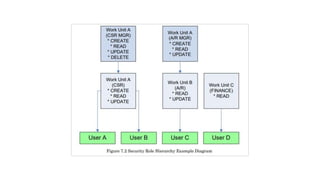
This document discusses data security management. It outlines key concepts and activities including understanding business and regulatory requirements, defining security policies, standards, controls and procedures, managing users, passwords and permissions. The goal is to protect information through proper authentication, authorization, access and auditing in alignment with privacy needs and regulations.