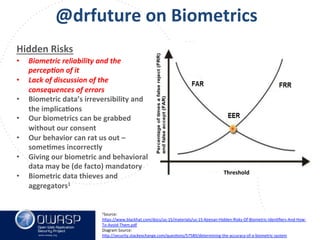
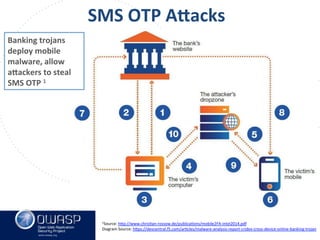
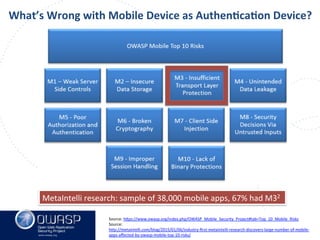
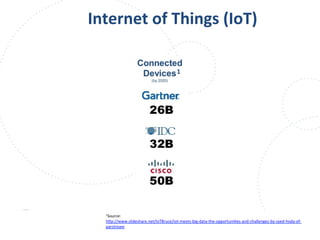
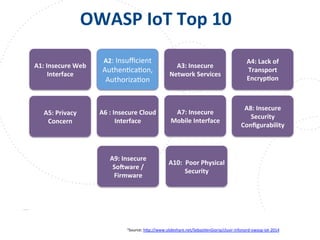
This document summarizes a talk given by Clare Nelson at OWASP on why some multi-factor authentication technology is irresponsible. Nelson discusses issues with the outdated NIST definition of multi-factor authentication and how some vendors rely on weak factors like SMS, biometrics, or location data. The talk argues for updated definitions of authentication factors and more responsible choices by vendors to better secure user accounts.