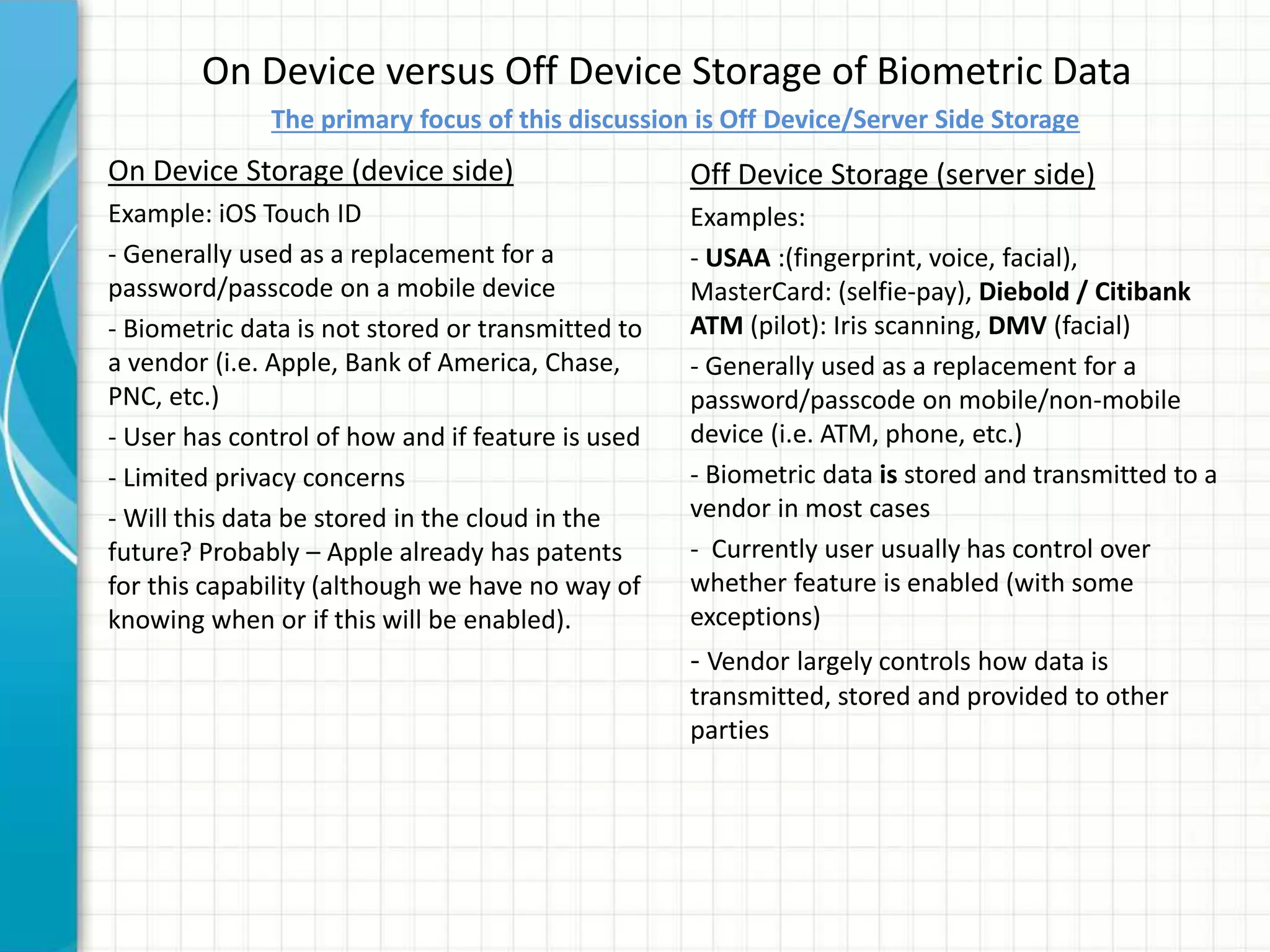
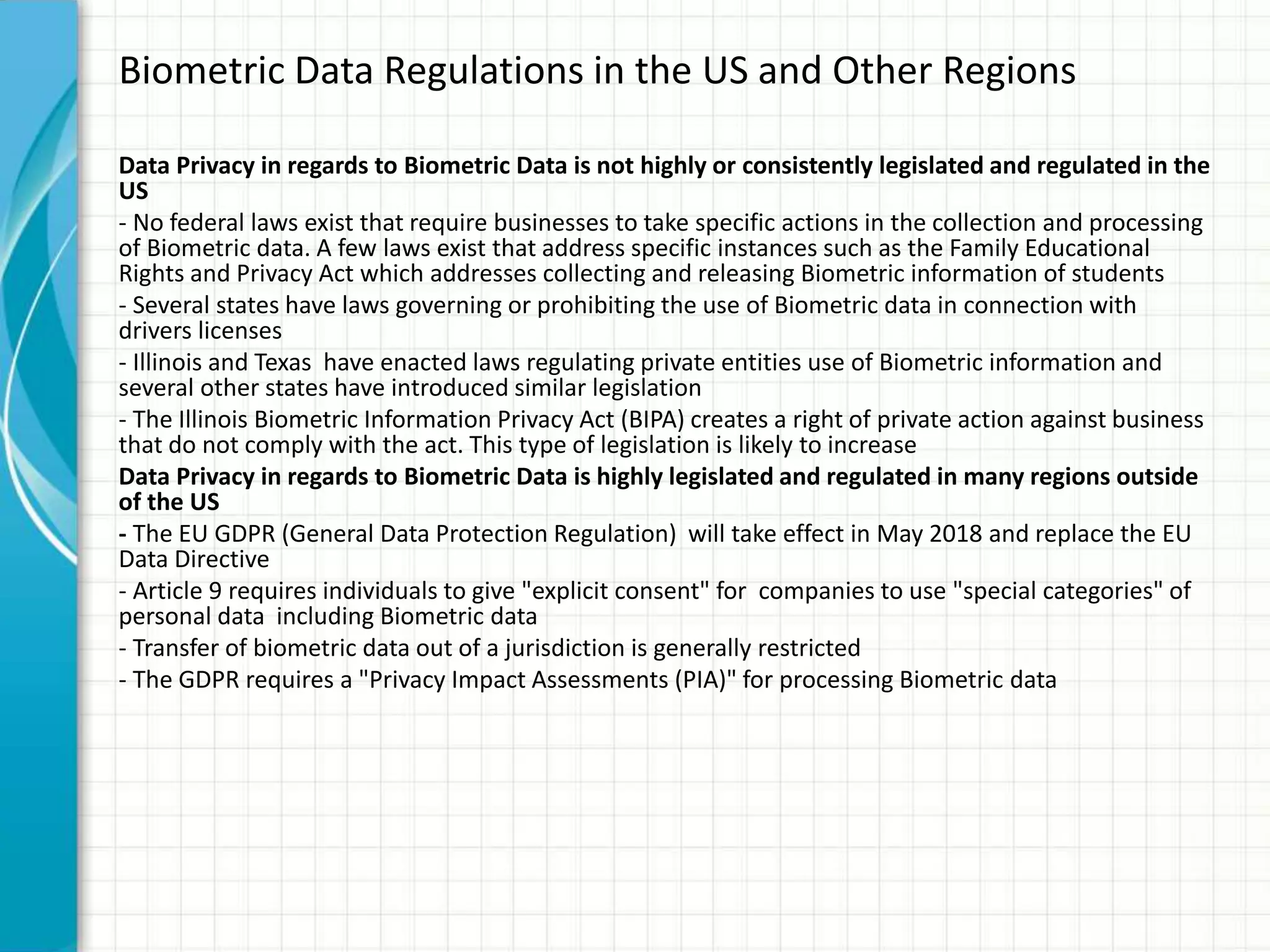
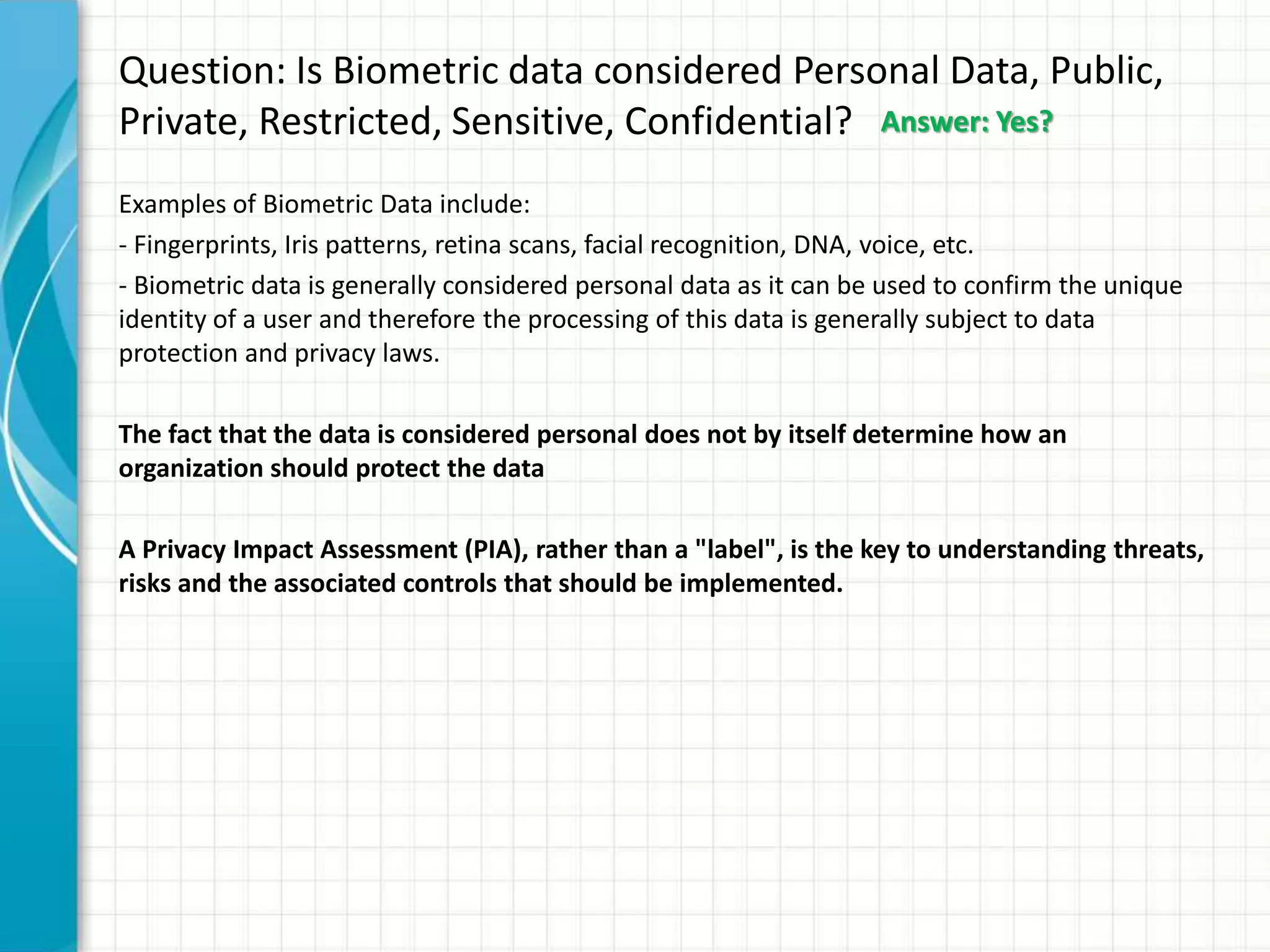
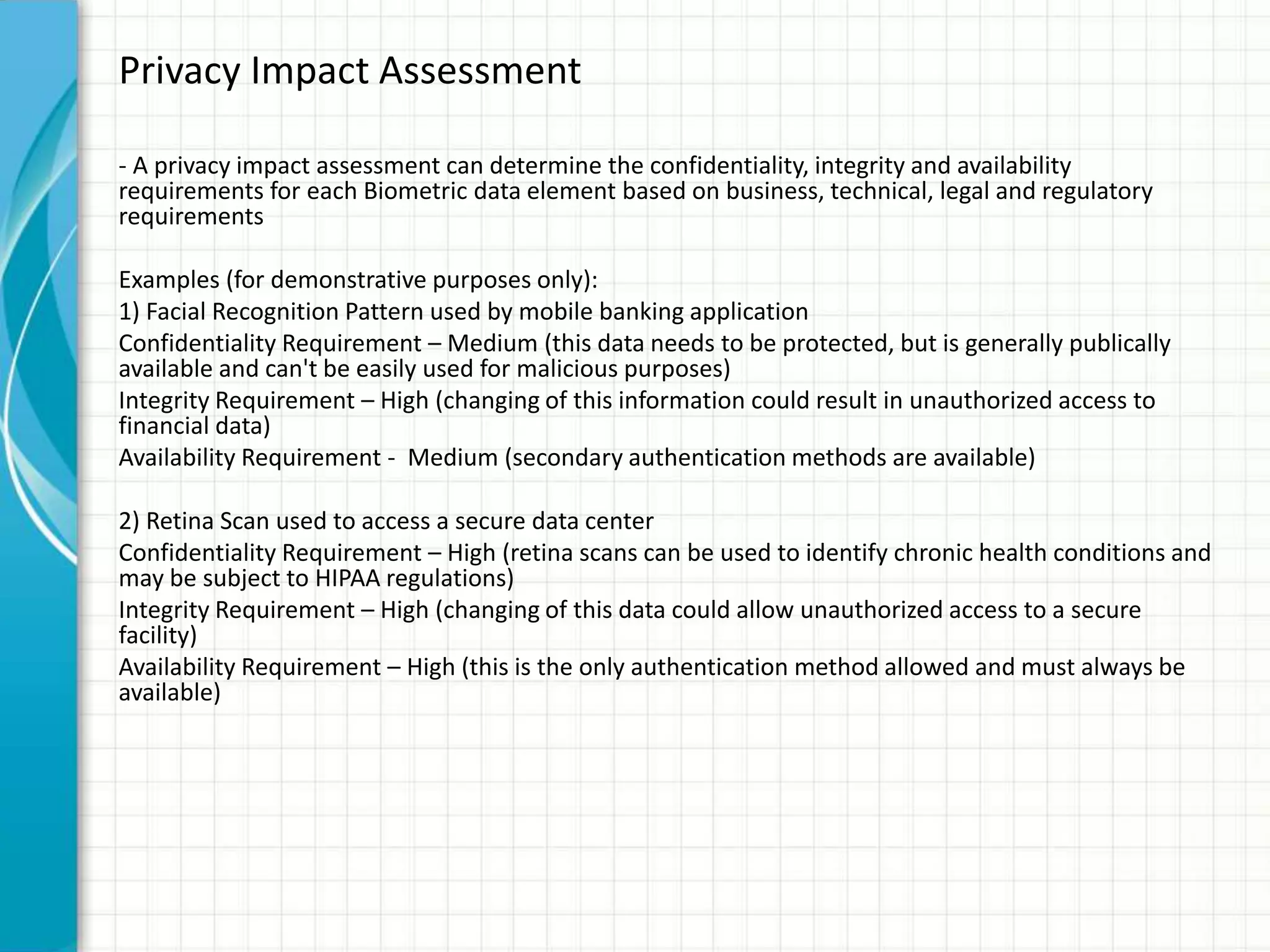
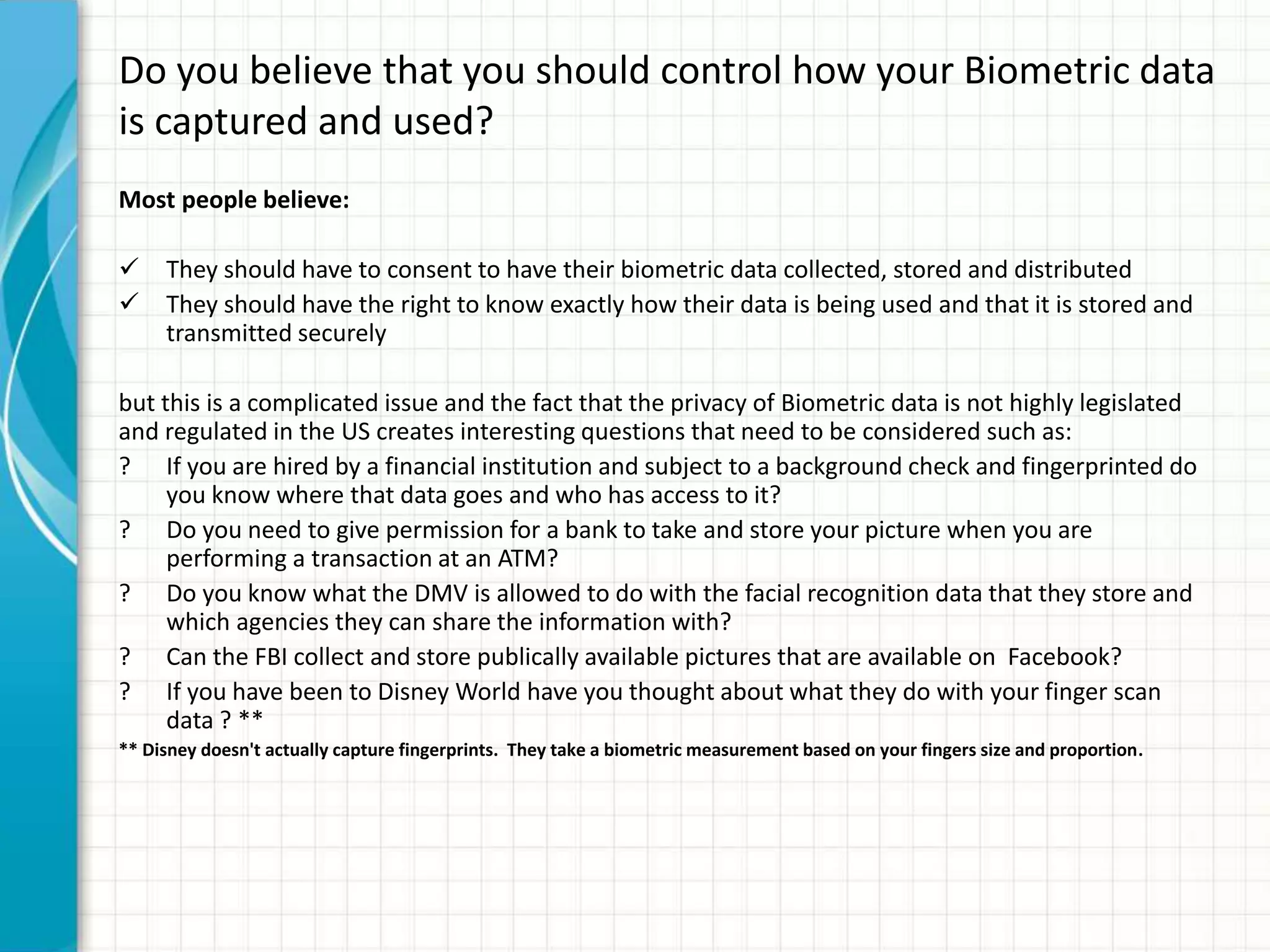
This document discusses privacy implications of biometric data. It provides examples of how biometric authentication is used for fraud prevention at ATMs and for banking in Africa. Benefits include security, safety, ease of use and speed. Biometric data can be stored on or off devices. Off-device storage raises more privacy concerns as the data is transmitted and stored by vendors. Regulations for biometric data vary globally, with the EU having stricter laws. Disclosure of biometric data like fingerprints can impact individuals even if current misuse potential is limited, due to integrity and availability risks. Social and privacy concerns must be addressed for broad biometric adoption.