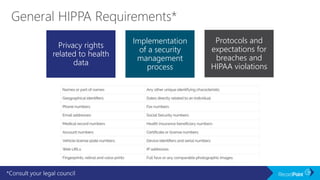
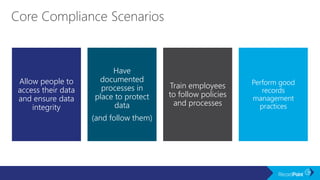
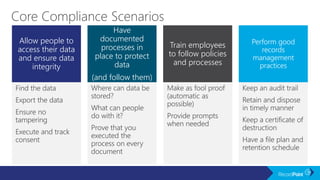
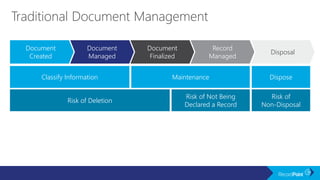
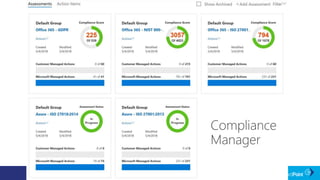
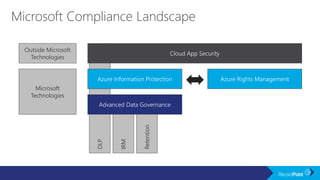
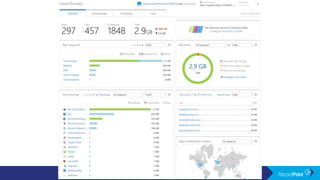
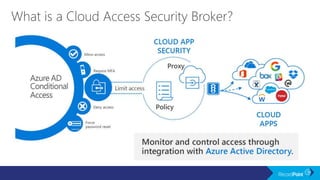
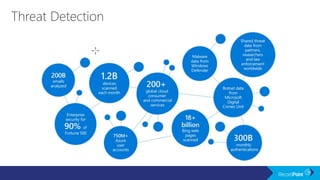
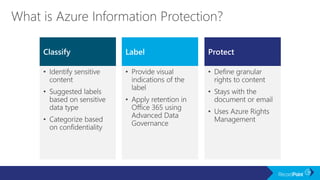
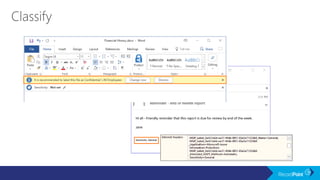
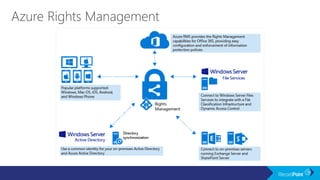
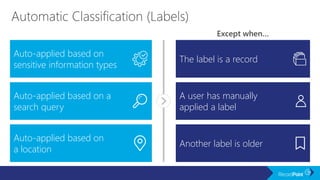
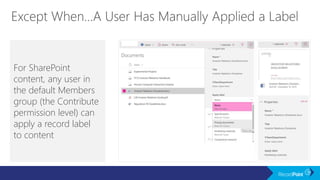
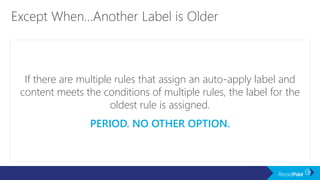
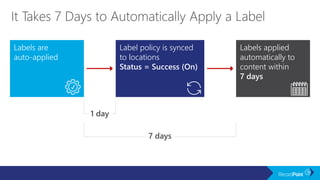
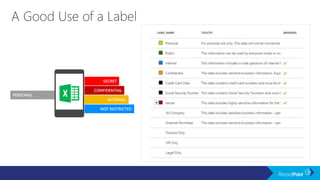
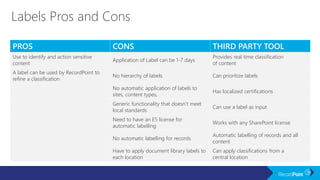
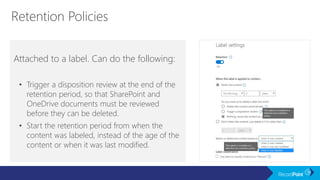
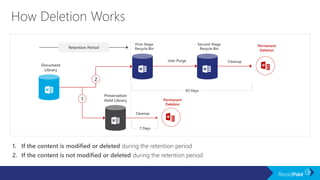
The document outlines a schedule for a conference focused on records management, compliance scenarios, and cloud security, detailing various topics and sessions. It emphasizes the importance of good records management practices, employee training, and data protection while discussing Microsoft's cloud app security features and regulatory compliance support. Additionally, it highlights processes for data classification, labeling, retention, and legal hold policies within Microsoft technologies.