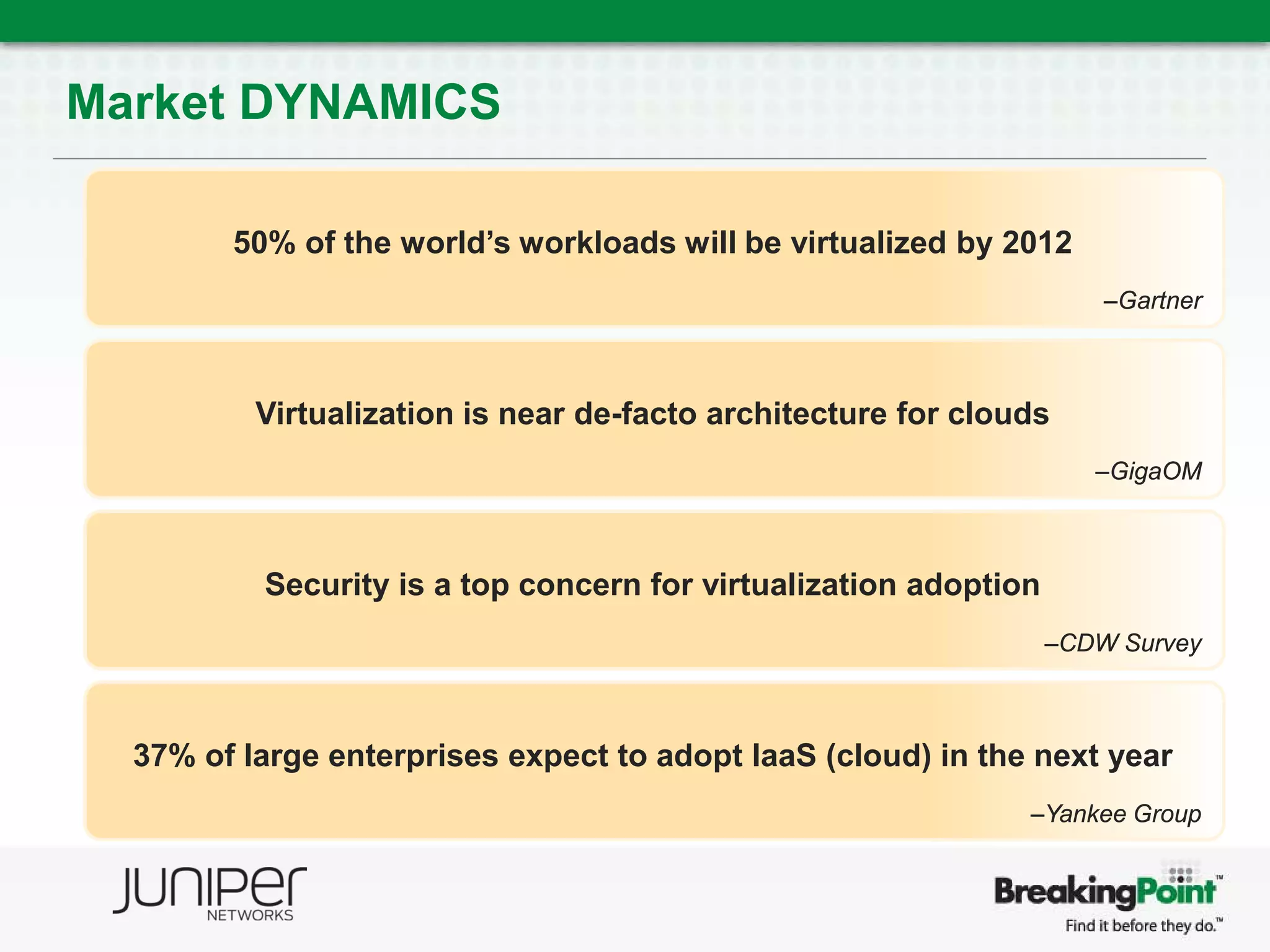
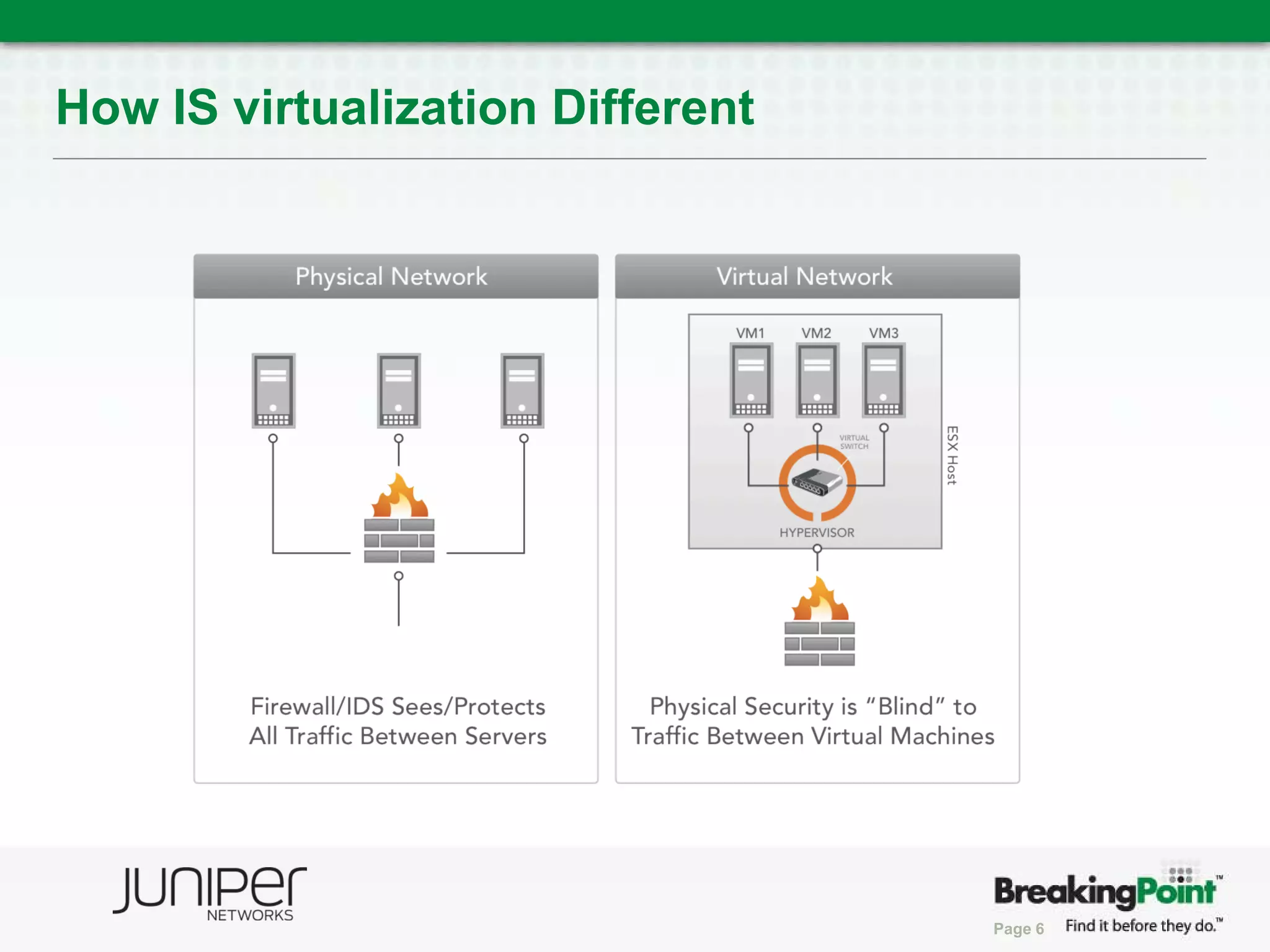
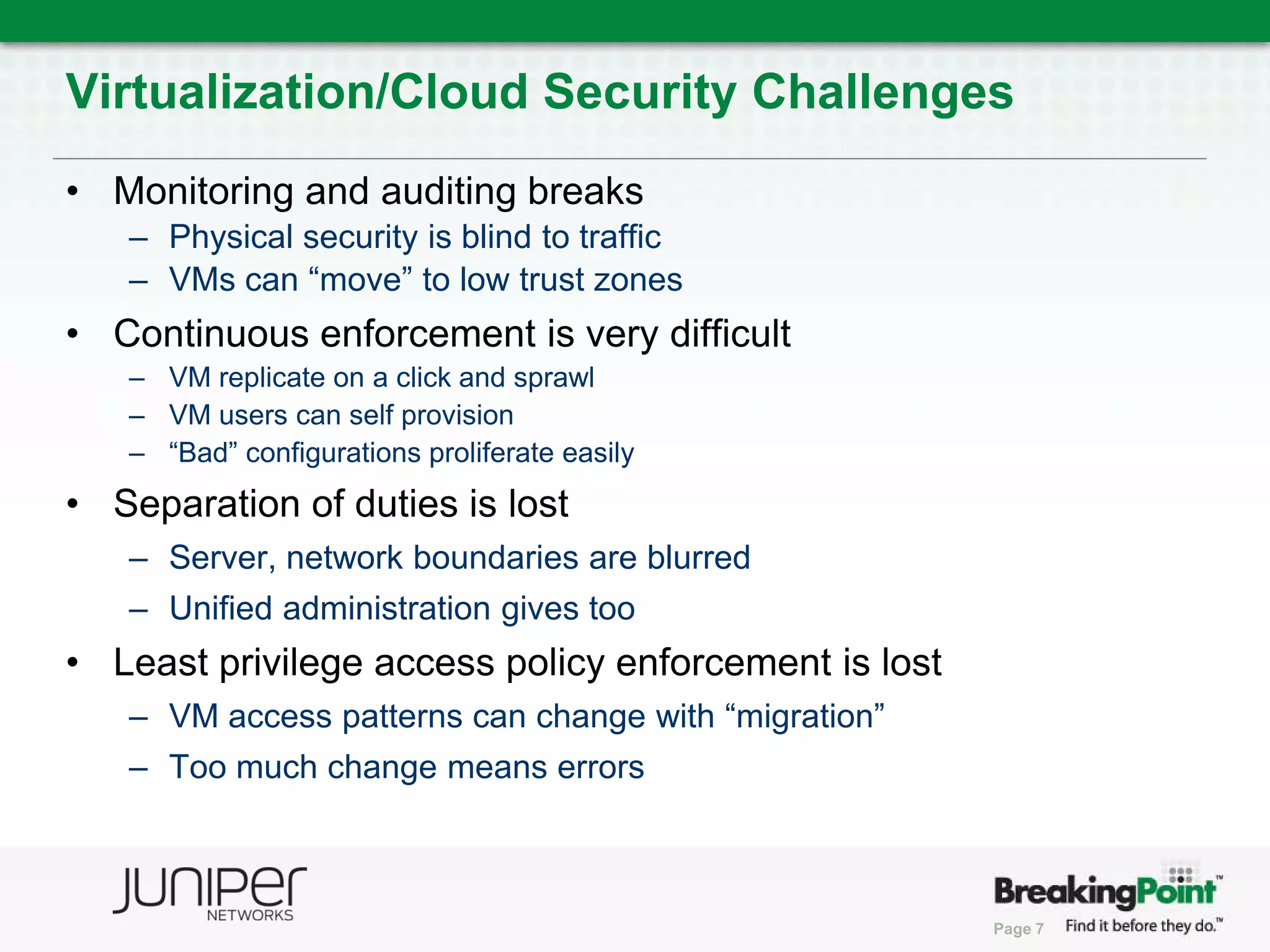
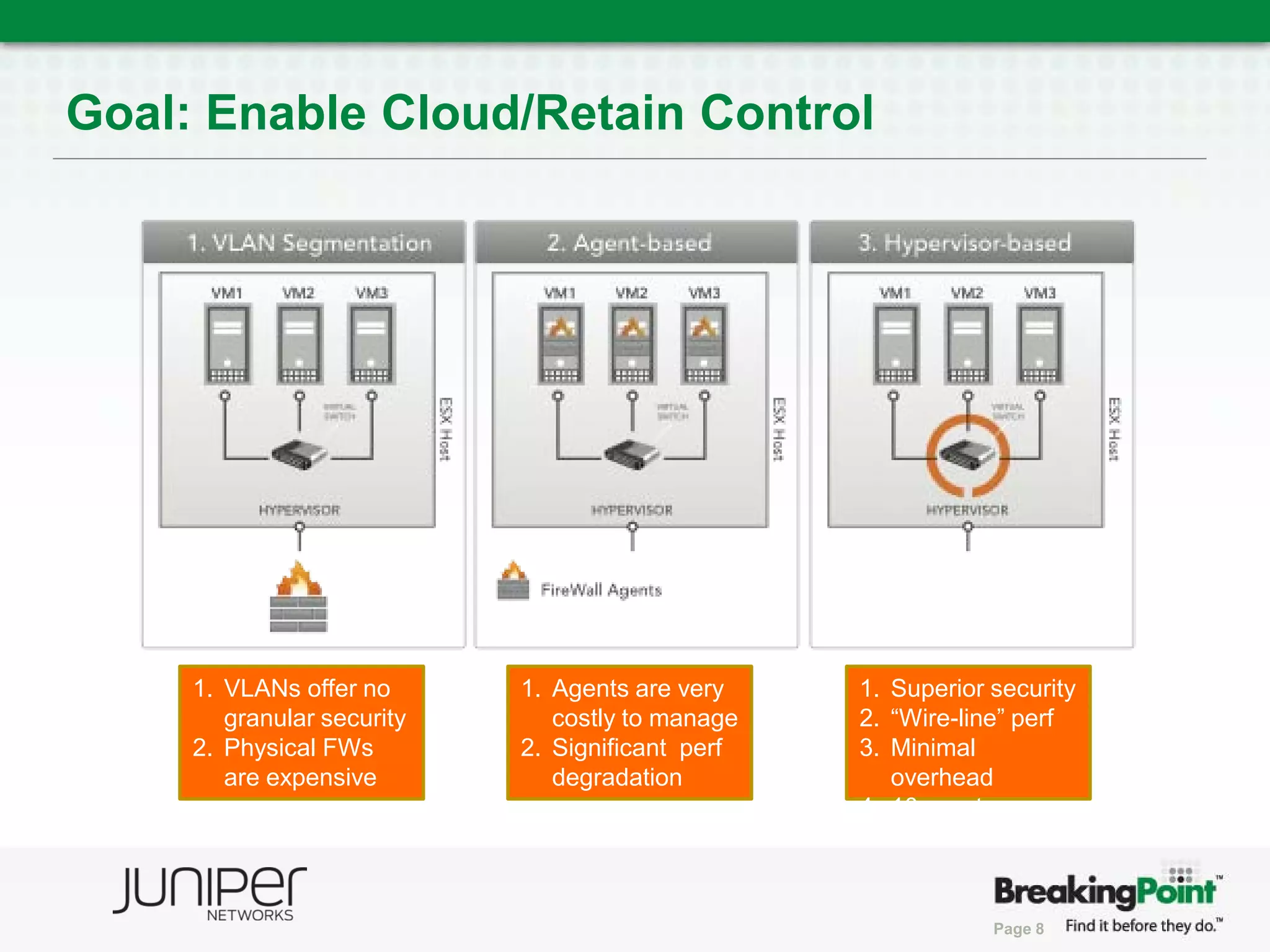
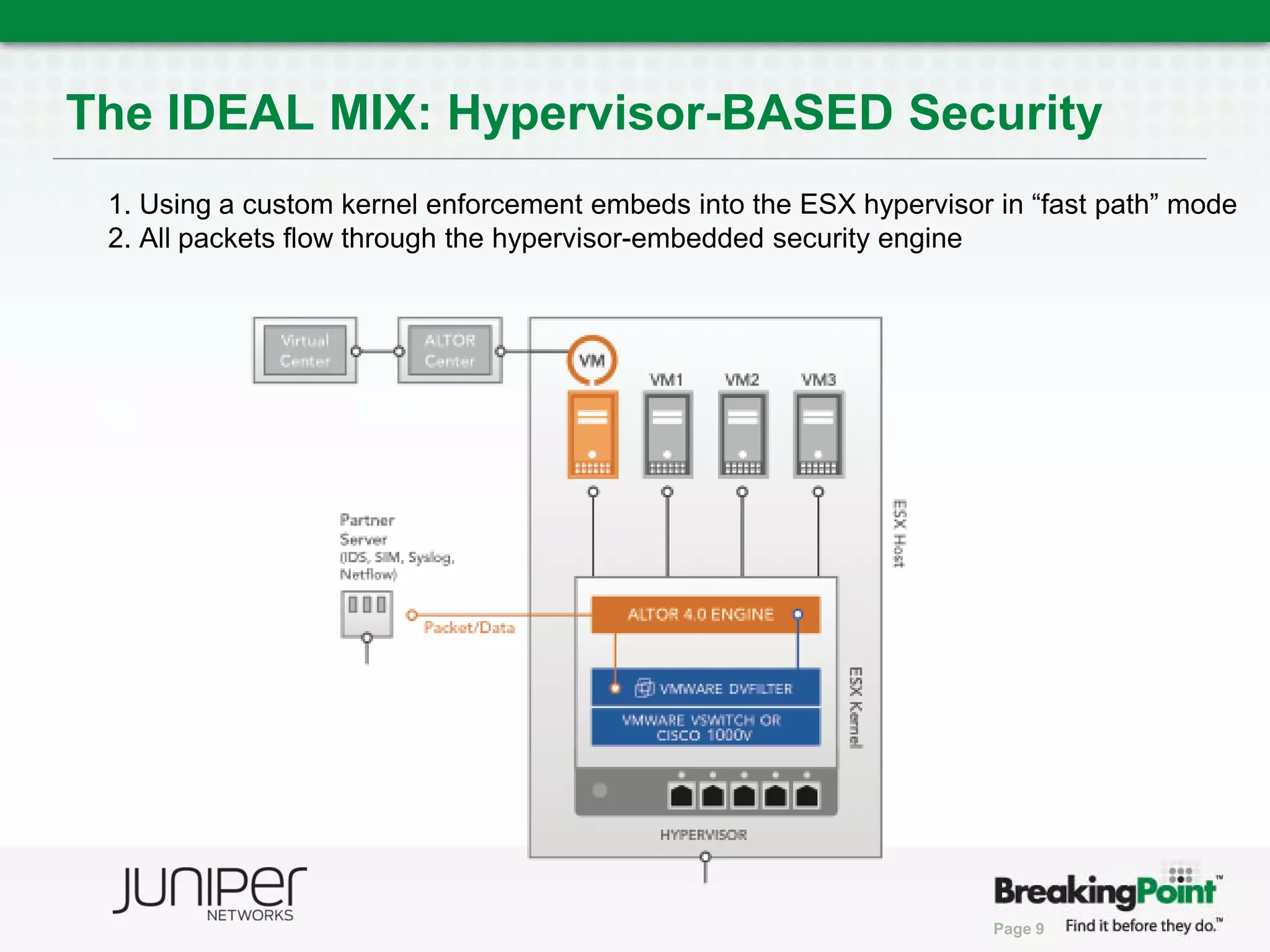
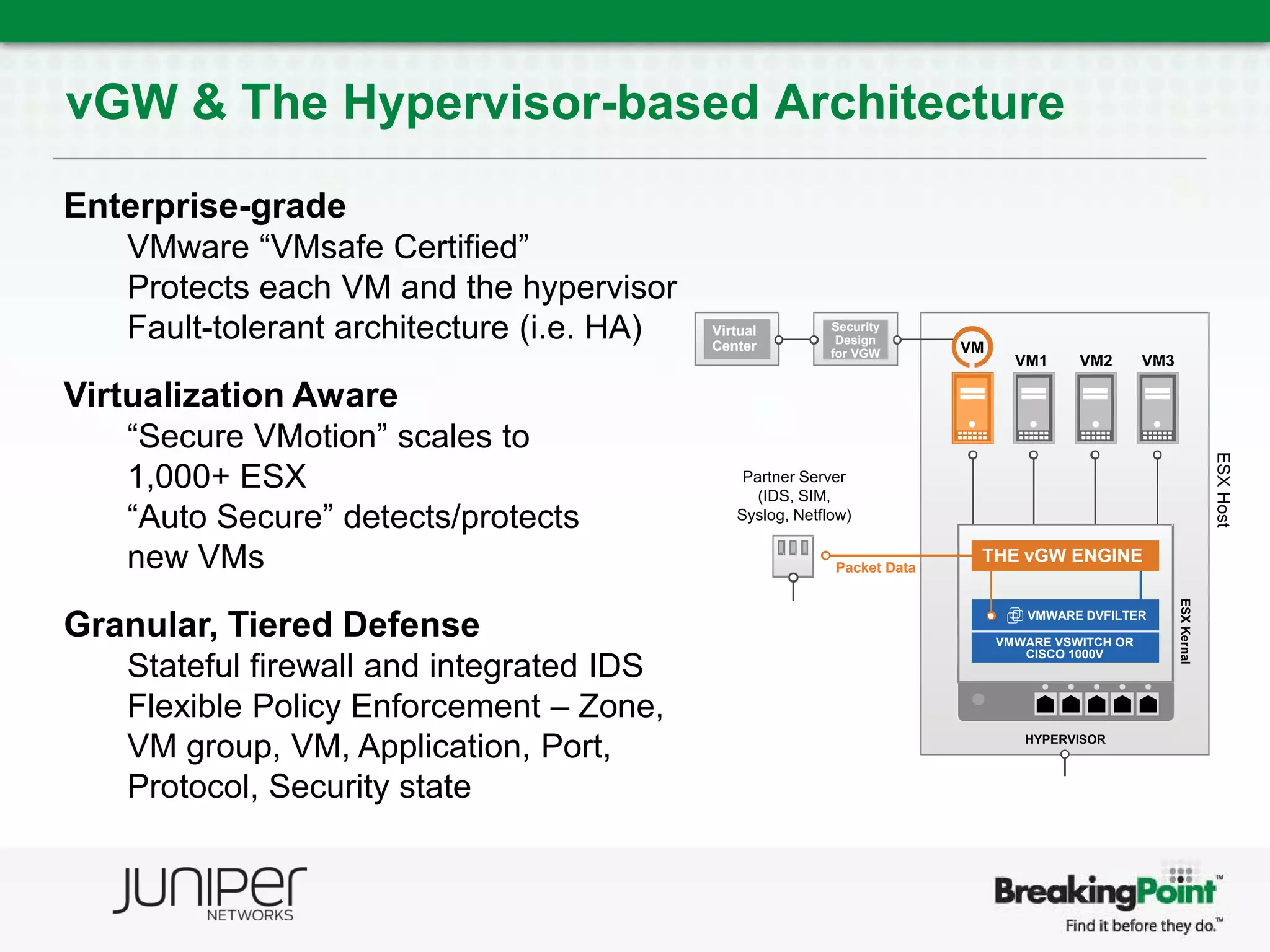
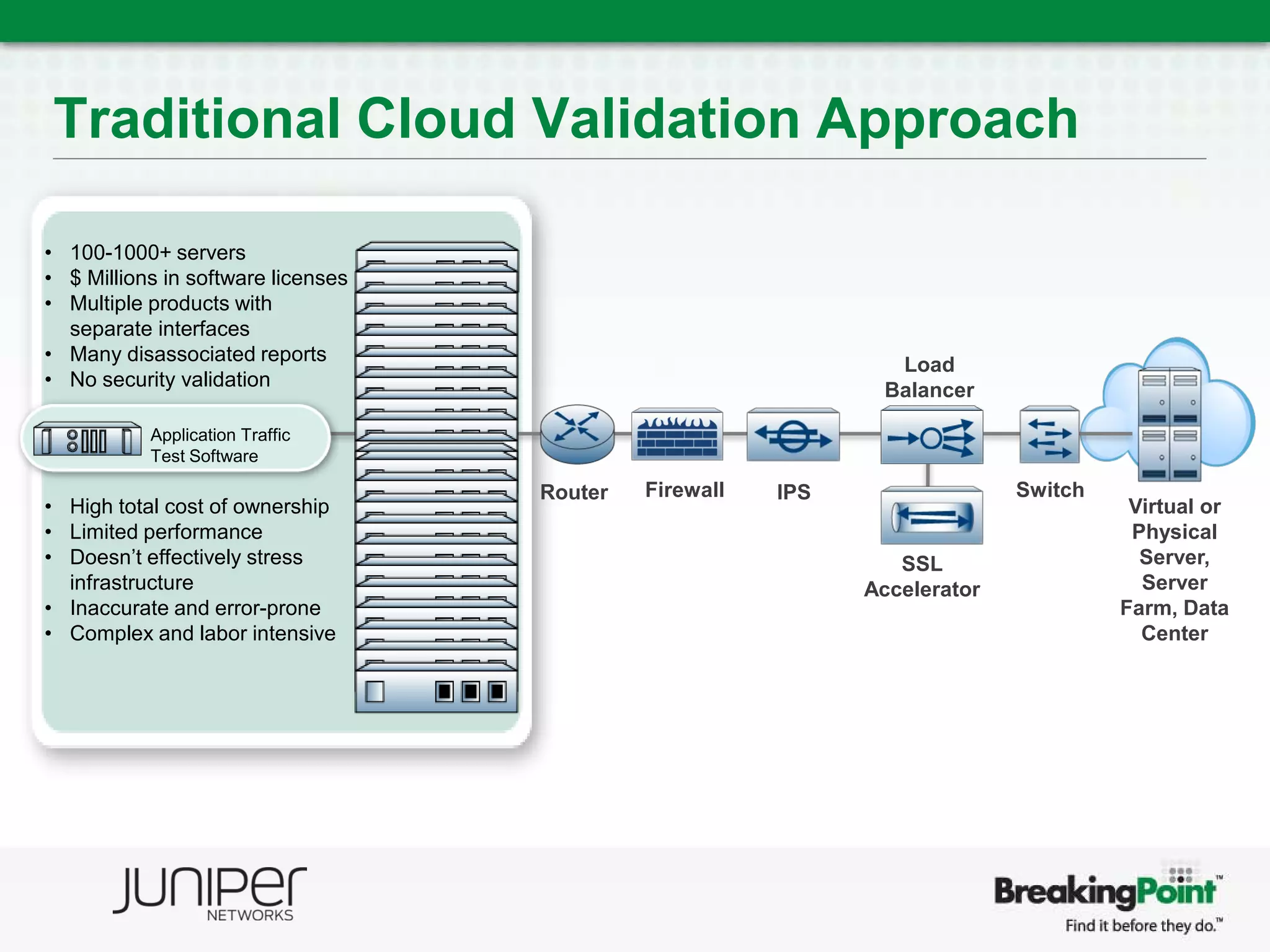
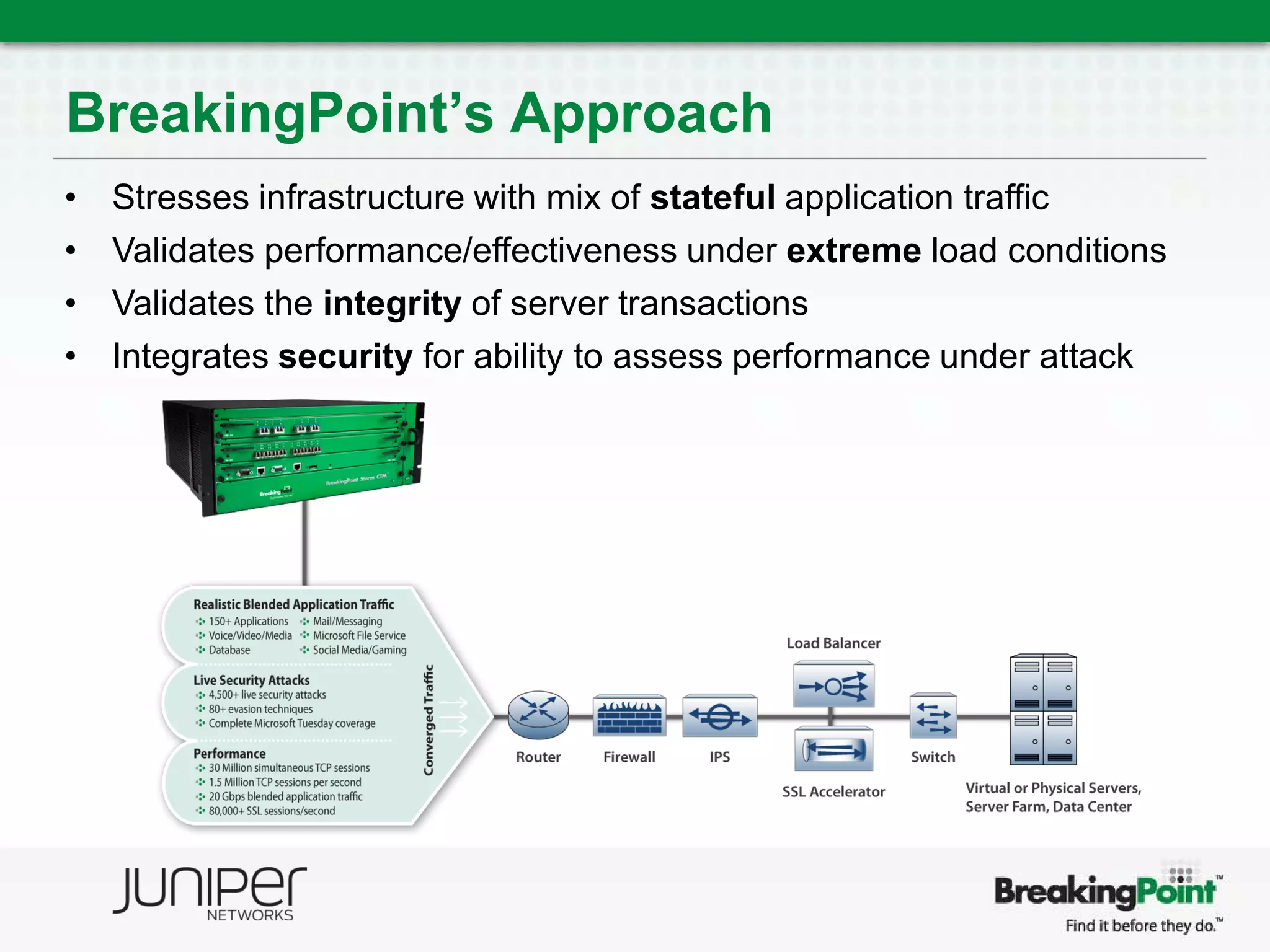
This document discusses securing virtualized and cloud environments. It notes that virtualization is becoming a common architecture for clouds, but security is a top concern for adoption. The challenges of securing virtualized environments are described, such as lack of visibility and difficulty with continuous enforcement. The goal is to enable secure clouds while retaining control. The ideal solution is described as using a hypervisor-based security architecture, with an engine embedded in the hypervisor, to provide granular security while minimizing overhead. Traditional validation approaches are discussed along with a proposed approach using BreakingPoint to effectively stress infrastructure and validate security under high load conditions.