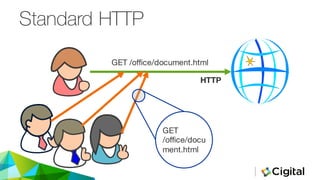
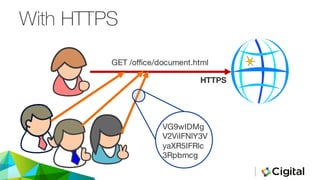
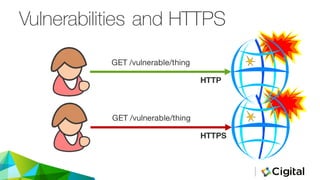
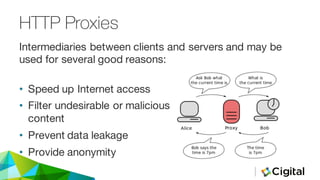
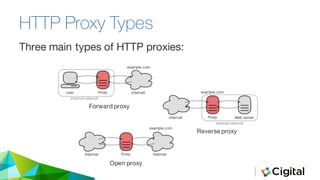
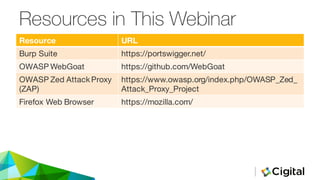
The document discusses three techniques for web security testing using proxies, focusing on understanding HTTP/S requests and the importance of testing beyond functional requirements to identify potential security vulnerabilities. It emphasizes the need for security testers to think creatively and highlights the use of tools like Burp Suite and OWASP ZAP for intercepting and modifying web requests and responses. Additionally, it addresses the role of cookies and HTTPS in web security, as well as potential pitfalls in proxy-based testing.





![Requests and Responses
GET / HTTP/1.1
Host: www.cigital.com
User-Agent: Mozilla/5.0 (Windows NT 6.1;
WOW64; rv:29.0) Gecko/20100101
Firefox/29.0
Accept:
text/html,application/xhtml+xml,applicati
on/xml;q=0.9,*/*;q=0.8
Accept-Language: en-gb,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
HTTP/1.1 200 OK
Date: Thu, 03 Jul 2014 10:24:38 GMT
Server: Apache
X-Powered-By: PHP/5.5.10
X-Pingback:
http://www.cigital.com/xmlrpc.php
Link: <http://www.cigital.com/>;
rel=shortlink
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
Content-Length: 27893
[HTML document]
Client¹ Sends Server Responds
¹ ”client” can be a browser, mobile device,
or anything making HTTP requests](https://image.slidesharecdn.com/pacohopewebsecuritytestingproxy1-160324135313/85/The-3-Top-Techniques-for-Web-Security-Testing-Using-a-Proxy-6-320.jpg)
![HTTP Requests GET /training/ HTTP/1.1
Host: www.cigital.com
User-Agent: Mozilla/5.0 (Windows NT 6.1;
WOW64; rv:29.0) Gecko/20100101
Firefox/29.0
Accept:
text/html,application/xhtml+xml,applicat
ion/xml;q=0.9,*/*;q=0.8
Accept-Language: en-gb,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://www.cigital.com/
Cookie:
__utma=269626595.872944553.1402325345.14
02909557.1404383087.3; [truncated...]
Connection: keep-alive
Structure
o Method/path/protocol
version
o Headers
• User-agent and referrer may not
always be there
• Browser includes all the cookies
it has for the site to which it
connects](https://image.slidesharecdn.com/pacohopewebsecuritytestingproxy1-160324135313/85/The-3-Top-Techniques-for-Web-Security-Testing-Using-a-Proxy-7-320.jpg)
![HTTP/1.1 200 OK
Date: Thu, 20 Mar 2014 17:05:51 GMT
Server: Apache/1.2.34 (Debian)
X-Powered-By: PHP/1.2.3-4+deb7u7
X-Pingback:
http://www.cigital.com/xmlrpc.php
Link: <http://www.cigital.com/?p=4370>;
rel=shortlink
Vary: Accept-Encoding
Content-Type: text/html; charset=UTF-8
Set-Cookie: name=value
Set-Cookie: name2=value2; Expires=Wed, 09
Jun 2021 10:18:14 GMT
Connection: Keep-Alive
[HTML document]
Structure:
• Headers first
• Blank line
• Content
Response codes:
• 200 OK
• 404 Not Found
HTTP Responses](https://image.slidesharecdn.com/pacohopewebsecuritytestingproxy1-160324135313/85/The-3-Top-Techniques-for-Web-Security-Testing-Using-a-Proxy-8-320.jpg)