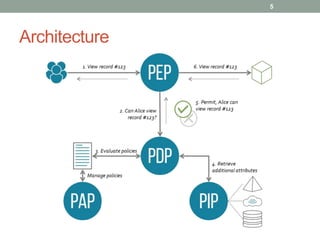
Attribute-Based Access Control (ABAC) is a model where access rights are granted to users based on policies that incorporate various attributes, such as user, resource, and environmental attributes. The architecture includes a Policy Enforcement Point (PEP), Policy Decision Point (PDP), and Policy Information Point (PIP) that interact to evaluate access requests and apply rules. Implementation of ABAC often utilizes standards like XACML and available open-source tools, such as AuthzForce and Balana.