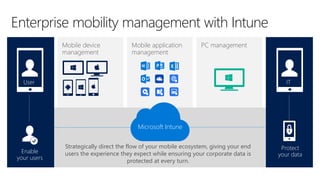
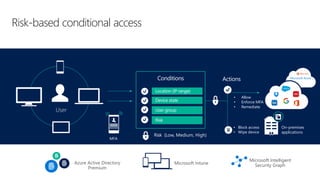
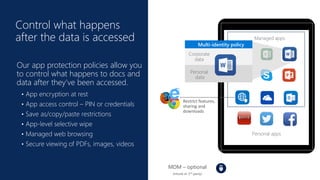
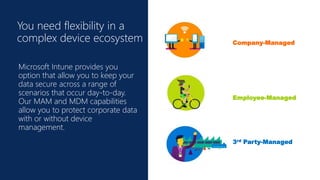
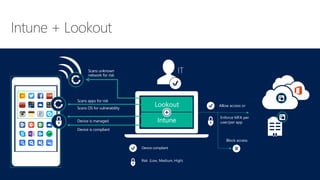
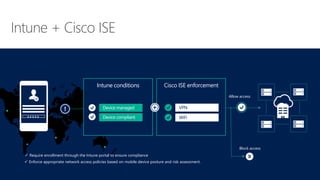
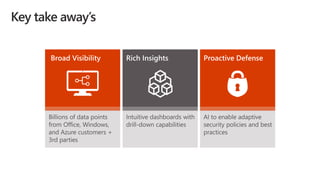
Cybersecurity is a complex problem due to constantly changing threats, attacks, regulations, and technology. Microsoft Intune provides unified management of mobile devices and applications to empower productivity while protecting data. Intune uses visibility and controls like conditional access to balance security and user experience across an organization's diverse mobile environment.












![[ Privacy/Compliance boundary ]](https://image.slidesharecdn.com/ateaerfamicrosoftmobilesecurity-170609085527/85/Atea-erfa-microsoft-mobile-security-20-320.jpg)