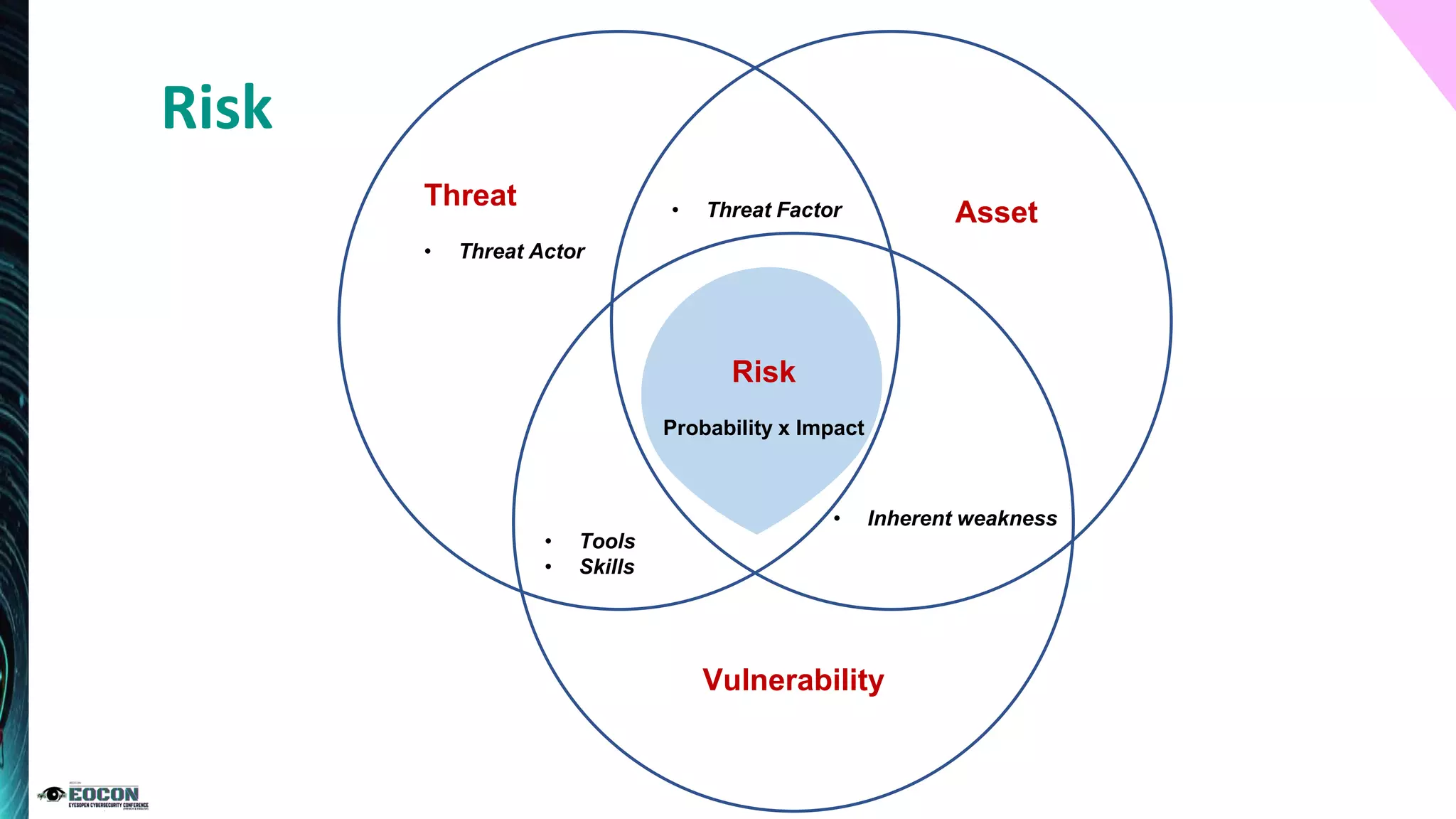
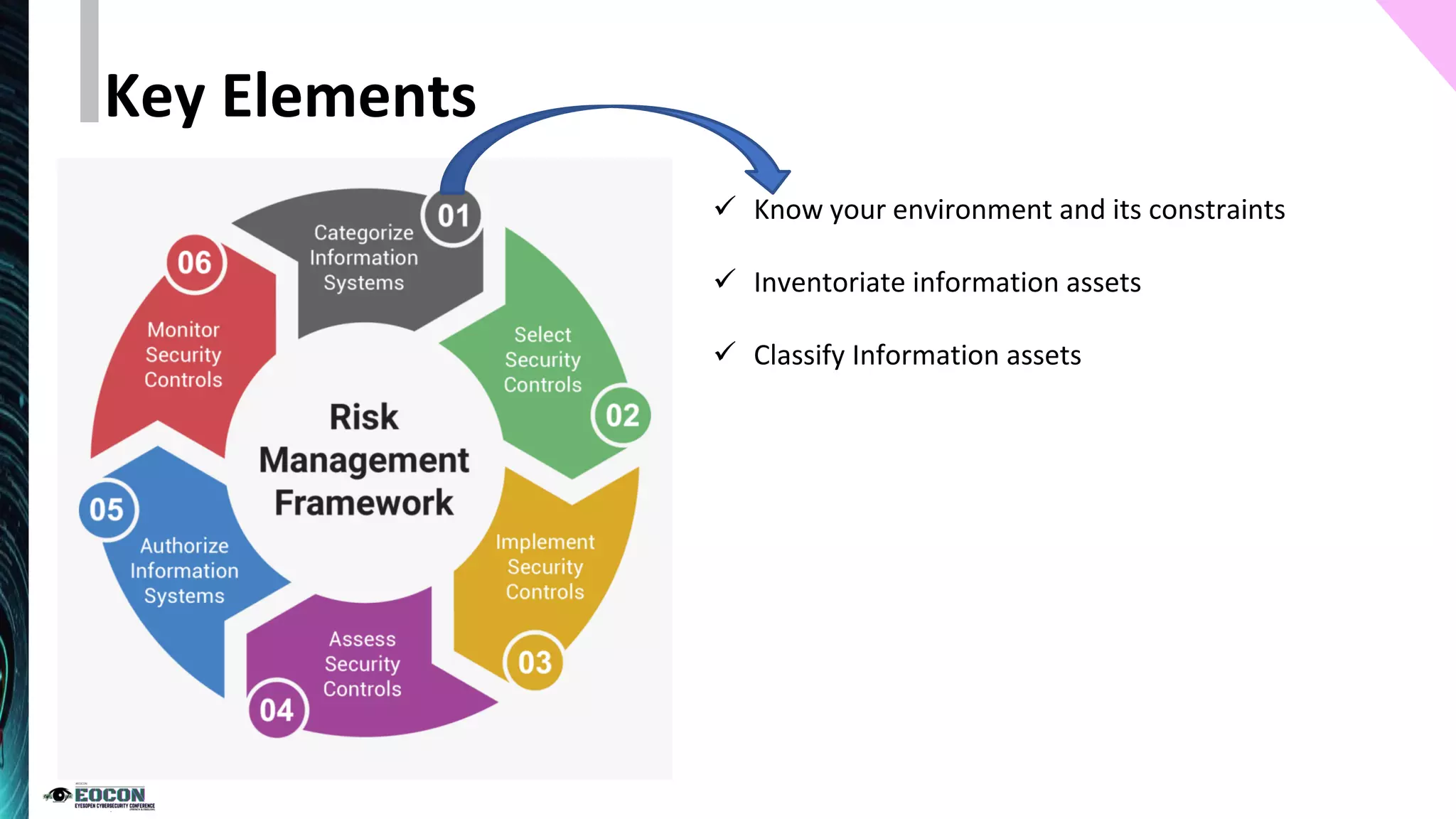
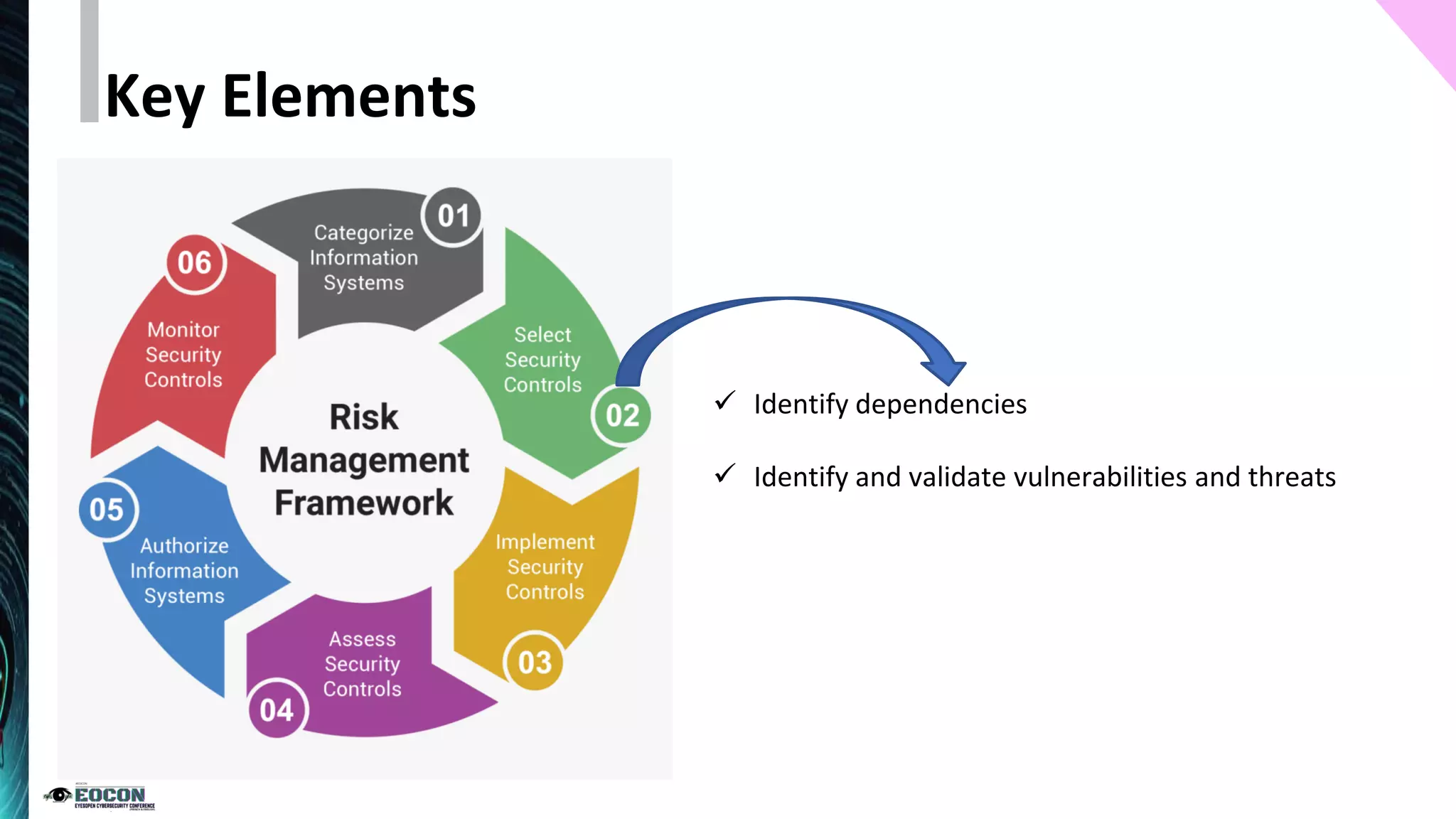
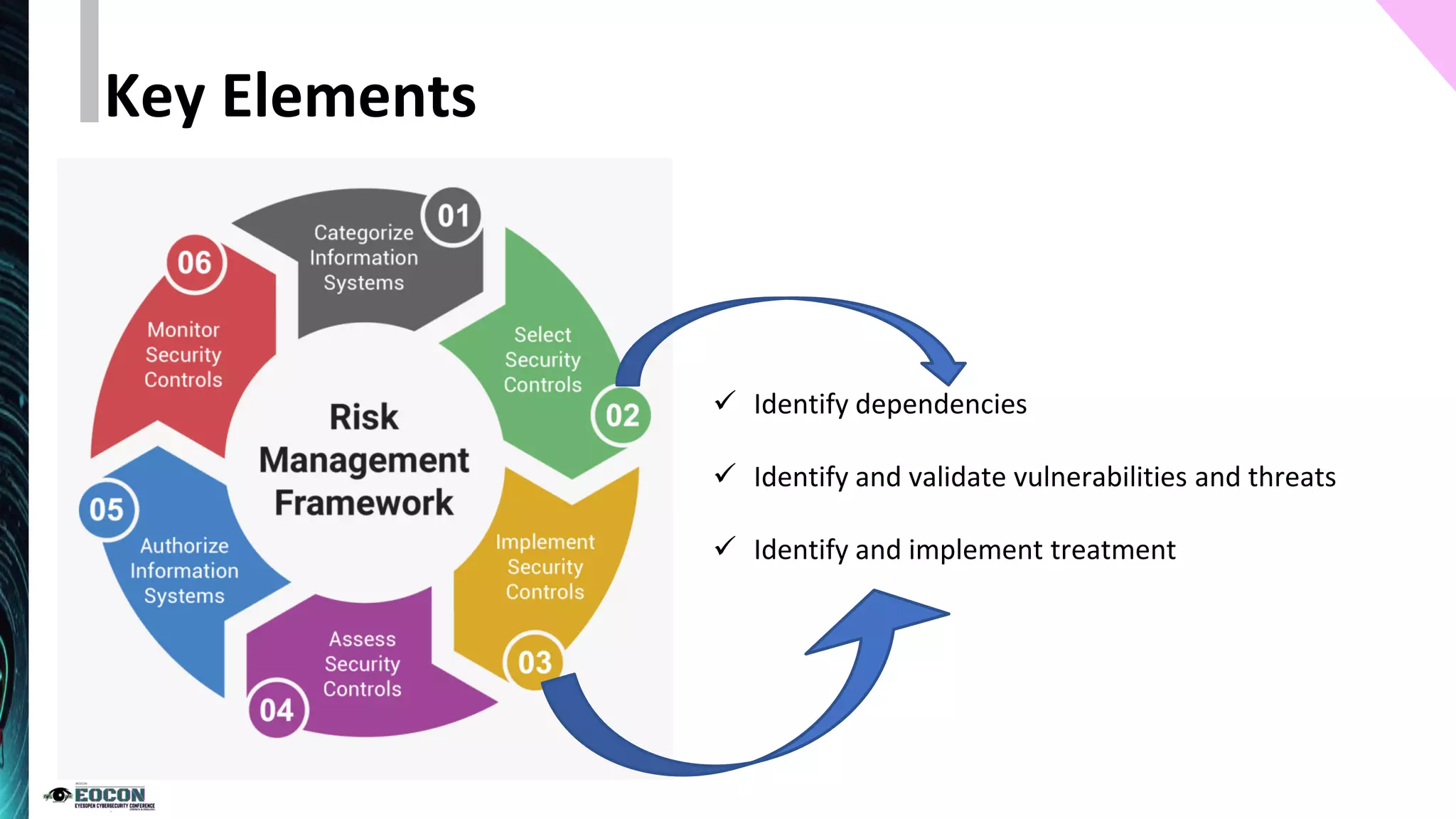
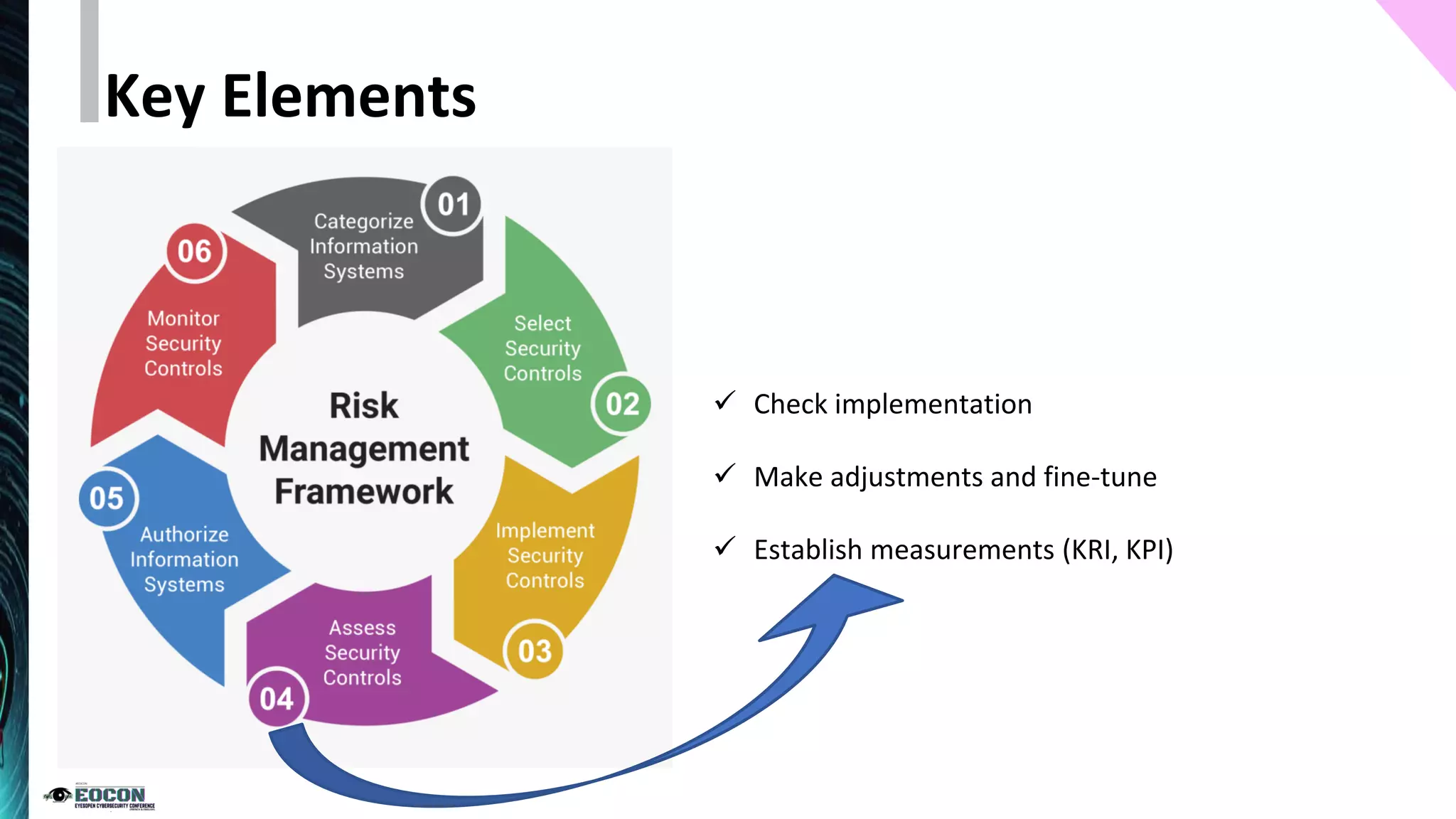
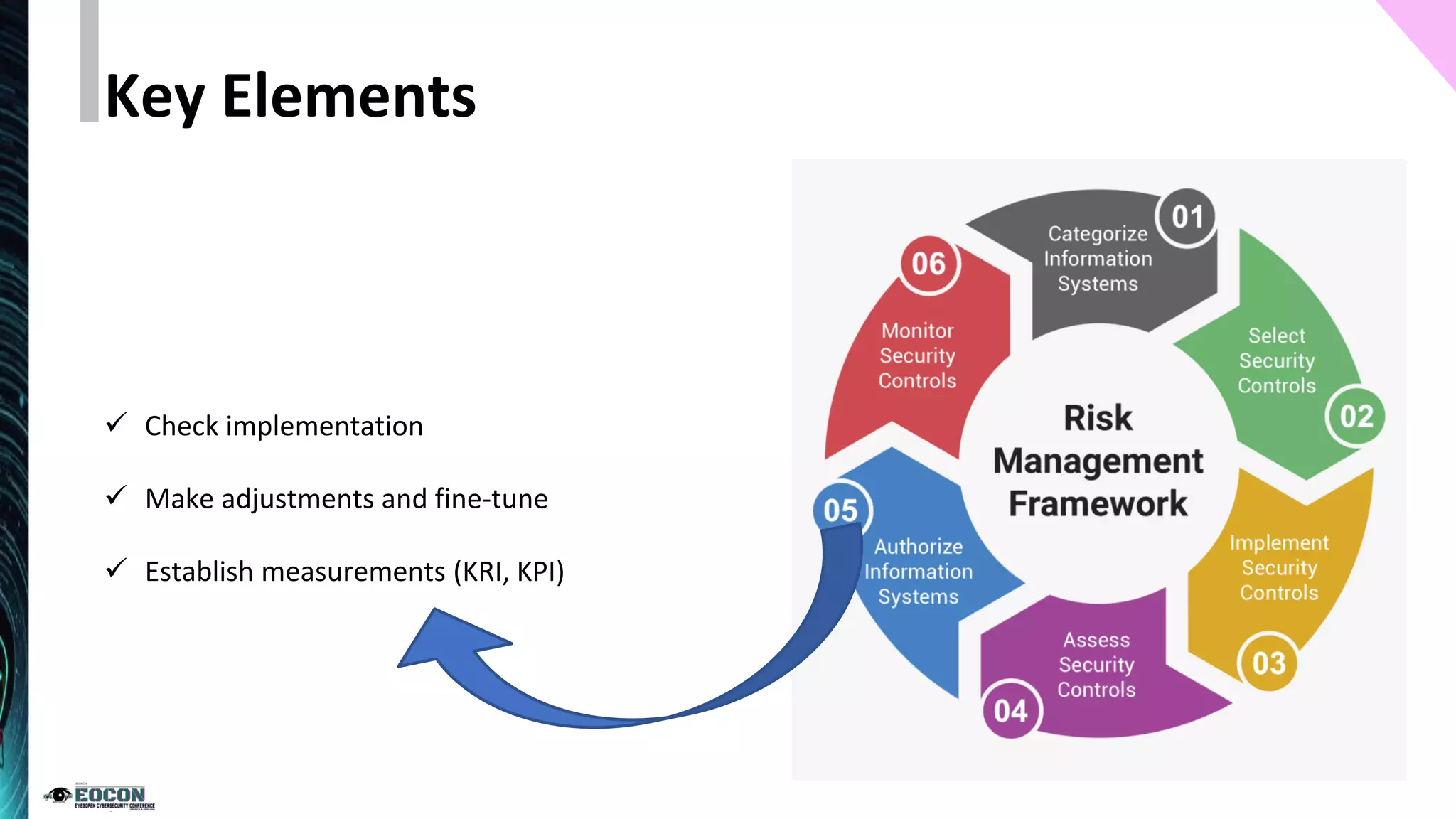
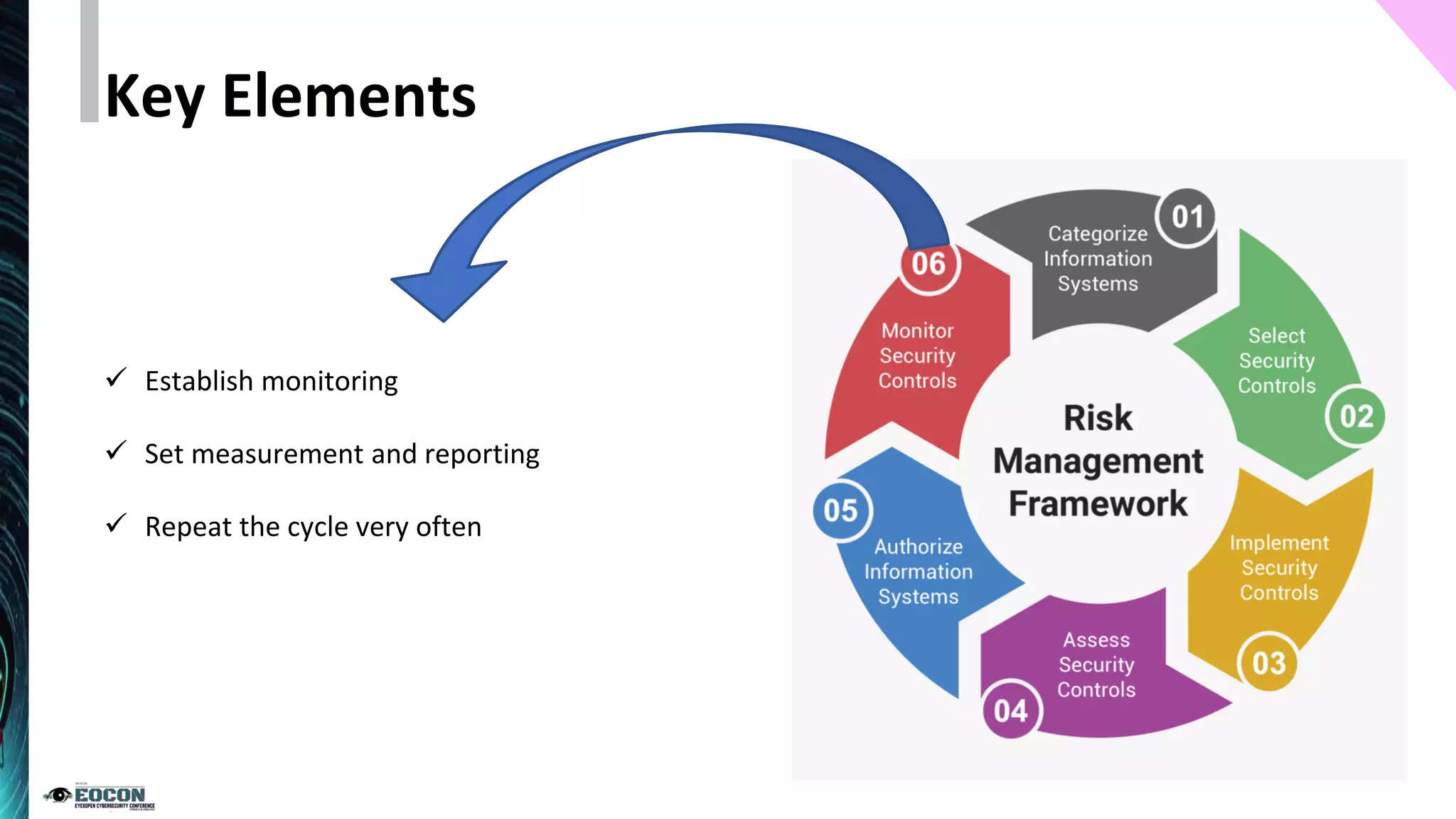
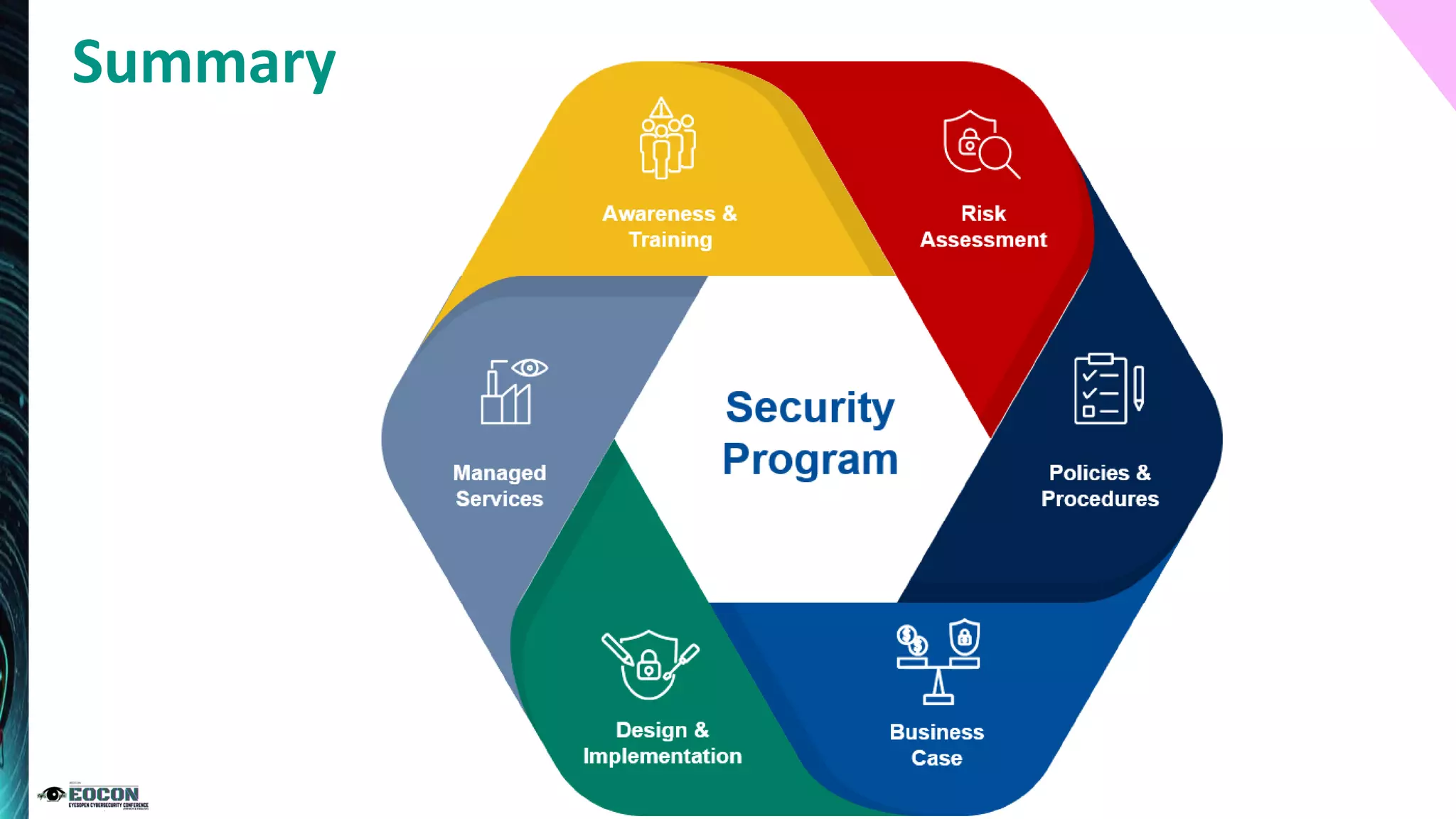
The document outlines the essentials of information security risk management, emphasizing the importance of understanding the environment, classifying information assets, and monitoring controls. It cites a specific incident involving Citibank's $900 million erroneous transaction due to software issues, which led to regulatory fines. Key dos and don'ts for effective risk management practices are also provided to enhance security efficiency.