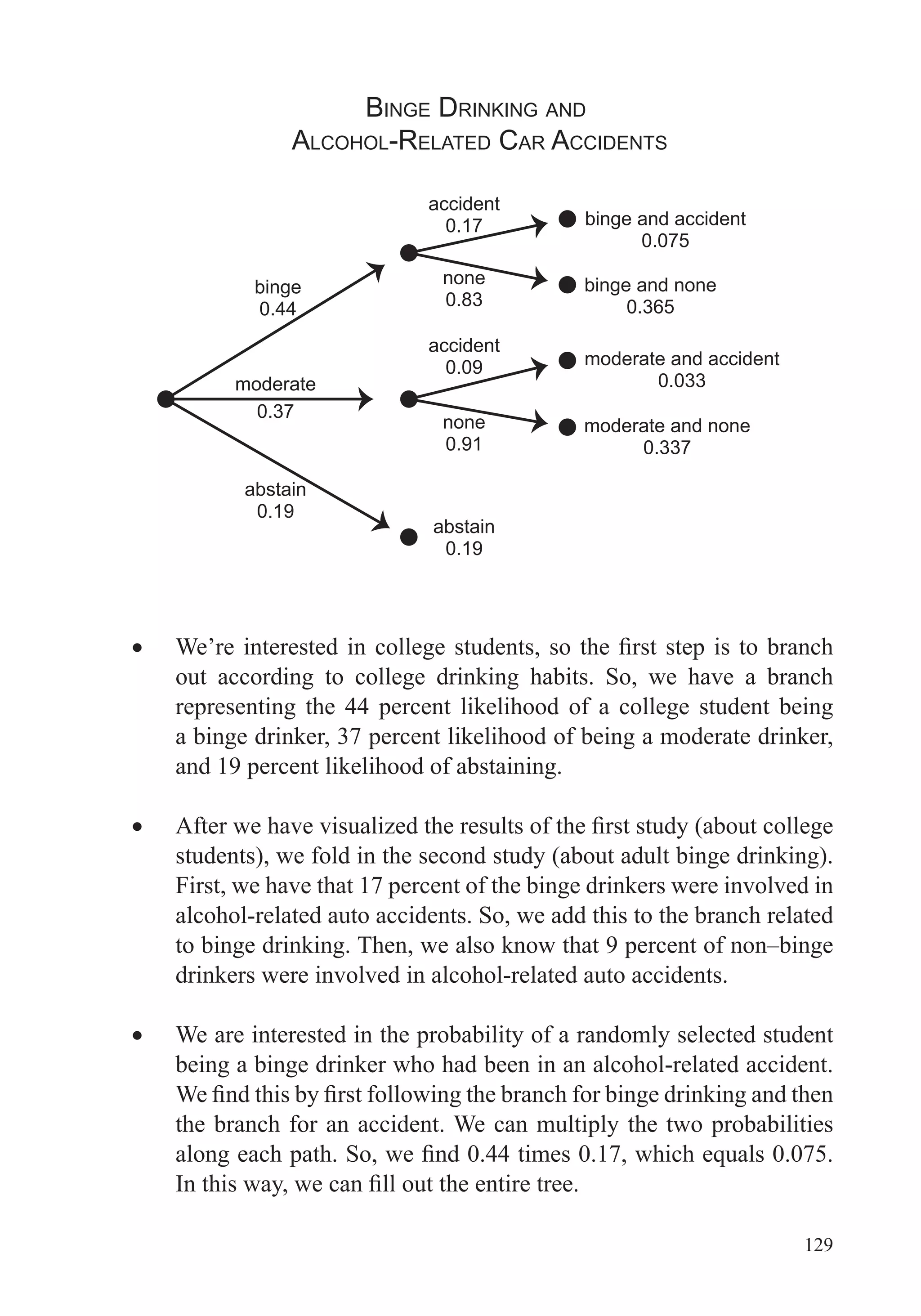
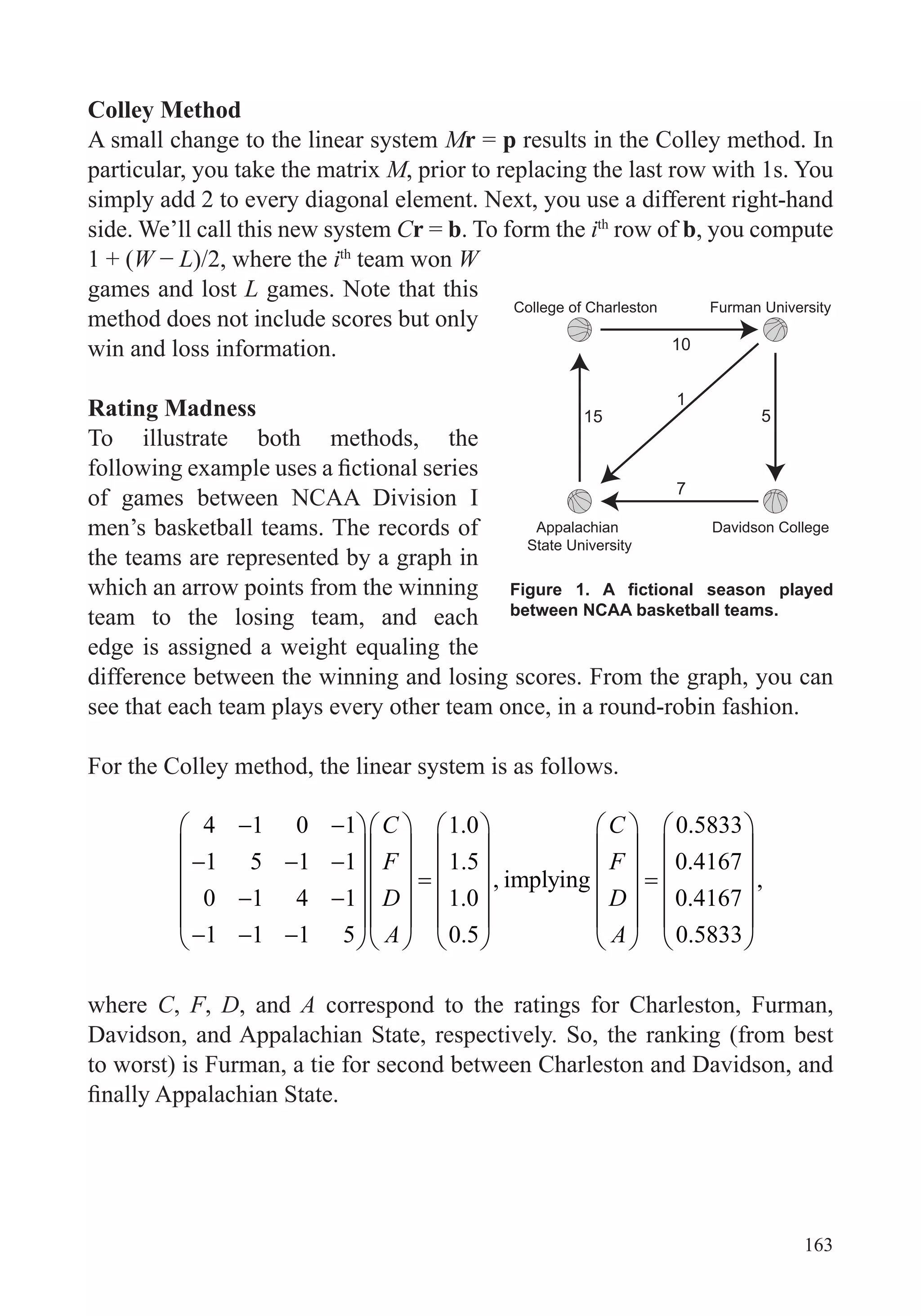
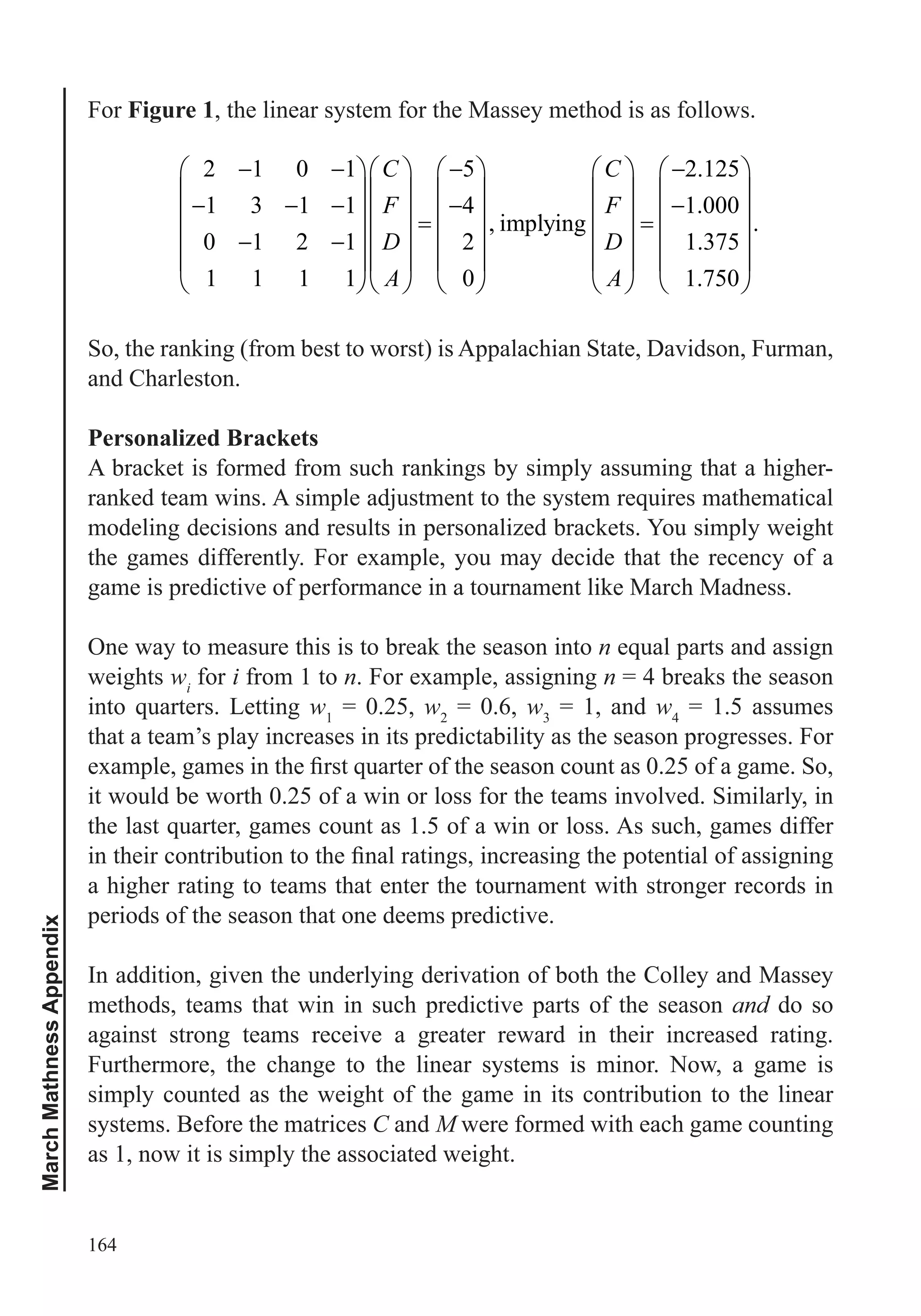
This document provides an overview of the scope and topics that will be covered in the course "Big Data: How Data Analytics Is Transforming the World". The course will demonstrate how various organizations are using new types of data and analytical tools to improve operations. It will cover important data analysis tools and techniques, including graphing data, data preparation, regression, anomaly detection, simulation, clustering, and network analysis. A variety of case studies will illustrate how these different methods have been applied successfully. The goal is to help learners understand the data analysis process and choose appropriate tools to analyze data sets of interest.