The document discusses challenges and security issues related to the Internet of Things (IoT). It notes that while IoT provides many benefits across various industries like healthcare, transportation, and more, it also faces challenges. Key challenges include the large number of devices and sensors requiring unique identification, and the need for proper data storage, management, and processing. Regarding security issues, the document states that IoT devices are vulnerable to attacks due to limited computing resources. It proposes using cloud computing and other techniques to help build a more secure IoT infrastructure.
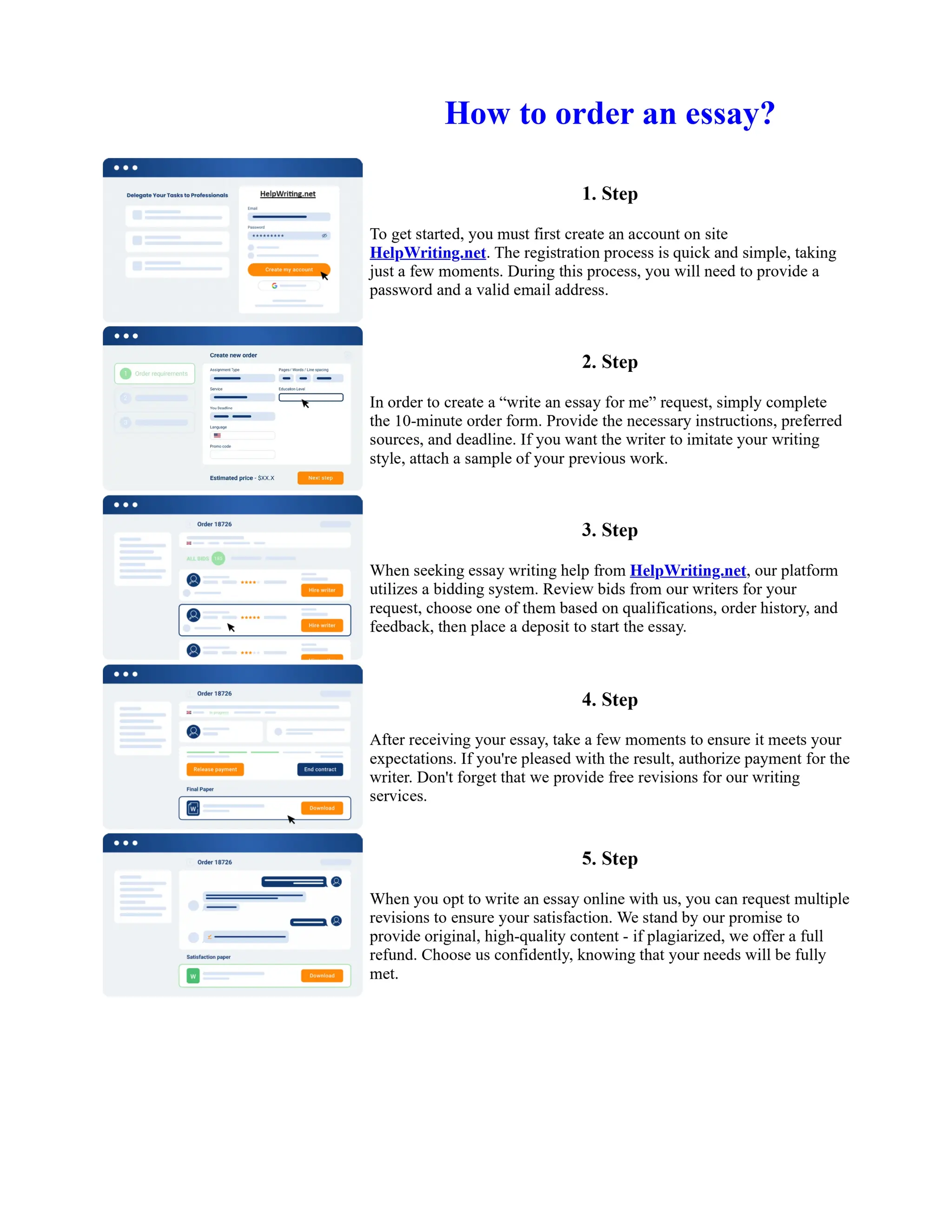
![What Is Routing Overhead Of The Network
PDR for proposed EEHM is maximal than other technique in WSN network. Maximum PDR value
for proposed approach is 0.98. Here EARC algorithm provides almost similar characteristics as of
EEHM whose PDR value is 0.96. Whereas the others existing techniques values are 0.4, 0.47 and
0.58 respectively. e. Routing Overhead of the Network Fig 7. Comparison of routing overhead
Figure 7 demonstrates the performance comparison plot for the routing overhead in the WSN for the
proposed approach. Through the simulation graph, it is clearly observed that proposed EEHM
provide effective routing overhead than other existing algorithms. Also, it is identified that EEHM
algorithm also provides almost similar characteristics as of EEHM algorithm. Other ... Show more
content on Helpwriting.net ...
The miss ratio is also minimized through an efficient buffer partition and management. In our future
study, the proposed protocol needs to be modified and tested to adopt the real–time dynamic
environment. The protocol needs to be tested for real–time WSN applications that require diverse
reliability required in the sensing field. 7– REFERENCES [1] Arbi, I. B., Derbel, F., & Strakosch, F.
(2017, May). Forecasting methods to reduce energy consumption in WSN. In Instrumentation and
Measurement Technology Conference (I2MTC), 2017 IEEE International (pp. 1–6). IEEE. [2]
Kułakowski, P., Calle, E., & Marzo, J. L. (2013). Performance study of wireless sensor and actuator
networks in forest fire scenarios. International journal of communication systems, 26(4), 515–529.
[3] Zhang, H., Zheng, M., Li, J., Yu, H., & Zeng, P. (2010, June). Redundancy control for
reliability–lifetime tradeoff in energy harvesting wireless sensor networks. In Computer Design and
Applications (ICCDA), 2010 International Conference on (Vol. 2, pp. V2–539). IEEE. [4] Bakr, B.
A., & Lilien, L. (2011, May). LEACH–SM: A protocol for extending wireless sensor network
lifetime by management of spare nodes. In Modeling and Optimization in Mobile, Ad Hoc and
Wireless Networks (WiOpt), 2011 International Symposium on (pp. 375–375). IEEE. [5] Hadim, S.,
& Mohamed, N. (2006). Middleware: Middleware
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/whatisroutingoverheadofthenetwork-231118164824-bec1373a/75/What-Is-Routing-Overhead-Of-The-Network-1-2048.jpg)

![1. 2 IEEE 802. 15. 4 : Lab Analysis
2.3.2 IEEE 802.15.4 IEEE 802.15.4 is the mostly used IoT standard for MAC. It has Source &
Destination address for communicating. In a word it follows frame format. Its specific MAC
features can be: Slot frame Structure, Scheduling, Synchronization, Channel Hopping, Network
formation. 2.3.3 IEEE 802.11 AH IEEE 802.11ah is a light version. Its applicable for low–energy.
For Laptop, smart mobile, smart Television and other digital devices using IEEE 802.11.AH. The
basic 802.11ah MAC layer features include: Synchronization Frame, Efficient Bidirectional Packet
Exchange, Short Mac Frame, Null Data Packet, Increase Sleep Time.2.3. 2.3.4 WirelessHART
WirelessHART is a datalink protocol that operates on the top of IEEE 802.15.4 PHY and adopts ...
Show more content on Helpwriting.net ...
HomePlug suite covers both PHY and MAC layers and has three versions: HomePlug–AV,
HomePlug–AV2, and HomePlugGP. [29] 2.3.10 G.9959 G.9959 is a MAC layer protocol from ITU,
designed for low bandwidth and cost, half–duplex reliable wireless communication. [30] 2.3.11
LTE–A Long–Term Evolution Advanced (LTE–A) is a set of standards designed to fit M2M
communication and IoT applications in cellular networks. LTE–A uses OFDMA (Orthogonal
Frequency Division Multiple Access) as a MAC layer access technology, which divides the
frequency into multiple bands and each one can be used separately. The architecture of LTE–A
consists of a core network (CN), a radio access network (RAN), and the mobile nodes. [31] Figure:
LTE–AArchitecture The CN is responsible for controlling mobile devices and to keep track of their
IPs. RAN is responsible for establishing the control and data planes and handling the wireless
connectivity and radio–access control. RAN and CN communicate using S1 link where RAN
consists of the eNB (E–UTRAN Node B)'s to which other mobile nodes are connected wirelessly.
2.3.12 LoRaWAN LoRaWAN is a newly arising wireless technology designed for low–power WAN
networks with low cost, mobility, security, and bi– directional communication for IoT applications.
[32] 2.3.13 Weightless Weightless is another wireless WAN technology for IoT applications
designed by the Weightless Special Interest Group (SIG) [33]
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/whatisroutingoverheadofthenetwork-231118164824-bec1373a/75/What-Is-Routing-Overhead-Of-The-Network-5-2048.jpg)


![Internet Of Things : Challenges And Security
Internet of Things: Challenges and Security
Srikant Reddy Duvvuru
Department of Computer Engineering San Jose State University
San Jose, CA–95112
Abstract –– Internet of Things is rapidly gaining popularity in the recent days. The availability of
different variety of sensors and wireless technologies is responsible for the existence of the Internet
of Things. The Internet of things finds a large number of applications in numerous fields such as
Energy sector, Healthcare, Transportation, Business field and Agriculture. This paper mainly
concentrates on the challenges and security issues of the Internet of things. In addition to that the
paper provides solutions to these issues with the help of a construction of secure IoT ... Show more
content on Helpwriting.net ...
Apart from wireless sensors and RFID's there is also a need to recognize each and every object
uniquely, which requires a large pool of IP Addresses, so undoubtedly IPv6 is the best choice. Cloud
computing is one of the emerging technologies which can give IoT a new dimension promising
proper storage, management and processing of the data.
According to Forrester in [2] "IoT uses information and communications technologies to make the
critical infrastructure components and services of a city administration, education, healthcare, public
safety, real estate, transportation and utilities more aware, interactive and efficient". It has the
capability to bring down the cost of all the major sectors like Healthcare, Transportation, Energy,
Education and Real State.
Security is one of the major concerns of the internet of things. As billions of objects will be
connected to it in the future. There has been an ever increasing need to address the security issues
related to the IoT. The data transmission across the networks need to be monitored and protected
from thefts and unauthorized malicious attacks. Different types of protocols and security measures
are available in the existing internet scenario but most of them have limited applicability in the
domain of IoT. Fig: 1 Survey of obstacles on IoT development.
According to the survey conducted by VDC Research as shown in fig 1,
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/whatisroutingoverheadofthenetwork-231118164824-bec1373a/75/What-Is-Routing-Overhead-Of-The-Network-10-2048.jpg)




![Importance Of Region-Based Threshold Threshold Sensitive...
Region–Based Enhanced Threshold Sensitive Stable Election Protocol
Shailie Rai
M.Tech
Department of Electronics and Communication
Babu Banarasi Das University
Lucknow, India shailierai11@gmail.com Ashutosh Rastogi
Assistant Professor
Department of Electronics and Communication
Babu Banarasi Das University
Lucknow, India ashutoshrastogi1984@gmail.com Abstract–A unique Region–Based Enhanced
Threshold Sensitive Stable Election Protocol (RBETSSEP) is proposed in this paper for the rise in
stability period and to enhance the lifespan of the heterogeneous wireless sensor networks
(HWSNs). It provides the improvement in ETSSEP protocol by dividing the sensing area into nine
regions and these are dedicated to the different ... Show more content on Helpwriting.net ...
Across the different field of applications, several routing protocols have been proposed to achieve
enhanced network lifetime via energy efficient transmission [5]. The main cause for the energy
depletion in batteries in WSN is the communication required to transmit and receive data to other
nodes. Mostly the energy consumption in the network is due to transmission and reception activities.
However, the energy consumed for the processing operation is less important than the energy used
for communication [6].
The wireless sensor networks mainly comprise stationary and mobile sensors that are deployed
randomly inside the network and they collect data from the surroundings via wireless
communication links [7, 8].
Single–hop or multi–hop protocols are used to further transmit collected data to one or more base
stations or sink [9]. An enormous amount of structured and unstructured data known as big data is
generated rapidly that requires a flexible and reliable storage infrastructure [10]. Sensor nodes
transfer the obtained useful information from a defined network either directly or via a chain of CHs
to the BS [11]. In designing a routing protocol for WSN the main concern is the energy efficiency
[12]. Thus, energy depletion of one node may vary from other, i.e., nodes near the BS or sink have
more energy depletion than the other nodes. This results in the creation of energy holes near the sink
[13].
Further transmission of data towards the sink is not
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/whatisroutingoverheadofthenetwork-231118164824-bec1373a/75/What-Is-Routing-Overhead-Of-The-Network-21-2048.jpg)









![Wireless Sensor Network
INDEX
1. INTRODUCTION 1 1.1 Wireless sensors Deployment 2 1.2 Wireless Sensor and Actor Networks
3 1.3 The Physical Architecture of WSANs 3 1.4 Difference between WSNS and WS 4 1.5
Requirement of WSNs 5
2. Wireless Ad–Hoc Network 5
3. Current Issues and solution 6 3.1 Key management issue for future 9
4. Advantages, Disadvantages and Applications of WSNs 10
5. Conclusion 11
6. References 12
List of figures
Figure 1 Working principle of WSNs 1
Figure 1.3 The Physical Architecture of WSANs 4 ... Show more content on Helpwriting.net ...
For achieving this goal, physical deployment of the nodes and the sample periods are pre–
determined by the scientists. To ensure that data is delivered as expected is the real role of the
network. For achieving this goal it is necessary to reduce the network complexity as much as
possible from the services and its application. It is possible to optimize communication performance
for that application–not for a generic set of users as each node executes a single application. For
achieving this it is necessary to translate them into a set of goals for media access protocol to satisfy
the requirement of wireless sensor network deployment and monitoring application. For WSNs
application, the common goals for a MAC protocol are:
1) Collision Avoidance in effective manner
2) High Data Rate and Efficient Channel Utilization
3) Network protocol should be Reconfigurable
4) Low Power Operation
5) Large number of nodes should be scalable
6) RAM size, Small Code, and Simple Implementation
7) Tolerant to changing RF/Networking conditions.
The B–MAC is proposed to meet these goals, a configurable MAC protocol for WSNs. It is simple
in both for implementation and design. MAC protocol support a wide variety of sensor network
workloads by factoring out some functionality and exposing control to higher services. In contrast to
the classic monolithic MAC protocol this minimalist model of MAC protocol is designed [1].
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/whatisroutingoverheadofthenetwork-231118164824-bec1373a/75/What-Is-Routing-Overhead-Of-The-Network-43-2048.jpg)


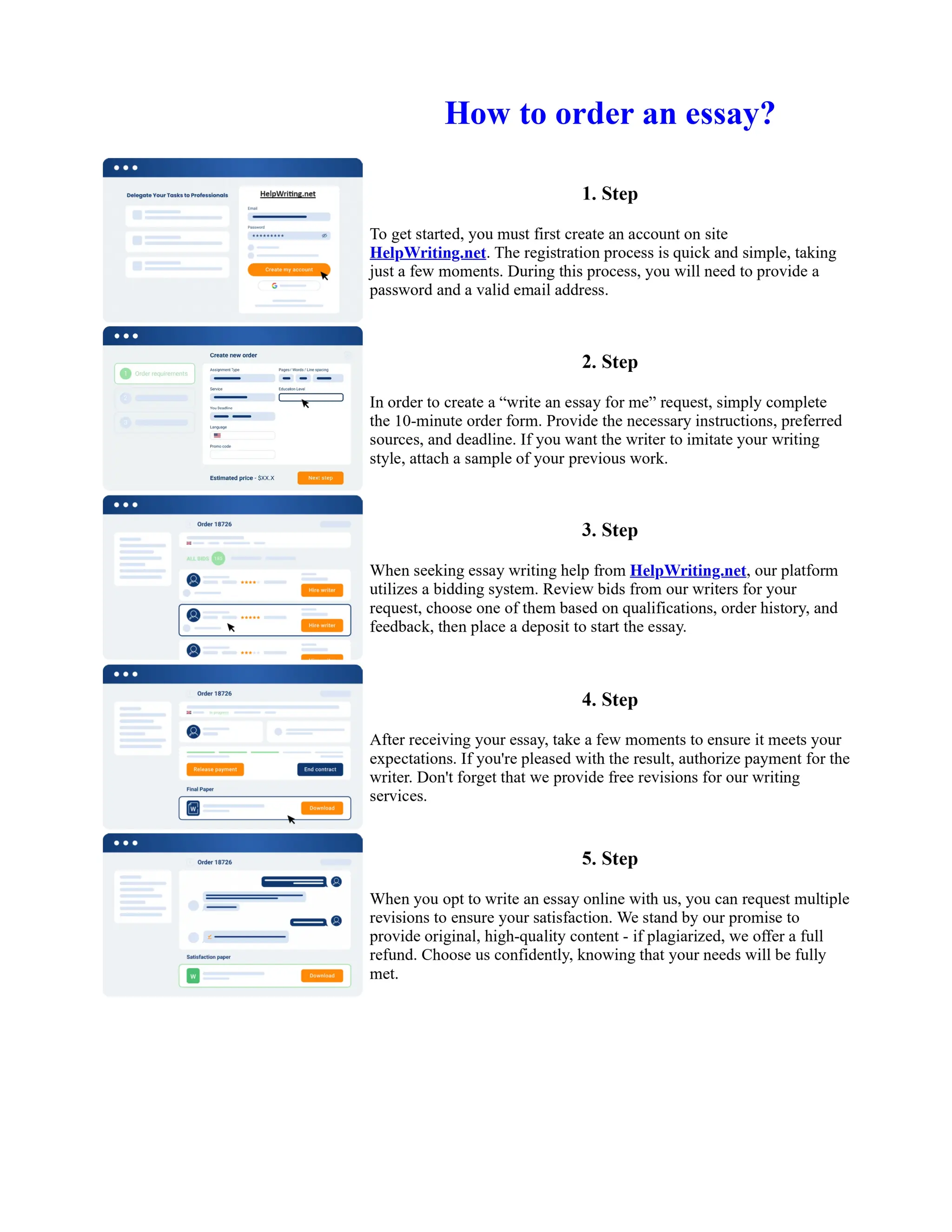
![Mobile Wireless Network Essay
Recent progress in mobile wireless network has provided a major impulse towards the development
of self–organized, self–created, and rapidly deployable network architecture referred to as Mobile
Ad Hoc Networks (MANETs). Although the application area of MANETs was initially proposed for
environments of disaster recovery and battle–field communications, the evolution of the Multimedia
Technology and the commercial interest of companies to reach widely civilian applications, have
made Quality of Service in such networks more important.
Many different protocols have been proposed to support Quality of service in MANETs, each based
on different intuitions & assumptions. Current proposals in the literature have attempted to provide
Quality of ... Show more content on Helpwriting.net ...
A Mobile Ad Hoc network is receiving attention due to several salient characteristics such as:
Dynamic topologies
Bandwidth–constrained links
Energy constrained operation
Limited physical security.
Therefore the routing protocols for wired networks cannot be directly used for wireless networks.
Some examples of the possible uses of Ad Hoc networking include students using laptop computers
to participate in an interactive lecture, business associates sharing information during a meeting,
soldiers relaying information for situational awareness on the battlefield and emergency disaster
relief personnel coordinating efforts after a hurricane or earthquake. A MANET uses multi–hop
routing instead of a static network infrastructure to provide network connectivity. Several routing
protocols have been proposed for MANETs. Initially, in this work, number of ways of classification
or categorization of existing routing protocols and the survey on the performance comparison of
important protocols such as AODV [2], DSR [3] and DSDV [4] are presented. A number of
researchers have done the performance analysis of Ad Hoc Routing protocols over the years using
different simulators like NS2, Qualnet, Opnet etc. From the survey of QoS Models and Protocols of
the IP network such as IntServ, DiffServ, FQMM (Flexible QoS Model for MANET), RSVP etc., it
is observed that they
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/whatisroutingoverheadofthenetwork-231118164824-bec1373a/75/What-Is-Routing-Overhead-Of-The-Network-49-2048.jpg)
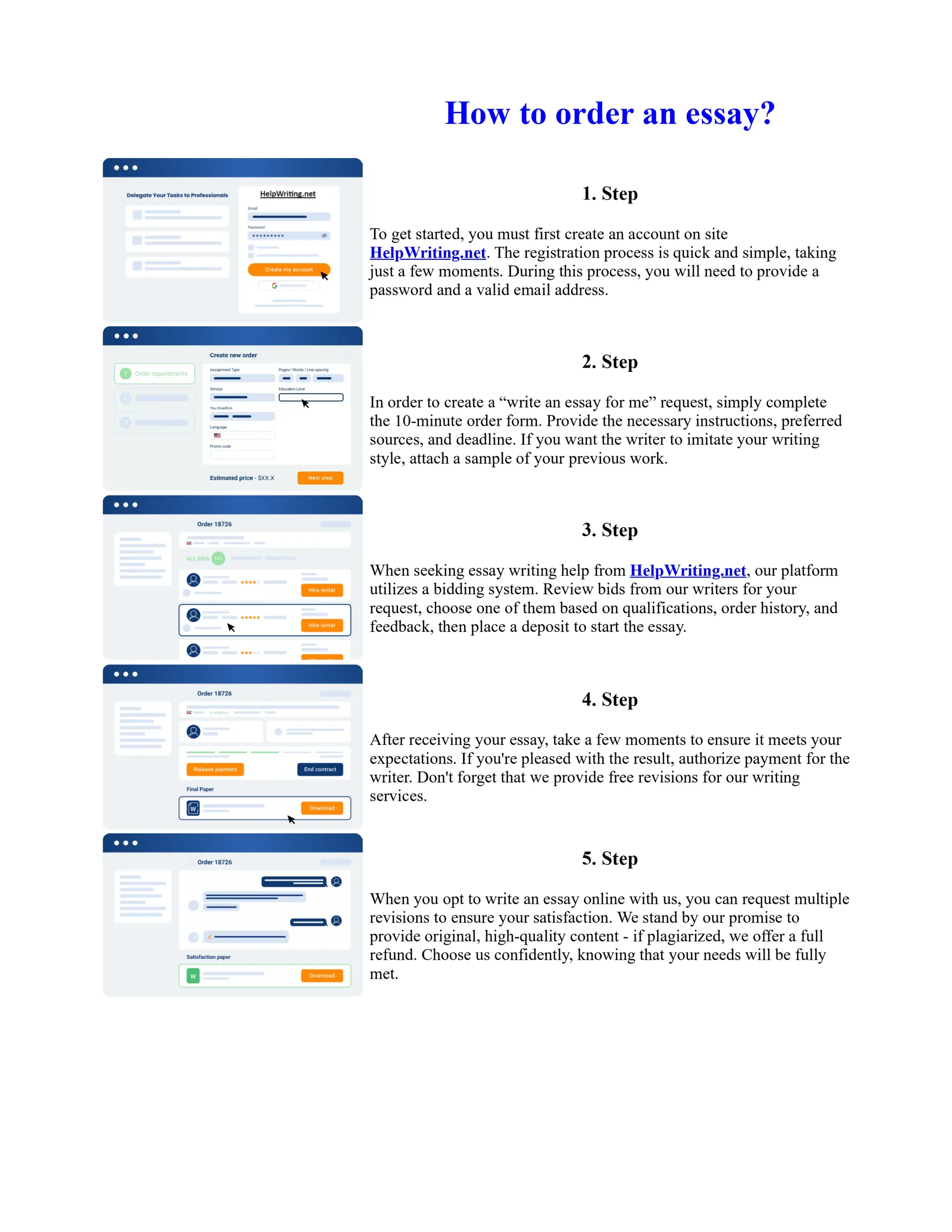
![Paper On Wireless Sensor Networking
Amandeep Singh1, Sunny Behal et al. [18]: Wireless sensor networks is very important field in
today's technology and one may concern about the life time of sensors as they have no facility to
change the battery of those sensors inside the field. Wireless Sensor Networks are prone to node
failure due to power loss. In order to provide reliable service through the network, the network
should be self–adjusting and must have adaptable properties as required from time to time. Here in
this research we have proposed a new algorithm which is capable of not only to do optimize routing
even with that it has the benefit to overcome through pits creating problem around the sink. In this
research, we have investigated the impact of sink mobility on ... Show more content on
Helpwriting.net ...
The collection of sensor nodes by enabling cooperation, coordination and collaboration among
sensor nodes is formed Wireless Sensor Network (WSN); the WSN consists of multiple autonomous
nodes with a base station.
.
I.F. Akyildiz et al. [21] performed a survey on WSNs in 2002. Previous works concentrate wired
sensor network concepts and architecture. But, this paper described the concept of Wireless sensor
networks which has been made viable by the convergence of MEMS Technology, wireless
communications and digital electronics. Then, the communication architecture for sensor networks
is outlined, and the algorithms and protocols developed for each layer in the literature are explored.
In the future, this wide range of application areas will make sensor networks an integral part of our
lives. F. L. Lewis et al. [22] conducted a review on wireless sensor networks in 2004. This paper
performed a review on wireless sensor network technologies, protocols and applications. In future,
conduct a review based on wireless sensor network routing techniques, power consumption
techniques, IEEE standards and MAC protocols.
Jennifer Yick et al. [23] performed a survey on wireless sensor network in 2008. The goal of survey
is to present a comprehensive review of the recent literature since the publication of [I.F. Akyildiz et
al., A survey on sensor networks, IEEE Communications Magazine, 2002]. This paper summarized
and compared different proposed designs,
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/whatisroutingoverheadofthenetwork-231118164824-bec1373a/75/What-Is-Routing-Overhead-Of-The-Network-51-2048.jpg)
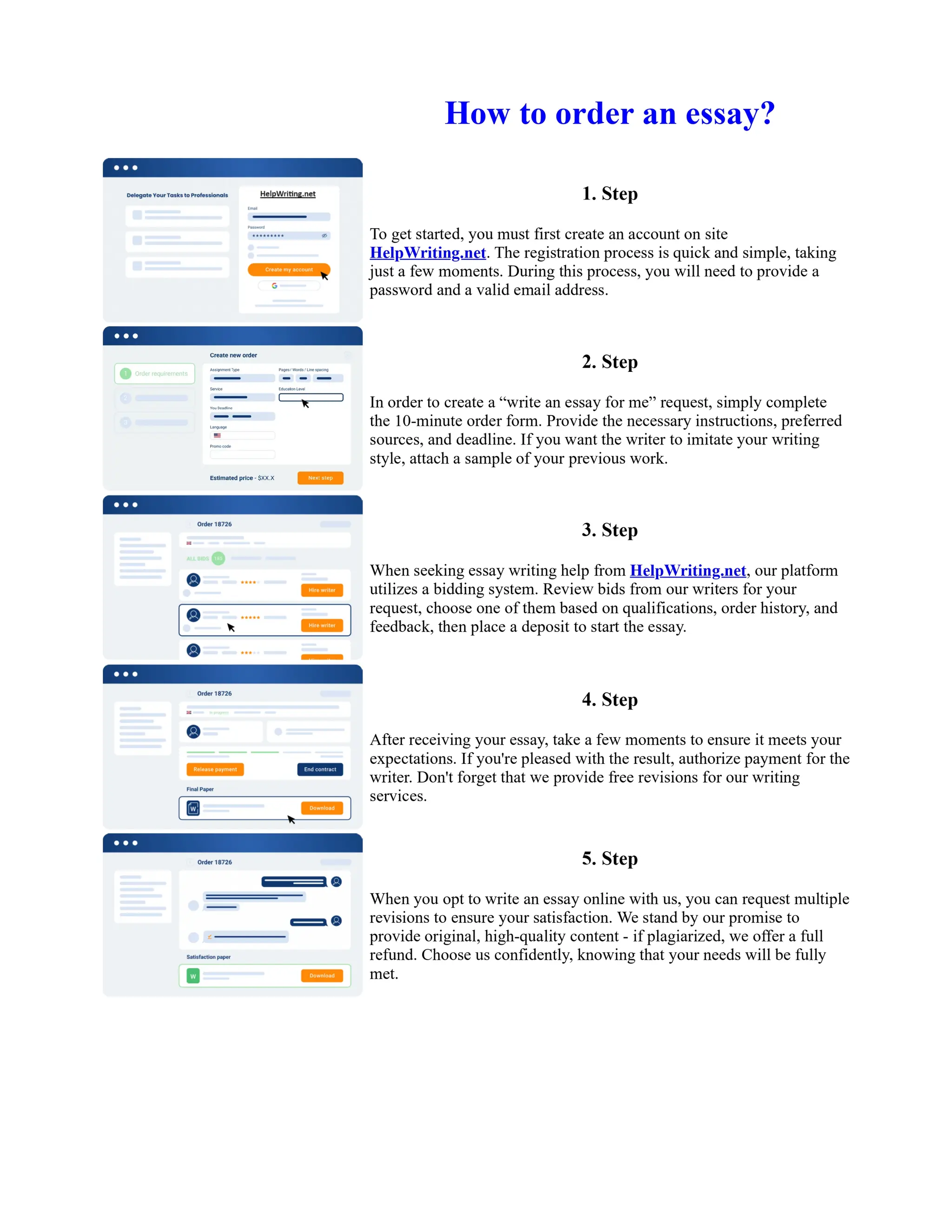

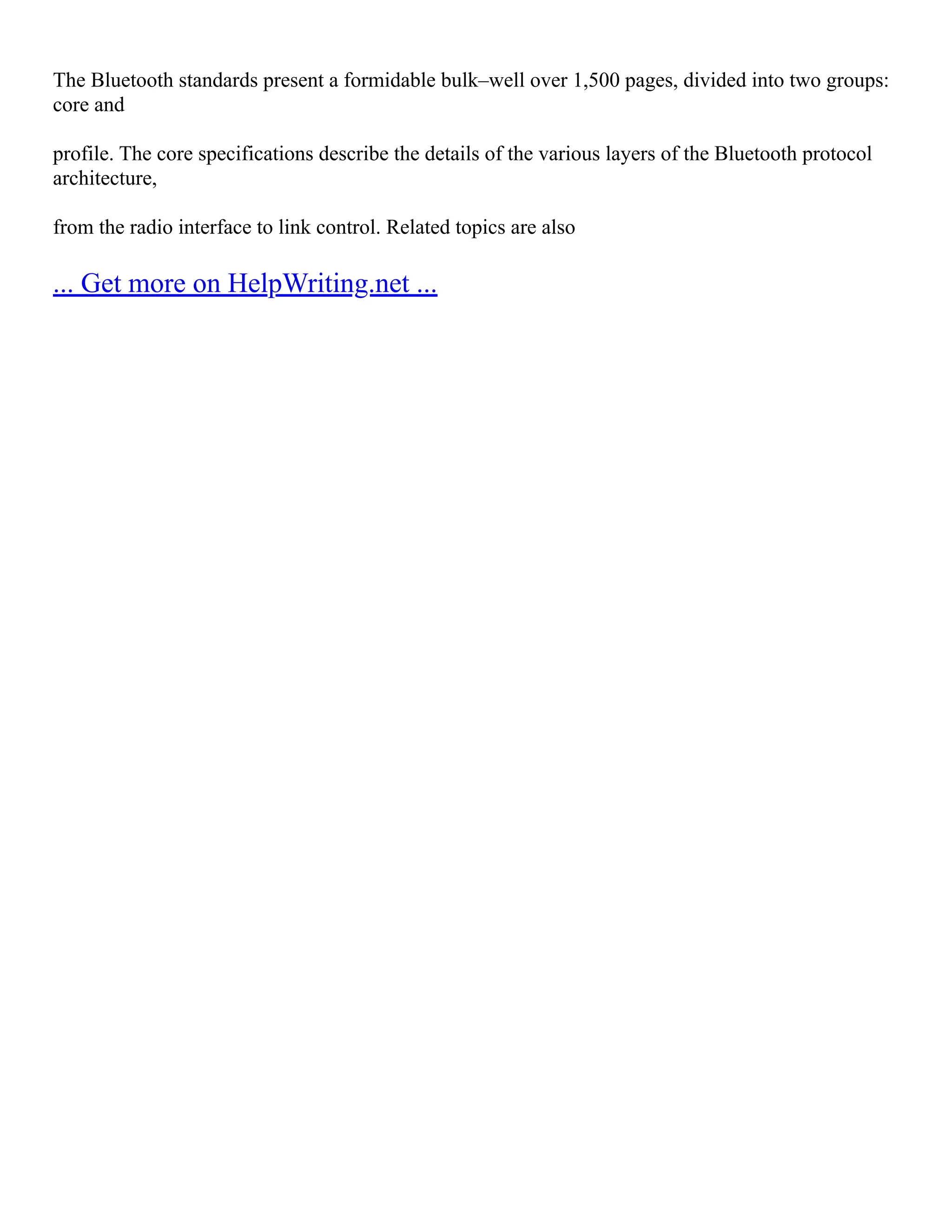



![What Are The Advantages And Disadvantages Of Network...
Chapter 4 Simulation & Experiment
4.1 Network Simulators "According to dictionary, Simulation can be defined as ―reproduction of
essential features of something as an aid to study or training." In simple words, this process is called
where we can build one model of math called simulated in order to solve the problem of the system.
In order to simulate the ad hoc network Networks or so–called MANET There are many simulation
available networks such as QUALNET , OPENET and NS2 etc[25]. First part of this section, we
will take the overview of all such networks with their usage, advantages and disadvantages of using
it. For our simulation, we have to finalize the one out of them depending on their availability and
problem compatibility ... Show more content on Helpwriting.net ...
Choice in which the routing is done along multiple paths because its provides the number of routing
protocols .
NS2 is developed as the completely object oriented network simulator by Using the technologies
such as OTcL and CPP. The class hierarchy which is presented in the OTcL and C++ interpreted is
very much supported by the network simulator in which there is one to one mapping in between
compile hierarchy and the class in the interpreted hierarchy .
NS2 contain two types of programming languages used that we have discussed above, such as C ++
and OTcl :
Use C++ : is used for the speed efficiency in the simulation of the networks.
Use OTcl: the reason is that OTcl language is suitable for the programs and configurations which are
demanding for the fast and frequent network changes.
Thus such tool is very flexible for the useNs–2 as it also allows user to existing protocols for their
application simulations as well as to develop their network protocol in order to extend the
functionality of the tool. Network simulator also helps for the performance measurement from the
trace analysis functionality which is very important for the research purposes in order to measure the
efficiency of particular application or particular routing protocol. NS2 is open source and free
software tool which is widely available for downloads from the Internet. It was initially developed
for the UNIX systems
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/whatisroutingoverheadofthenetwork-231118164824-bec1373a/75/What-Is-Routing-Overhead-Of-The-Network-62-2048.jpg)



![Wireless Sensor Network Essay
I. INTRODUCTION
Wireless Sensor Network consists of highly distributed
Autonomous sensors nodes to monitor physical or environmental conditions, such as temperature,
sound, vibration, pressure, motion or pollutants and to cooperatively pass their data through the
network to a receiver (destination) [1] [7].
A sensor node consist of a radio transceiver with internal antenna or connected to external antenna, a
microcontroller and electronic circuits for interfacing with the sensors and energy source such as
battery[1][7].
A. Topologies:
Topologies used in Wireless Sensor Network are Mesh, Star, Ring, Tree, and Bus, Fully connected.
Mesh Network.
B. Characteristics:
Power consumption constrains for nodes using batteries or energy ... Show more content on
Helpwriting.net ...
Wireless Sensor Network Protocols:
Physical layer: Sonet , ISDN
Data link Layer: Frame Relay, FDDI, Ethernet
Network Layer: RIP,OSPF, EGP,IPX,IPv6,ARP
Transport Layer: TCP, UDP, SPX
Application Layer: BOOTP, DHCP, HTTP, DNS
Classifications of the Protocols
Protocols are classified into the following major categories.
TCP/IP IP, TCP, UDP, SMTP, POP3, RIP, FTP, DHCP
Cellular GPRS, GSM, WAP and CDMA
VOIP SIP, RTP, MGCP and H.323
General Frame Relay, ATM, X.25, PPP[1].
II.OBSTACLES IN WIRELESS SENSOR SECURITY
Wireless sensor nodes[2] have limited resources such as limited memory and limited power. There is
unreliable communication in wireless sensor network that leads to threat to sensor security. The
security of network depend on communication which relies on protocol.](https://image.slidesharecdn.com/whatisroutingoverheadofthenetwork-231118164824-bec1373a/75/What-Is-Routing-Overhead-Of-The-Network-72-2048.jpg)



![Wireless Network Method Using Smart Grid Communications
WIRELESS NETWORK METHOD USING IN SMART GRID COMMUNICATIONS
Ehsan Dolatshahi
Independent Study
April 22, 2015
Introduction
The old generation of electrical power grid has taken care of our needs in the past. However, as our
world progress technologically, so do the expectations from different infrastructures around us.
Smart grid is an initiative to completely restructure the electrical power grid to meet the current and
future requirements of its clients. Upgrading our electrical power grid could bring novel security
vulnerabilities into the system. Thus, security is one of the key parts in smart grid technology. Smart
grid technology also puts more reliability demands on WAN (wide area network) infrastructures. [1]
A smart grid is an intelligent electricity network that integrates the actions of all users connected to
it and makes use of innovative information, control, and communication technologies to save
energy, cut cost, and raise reliability and transparency. The smart grid is an upgrade to the current
electrical power structure. Meaning, on top of the functionality of our existing power system, it has
upgraded with some novel specifications. These new features adds more vulnerability to the system.
[2]
Smart grid is mainly composed of six basic systems: power generation system, distribution system,
transmission network, data management and processing system, smart metering system, and
customer information system. The network architecture of smart grid
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/whatisroutingoverheadofthenetwork-231118164824-bec1373a/75/What-Is-Routing-Overhead-Of-The-Network-81-2048.jpg)