Embed presentation
Downloaded 51 times







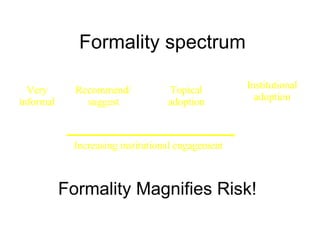






The document discusses the risks associated with Web 2.0 services, including confidentiality, security, and data protection. It emphasizes the importance of institutional engagement and user education in managing these risks. Additionally, it touches on the evolution towards Web 3.0 and the implications for decentralized user control.


















