Embed presentation
Downloaded 66 times


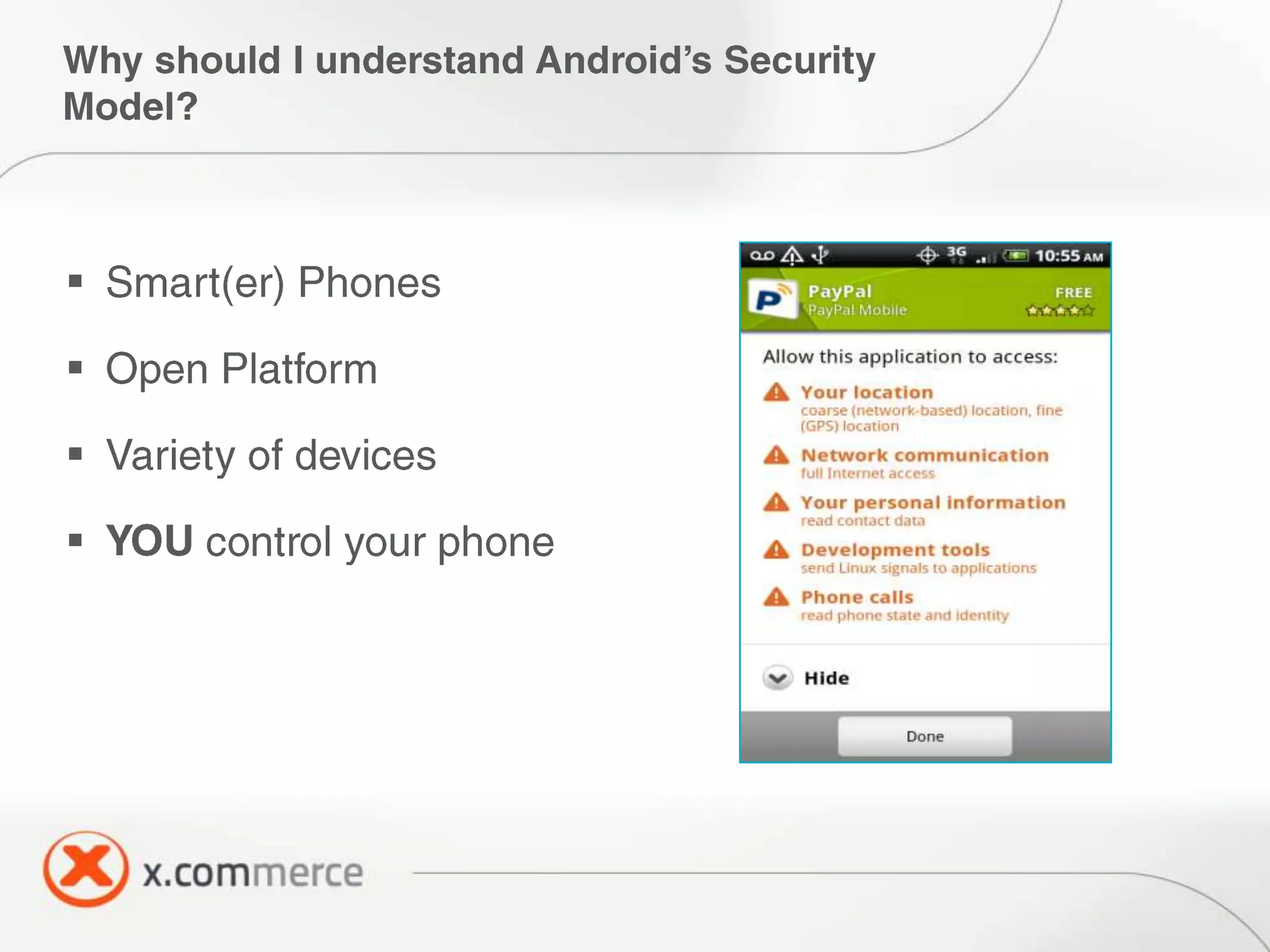
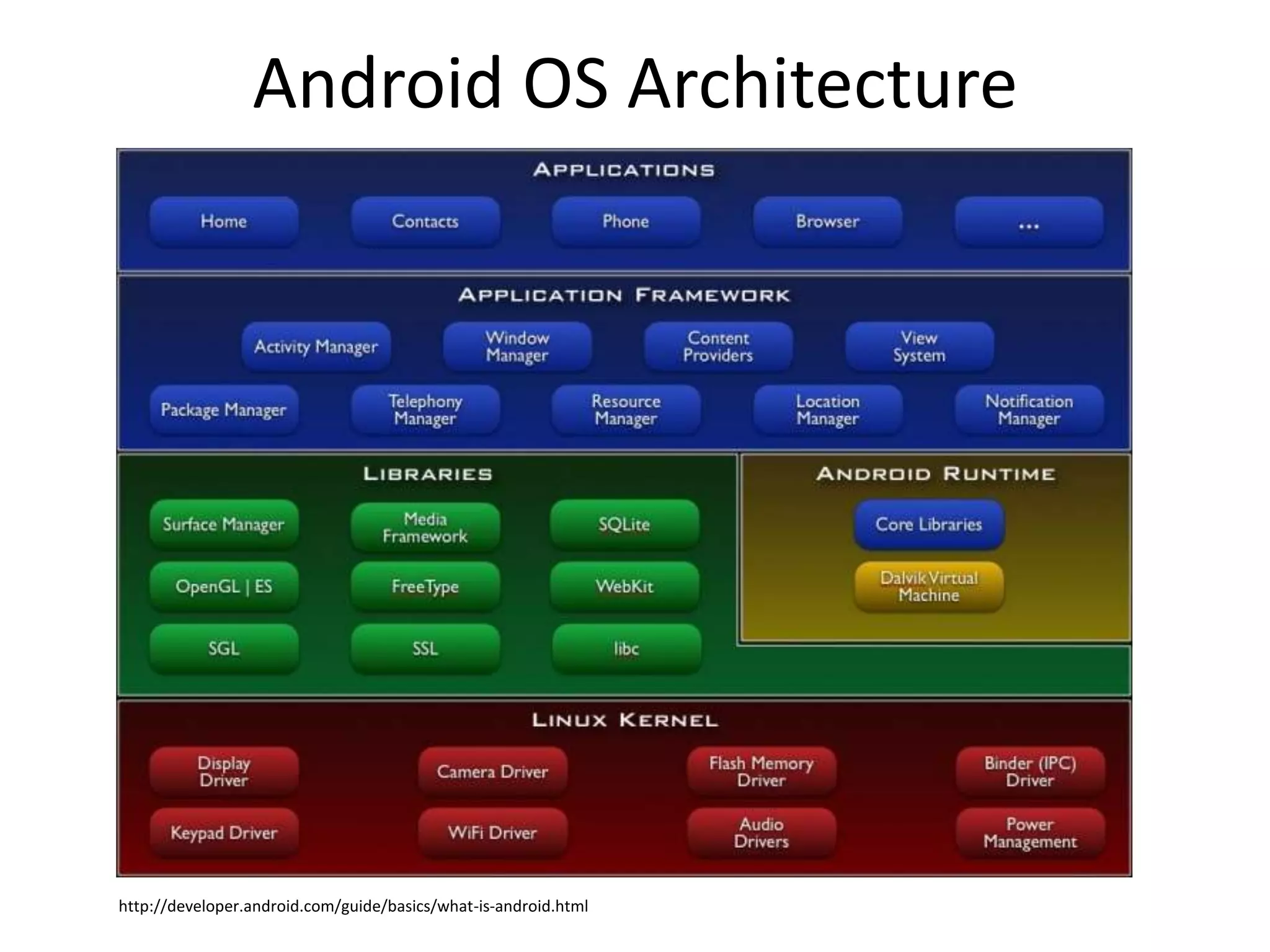
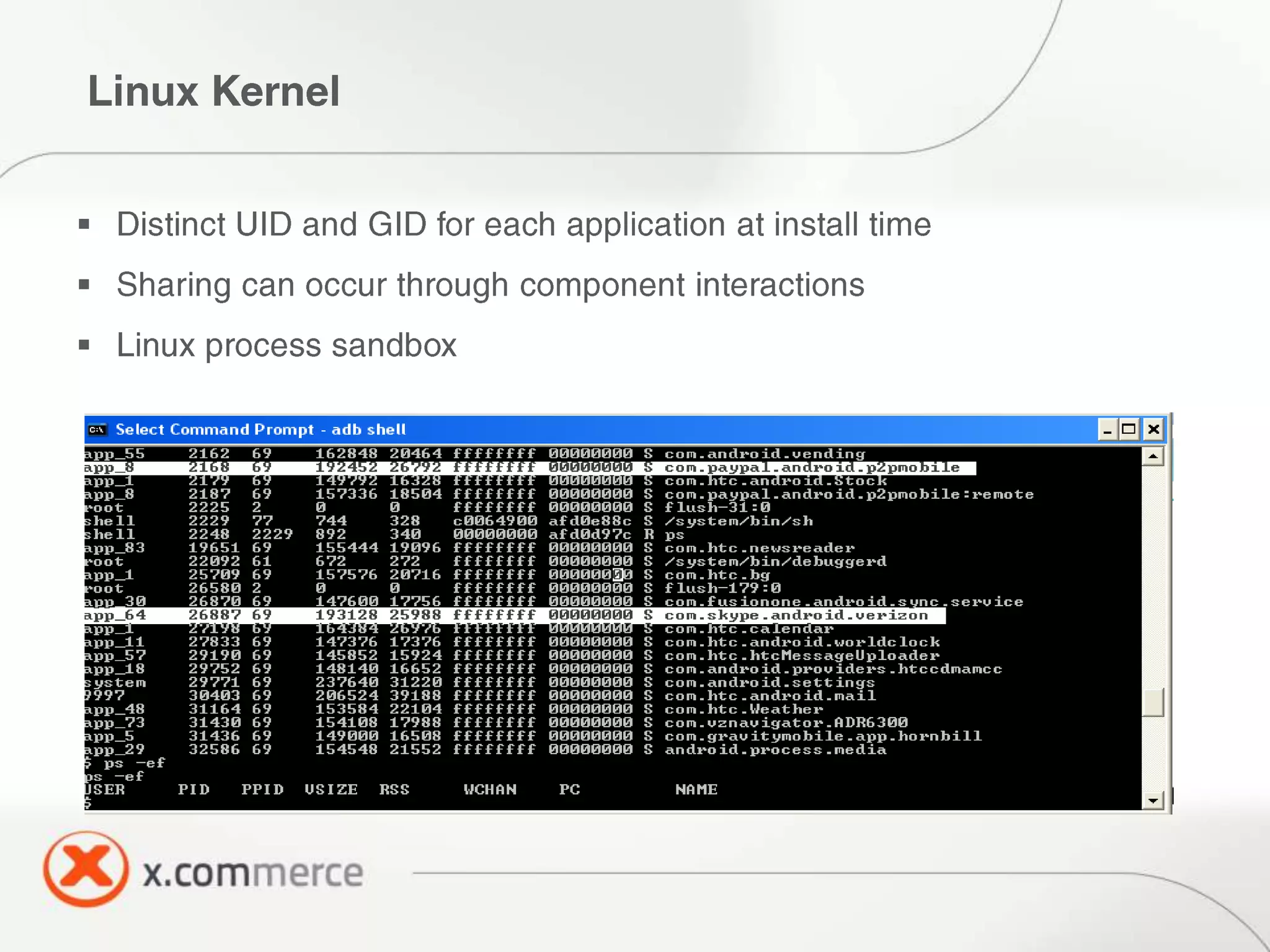
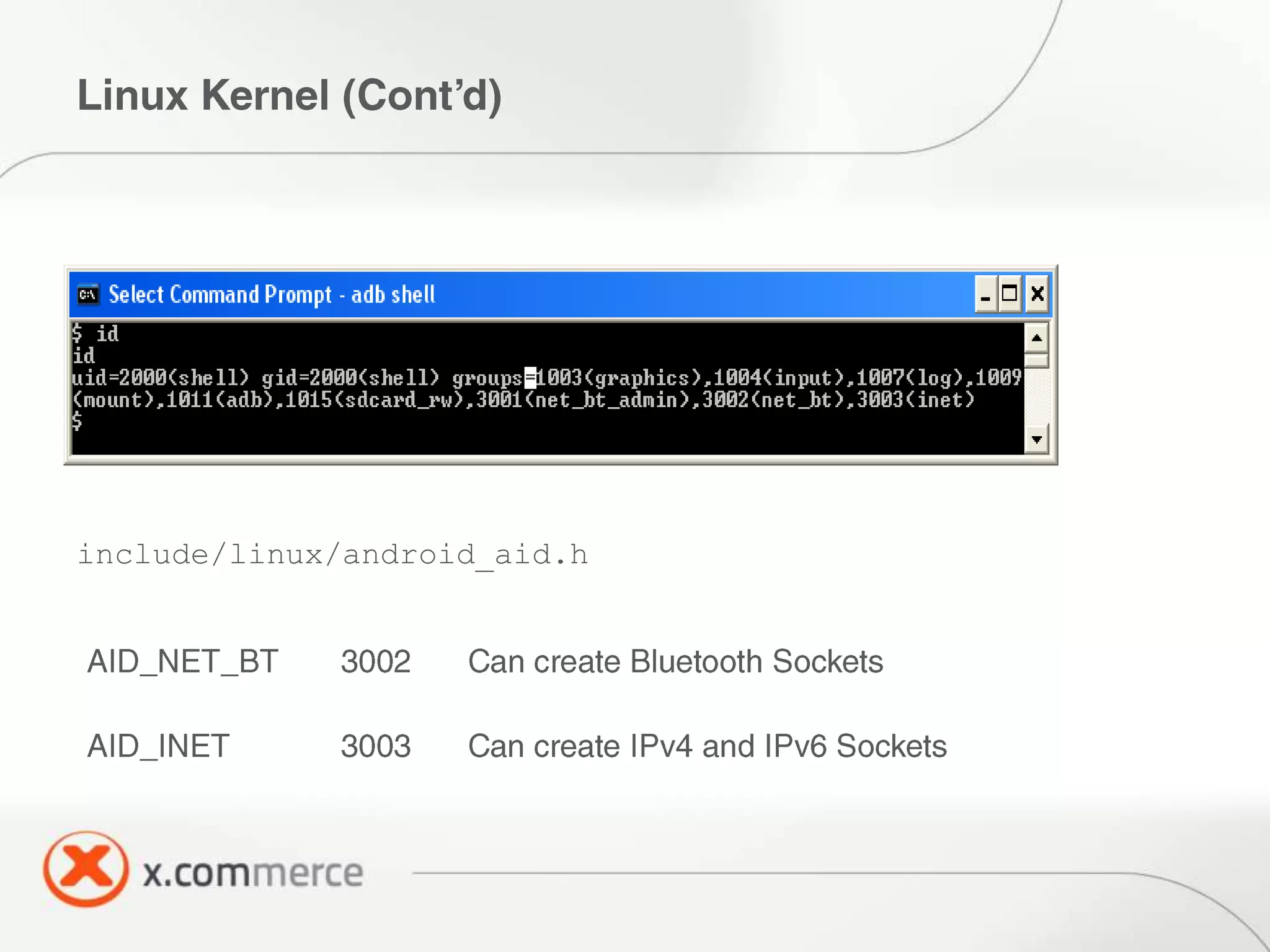
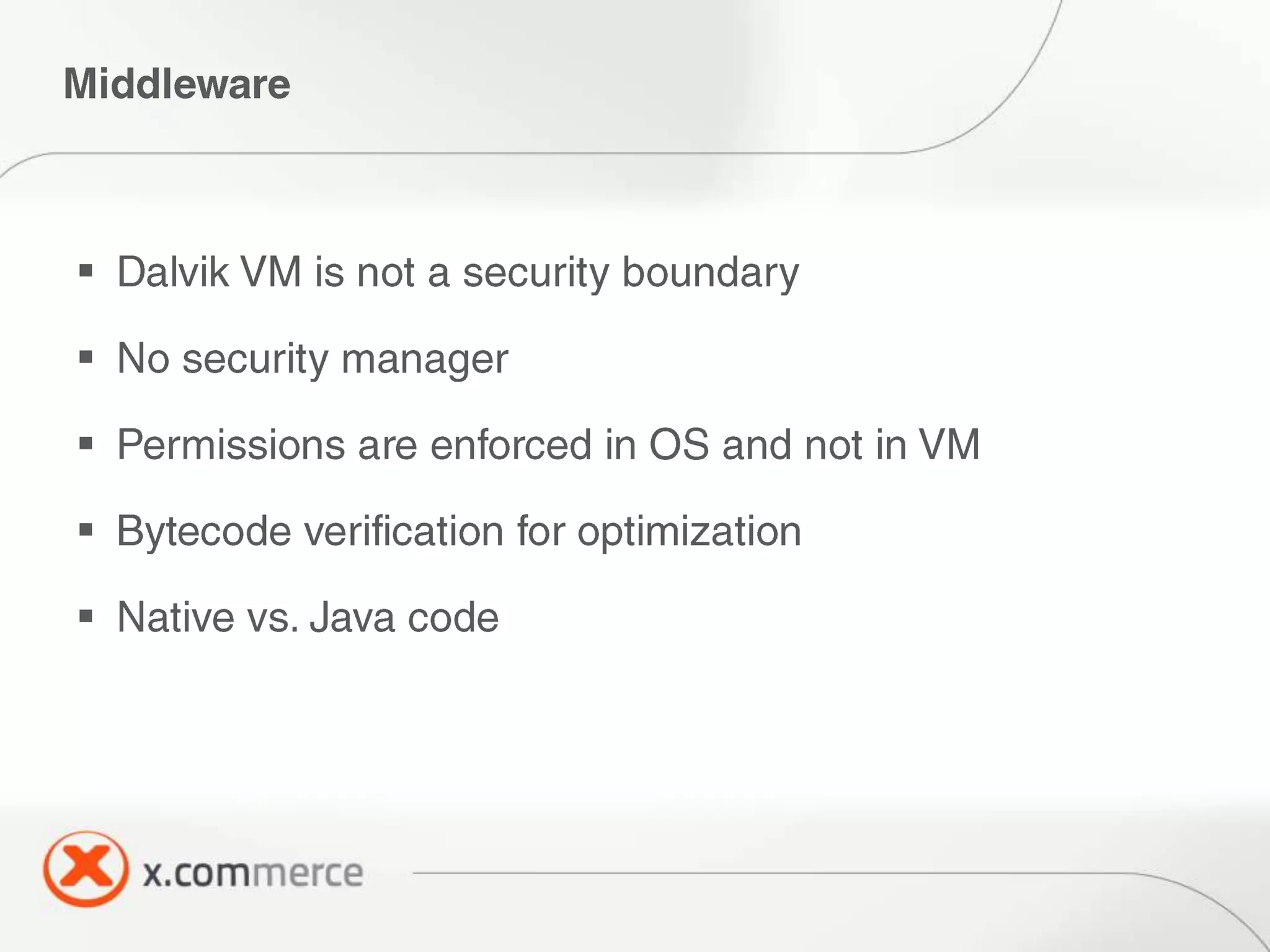

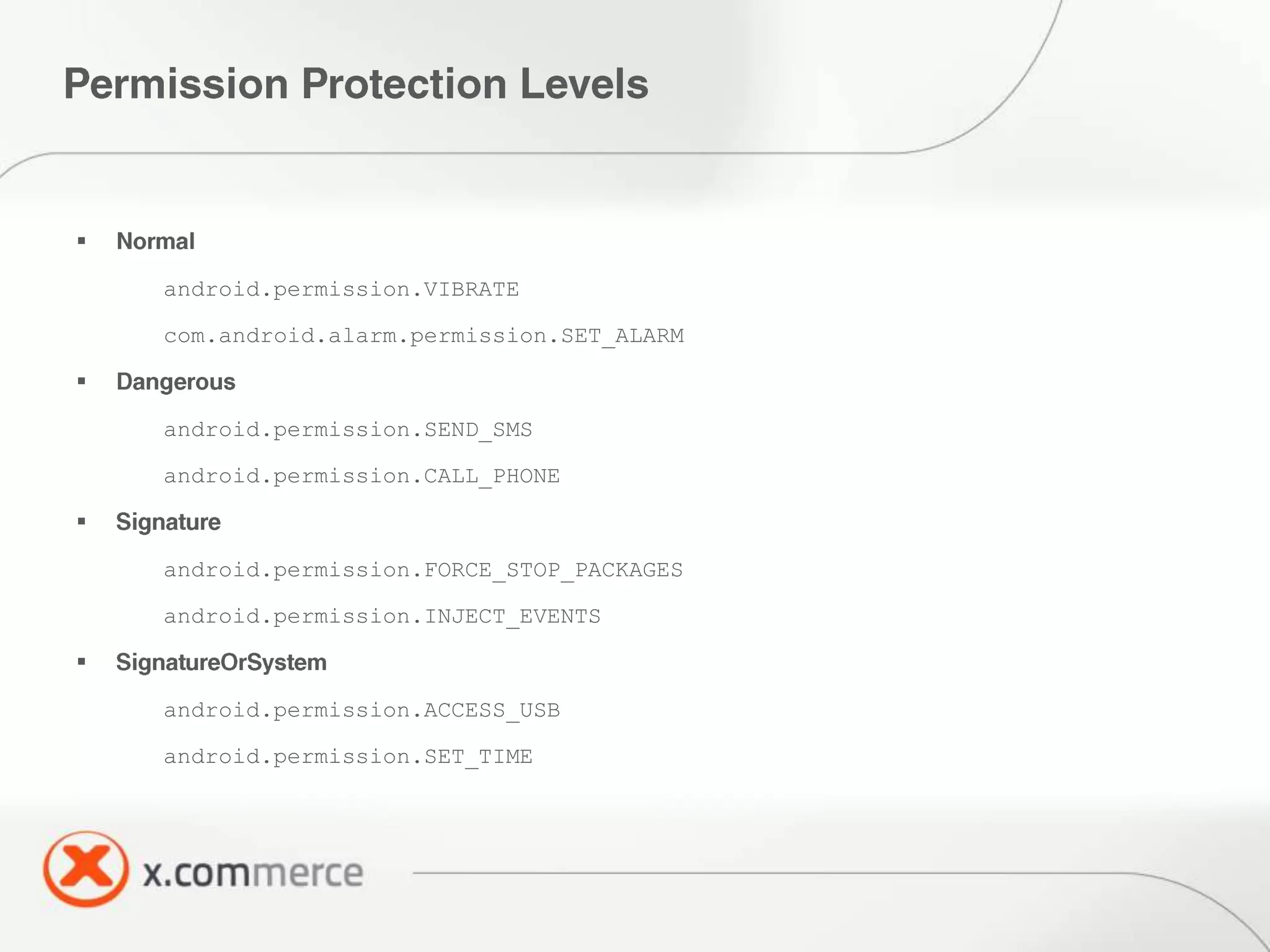
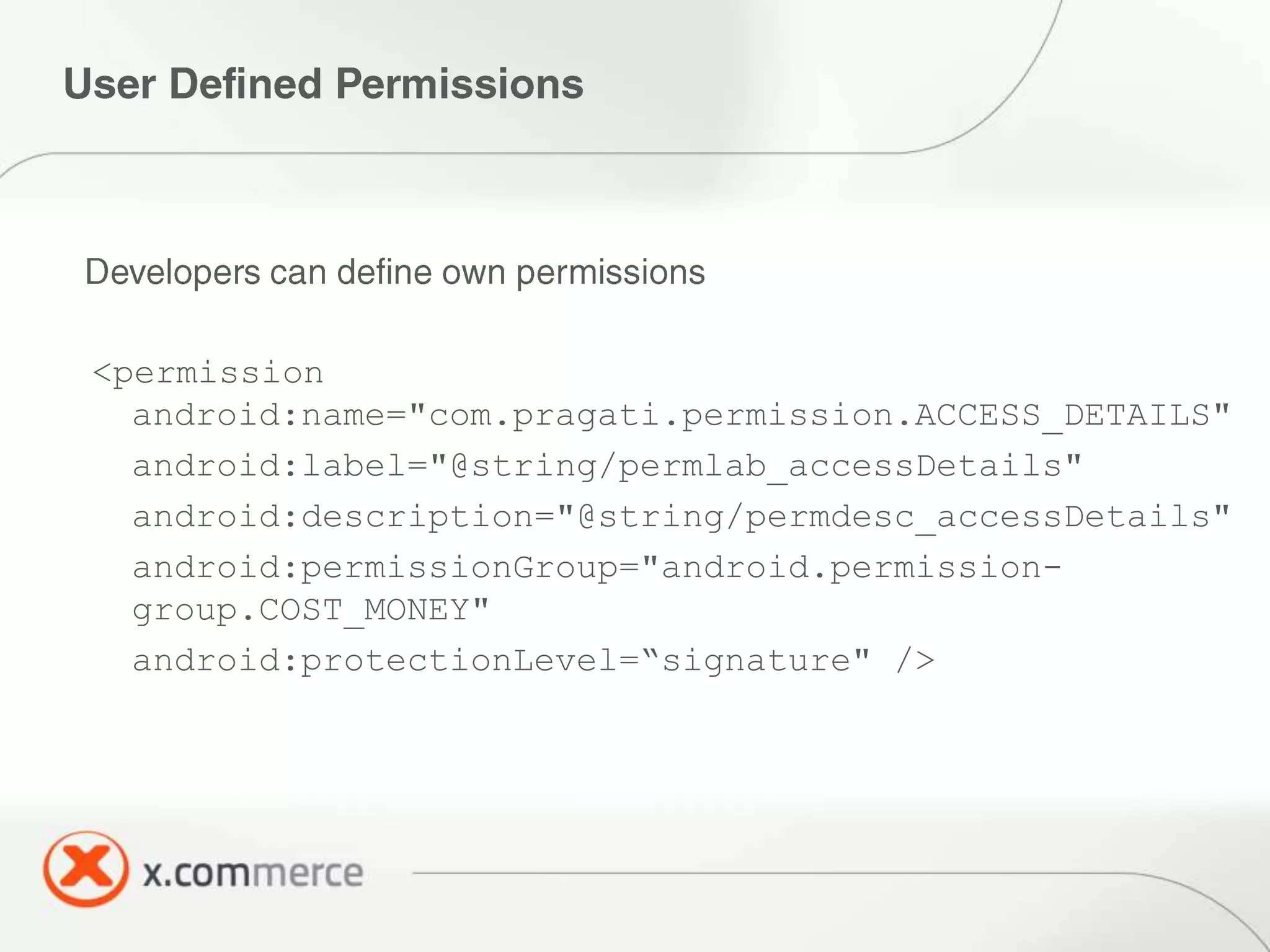
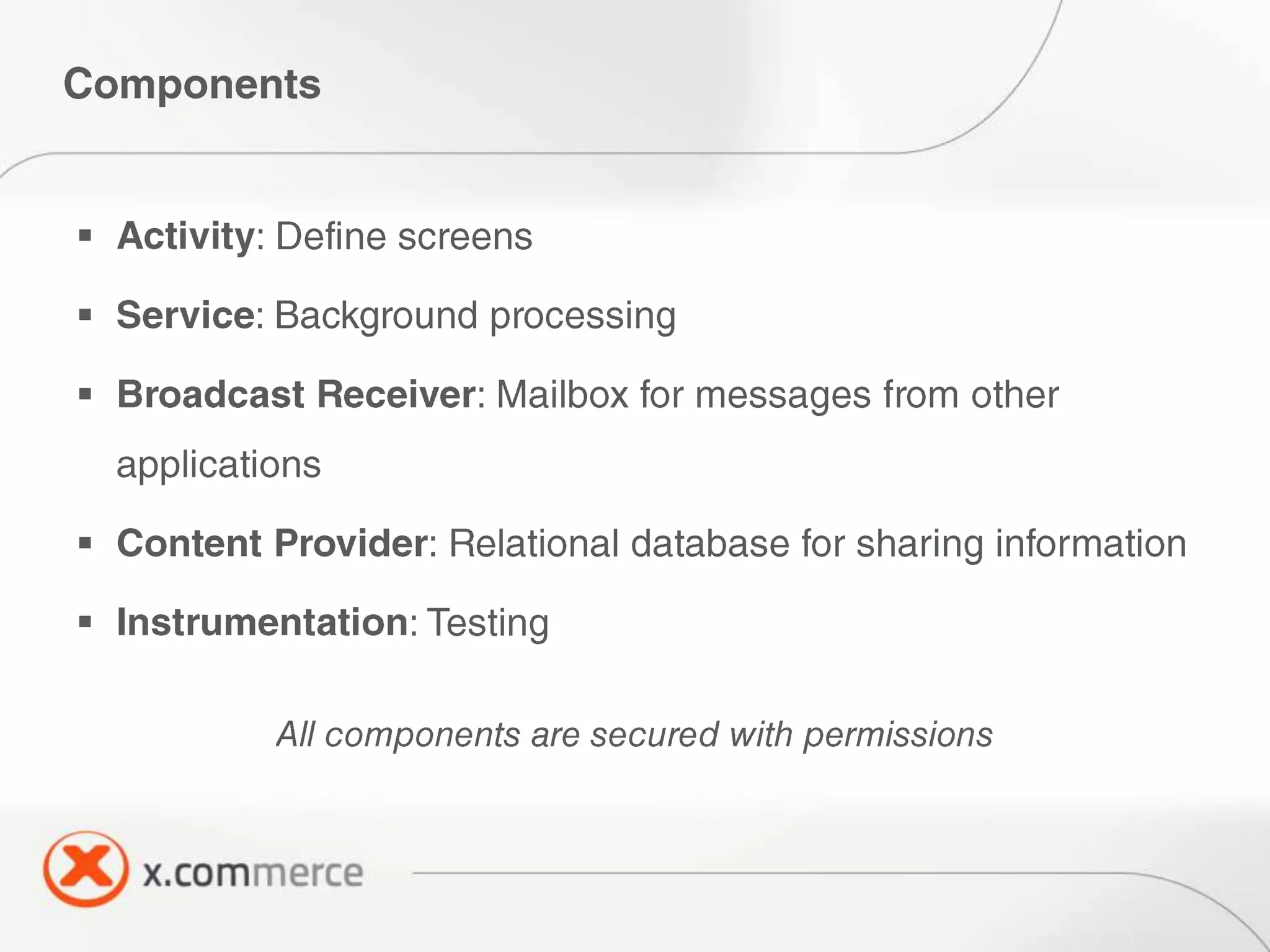
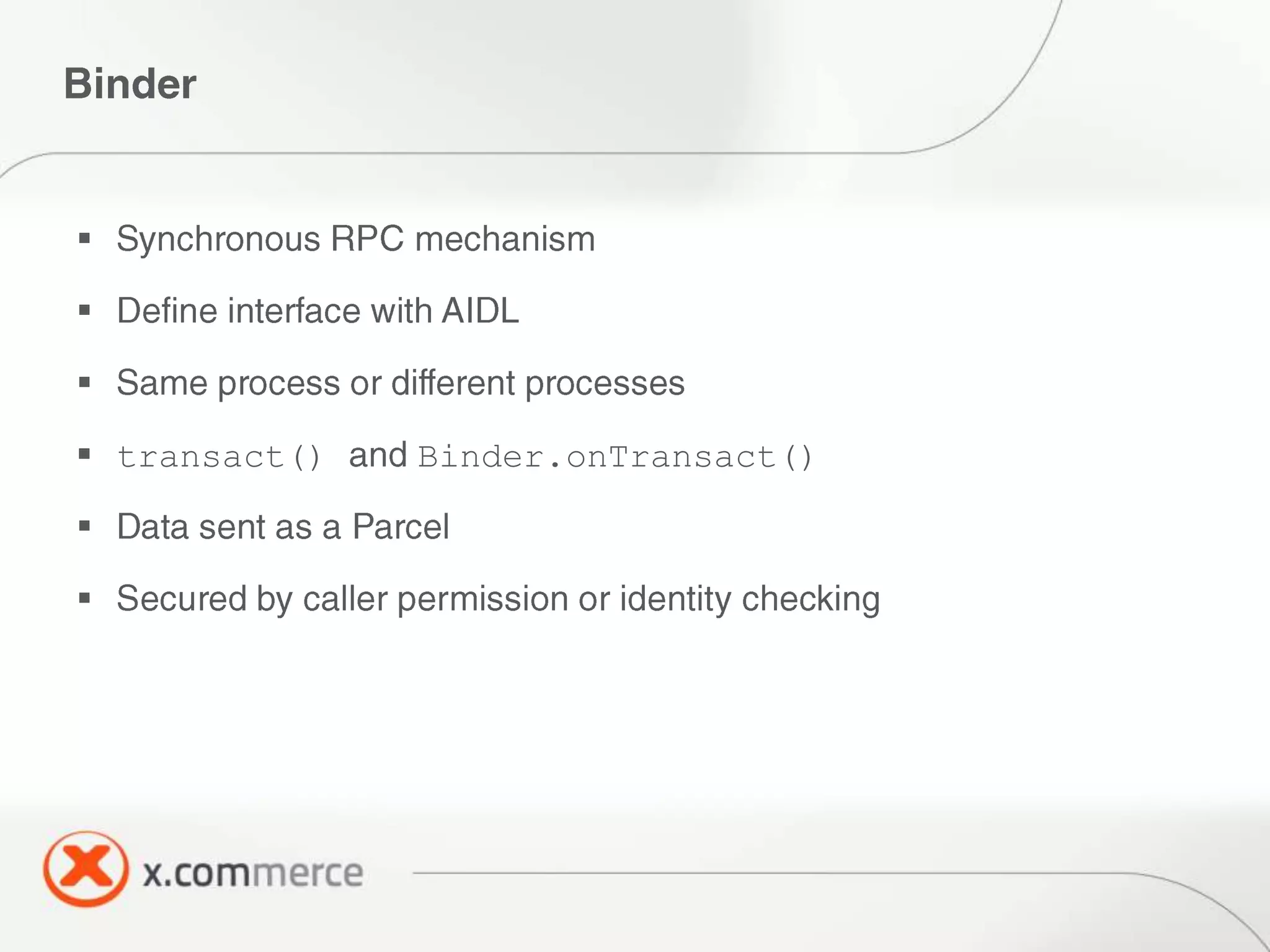
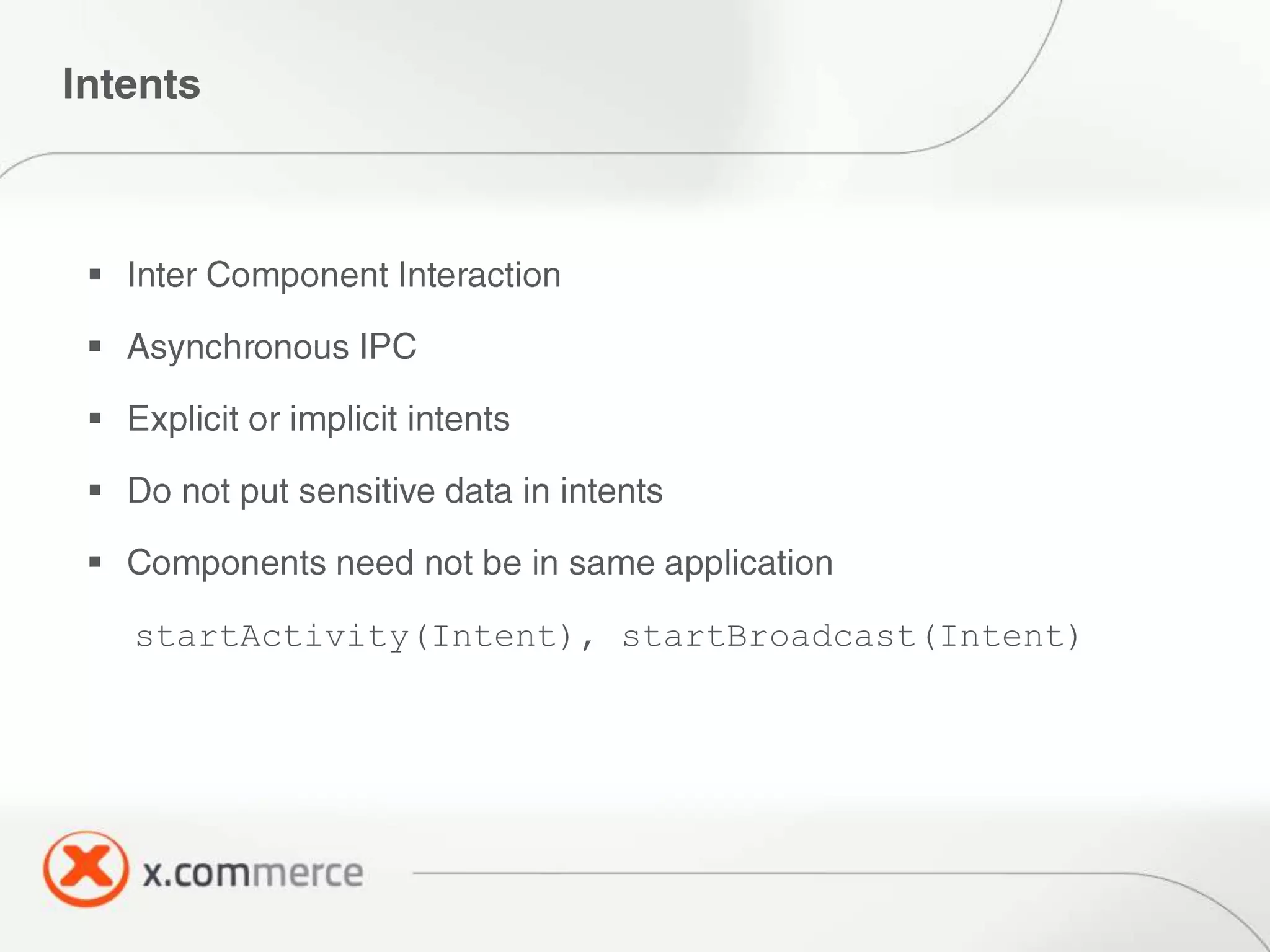
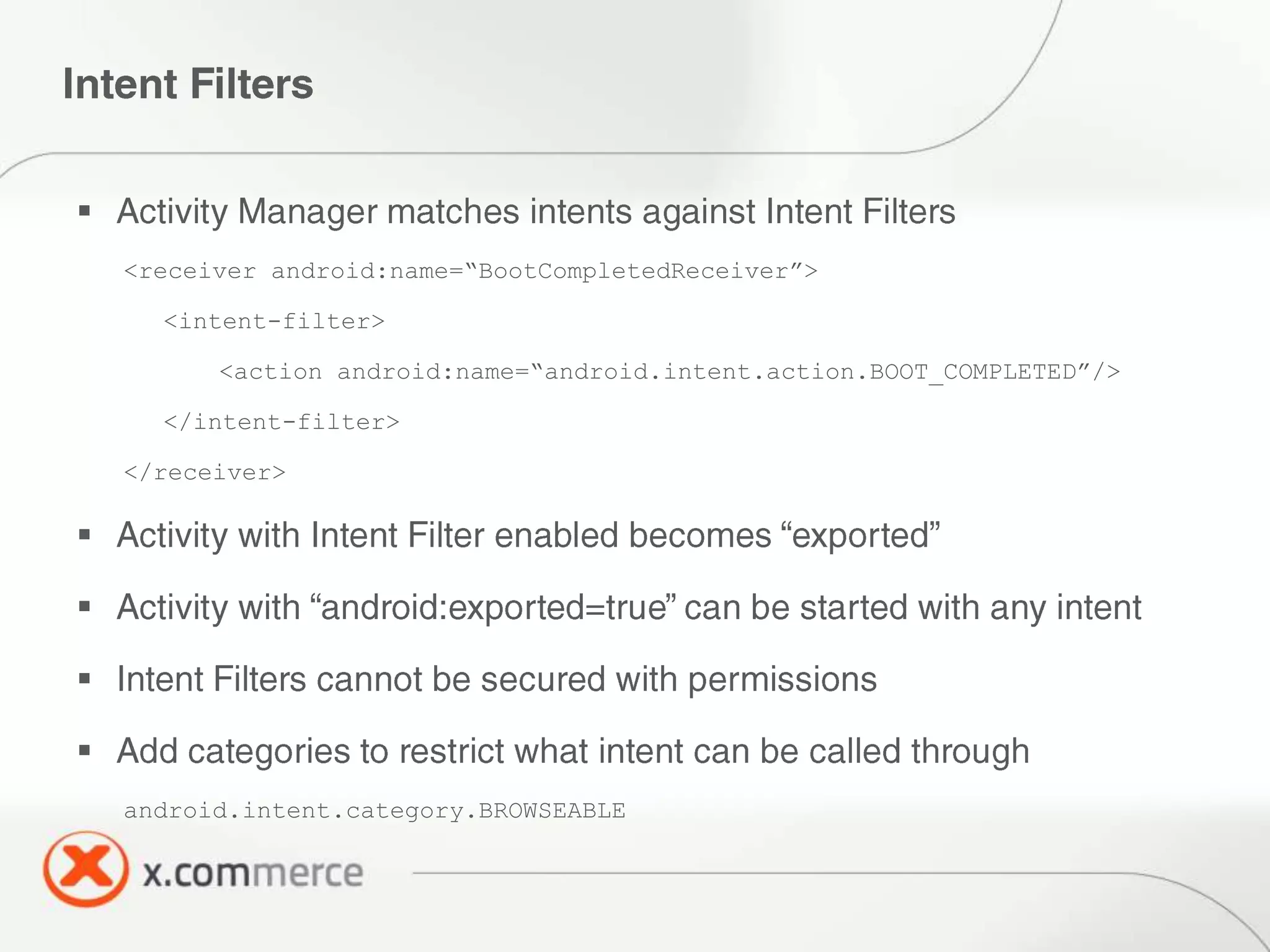
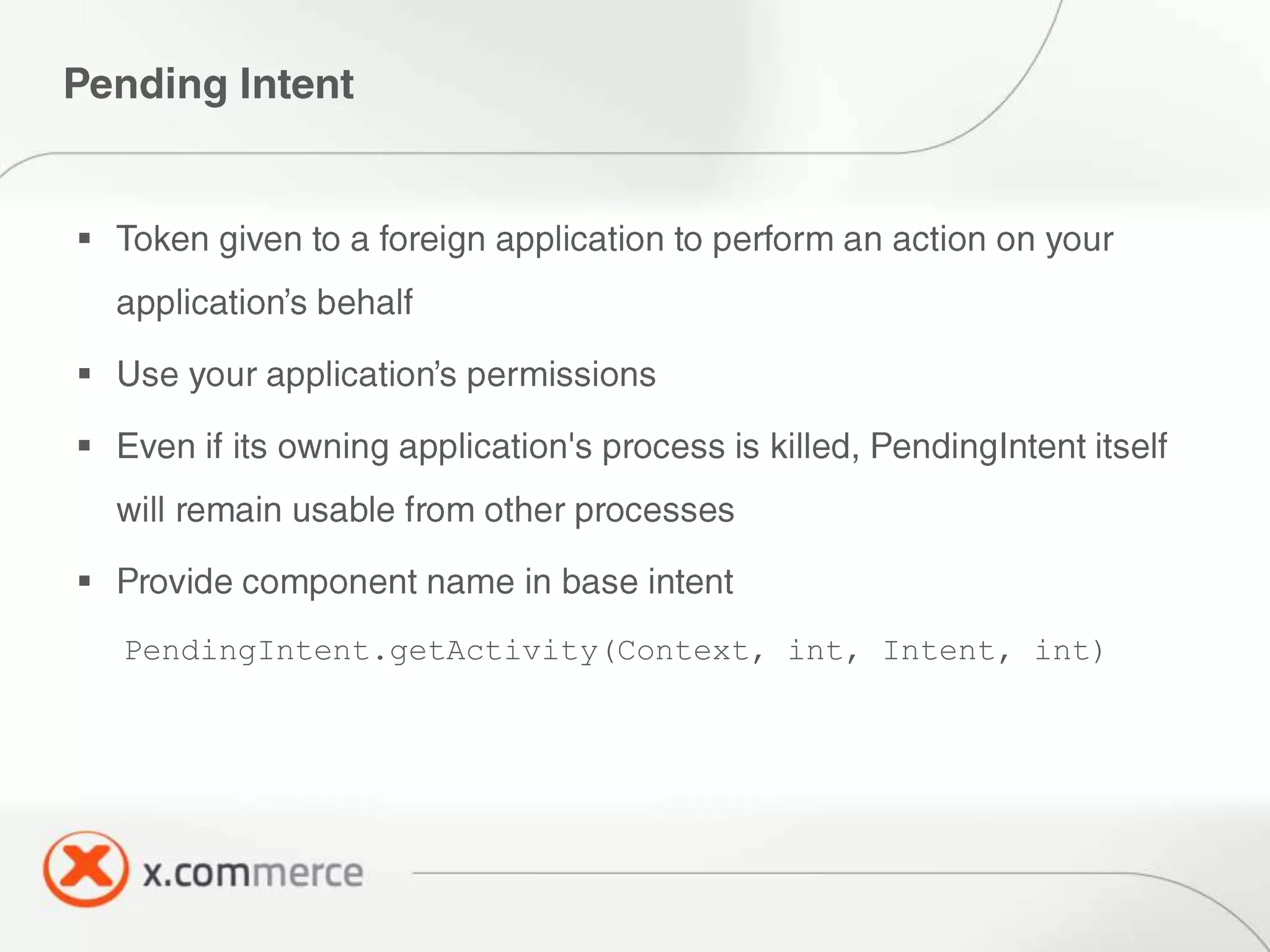





The document outlines key elements of Android security essentials, including OS architecture, permissions, and application components such as activities and broadcast receivers. It provides technical specifics on various Android permissions and system interactions. Pragati Ogal Rai, a mobile technology evangelist, is credited with the content and can be contacted for further inquiries.






















