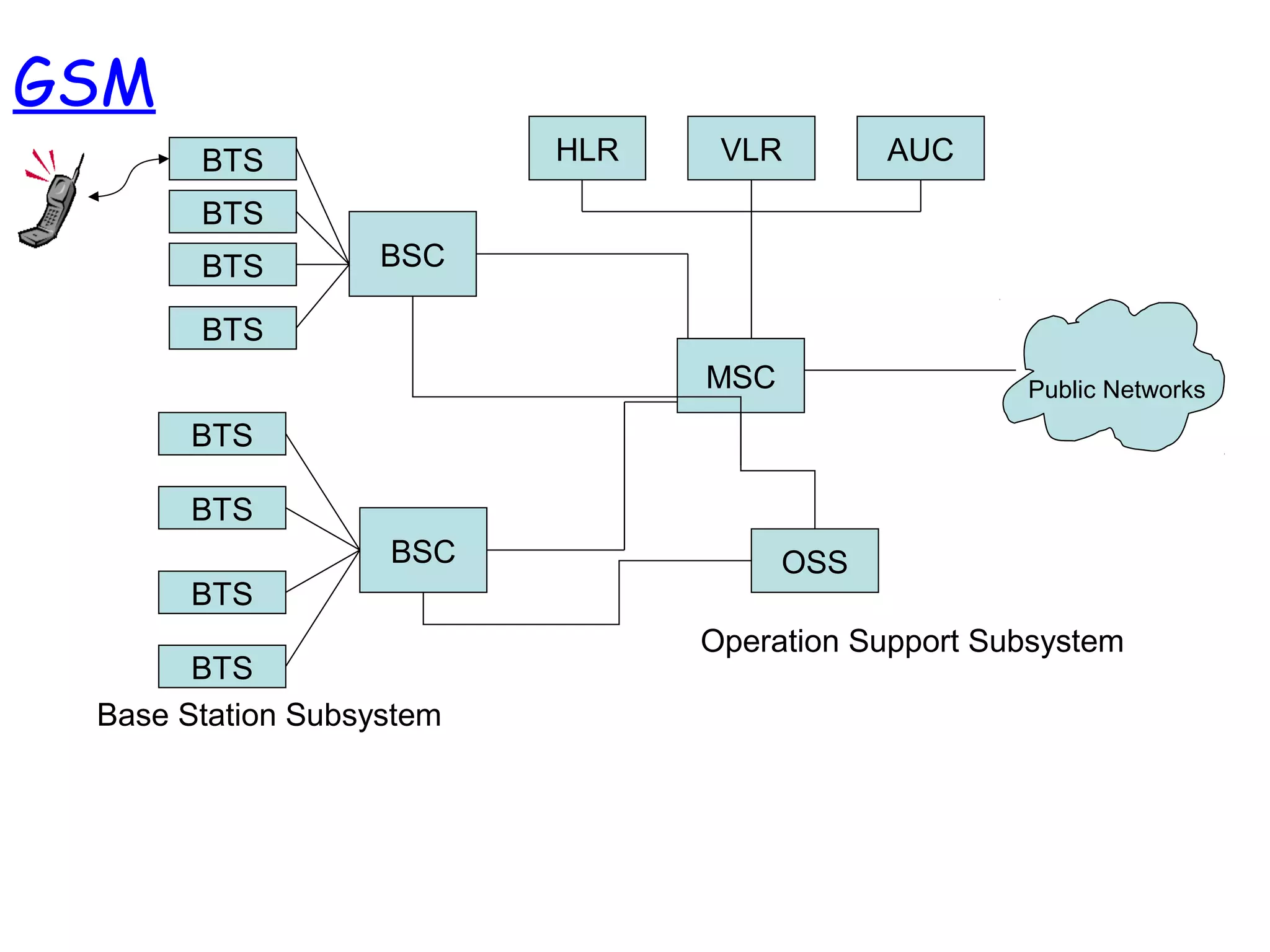
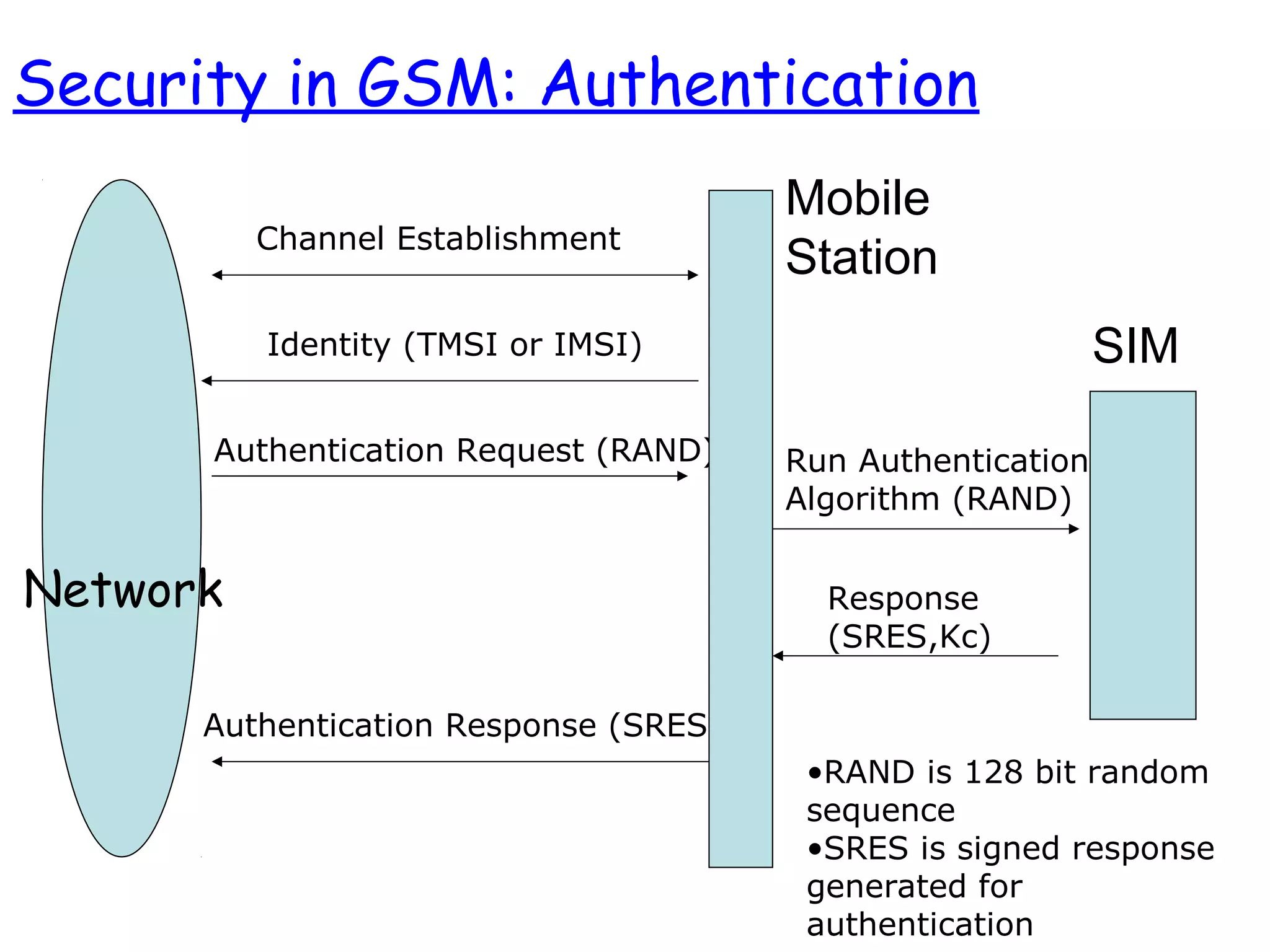
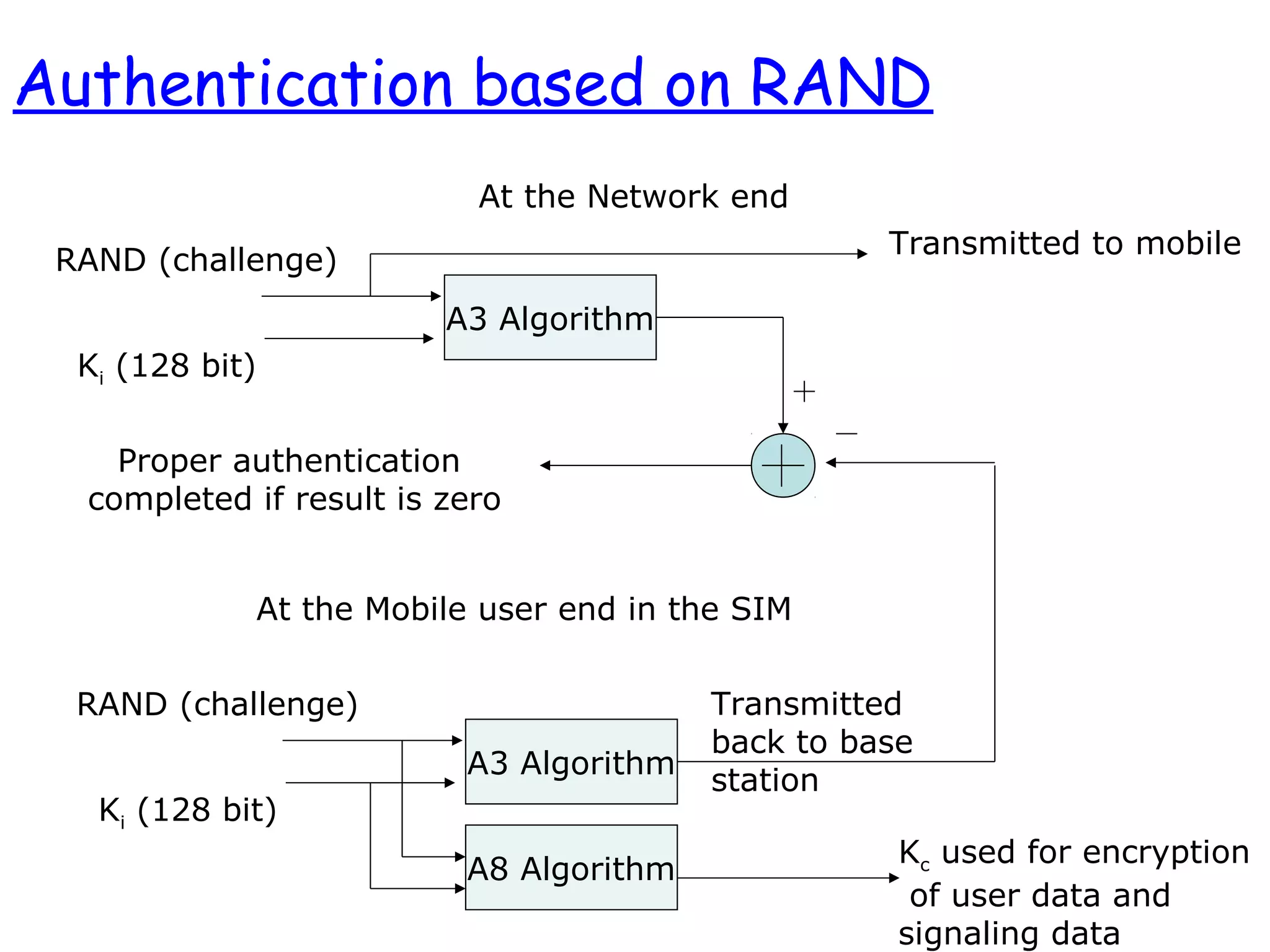
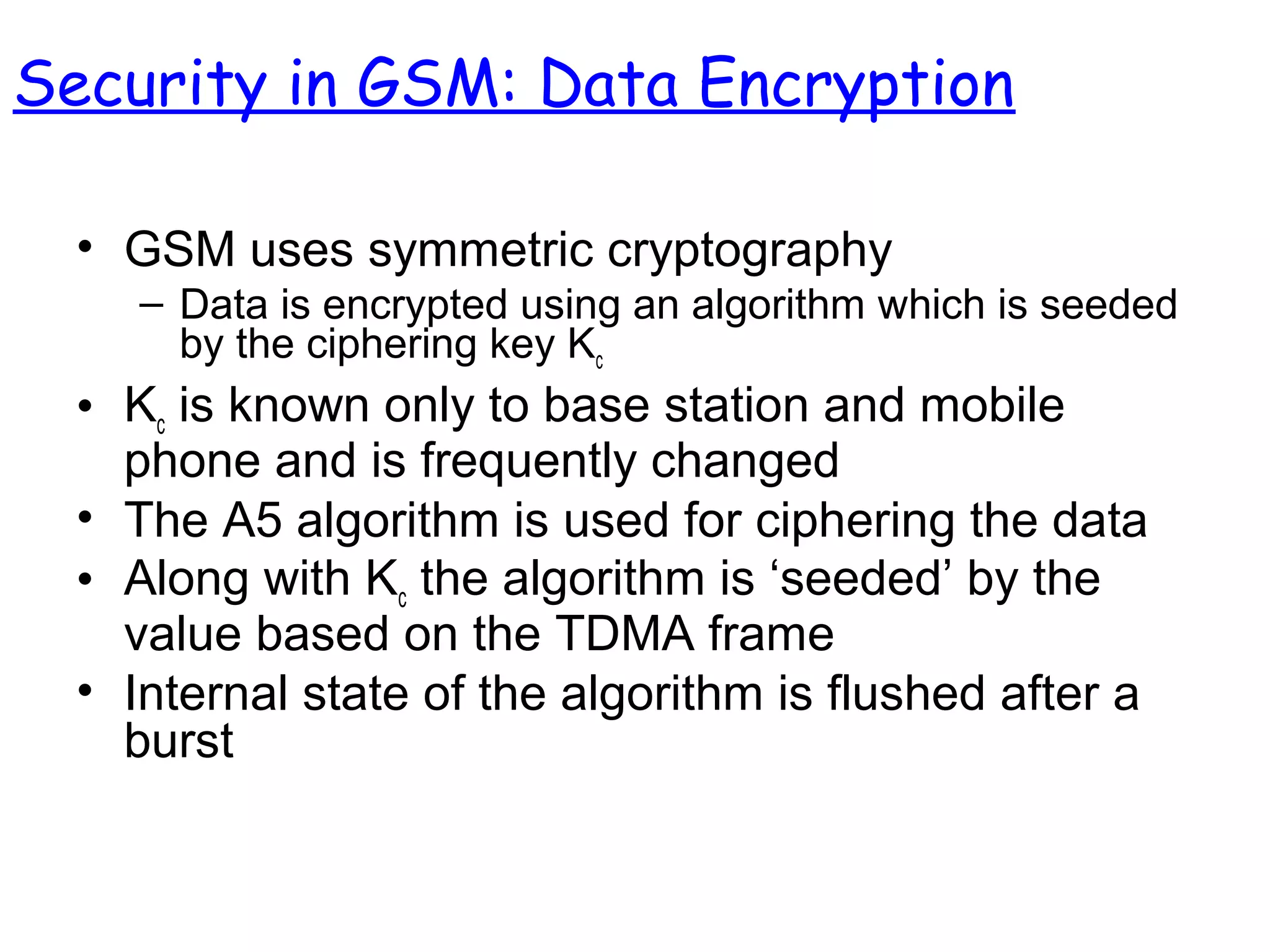
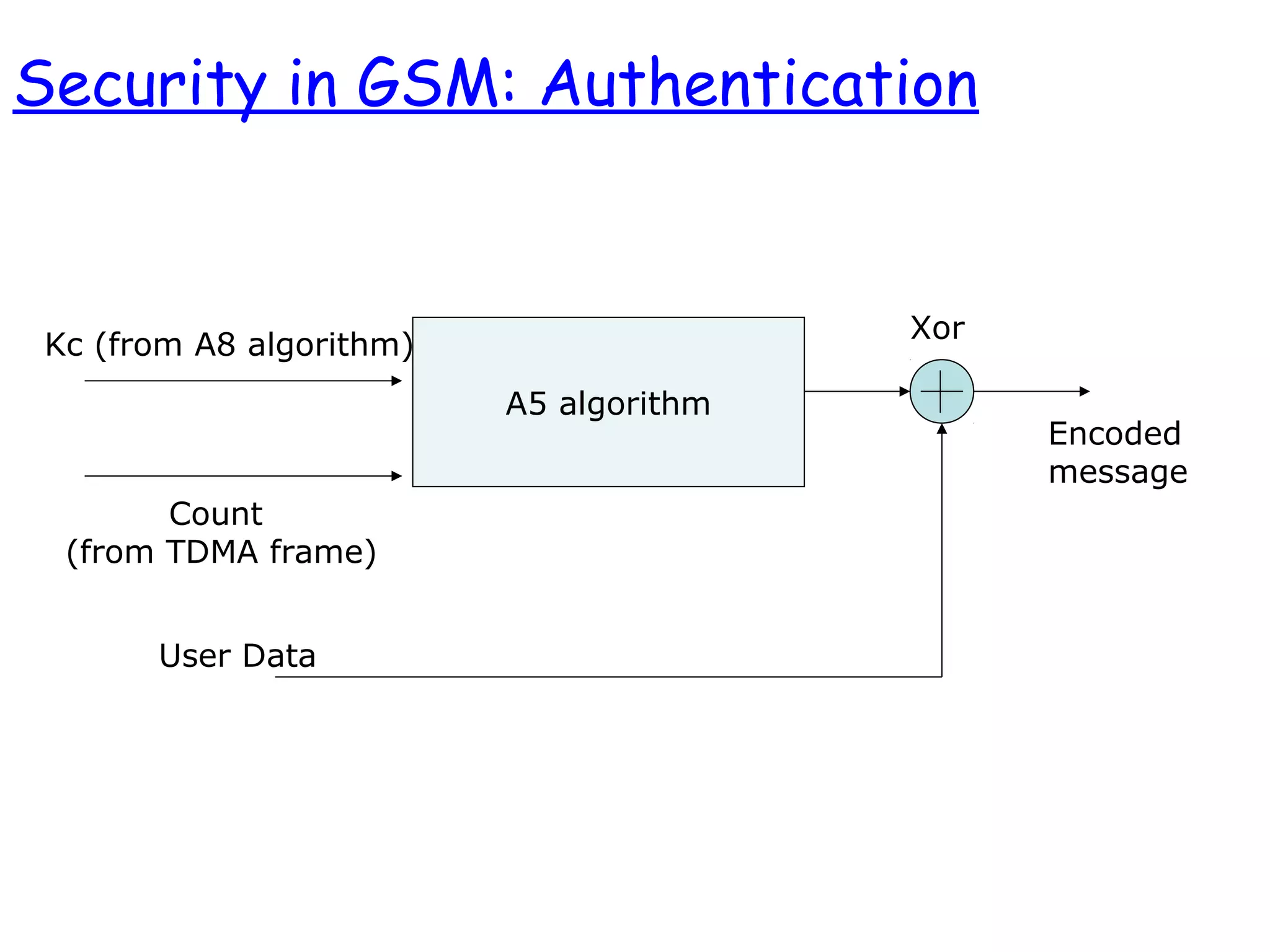
- The architecture and operation of the 1G AMPS network and 2G GSM network, including core network elements and authentication procedures in GSM.
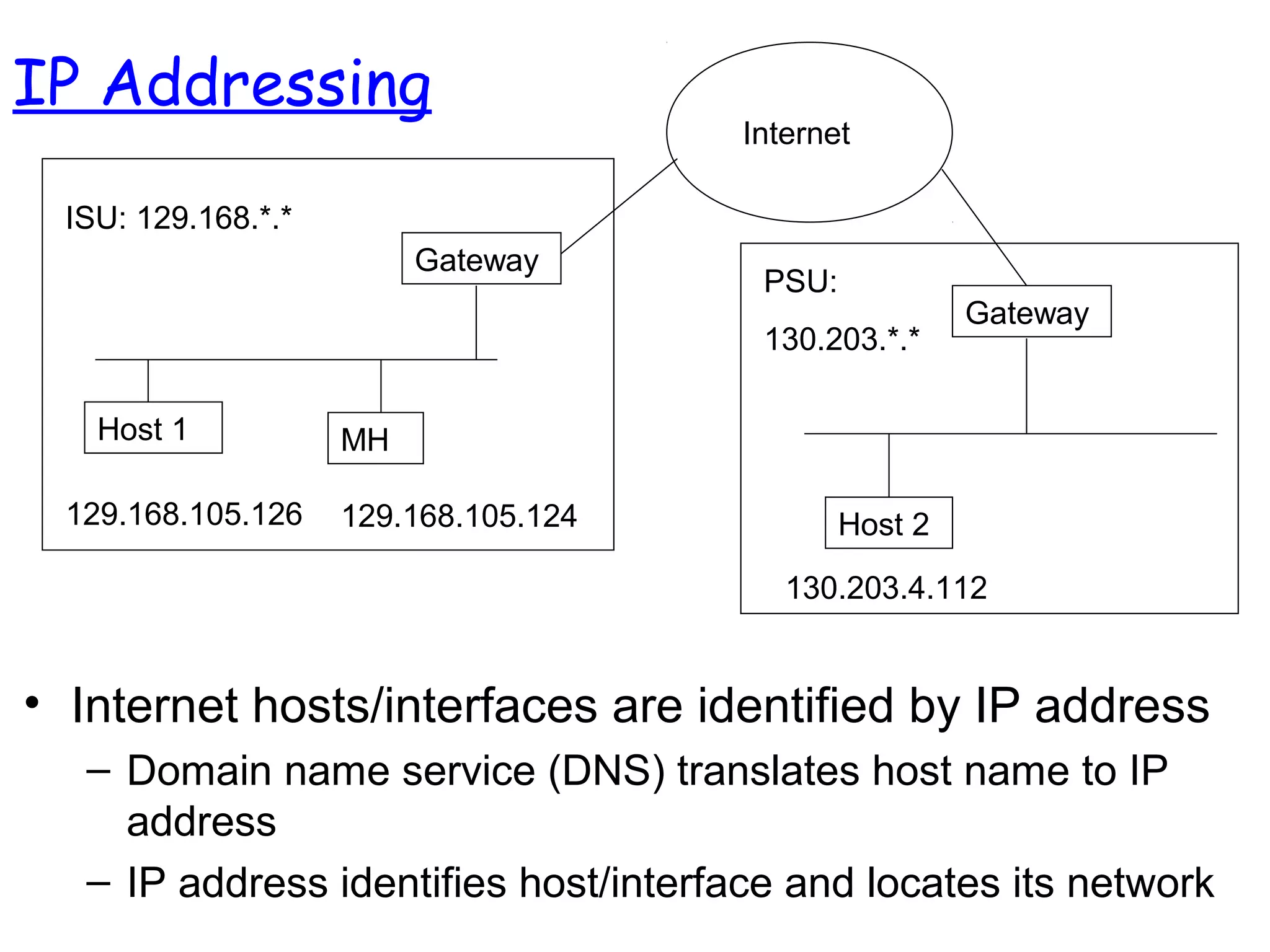
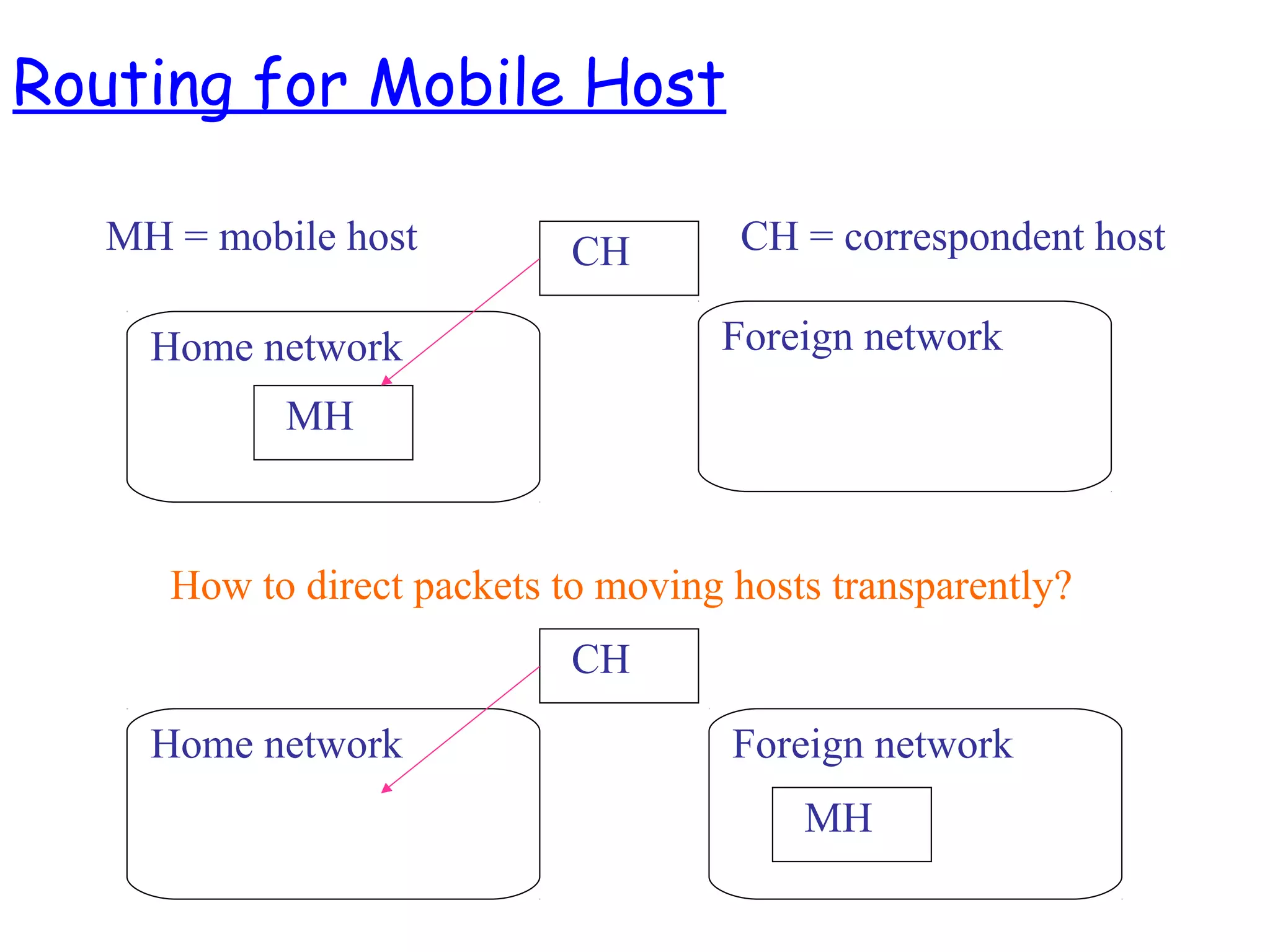
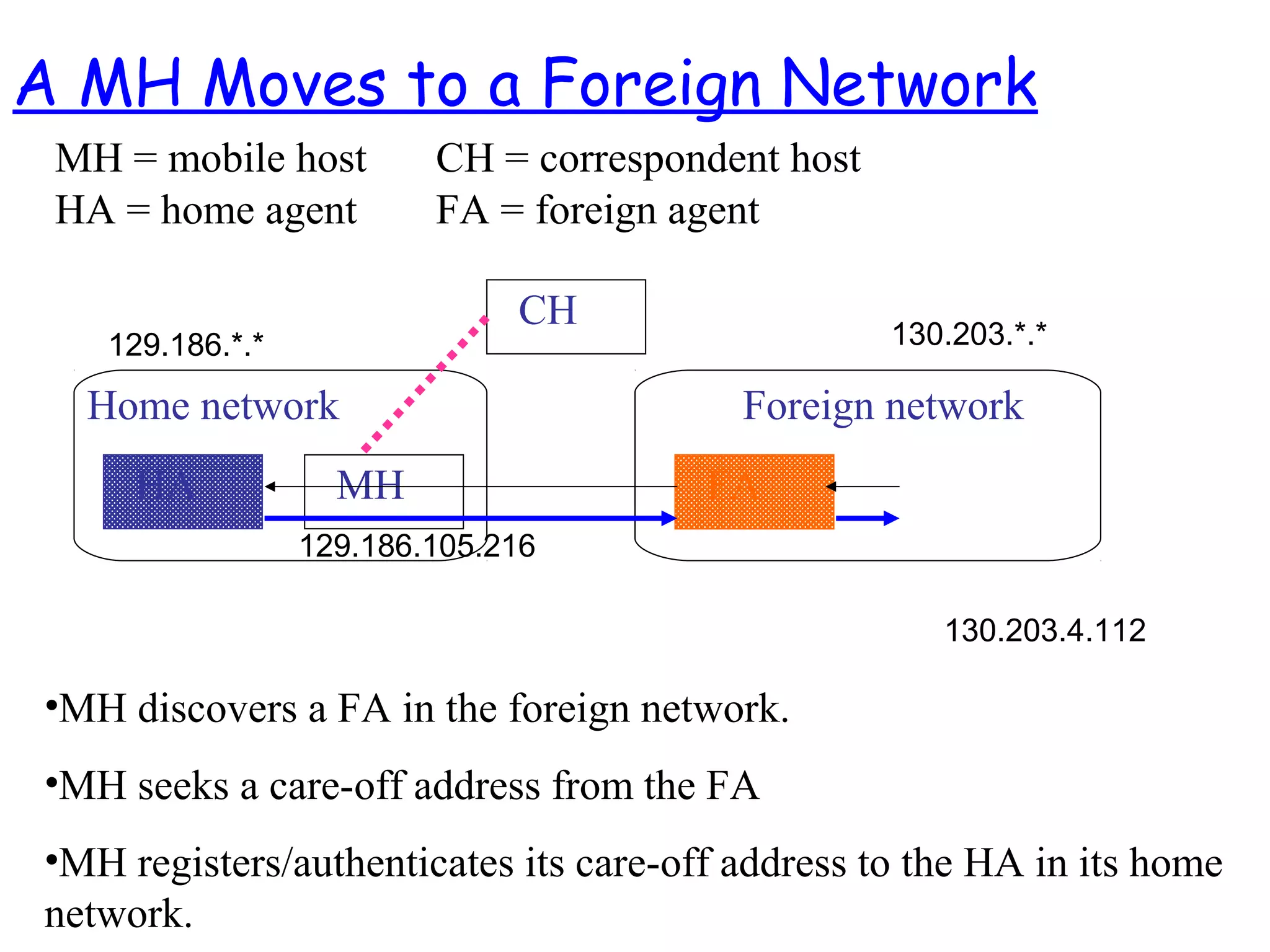
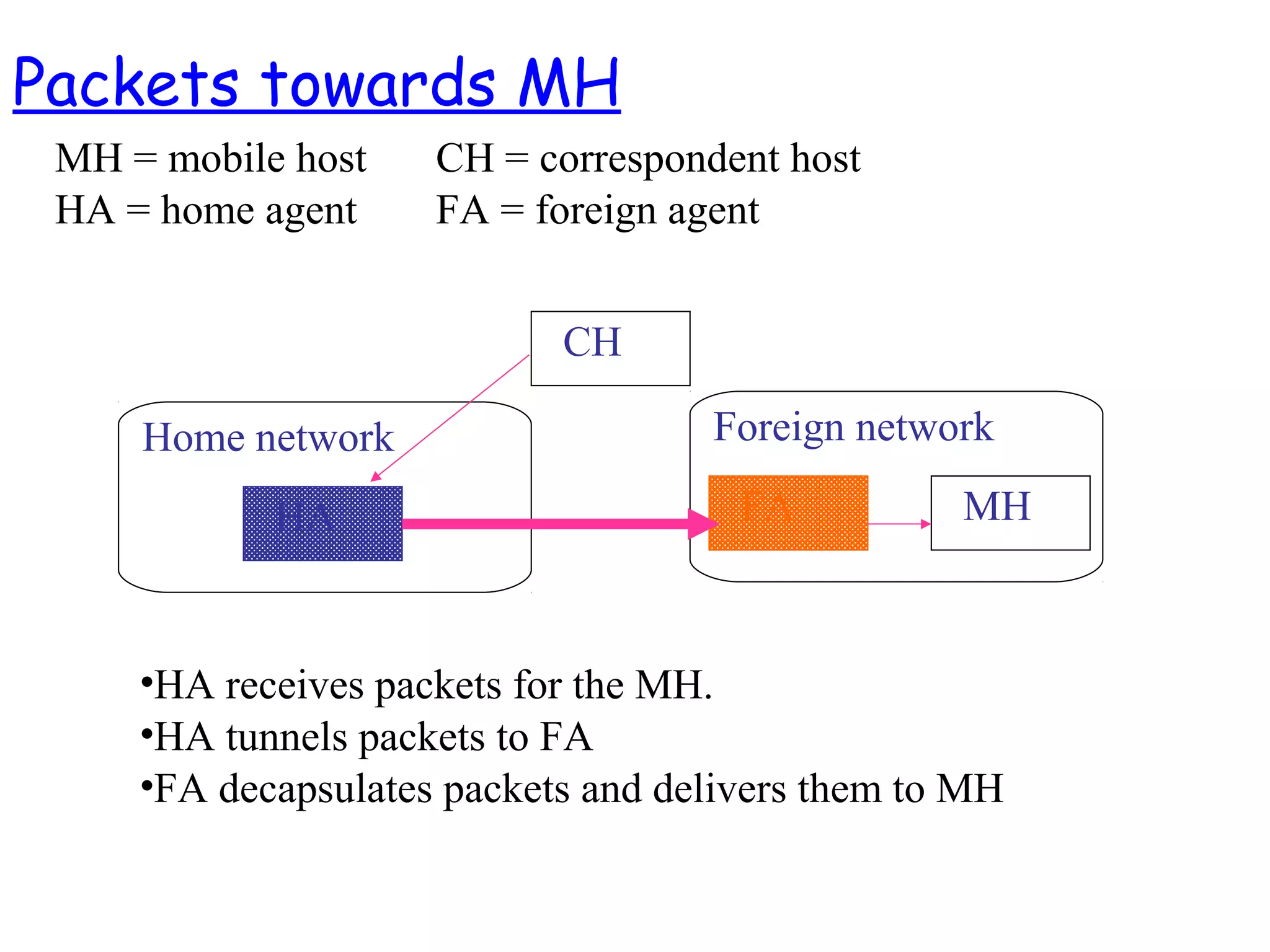
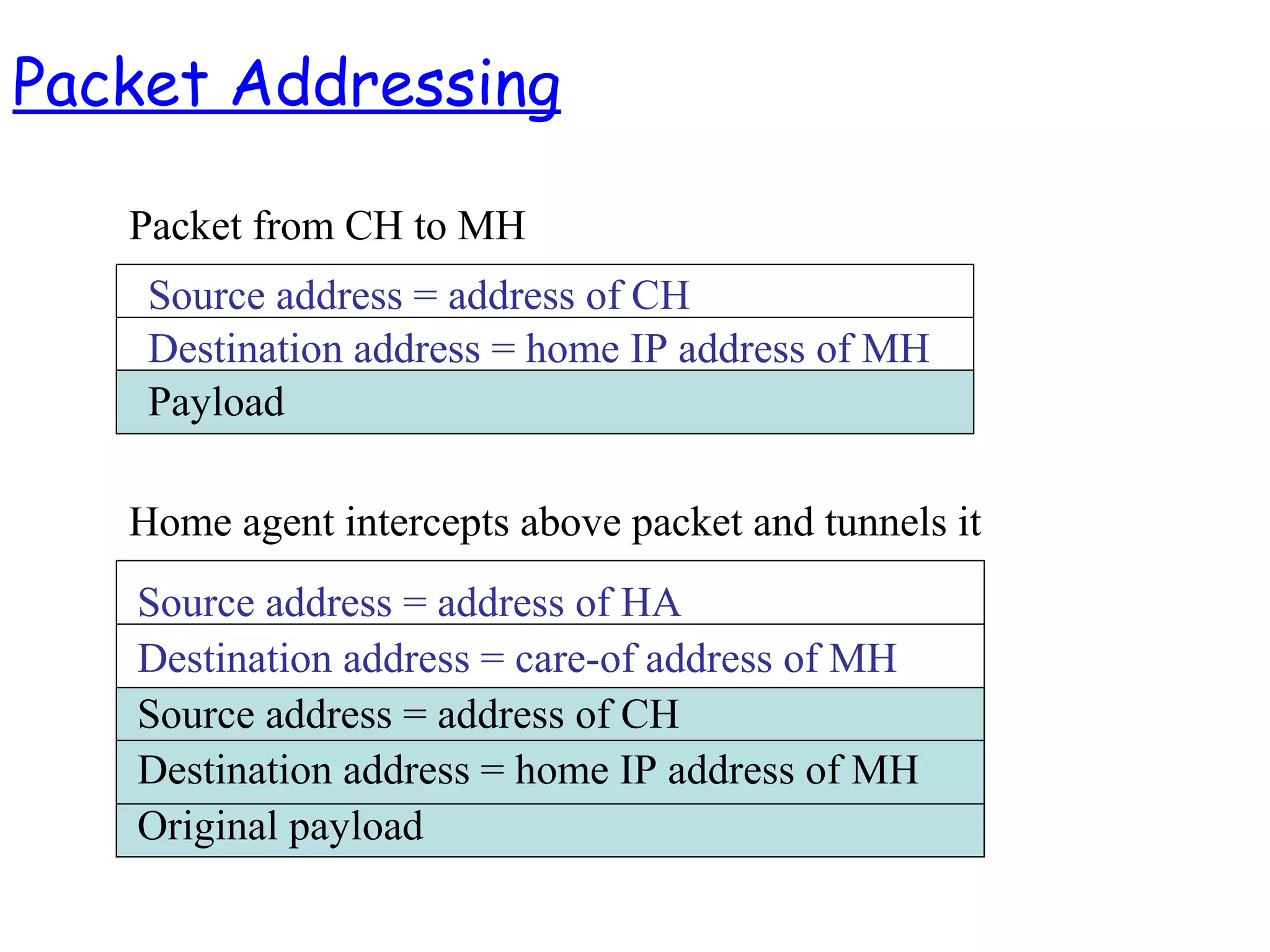
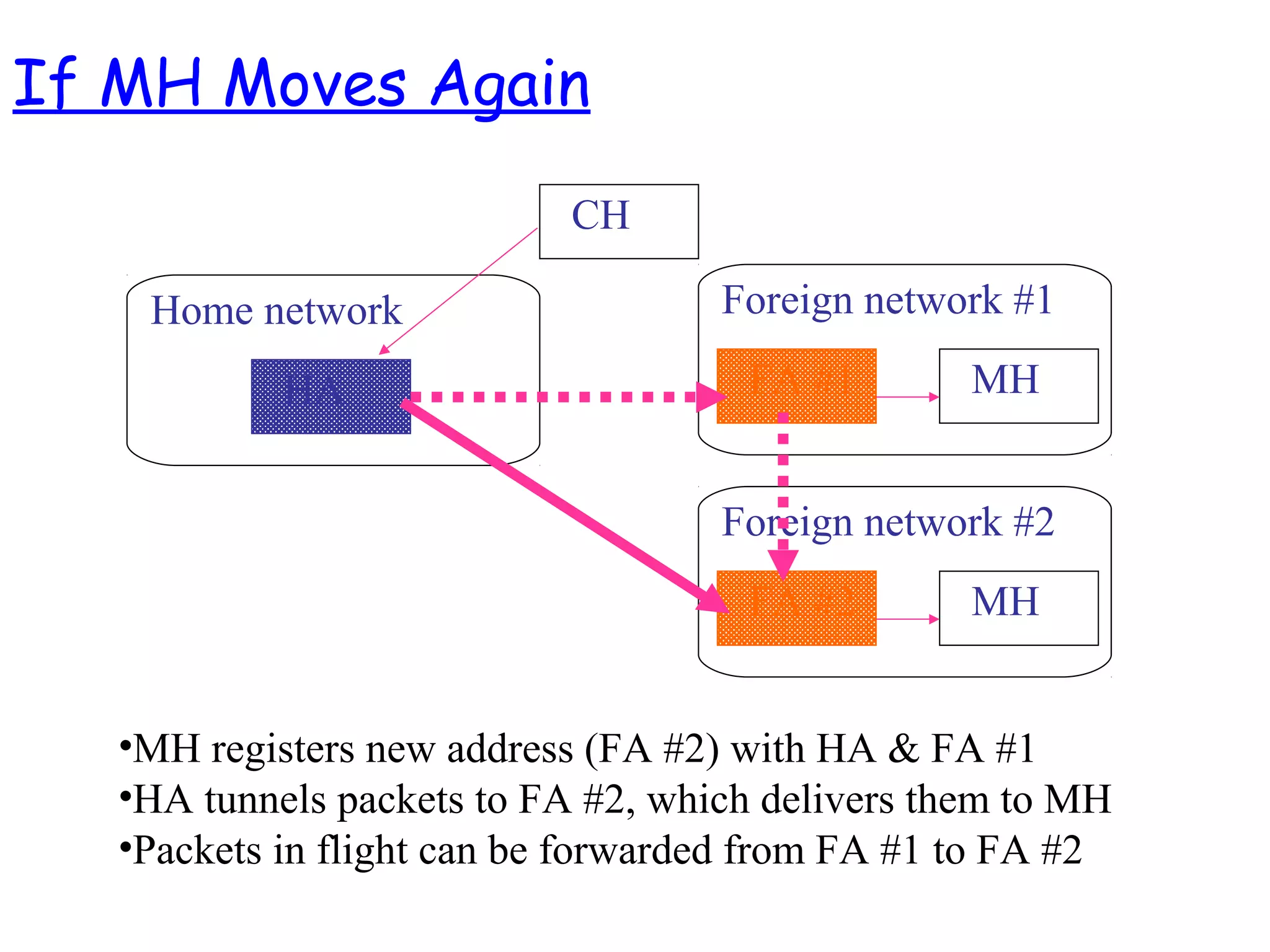
- The motivation for mobile IP to allow IP devices to move between networks while maintaining ongoing connections, using the concepts of