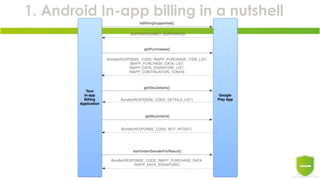
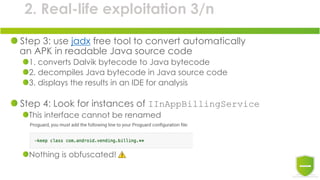
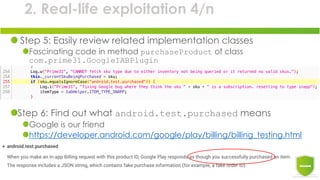
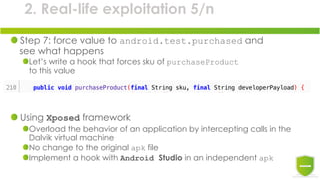
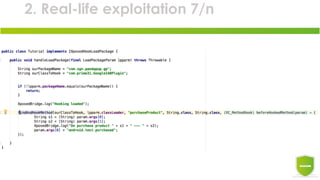
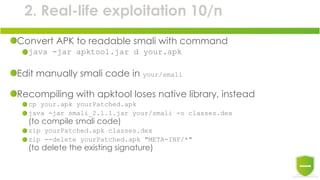
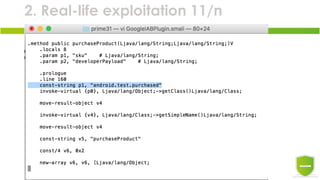
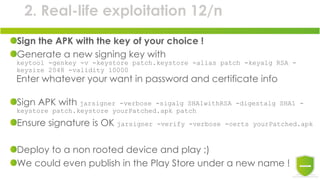
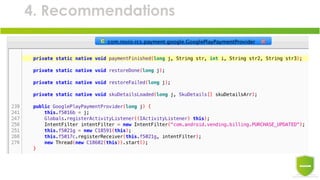
The document discusses the exploitation of Android's in-app billing feature through Java reverse engineering and the Xposed framework, detailed with a case study on the game 'Pandapop'. It outlines a process for manipulating application code to obtain free in-game credits, highlighting security flaws in the in-app billing system. The author concludes with lessons learned and recommendations for improving security measures in Android applications.