This document provides an overview of Amazon Web Services (AWS) CloudFormation. It discusses CloudFormation as a method to create and manage collections of AWS resources using JSON template files, often described as "infrastructure as code." The document outlines the structure and syntax of CloudFormation templates, including template versions, parameters, mappings, resources, outputs, and intrinsic functions. It also discusses CloudFormation helper scripts like cfn-init and cfn-signal that are used to deploy resources defined in templates.


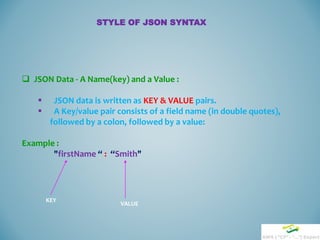
![STYLE OF JSON SYNTAX
JSON syntax is a subset of the JavaScript object notation syntax:
Data is in Key/value pairs : “Key” : “Value”
Data is separated by commas : “data1”, “data2”
Curly braces hold objects : { … }
Square brackets hold arrays : [ … ]](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-3-320.jpg)

![ JSON Arrays
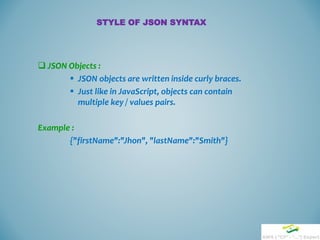
JSON arrays are written inside square brackets.
Just like in JavaScript, an array can contain multiple objects.
Example:
"employees":[
{"firstName":"John", "lastName":"Doe"},
{"firstName":"Anna", "lastName":"Smith"},
{"firstName":"Peter", "lastName":"Jones"}
]
STYLE OF JSON SYNTAX](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-7-320.jpg)
![{
"Title" : "The Daughter Of Time",
"Author" : "Josephine Tey",
"Genre" : " Crime, Thrillers & Mystery ",
"Detail" : {
"Publisher" : " Simon & Schuster ",
"Publication_Year" : 2009 ,
"ISBN" : “0-684-80386-0",
“Language" : "English",
"Pages" : 999
},
"Price" : [
{
"type" :"Hardcover",
"price" : "17.99"
},
{
"type" : "Kindle Edition",
"price" : "5.22"
}
]
}
Json Script Example
Main Object Starts
Nested Object Starts
Nested Object Starts
First Sub Object Starts
First Sub Object Ends
Main Object Ends
Nested Object Ends
Nested Object Ends
Array Starts (second object as array)
Array Ends
Value: String
Value : Number
No comma (, ) after last value](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-8-320.jpg)
![ Cloud Formation uses Json scripting style & syntax.
Objects are wrapped within '{' and '}‘.
Arrays are enclosed by '[' and ']'.
Objects are list of key & Value pairs.
Arrays are list of values.
Both objects and arrays can be nested.
strings, numbers, booleans (i.e true and false) and null
can be used as values.
CLOUD-FORMATION SYNTAX](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-9-320.jpg)
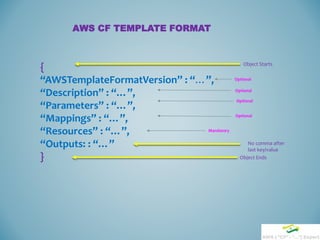


![EXAMPLE OF CLOUD-FORMATION BLOCK
{
“AWSTemplateFormatVersion” : “2010-09-09”,
“Description” : ”This is a test template”
“Parameters” : {
“Customer” : {
“Description” : “Name of the customer”,
“Type” : “String”,
“Default” : “claro”,
“AllowedValues” : [“claro”,”tyco”, “qpass”]
}
}
}
Static/fixed
Name
Variable/Cus
tomizable
Name
Optional
Optional
Optional](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-13-320.jpg)
![EXAMPLE OF CLOUD-FORMATION BLOCK
{
"Mappings" : {
“MyRegionMap" : {
"us-east-1" : {
"AMI" : "ami-76f0061f“ },
"us-west-1" : {
"AMI" : "ami-655a0a20“ },
"eu-west-1" : {
"AMI" : "ami-7fd4e10b“ },
}
}
},
"Resources" : {
"Ec2Instance" : {
"Type" : "AWS::EC2::Instance",
"Properties" : {
"KeyName" : "MyKey",
"ImageId" : { "Fn::FindInMap" : [ “MyRegionMap", { "Ref" :
"AWS::Region" }, "AMI" ]}
}
}
},
“Outputs” : { }
}
Static Name
Static Name
Static Name
First Key
Second Name
User Defined Name
User Defined Name](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-14-320.jpg)

![{
"AWSTemplateFormatVersion" : "2010-09-09",
"Description" : "Ec2 block device mapping",
"Resources" : {
"MyEC2Instance" : {
"Type" : "AWS::EC2::Instance",
"Properties" : {
"ImageId" : "ami-79fd7eee",
"KeyName" : "testkey",
"BlockDeviceMappings" : [
{
"DeviceName" : "/dev/sdm",
"Ebs" : {
"VolumeType" : “gp2",
"Iops" : "200",
"DeleteOnTermination" : "false",
"VolumeSize" : "20“ }
}
]
}
}
}
}
Resource
Type
Resource
Property Block
Resource
Attributes](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-16-320.jpg)
![How Do I know all AWS Resource names, Resource Types,
Resource Attributes ?
Amazon online link :
http://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/Welcome.html
And Go to “Template Reference” section.
Refer cloud-formation user guide pdf [cfn-ug.pdf]](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-17-320.jpg)
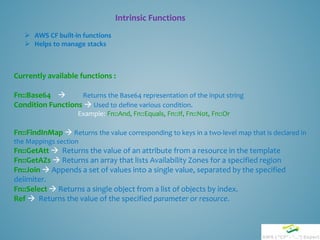
![Intrinsic Function Usage
Fn::Base64
Usage : Usually used in Userdata section
Declaration : { "Fn::Base64" : valueToEncode }
Example :
{
"MyInstance": {
"Type": "AWS::EC2::Instance",
"Metadata": {
:
},
"Properties": {
"ImageId" : "ami-12345678",
"UserData" : {
"Fn::Base64" : {
"Fn::Join" : ["", [
"#!/bin/bashn",
"/opt/aws/bin/cfn-init -s ", { "Ref" : "AWS::StackName" },
" -r MyInstance ",
" --region ", { "Ref" : "AWS::Region" }, "n",
"/opt/aws/bin/cfn-signal -e 0 --stack ", { "Ref" : "AWS::StackName" },
" --resource MyInstance n"
] ]
}
}
}
}
}](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-19-320.jpg)
![Intrinsic Function Usage
Condition Functions
Fn::And
Declaration : "Fn::And": [{condition}, {...}]
Parameters :
condition : A condition that evaluates to true or false.
Example : The following MyAndCondition evaluates to true if the referenced security group name
is equal to sg-mysggroup and if SomeOtherCondition evaluates to true:
"MyAndCondition": {
"Fn::And": [
{"Fn::Equals": ["sg-mysggroup", {"Ref": "ASecurityGroup"}]},
{"Condition": "SomeOtherCondition"}
]
}](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-20-320.jpg)
![Intrinsic Function Usage
Fn::FindInMap
Declaration : "Fn::FindInMap" : [ "MapName", "TopLevelKey", "SecondLevelKey"]
Parameters :
MapName : The logical name of a mapping declared in the Mappings section that contains the keys and values.
TopLevelKey: The top-level key name. Its value is a list of key-value pairs.
SecondLevelKey: The second-level key name, which is set to one of the keys from the list assigned to TopLevelKey.
Return Value: The value that is assigned to SecondLevelKey.
{
...
"Mappings" : {
"RegionMap" : {
"us-east-1" : { "32" : "ami-6411e20d", "64" : "ami-7a11e213" },
"us-west-1" : { "32" : "ami-c9c7978c", "64" : "ami-cfc7978a" },
"eu-west-1" : { "32" : "ami-37c2f643", "64" : "ami-31c2f645" },
"ap-southeast-1" : { "32" : "ami-66f28c34", "64" : "ami-60f28c32" },
"ap-northeast-1" : { "32" : "ami-9c03a89d", "64" : "ami-a003a8a1" }
}
},
"Resources" : {
"myEC2Instance" : {
"Type" : "AWS::EC2::Instance",
"Properties" : {
"ImageId" : { "Fn::FindInMap" : [ "RegionMap", { "Ref" : "AWS::Region" },
"32"]},
"InstanceType" : "m1.small"
}
}
}
}
NB : In above example, if you are build stack in us-west-1 region, for 64 bit instance, it’ll use “ami-cfc7978a”](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-21-320.jpg)
![Intrinsic Function Usage
Fn::GetAtt
Declaration : "Fn::GetAtt" : [ "logicalNameOfResource", "attributeName" ]
Parameters :
logicalNameOfResource: The logical name of the resource that contains the attribute
you want.
attributeName: The name of the resource-specific attribute whose value you want.
Example :
“Outputs” : {
"PrivateIP" : {
"Description" : "Private IP of newly created EC2 instance",
"Value" : { "Fn::GetAtt" : ["EC2Instance", "PrivateIp"] }
}
}](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-22-320.jpg)
![Intrinsic Function Usage
Fn::Join
Declaration : "Fn::Join" : [ "delimiter", [ comma-delimited list of values ] ]
Return Value : The combined string.
Example :
"Fn::Join" : [ ":", [ "a", "b", "c" ] ]
This example returns: "a:b:c".](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-24-320.jpg)


![CF Helper Scripts Usage
"UserData":{
"Fn::Base64":{ "Fn::Join":[ "", [
"#!/bin/bash -xen",
"# Install the files and packages from the metadatan",
"/opt/aws/bin/cfn-init -v ",
" --stack ", { "Ref" : "AWS::StackName" },
" --resource EC2Instance",
" --configsets InstallSoftware",
" --region ", { "Ref" : "Region" }, "n",
"# Start up the cfn-hup daemon to listen for changes to the metadatan",
"/opt/aws/bin/cfn-hup || error_exit 'Failed to start cfn-hup'n",
"# Signal the status from cfn-initn",
"/opt/aws/bin/cfn-signal -e $? ",
" --stack ", { "Ref" : "AWS::StackName" },
" --resource EC2Instance",
" --region ", { "Ref" : "Region" }, "n"
]]
}
}
User data section of EC2
resource
Called cfn-init script
Run cfn-hup deamon
Checks return status
of cfn-init](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-27-320.jpg)
!["Metadata" : {
"AWS::CloudFormation::Init" : {
"configSets" : {
"InstallSoftware" : ["Install"]
},
"Install" : {
"files" : {
"/etc/cfn/cfn-hup.conf" : {
"content" : { "Fn::Join" : ["", [
"[main]n",
"stack=", { "Ref" : "AWS::StackId" }, "n",
"region=", { "Ref" : "Region" }, "n"
]]},
"mode" : "000400", "owner" : "root", "group" : "root“ },
"/etc/cfn/hooks.d/cfn-auto-reloader.conf" : {
"content": { "Fn::Join" : ["", [
"[cfn-auto-reloader-hook]n",
"triggers=post.updaten",
"path=Resources.WebServerInstance.Metadata.AWS::CloudFormation::Initn",
"action=/opt/aws/bin/cfn-init -v ",
" --stack ", { "Ref" : "AWS::StackName" },
" --resource EC2Instance ",
" --configsets InstallSoftware ",
" --region ", { "Ref" : "Region" }, "n",
"runas=rootn"
]]}
}
},
"commands" : {
"configure node" : {
"command" : { "Fn::Join" : ["", [
"logger 'finised commandlines' n"
]]
}
}
},
"services" : {
"sysvinit" : {
"cfn-hup" : { "enabled" : "true", "ensureRunning" : "true",
"files" : ["/etc/cfn/cfn-hup.conf", "/etc/cfn/hooks.d/cfn-auto-
reloader.conf"]}
}
}}
}
}
EC2 Metadata section
EC2 standard cfn-init section
Cfn-hup config file
Cfn-hup autoloader config file
Auto-loader will be used for post update only
Starts cfn-hup as daemon](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-28-320.jpg)
![CF Stack & Template
Nested Template can be called to reuse same template
Resource "Type" : "AWS::CloudFormation::Stack“ must be used.
"TemplateURL" needs to be used in Property section.
"Parameters" can be passed from master to nested template
Example :
"Resources" : {
"FrontNodeStack" : {
"Type" : "AWS::CloudFormation::Stack",
"Properties" : {
"TemplateURL" : "https://s3-sa-east-1.amazonaws.com/claro-templates-static-sa-
east-1/tyco-front-back-nested-ec2-gru1.json",
"Parameters" : {
"Customer" : { "Ref" : "Customer“ },
[…]
"PuppetMaster" : {"Ref" : "PuppetMaster"}
}
}
}
}
Stack resource Type](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-29-320.jpg)



![Auto-Scaling
“MyInstance" : {
"Type" : "AWS::AutoScaling::LaunchConfiguration",
"Properties" : {
"SecurityGroups" : [“XXXX"],
[…]
}
}
“AppAutoScalingGroup" : {
"Type" : "AWS::AutoScaling::AutoScalingGroup",
"Properties" : {
"AvailabilityZones" : { "Fn::GetAZs" : "" },
"LaunchConfigurationName" : { "Ref" : “MyInstance" },
"MinSize" : "1",
"MaxSize" : "2",
"Cooldown" : "600",
"TerminationPolicies" : [ "NewestInstance" ],
"VPCZoneIdentifier" : [ "subnet-XXX" ],
"NotificationConfiguration" : {
"TopicARN" : { "Ref" : "SNSTopic" },
"NotificationTypes" : [
"autoscaling:EC2_INSTANCE_LAUNCH",
"autoscaling:EC2_INSTANCE_LAUNCH_ERROR",
"autoscaling:EC2_INSTANCE_TERMINATE",
"autoscaling:EC2_INSTANCE_TERMINATE_ERROR"
]
}
}
},
"AppServerScaleUpPolicy" : {
"Type" : "AWS::AutoScaling::ScalingPolicy",
"AutoScalingGroupName" : { "Ref" :
"AppAutoScalingGroup" },
[..]
"ScalingAdjustment" : "1"
"AppServerScaleDownPolicy" : {
"Type" : "AWS::AutoScaling::ScalingPolicy",
"AutoScalingGroupName" : { "Ref" :
"AppAutoScalingGroup" },
[..]
"ScalingAdjustment" : "-1"
“AppCPUAlarmHigh": {
"Type": "AWS::CloudWatch::Alarm",
"Properties": {
"AlarmDescription": "Scale-up if CPU > 7% for 1 minute",
"MetricName": "CPUUtilization",
"Namespace": "AWS/EC2",
"Statistic": "Average",
"Period": "60",
"EvaluationPeriods": "1",
"Threshold": "7",
"AlarmActions": [ { "Ref": "AppServerScaleUpPolicy" } ],
[…]
"ComparisonOperator": "GreaterThanThreshold"
“AppCPUAlarmLow": {
"Type": "AWS::CloudWatch::Alarm",
"Properties": {
"AlarmDescription": "Scale-down if CPU < 5% for 2 minutes",
"MetricName": "CPUUtilization",
"Namespace": "AWS/EC2",
"Statistic": "Average",
"Period": "120",
"EvaluationPeriods": "1",
"Threshold": "5",
"AlarmActions": [ { "Ref": "AppServerScaleDownPolicy" } ],
[…]
"ComparisonOperator": "LessThanThreshold"](https://image.slidesharecdn.com/cf-session-150727185210-lva1-app6891/85/AWS-CloudFormation-Session-33-320.jpg)



