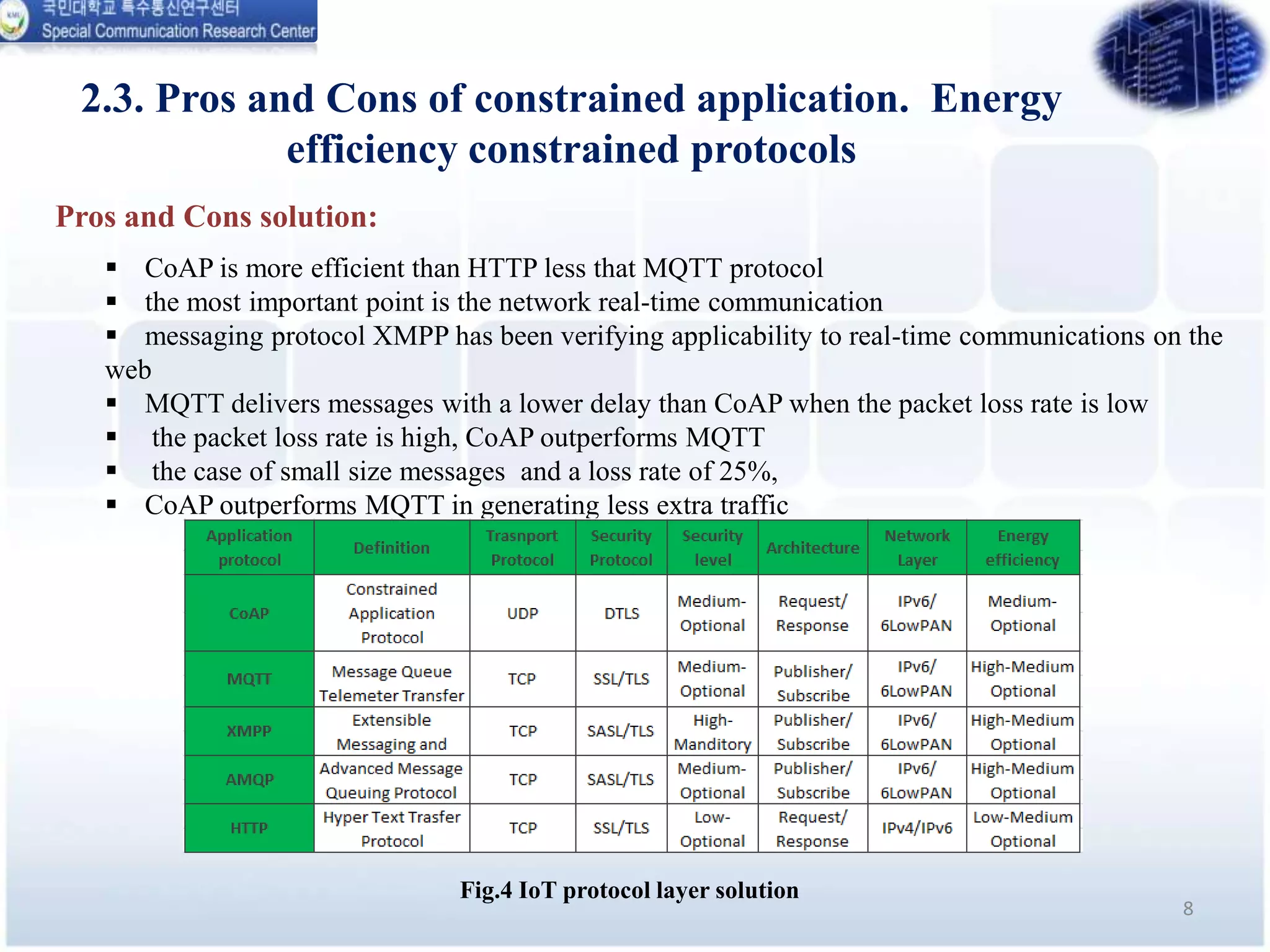
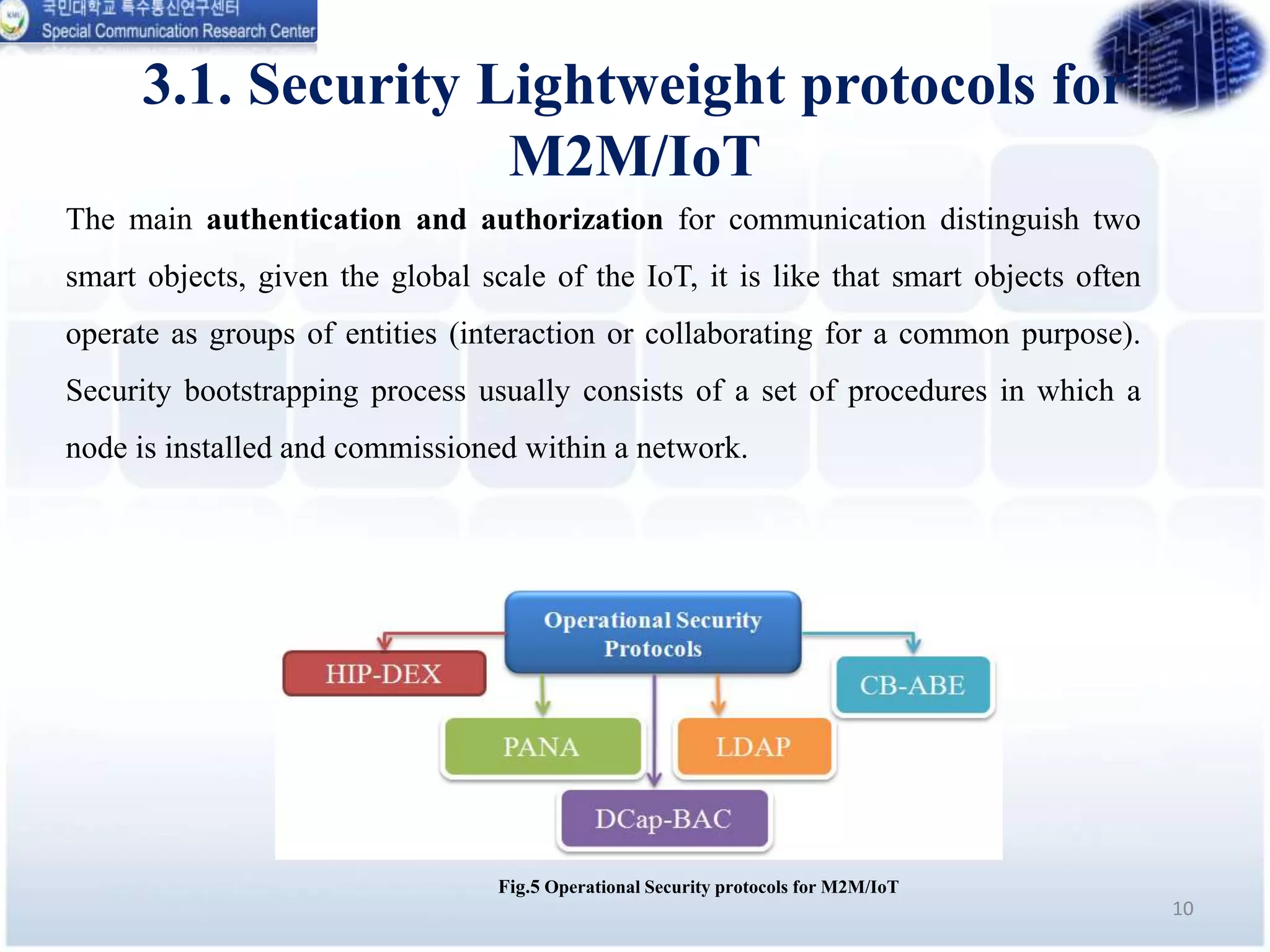
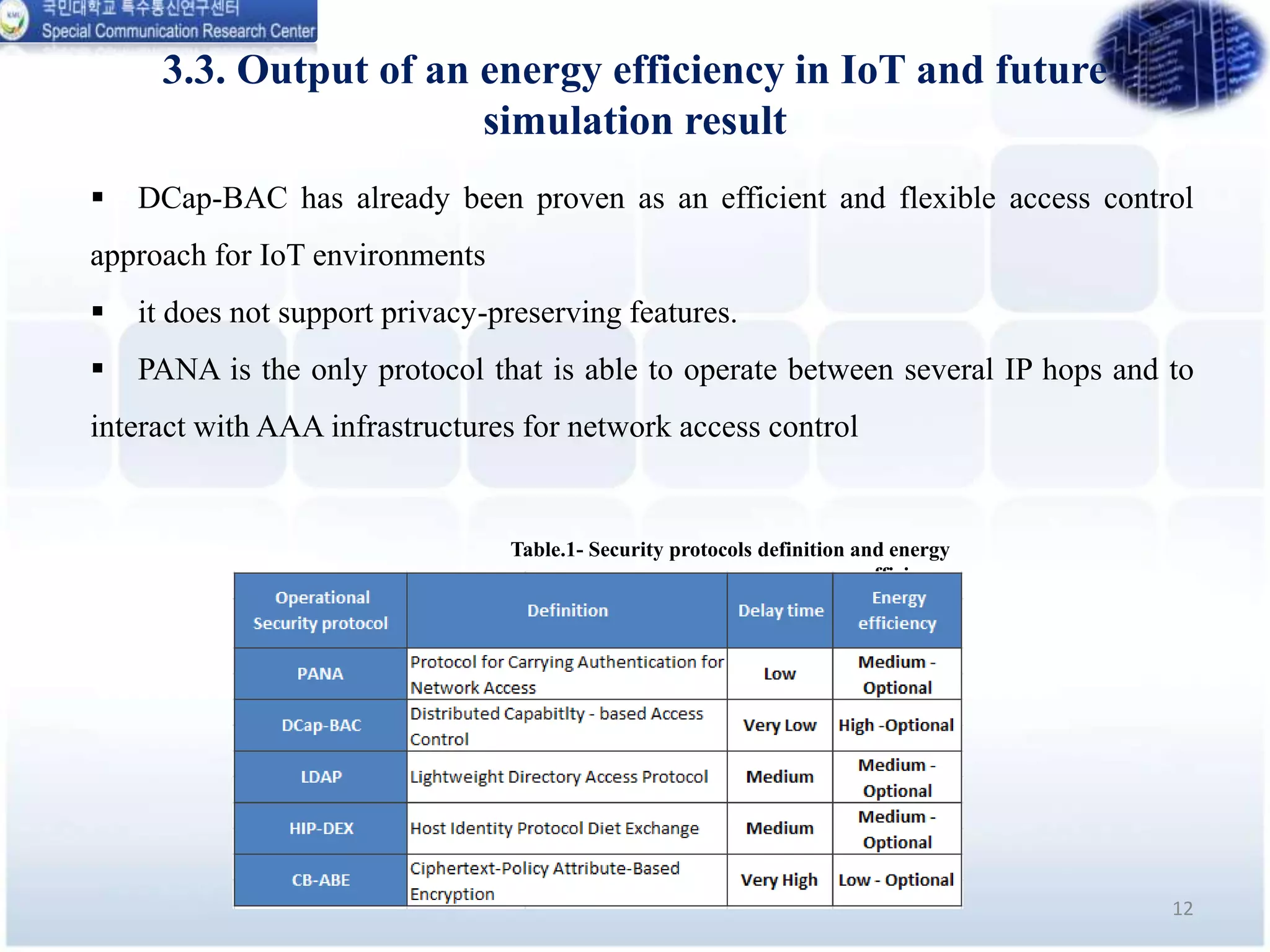
This document analyzes the energy efficiency of lightweight security protocols for machine-to-machine (M2M) and internet of things (IoT) environments. It discusses resource-constrained IoT device protocols like CoAP, MQTT, and XMPP. It also examines security protocols like PANA, LDAP, HIP-DEX, CB-ABE, and XACML. Simulation results are presented comparing the energy efficiency and performance of these protocols. The conclusion discusses plans to simulate protocols over delay tolerant networks and develop underwater variants of CoAP and MQTT with security.