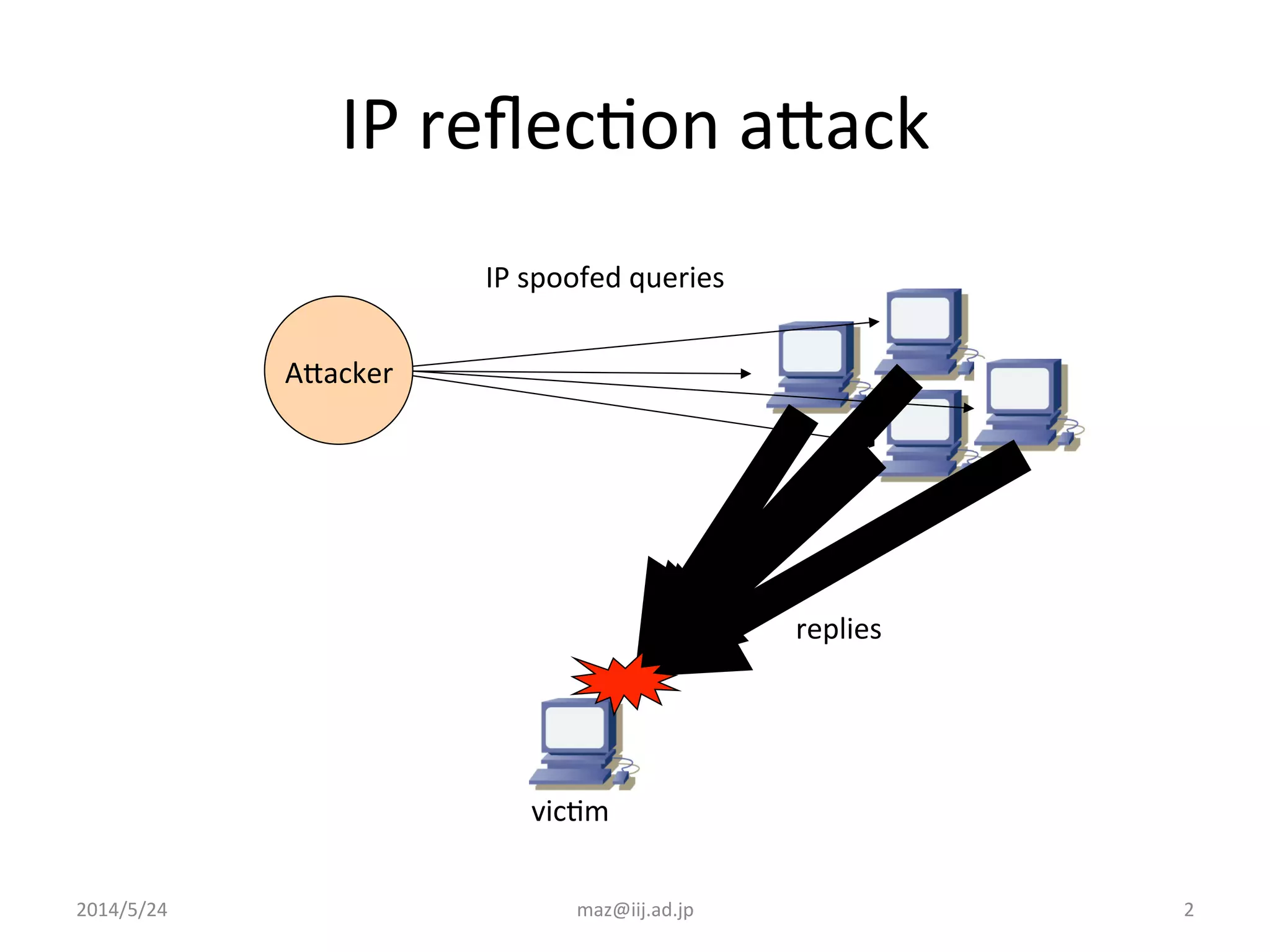
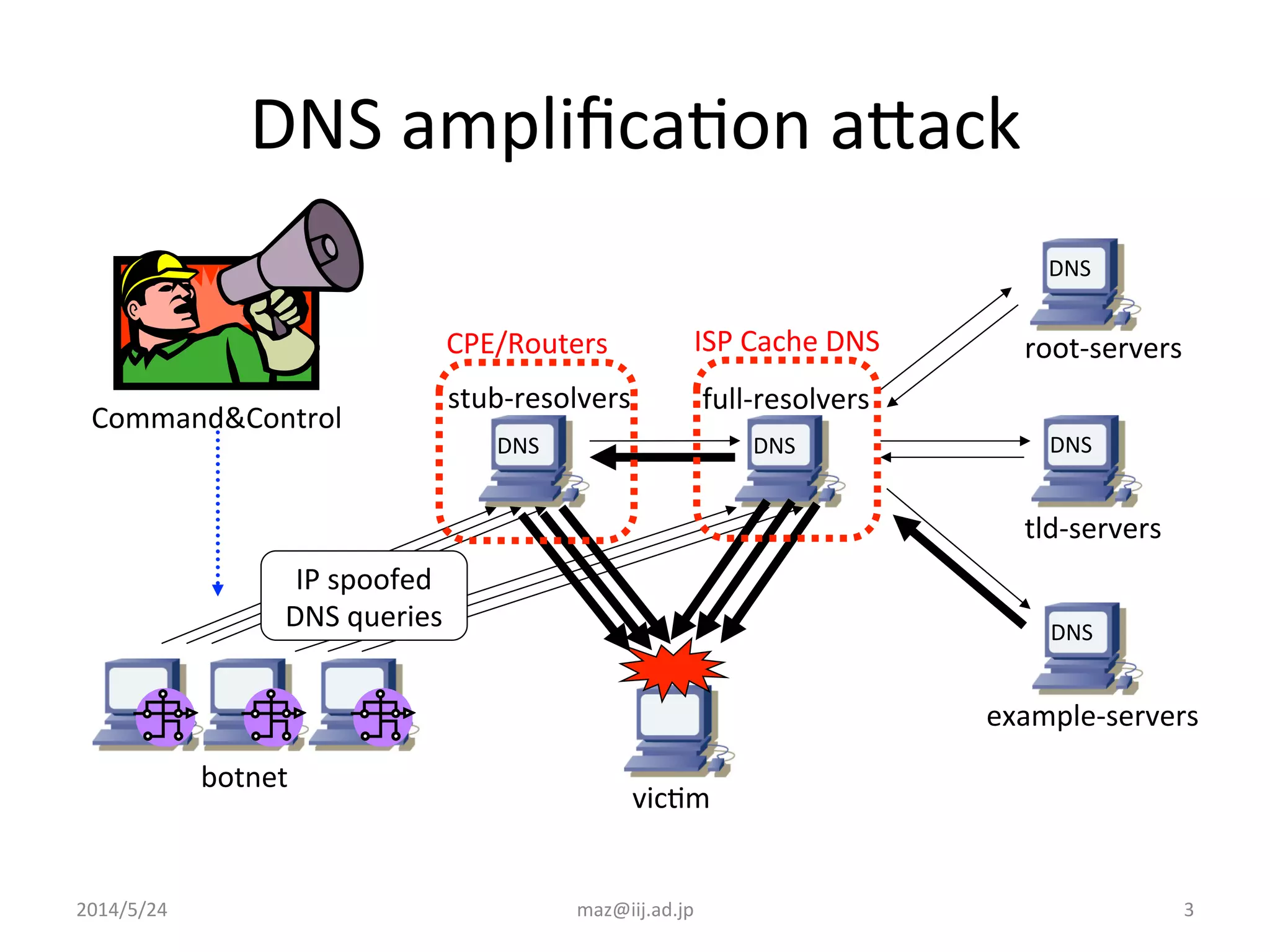
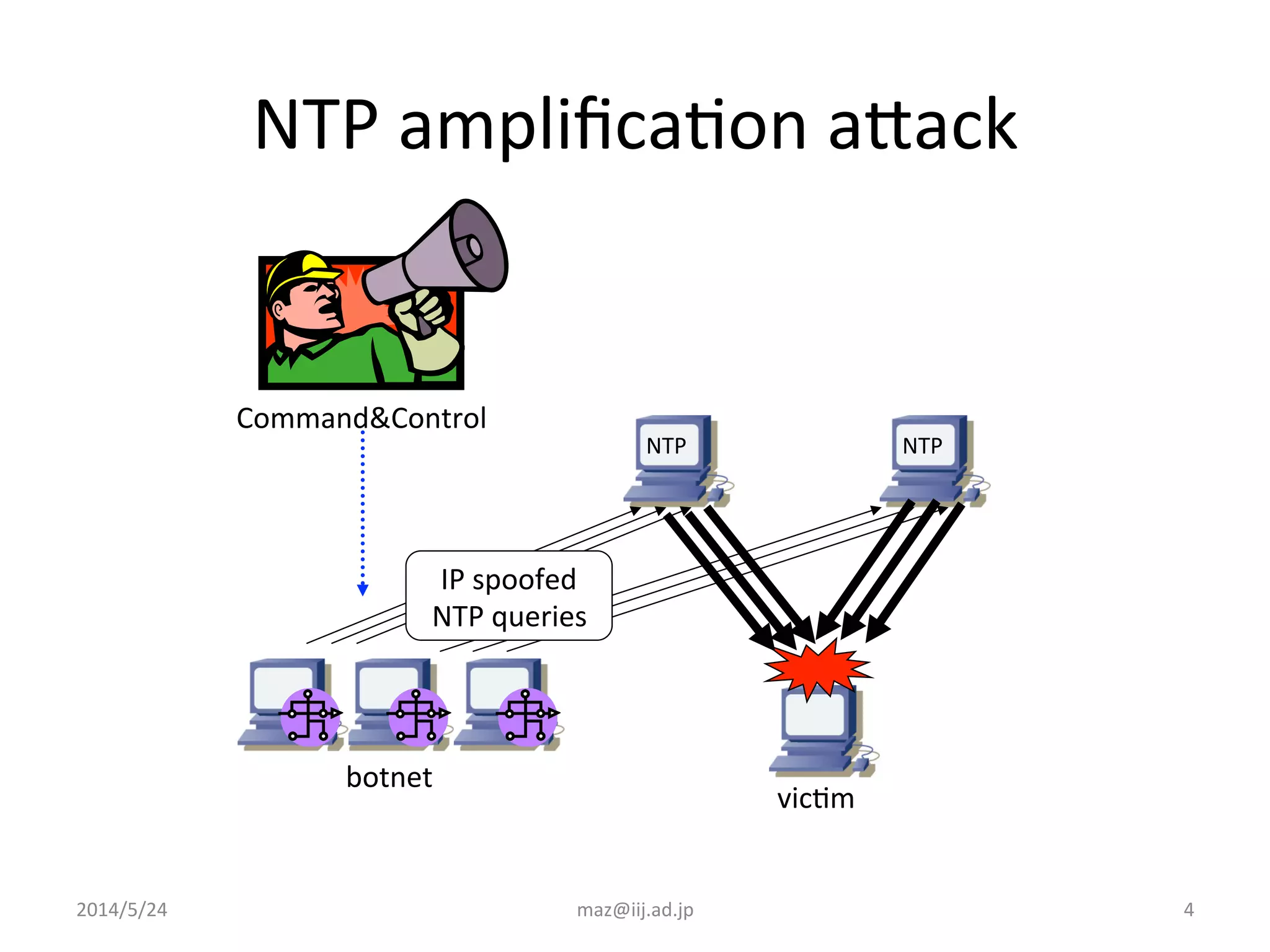
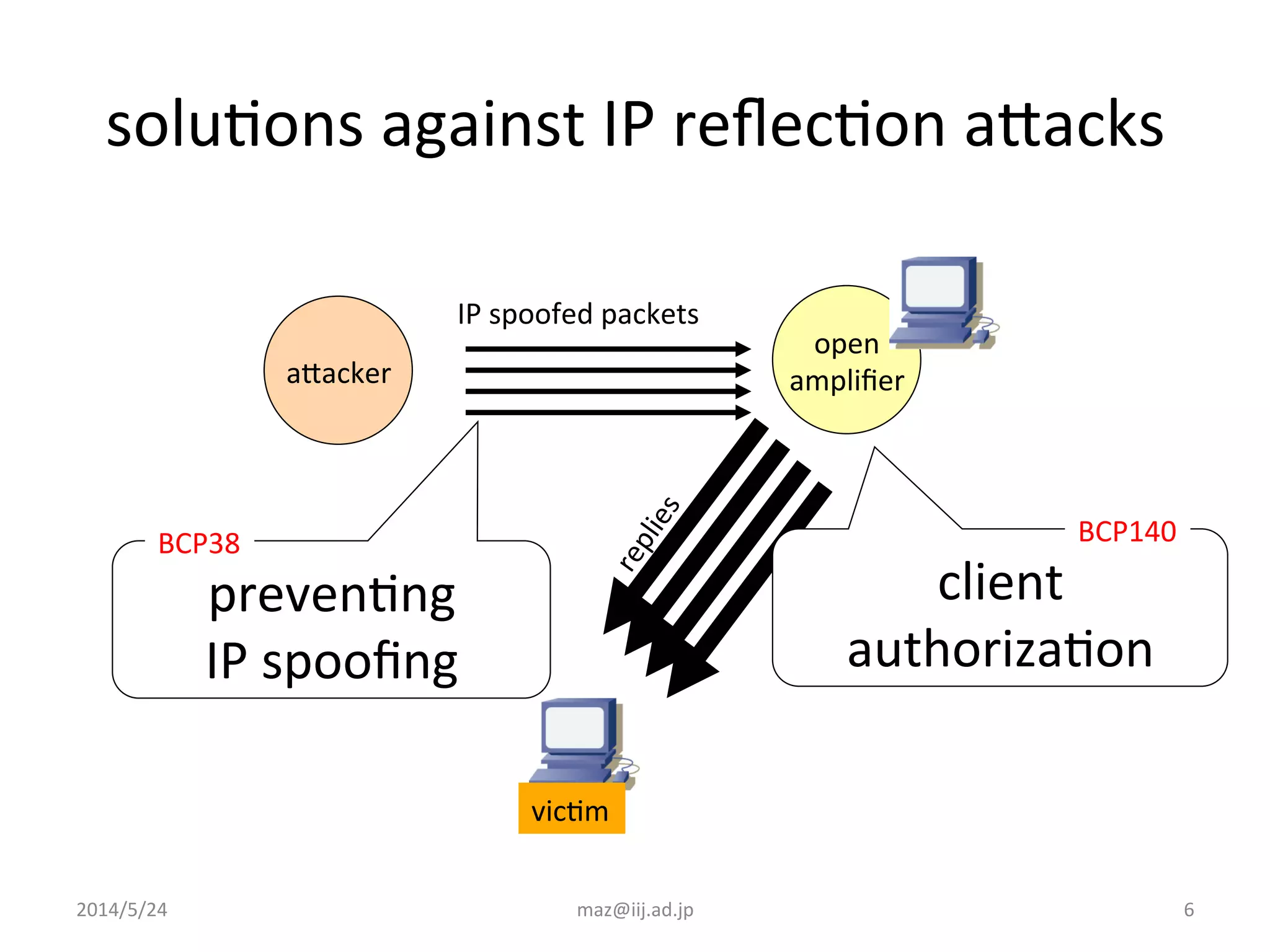
The document discusses various techniques that internet service providers can use to prevent IP reflection attacks, including:
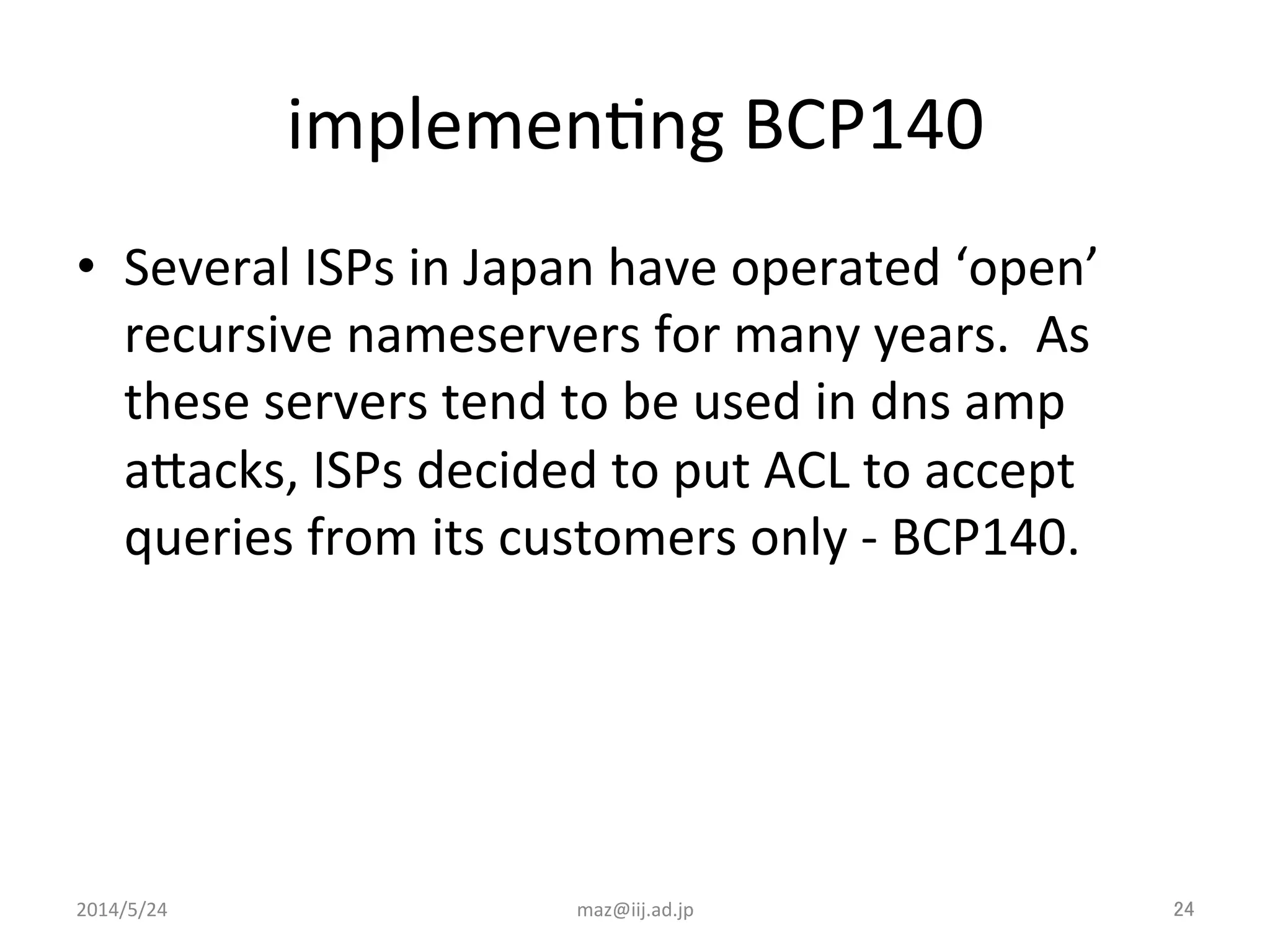
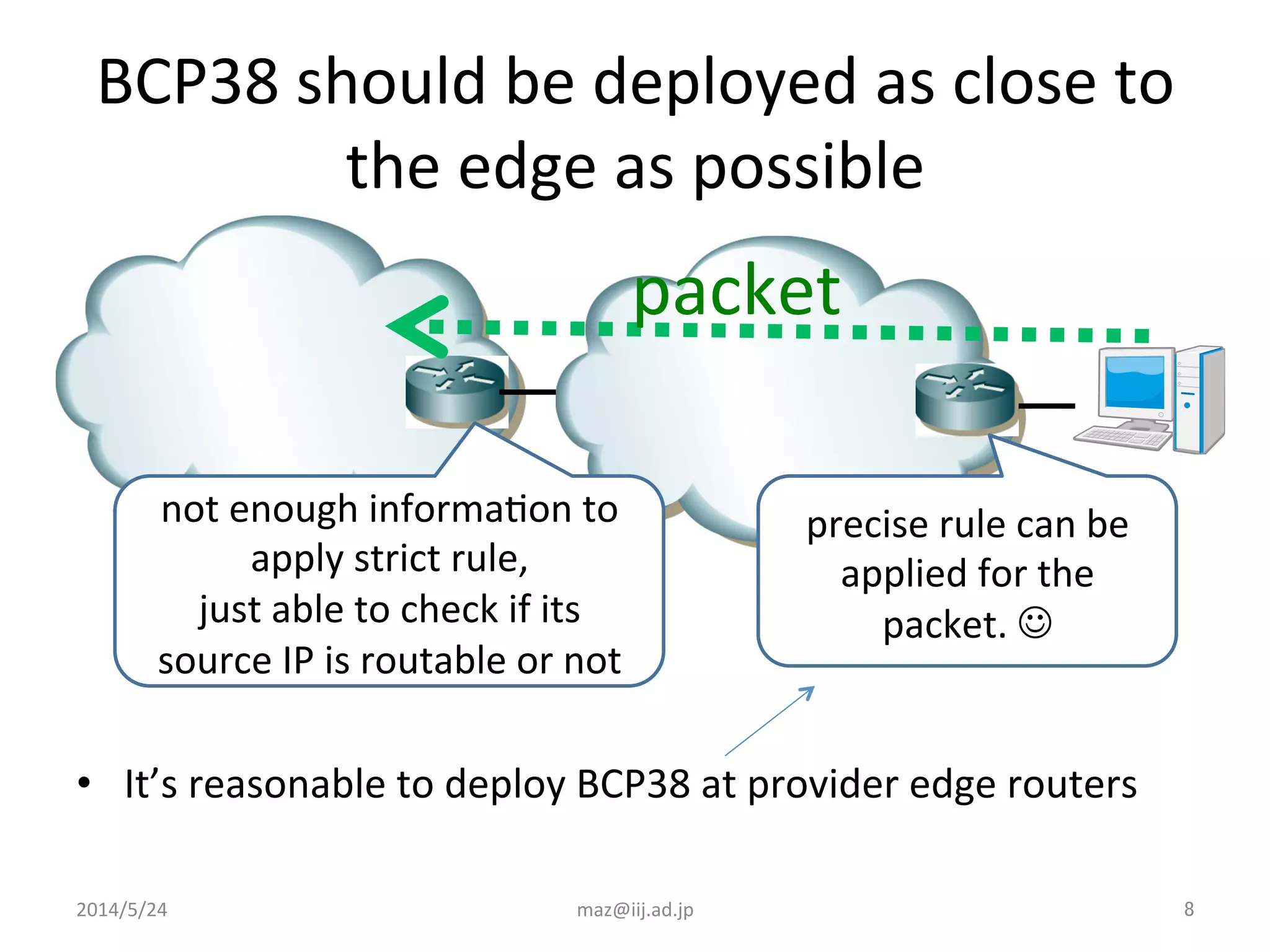
- Implementing BCP38 and BCP140, which involve validating the source IP address of incoming packets to prevent spoofing. This is recommended to be deployed as close to the edge of the network as possible.
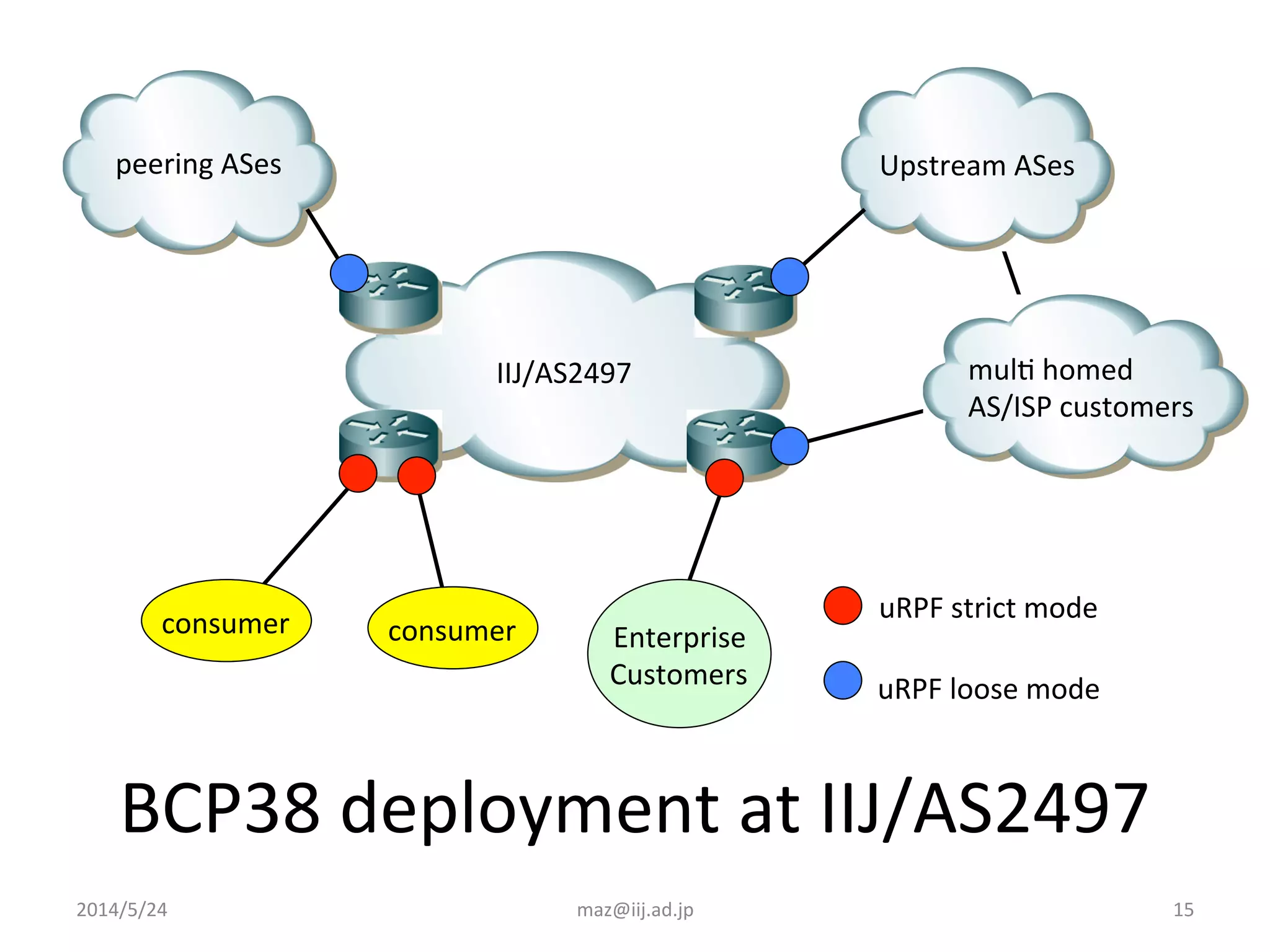
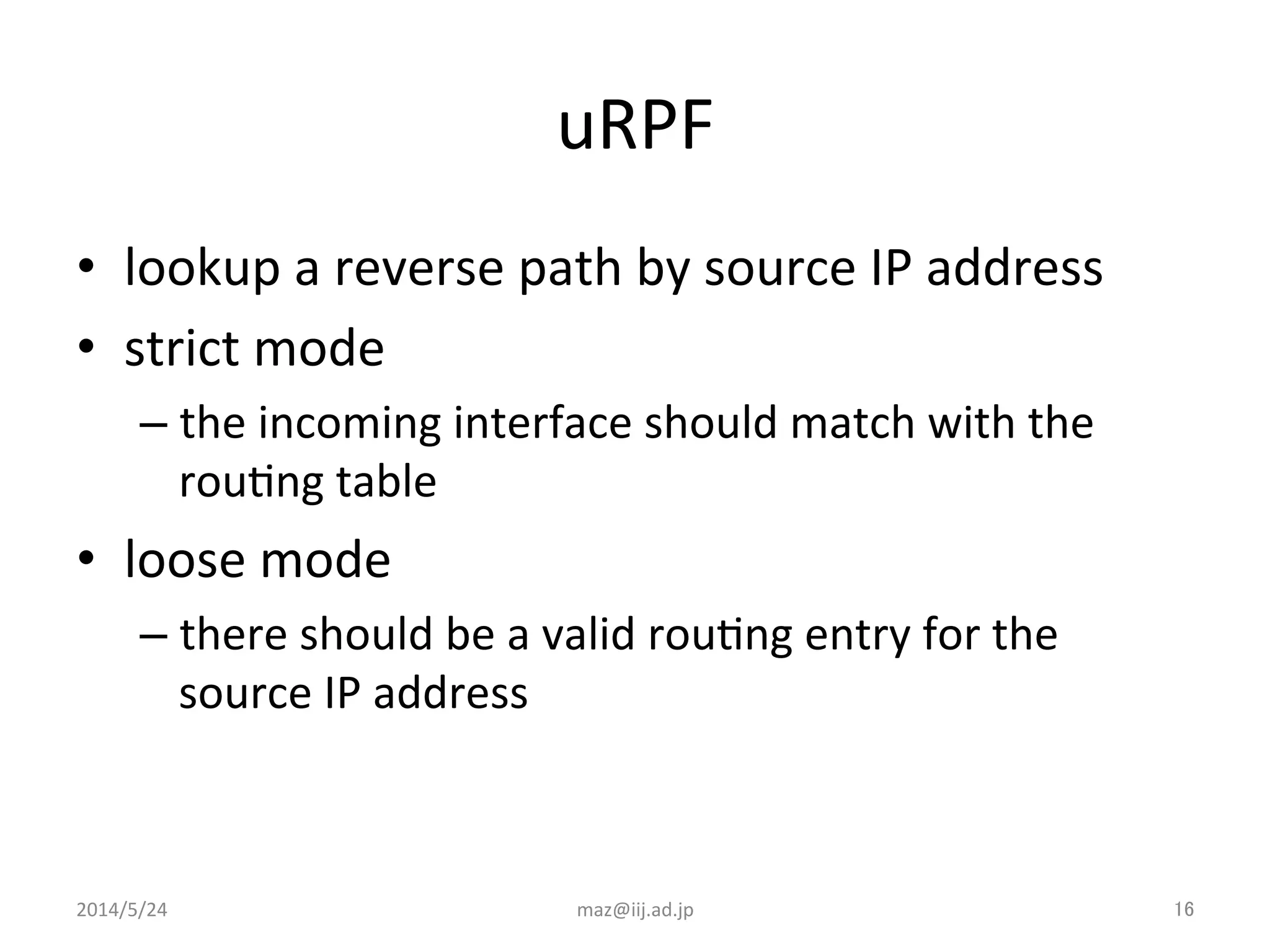
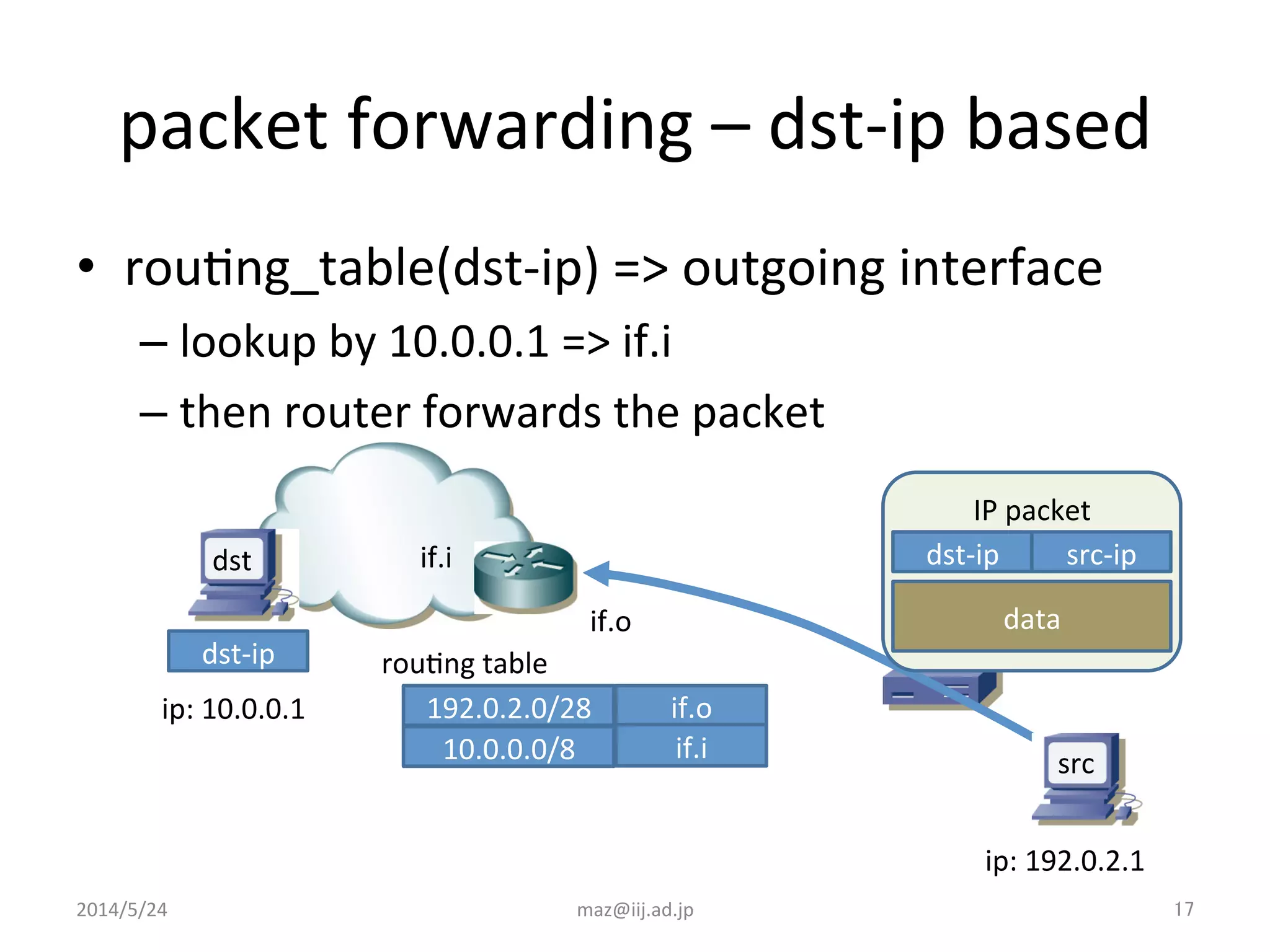
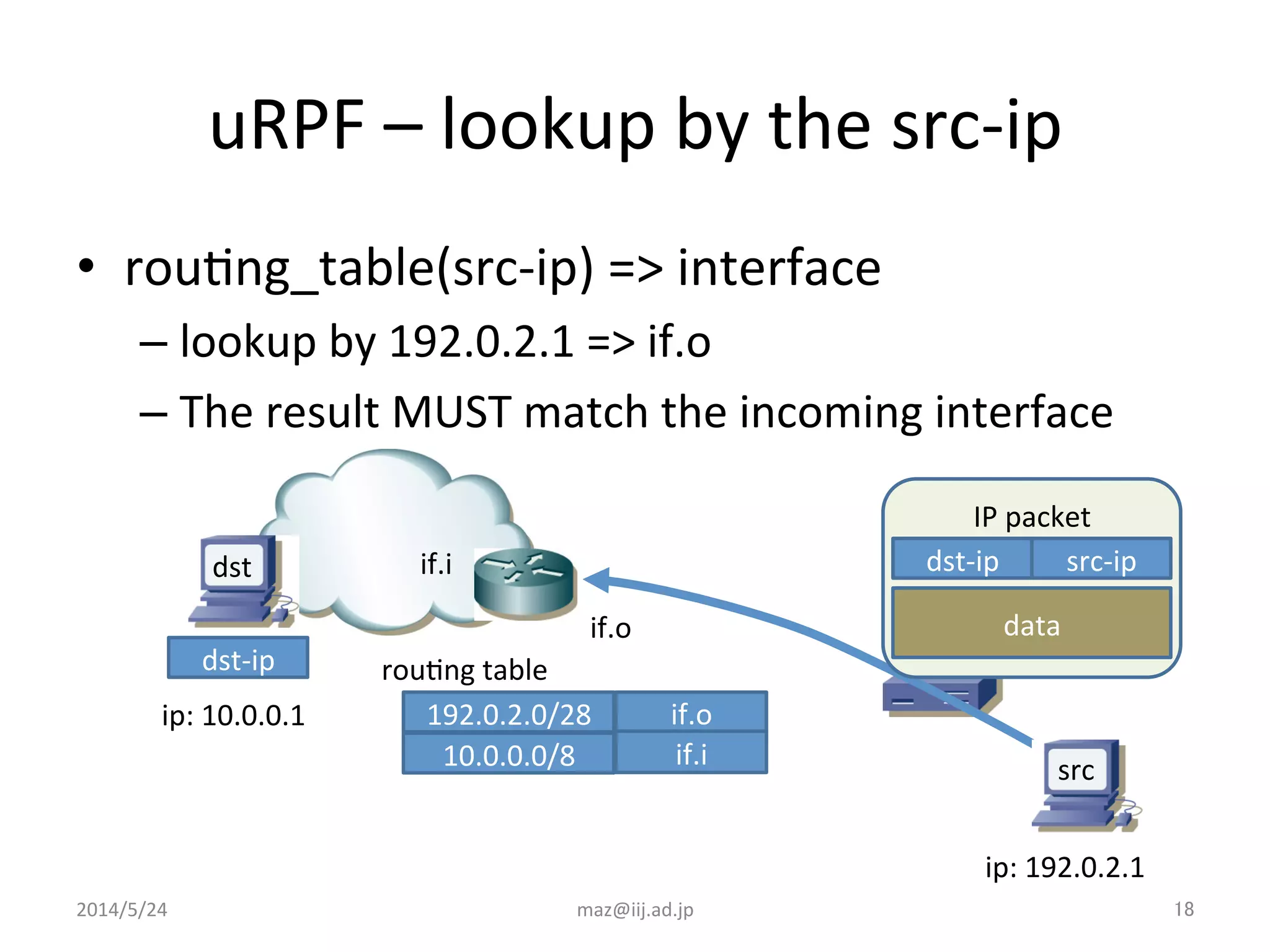
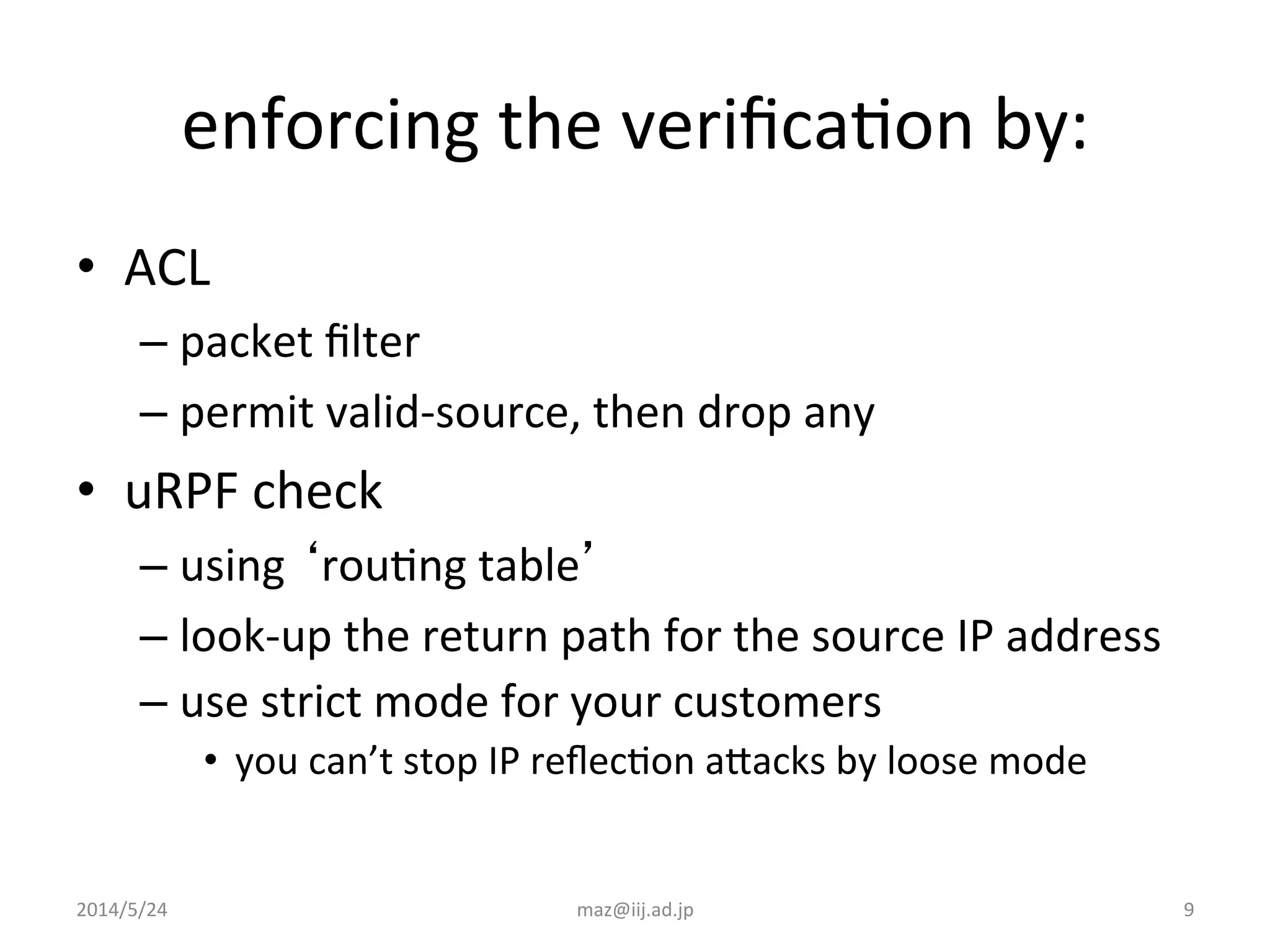
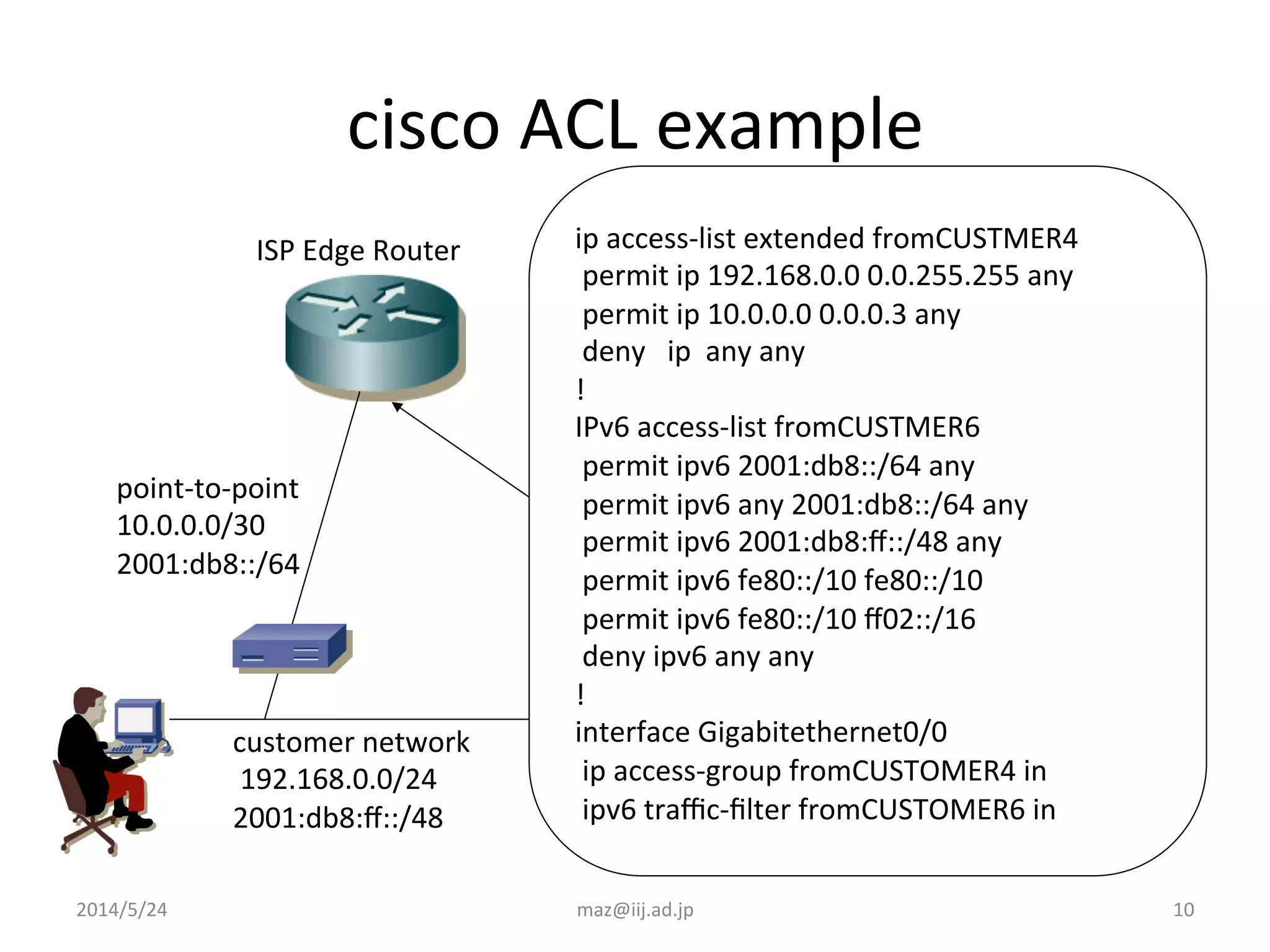
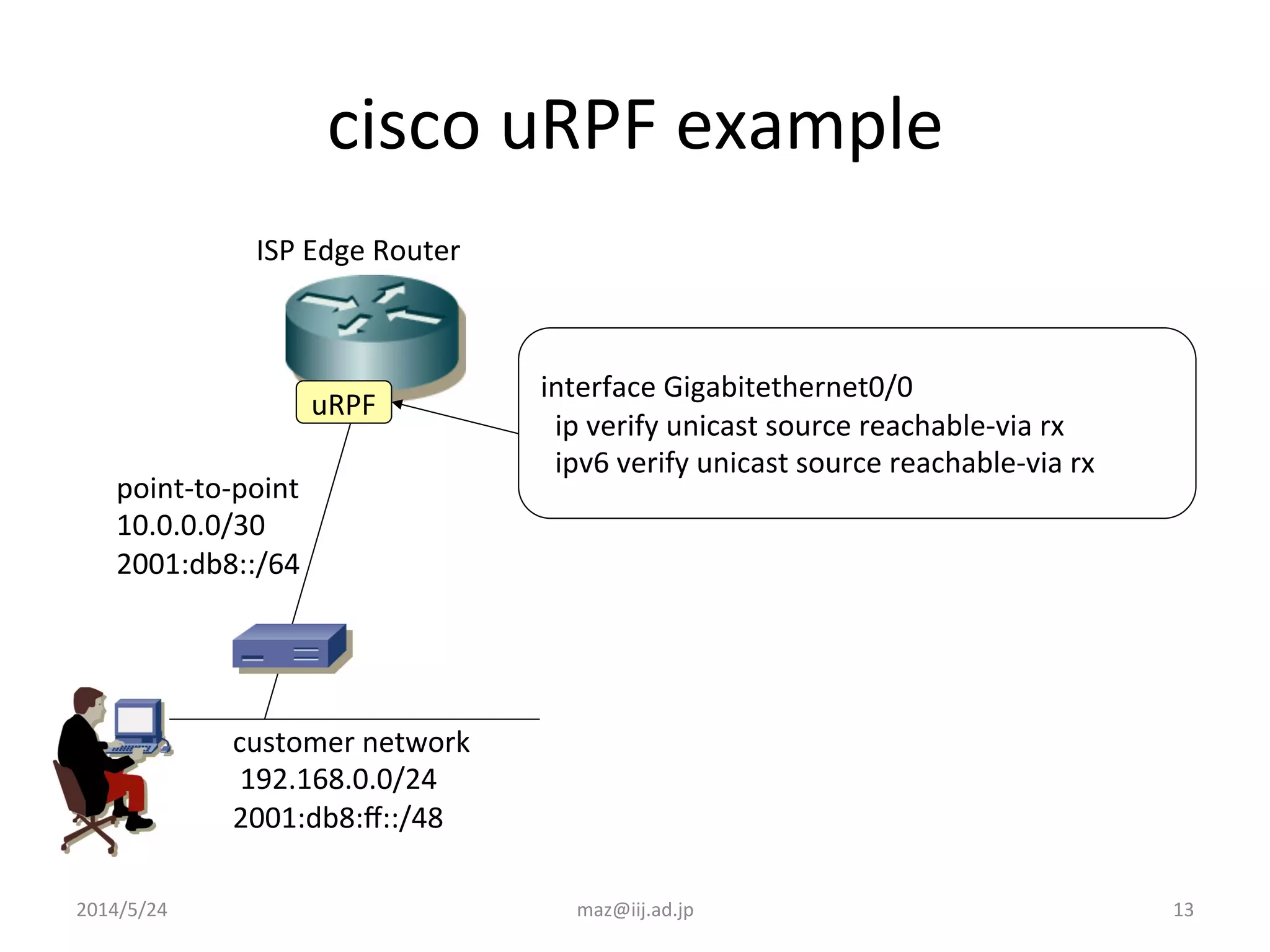
- Enforcing validation using access control lists (ACLs) to filter packets and unicast reverse path forwarding (uRPF) to check the return path of source IP addresses. Strict uRPF is recommended for customers.
- Example ACL and uRPF configurations are provided for Cisco and Juniper routers to filter traffic from customer networks connected to the ISP edge router.



![11
juniper
IPv4
ACL
example
firewall
family
inet
{
filter
fromCUSTOMER4
{
term
CUSTOMER4
{
from
source-‐address
{
192.168.0.0/16;
10.0.0.0/30;
}
then
accept;
}
term
Default
{
then
discard;
}}}
[edit
interface
ge-‐0/0/0
unit
0
family
inet]
filter
{
input
fromCUSTOMER;
}
customer
network
192.168.0.0/24
2001:db8:ff::/48
point-‐to-‐point
10.0.0.0/30
2001:db8::/64
ISP
Edge
Router
2014/5/24
maz@iij.ad.jp](https://image.slidesharecdn.com/bdnog1-maz-bcp38-bcp140-151103173446-lva1-app6891/75/Network-Security-Best-Practice-BCP38-140-11-2048.jpg)
![12
juniper
IPv6
ACL
example
firewall
family
inet6
{
filter
fromCUSTOMER6
{
term
CUSTOMER6
{
from
source-‐address
{
2001:db8::/64;
2001:db8:ff::/48;
}
then
accept;
}
term
LINKLOCAL
{
from
source-‐address
{
fe80::/10;
}
desInaIon-‐address
{
fe80::/10;
ff02::/16;
}
then
accept;
}
term
Default
{
then
discard;
}}}
[edit
interface
ge-‐0/0/0
unit
0
family
inet6]
filter
{
input
fromCUSTOMER6;
}
customer
network
192.168.0.0/24
2001:db8:ff::/48
point-‐to-‐point
10.0.0.0/30
2001:db8::/64
ISP
Edge
Router
2014/5/24
maz@iij.ad.jp](https://image.slidesharecdn.com/bdnog1-maz-bcp38-bcp140-151103173446-lva1-app6891/75/Network-Security-Best-Practice-BCP38-140-12-2048.jpg)
![14
juniper
uRPF
example
[edit
interface
ge-‐0/0/0
unit
0]
family
inet
{
rpf-‐check;
}
family
inet6
{
rpf-‐check;
}
uRPF
customer
network
192.168.0.0/24
2001:db8:ff::/48
point-‐to-‐point
10.0.0.0/30
2001:db8::/64
ISP
Edge
Router
2014/5/24
maz@iij.ad.jp](https://image.slidesharecdn.com/bdnog1-maz-bcp38-bcp140-151103173446-lva1-app6891/75/Network-Security-Best-Practice-BCP38-140-14-2048.jpg)