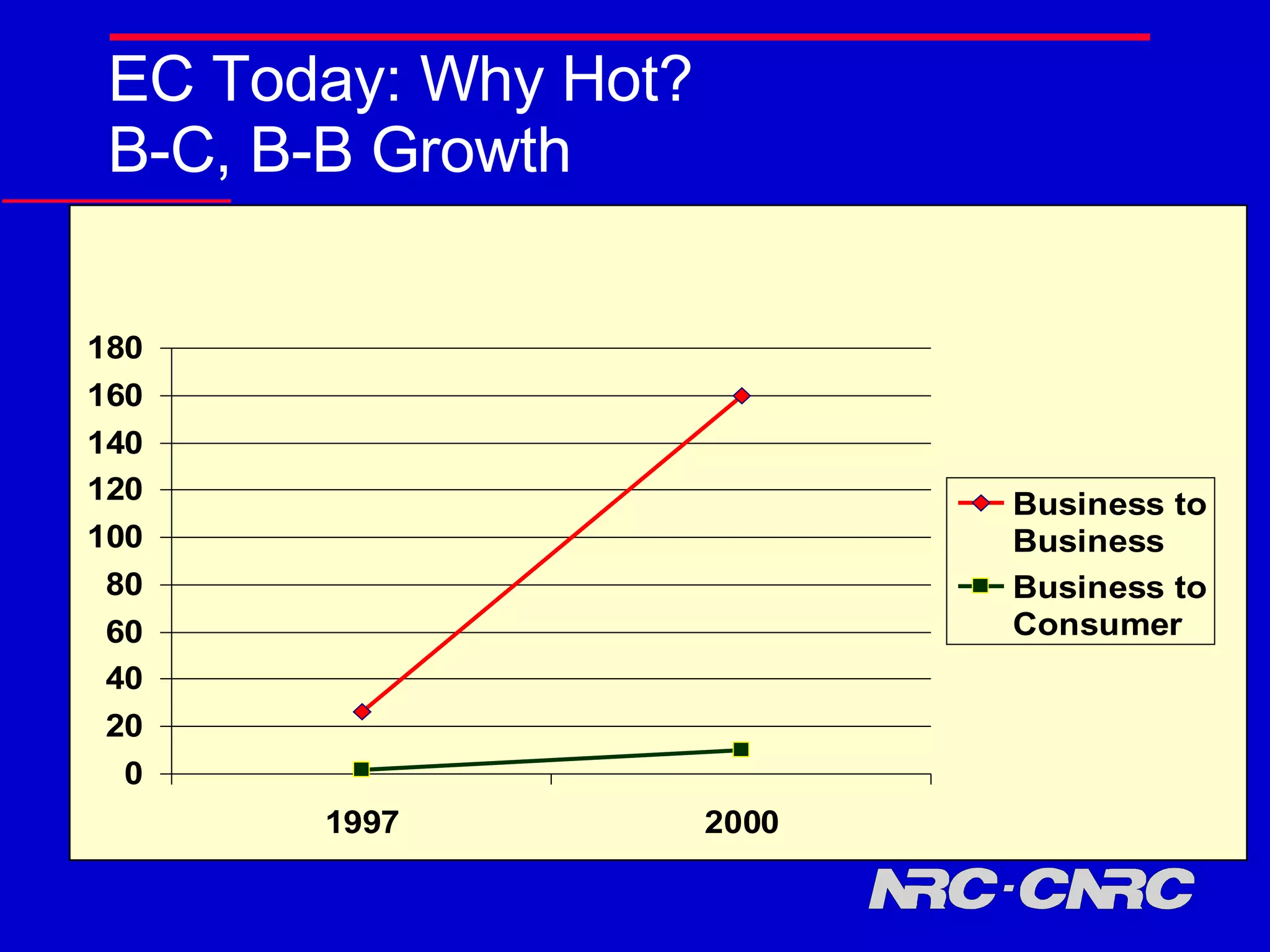
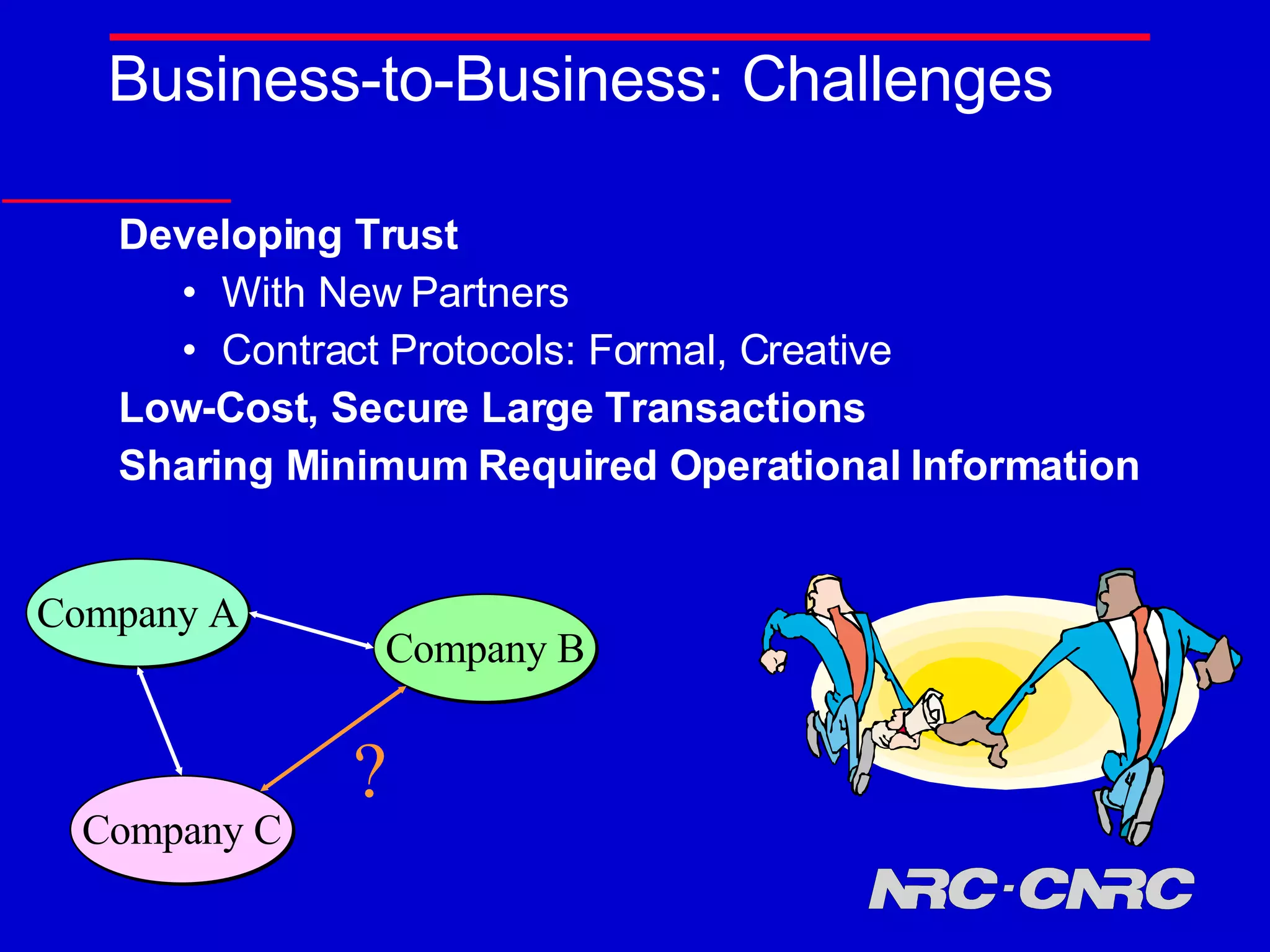
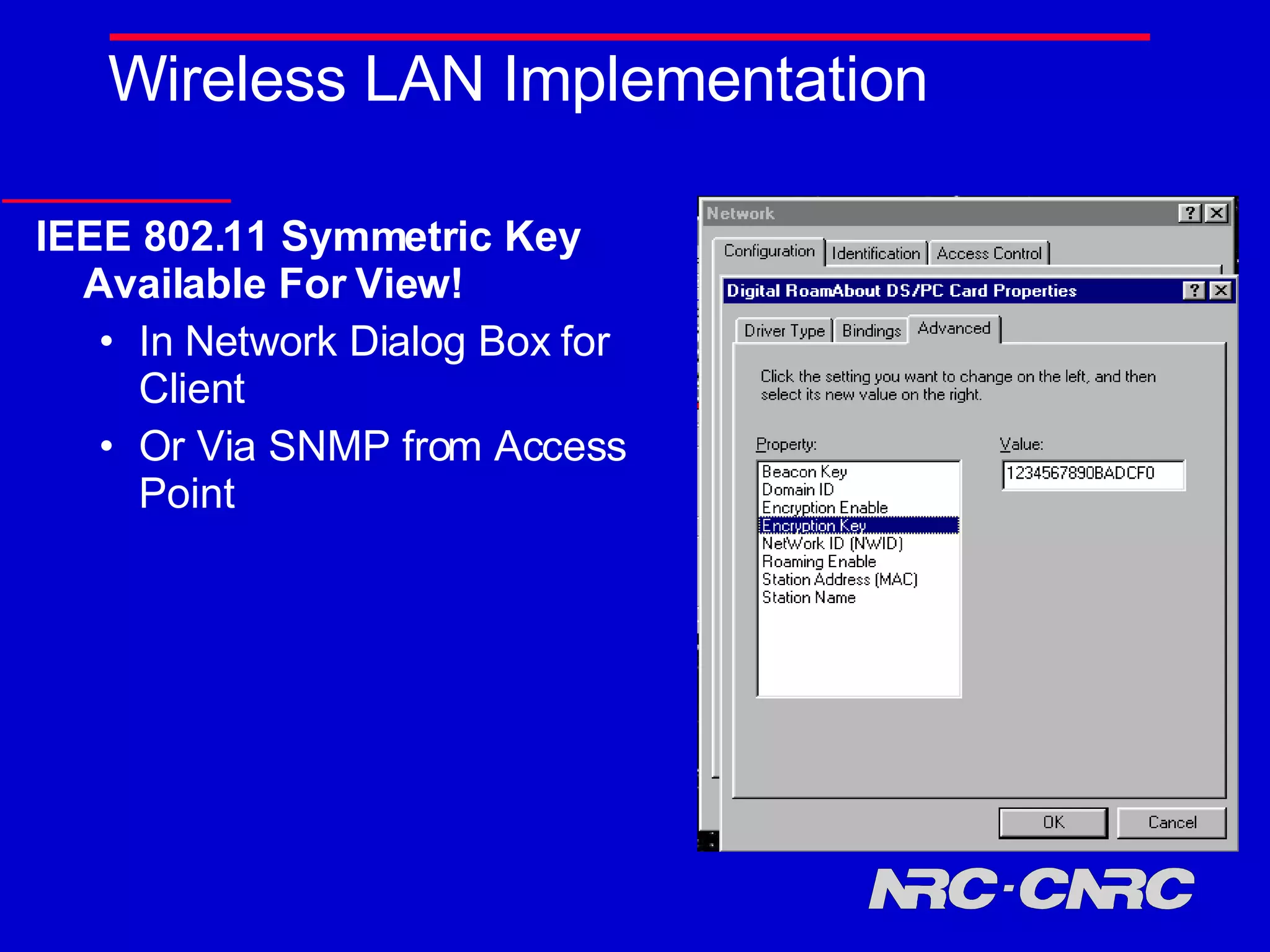
E-commerce is thriving but faces many challenges. Standardization, trust, business-to-business transactions, and intellectual property protection present open research questions. As e-commerce expands to new areas like wireless and agent-based systems, additional challenges arise regarding security, privacy, and establishing trust in new environments and between new parties. Continued research aims to address these challenges and further innovation in electronic commerce.
![E-Commerce: Hype, Hope… Help Needed Larry Korba National Research Council of Canada [email_address] http://www.iit.nrc.ca National Research Council Canada Conseil national de recherches Canada Institute for Institut de technologie Information Technology de l'information C a n a d a](https://image.slidesharecdn.com/bhkorba-1226684091258267-8/75/B-Hkorba-1-2048.jpg)




























![Summary (Continued) Secure E-Commerce Everywhere Portable Electronic Wallet Biometry E-Commerce Agents Trust and Privacy Agent Mobility Room for Innovation Resource Page: http://132.246.128.180/ecommerce/ecomlinks.html Email Address: [email_address]](https://image.slidesharecdn.com/bhkorba-1226684091258267-8/75/B-Hkorba-36-2048.jpg)