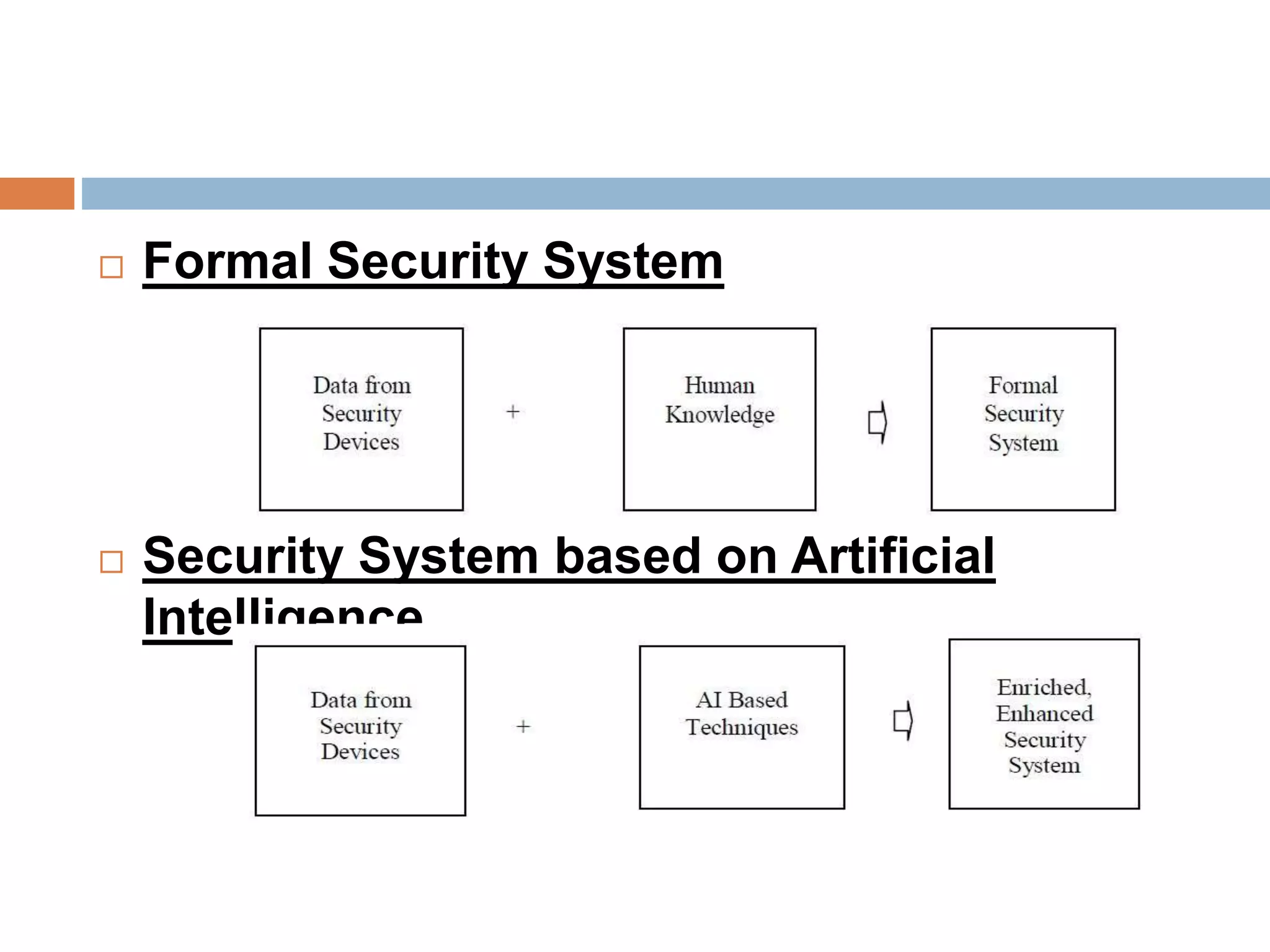
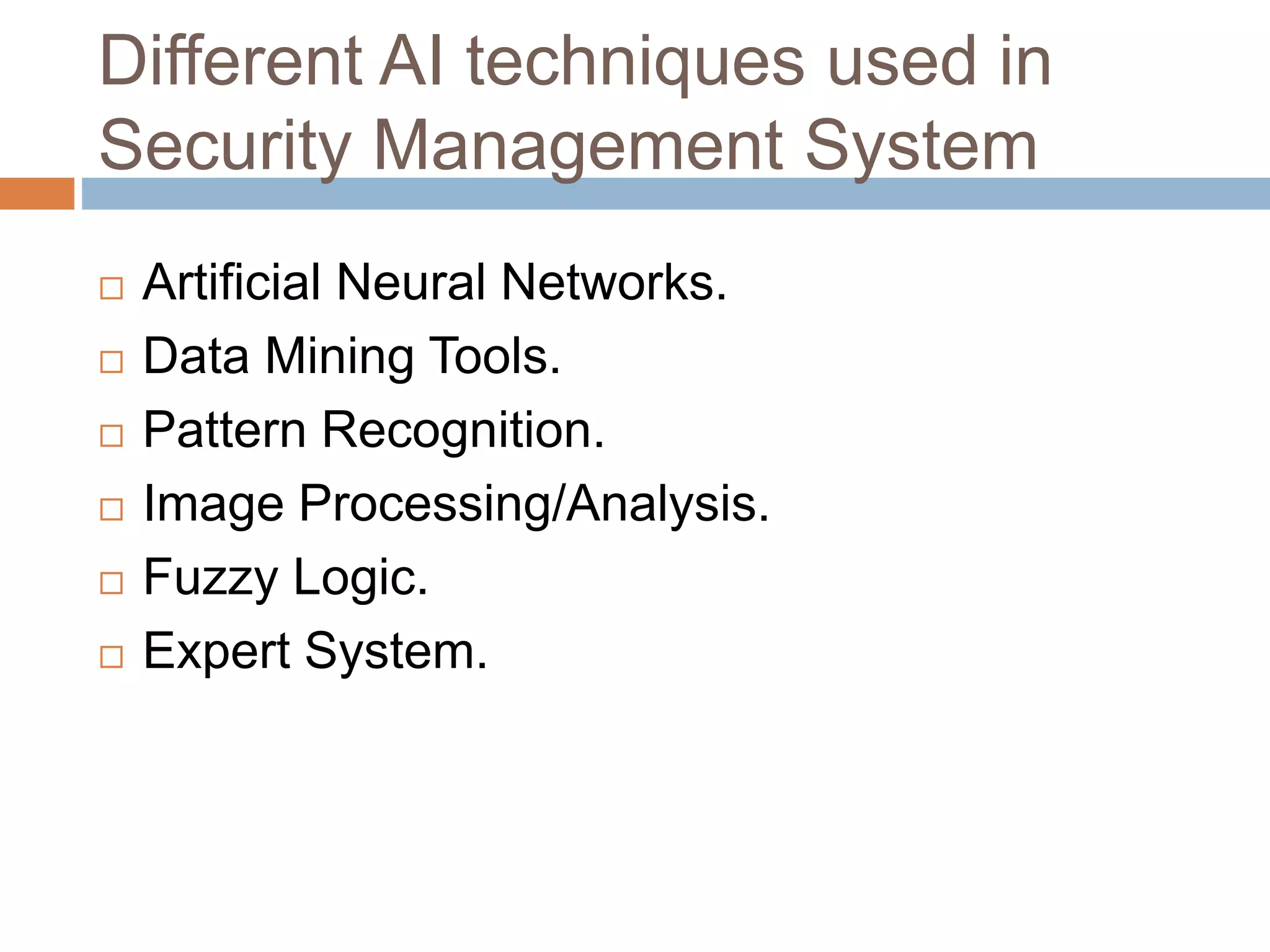
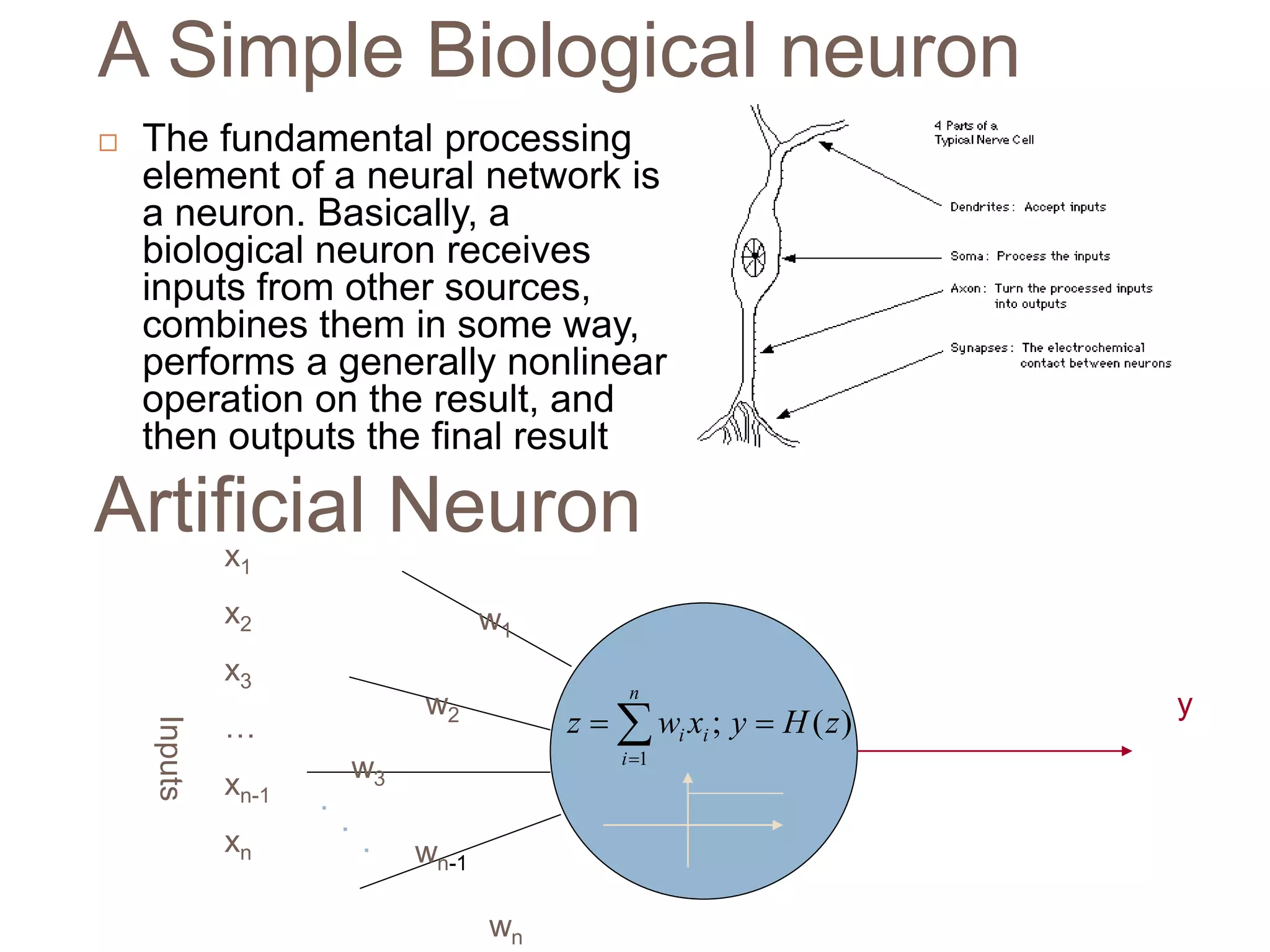
The document discusses the integration of artificial intelligence (AI) techniques in security management, highlighting AI's ability to enhance security systems by compensating for human limitations in processing information. Various AI techniques such as artificial neural networks, data mining, and fuzzy logic are explored for their applications in improving security measures like intrusion detection and cyber security. It concludes that AI can significantly improve security system performance, reduce manpower requirements, and provide proactive threat alerts.

![What is
Artificial Intelligence[AI]…???
The artificial intelligence is the process in which
machine can act like a human
AI techniques gives rise to important applications
where human processing ability weakens
Some of the field where AI is massively used are
Military, Antiterrorism, Automobile Industry,
Internet Search Engines and Robotics, Speech
recognition, Expert & fuzzy system etc.,
The central goals of AI research
include reasoning, knowledge, planning, learning,
natural language processing
(communication),perception and the ability to
move and manipulate objects.
General intelligence is still among the field's long-
term goals.](https://image.slidesharecdn.com/artificialintelligenceinsecuritymgmt-170821170132/75/BE-EEE-8th-sem-Presentation-Artificial-intelligence-in-security-managenent-2-2048.jpg)