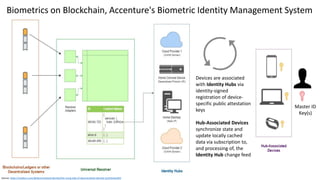
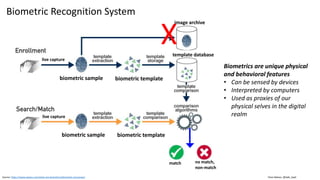
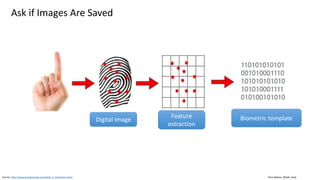
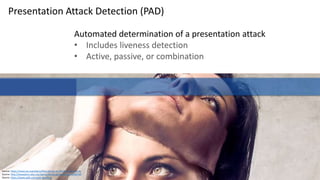
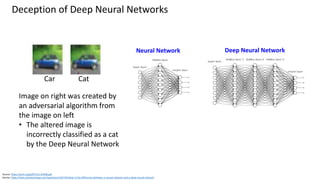
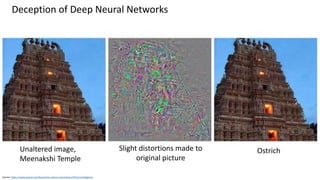
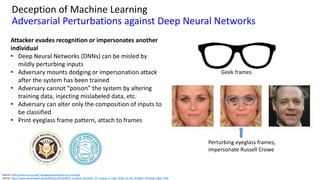
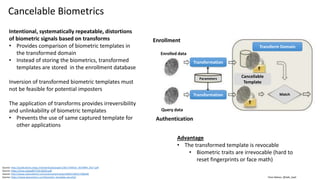
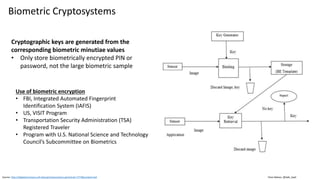
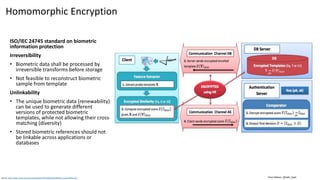
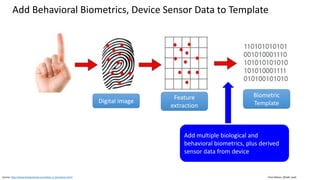
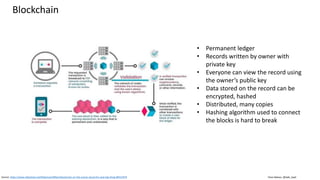
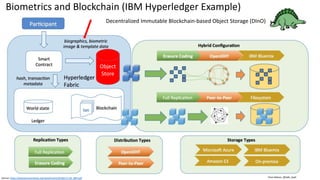
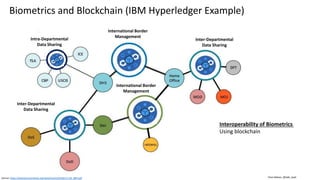
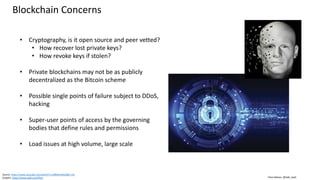
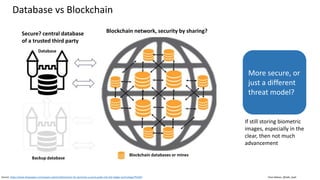
This document discusses vulnerabilities in biometric recognition systems. It begins by noting that while biometrics offer promise for authentication, spoofing attacks remain too easy. It then provides examples of recent fingerprint and facial spoofing attacks against Samsung and iPhone devices. The document outlines different types of presentation attacks and discusses presentation attack detection methods. It also explains how machine learning systems can be deceived through adversarial examples and perturbations. The document notes vulnerabilities in using biometrics on mobile devices and discusses how templates and systems must evolve for stronger security. It concludes by mentioning the potential role of blockchain.











































![Clare Nelson, @Safe_SaaS
• Hardjono, Thomas; Pentland, Alex “Sandy”; MIT Connection Science & Engineering; Core Identities for Future Transaction Systems,
https://static1.squarespace.com/static/55f6b5e0e4b0974cf2b69410/t/57f7a1653e00be2c09eb96e7/1475846503159/Core-Identity-Whitepaper-
v08.pdf (October 7, 2016). [TBD: check back, right now it is a DRAFT, do not cite]
• Jankovich, Thomas; “Blockchain Makes Digital ID a Reality,” https://finxtech.com/2016/12/02/blockchain-makes-digital-id-reality/ (December 2016)
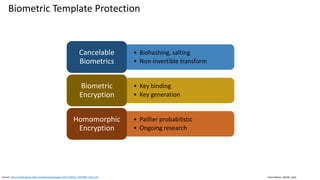
• Jin, Zhe; Lai, Yen-Lung; Hwang, Jung Yeon; Ranking Based Locality Sensitive Hashing Enabled Cancelable Biometrics: Index-of-Max Hashing,
https://arxiv.org/pdf/1703.05455.pdf (2017)
• Johnstone, Mike; Why we need privacy-preserving authentication in the Facebook age,
http://www.iaria.org/conferences2015/filesICSNC15/ICSNC_Keynote_v1.1a.pdf (November 2013).
• Kunk, S.K., Biometric Authentication: A Machine Learning Approach, Prentice Hall (2005).
• mikeh, Machine Learning and Biometrics, Neya Systems blog, http://neyasystems.com/machine-learning-biometrics/ (March 23, 2013)
• MyData Identity Network based on User Managed Access (UMA),
https://docs.google.com/presentation/d/1j3aX8AQGdVtigF1WZouL8WccmYQzZQQje3wuaC2Zb1I/edit#slide=id.g1386e8a6aa_2_914
• Nelson, Clare, Multi-Factor Authentication: What to Look For, Information Systems Security Association (ISSA)
Journalhttp://www.bluetoad.com/publication/?i=252353 (April 2015)
References, 2 of 3](https://image.slidesharecdn.com/lascon2017v1-171025224032/85/Attack-Vectors-in-Biometric-Recognition-Systems-68-320.jpg)































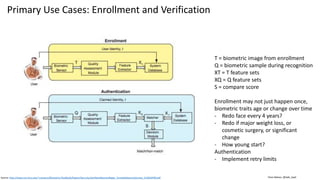
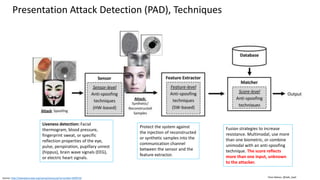
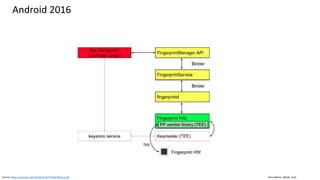

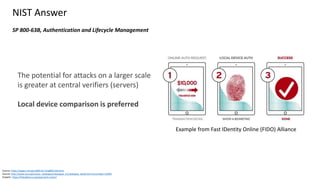
![Clare Nelson, @Safe_SaaS
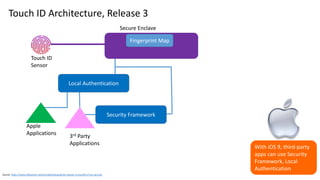
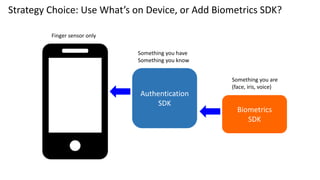
Why Add Biometrics SDK?
Some authentication vendors only support what is
integrated, manufactured in the phone
Touch ID [Face ID] can be used for verification by third
party apps
Similarly, works with Android, some variations.
Third party applications
• Can bypass Touch ID fallback to password or device
passcode
• User may have an unlimited number of Touch ID
verification attempts with this option
• Defeat retry limits
Source: https://courses.csail.mit.edu/6.857/2016/files/12.pdf
Source: https://www.arxan.com/wp-content/uploads/2016/09/ARXAN_Mobile-DATA.3-.pdf](https://image.slidesharecdn.com/lascon2017v1-171025224032/85/Attack-Vectors-in-Biometric-Recognition-Systems-121-320.jpg)