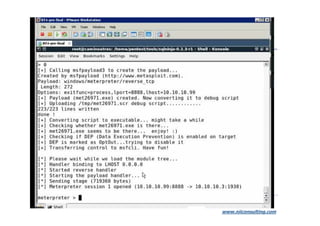
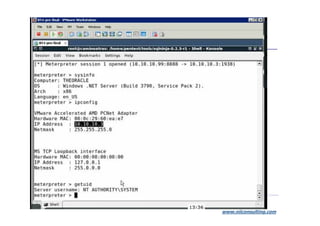
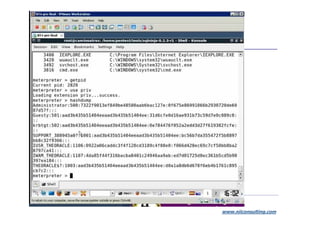
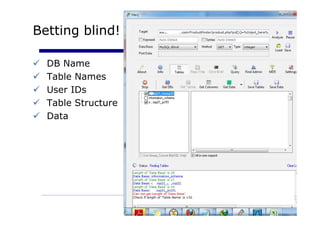
The document discusses application security strategies for enterprises. It summarizes a talk on the biggest hack in history that stole over 200 million credit card numbers. The hacker used SQL injection to hack retail websites and steal card data. It then discusses how application vulnerabilities can be exploited and the high costs of data breaches for companies. The rest of the document outlines a holistic solution to application security that includes secure design, development, testing, training and management.




![The hacker underground
Albert Gonzalez
a/k/a “segvec,”
a/k/a “soupnazi,”
a/k/a “j4guar17”
Malware, scripts and hacked data hosted on servers in:
Latvia Ukraine
New Jersey
Netherlands
California
IRC chats
March 2007: Gonzalez “planning my second phase against
Hannaford”
December 2007: Hacker P.T. “that’s how [HACKER 2]
hacked Hannaford.”
www.niiconsulting.com](https://image.slidesharecdn.com/applicationsecurity-enterprisestrategies-111101031719-phpapp02/85/Application-security-enterprise-strategies-6-320.jpg)