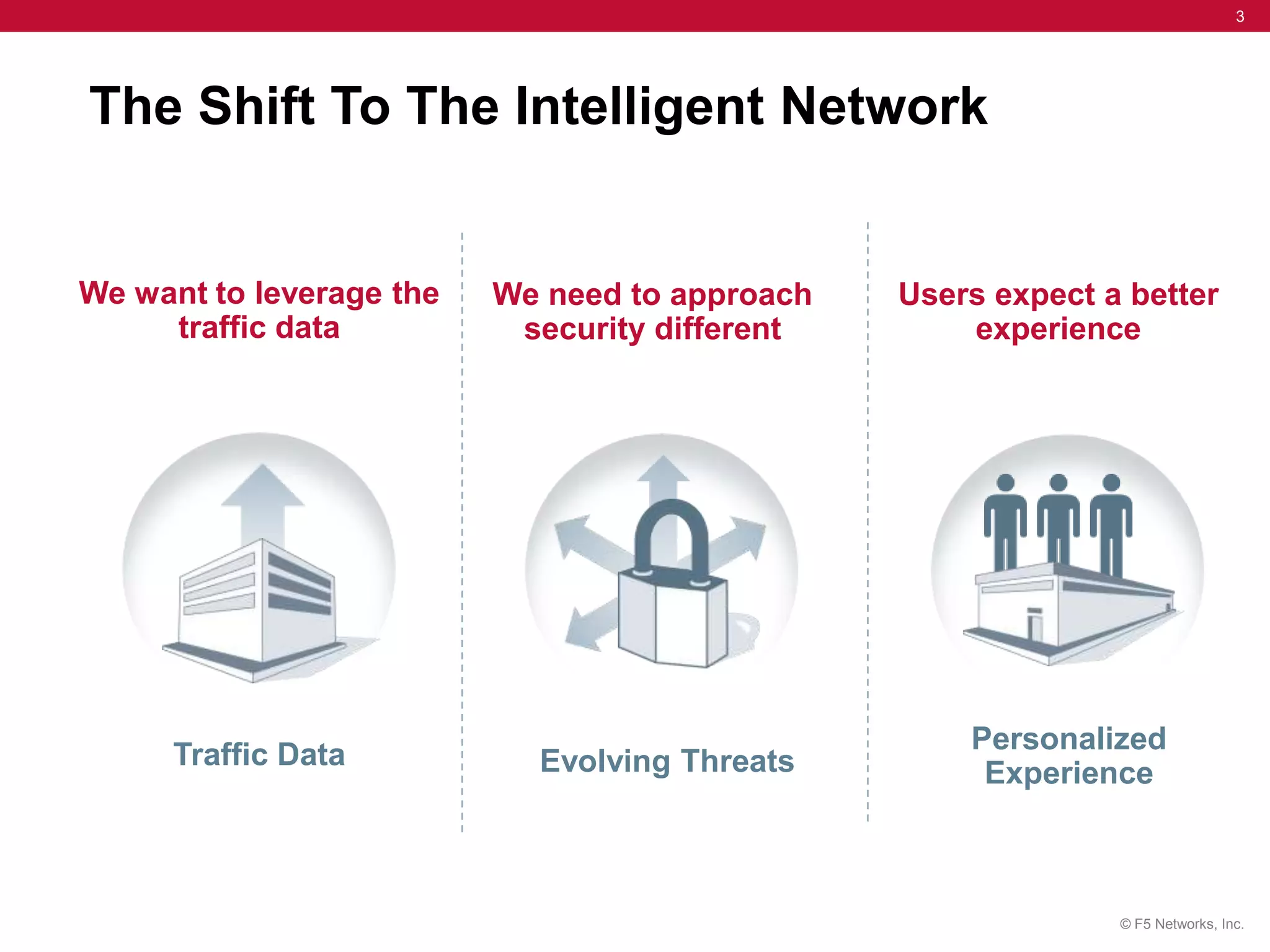
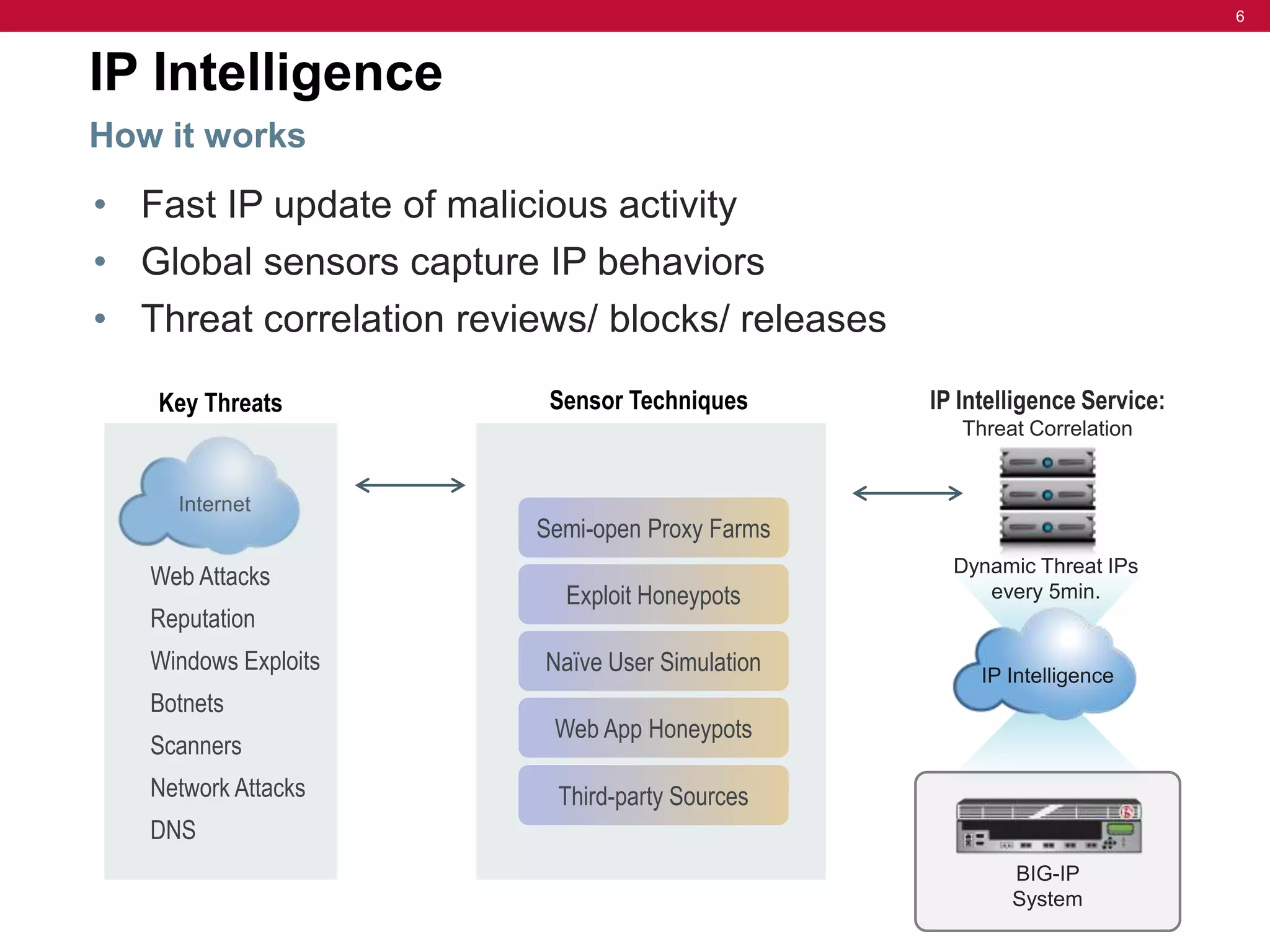
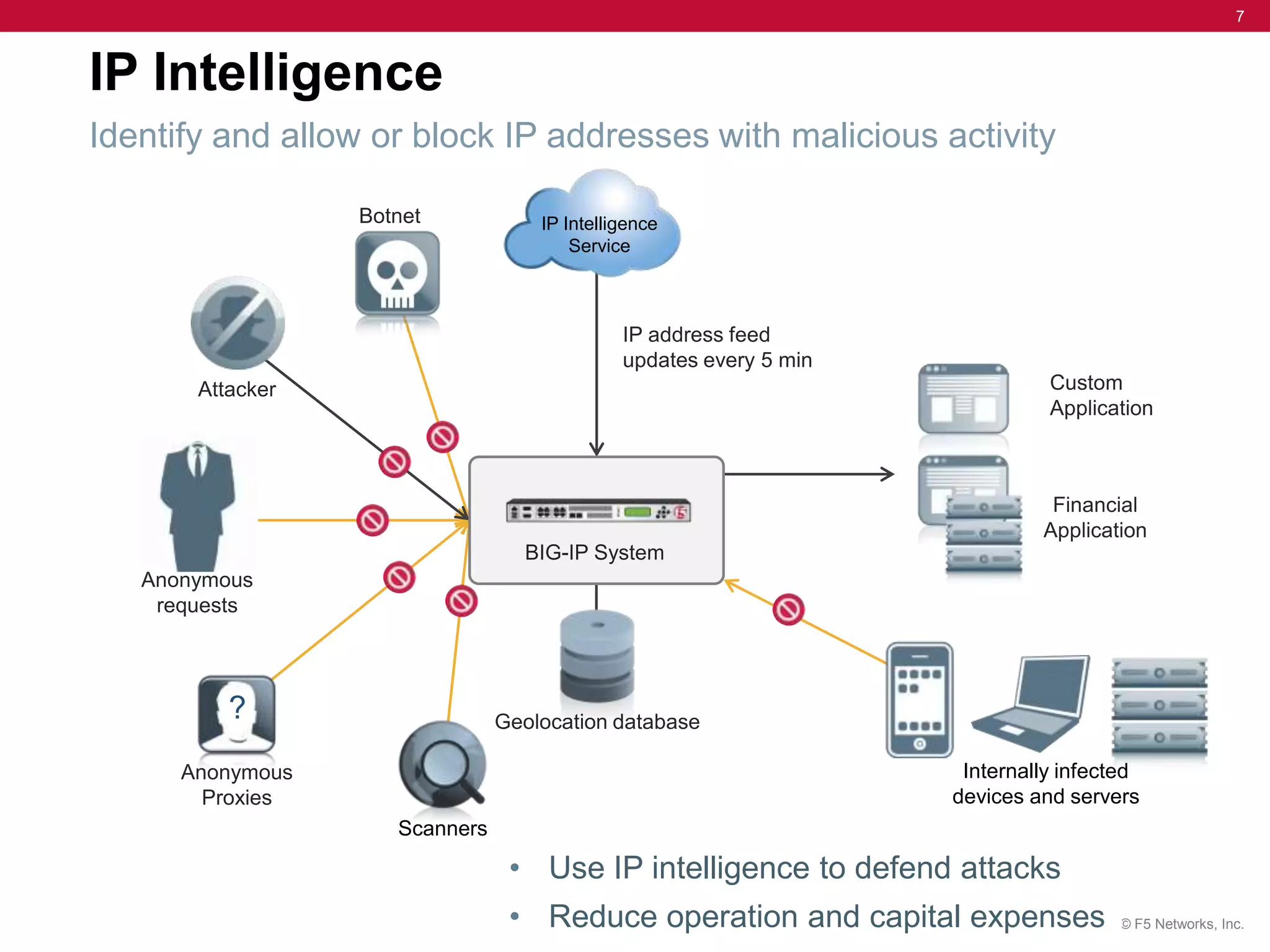
The document discusses the evolution of security challenges, particularly highlighting the rise of hacktivism and the need for enhanced threat detection through IP intelligence services. It emphasizes the importance of context-based delivery and protection against malicious activities, with a focus on real-time updates and leveraging a global network of sensors to track high-risk IP addresses. The service aims to improve performance and reduce network costs while providing ongoing protection from evolving cyber threats.