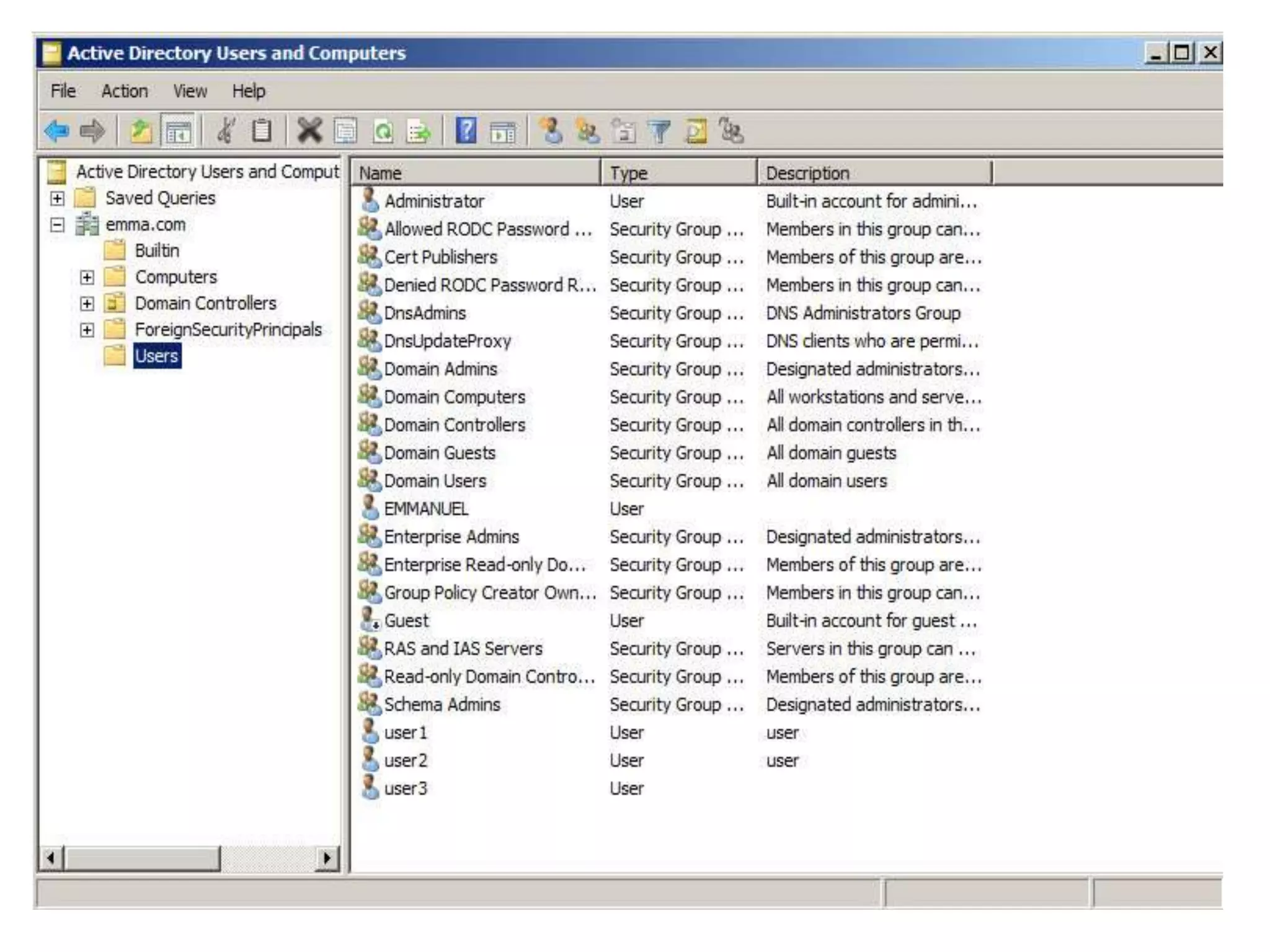
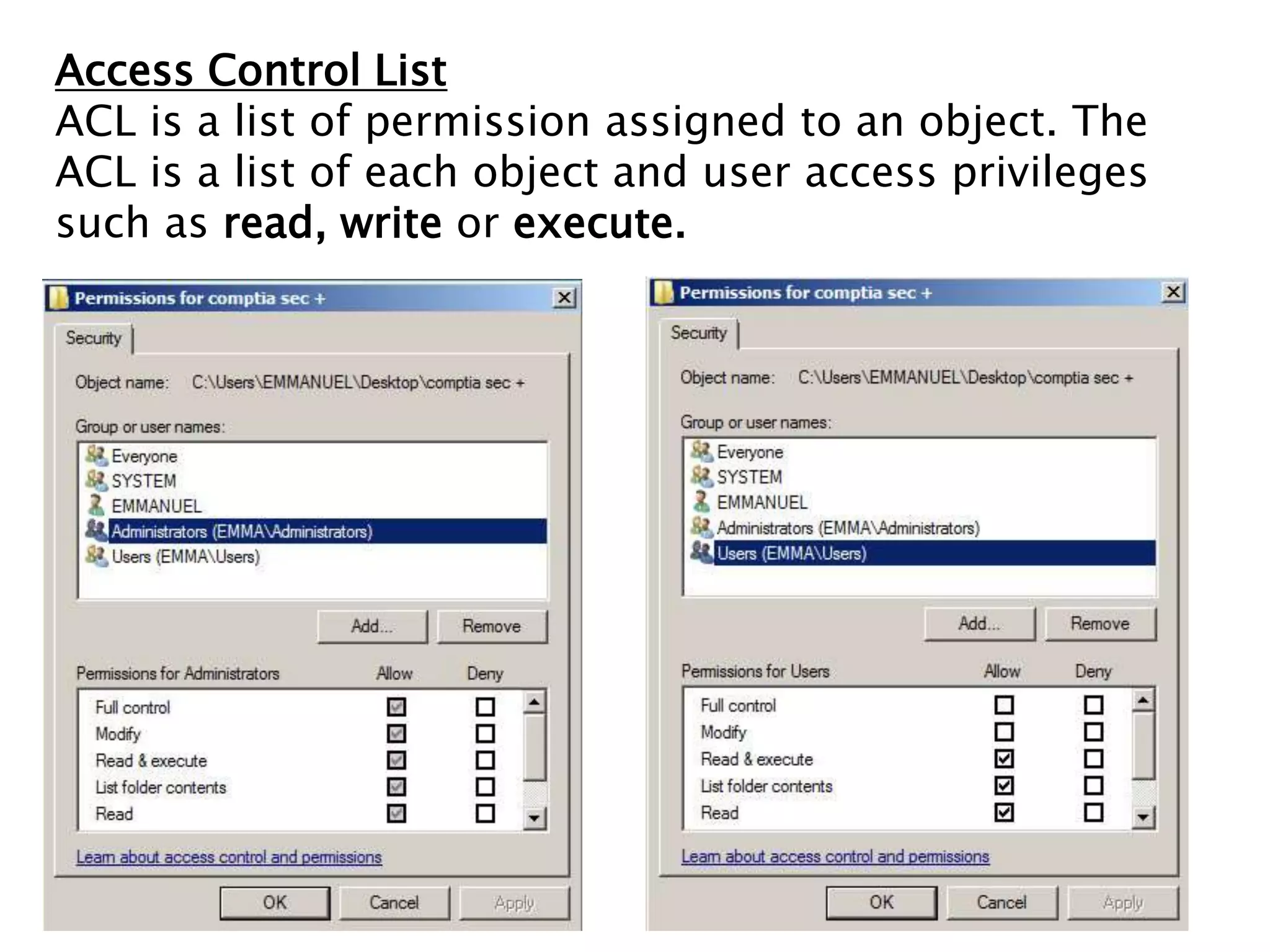
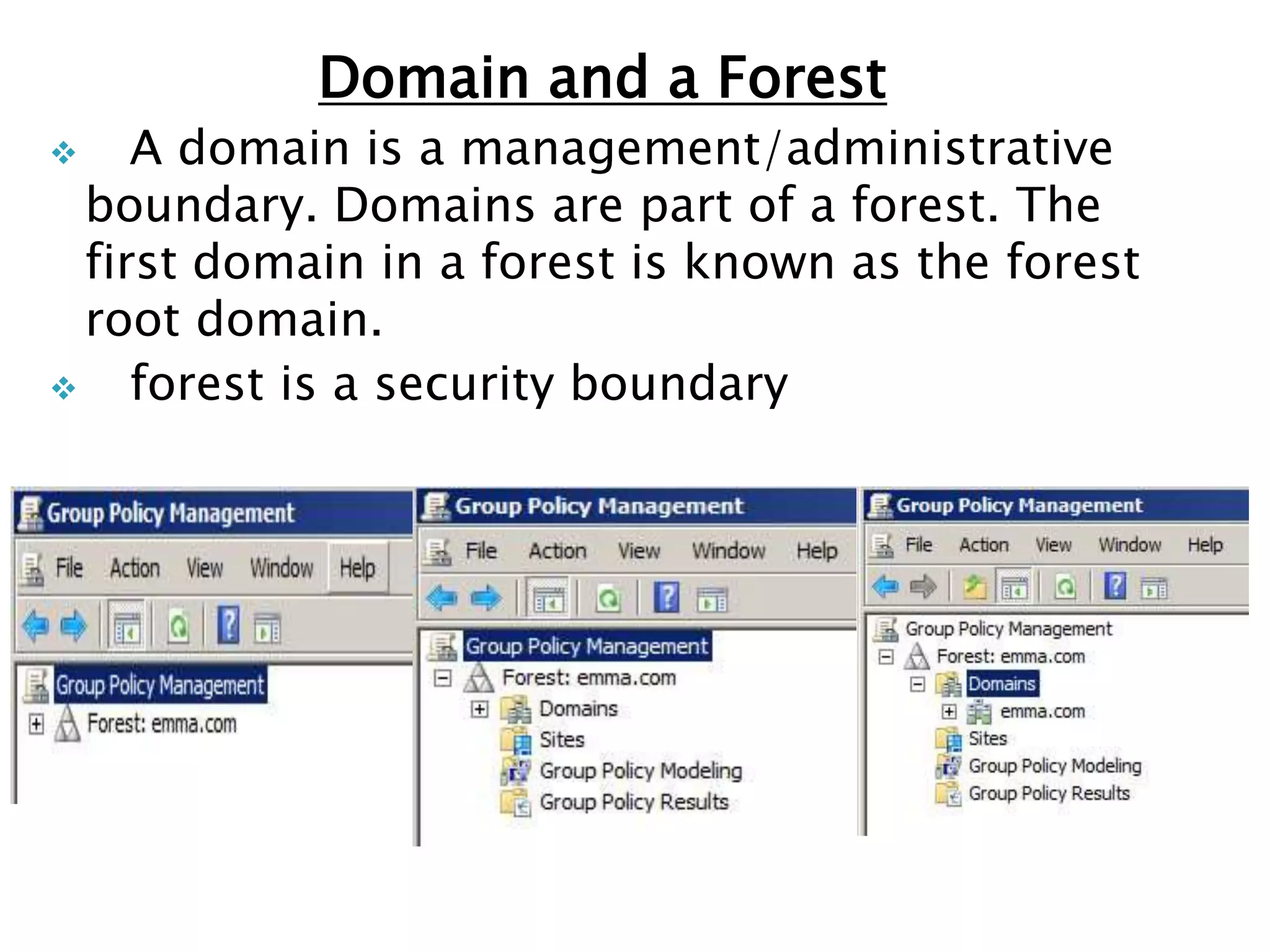
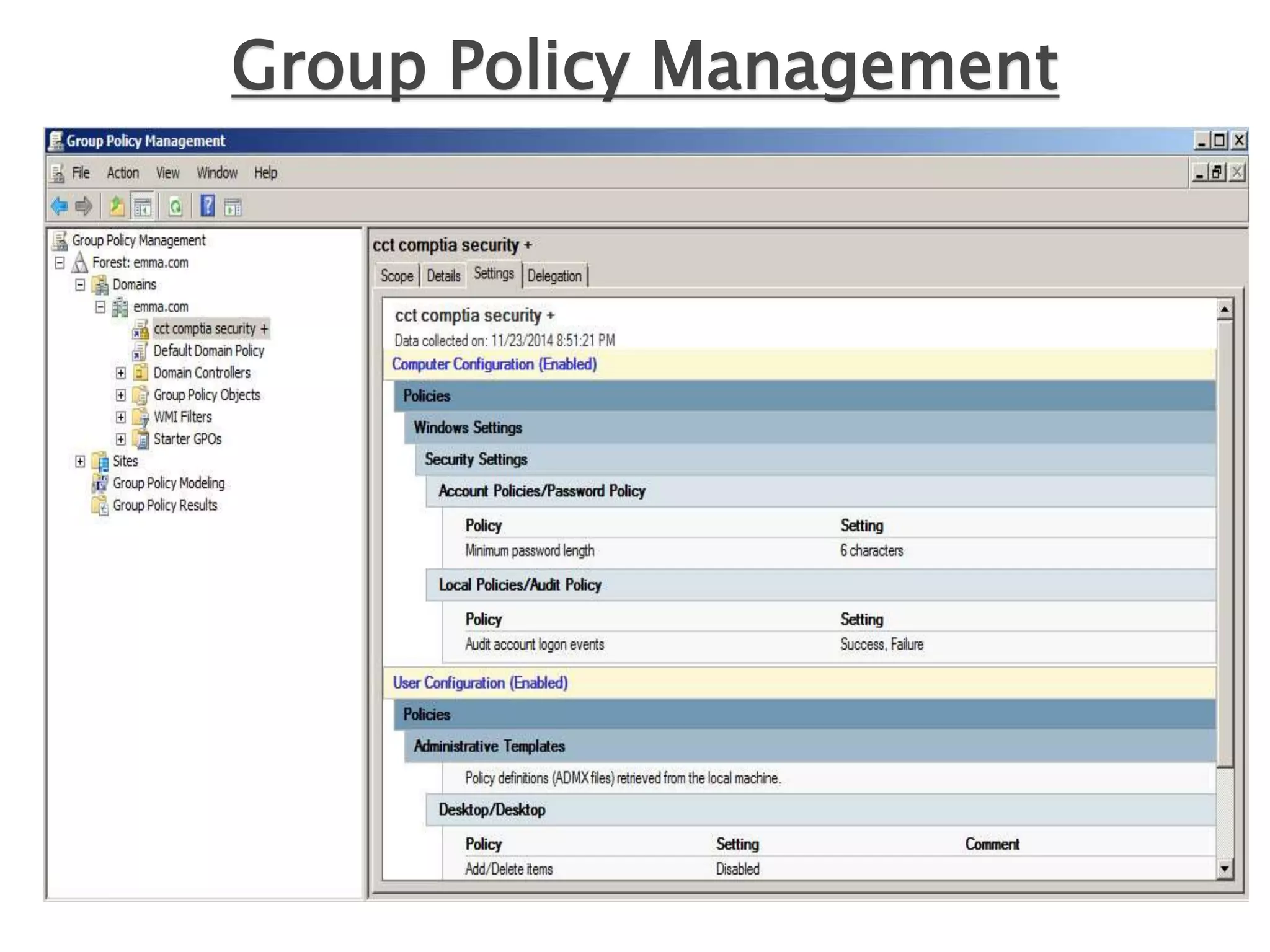
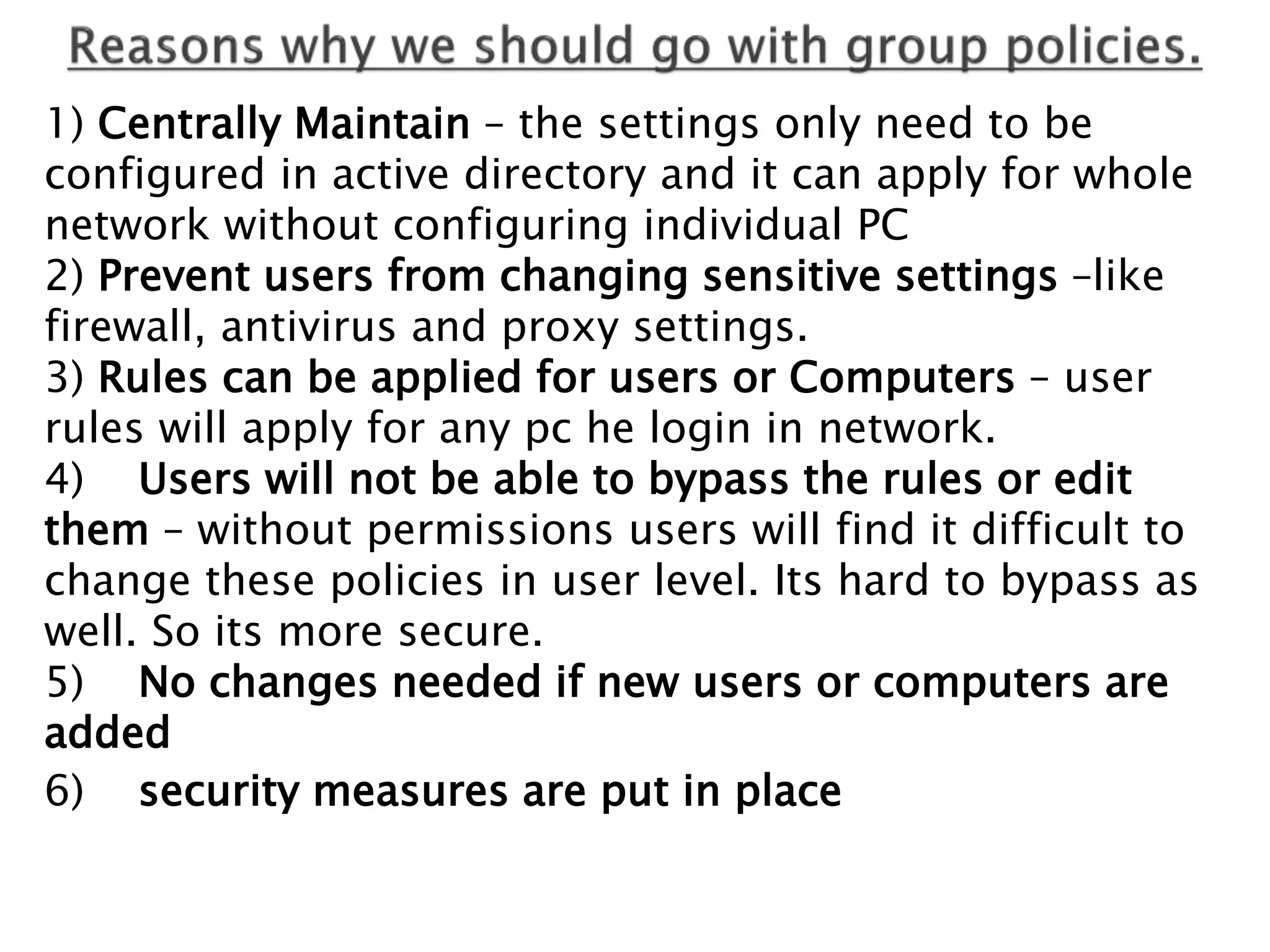
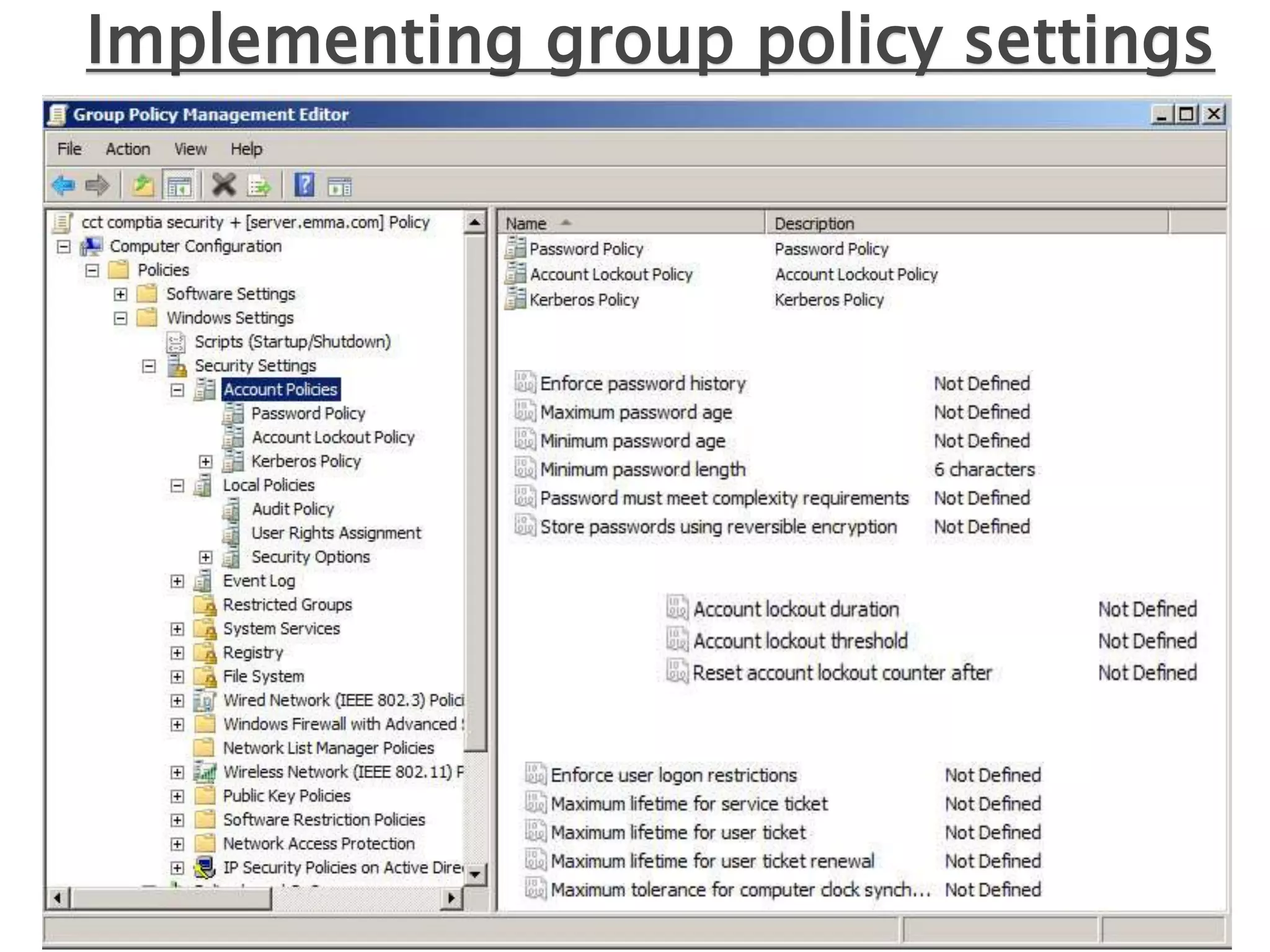
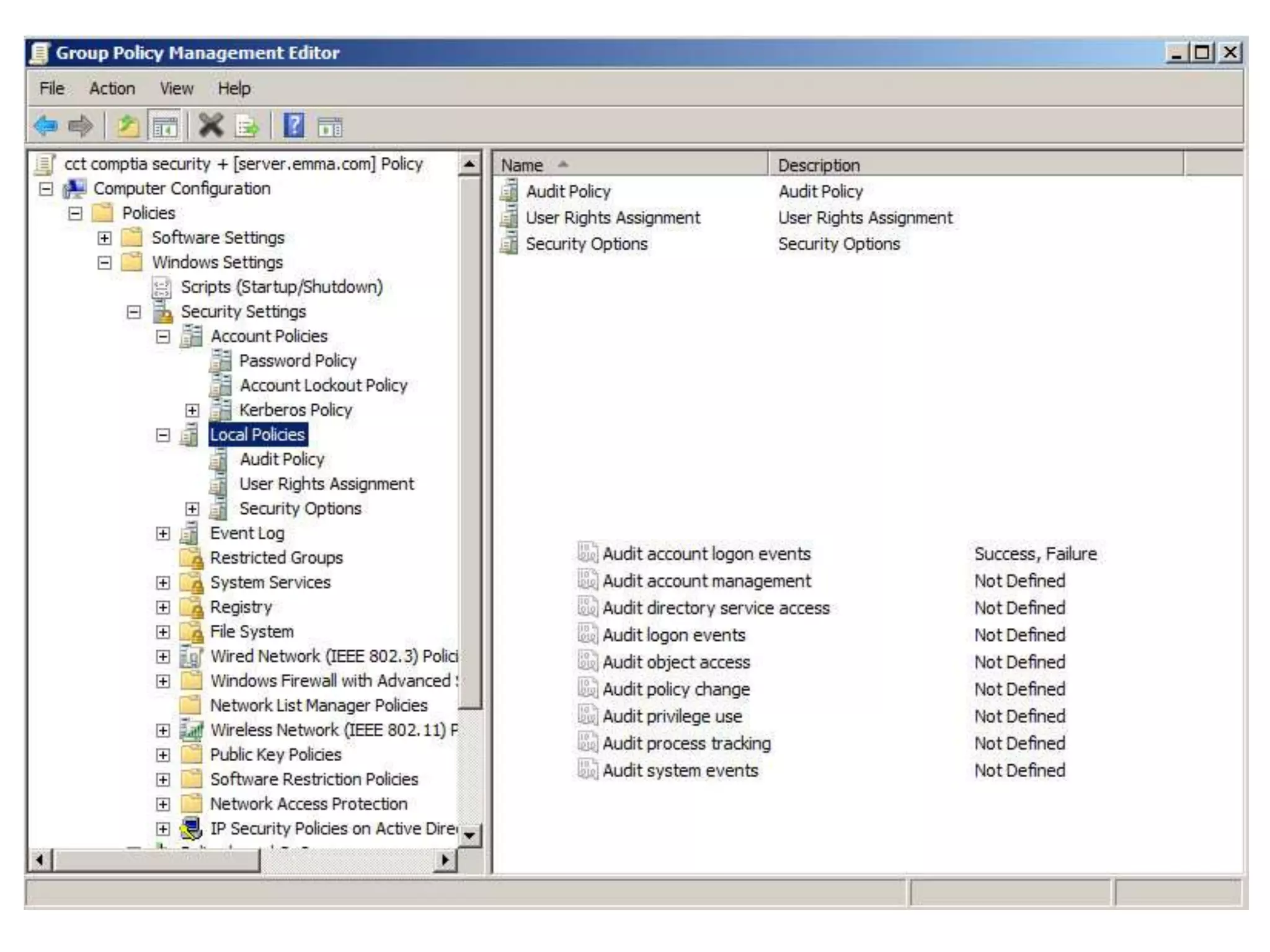
Group policy is an administrative tool in Active Directory that allows administrators to apply settings and rules to users and computers across an organization. It provides a centralized way to manage settings related to security, software installation, and user permissions. While group policy is effective for enforcing organizational standards, applying too many policies can slow down systems. It is important to balance security with usability when designing group policies.