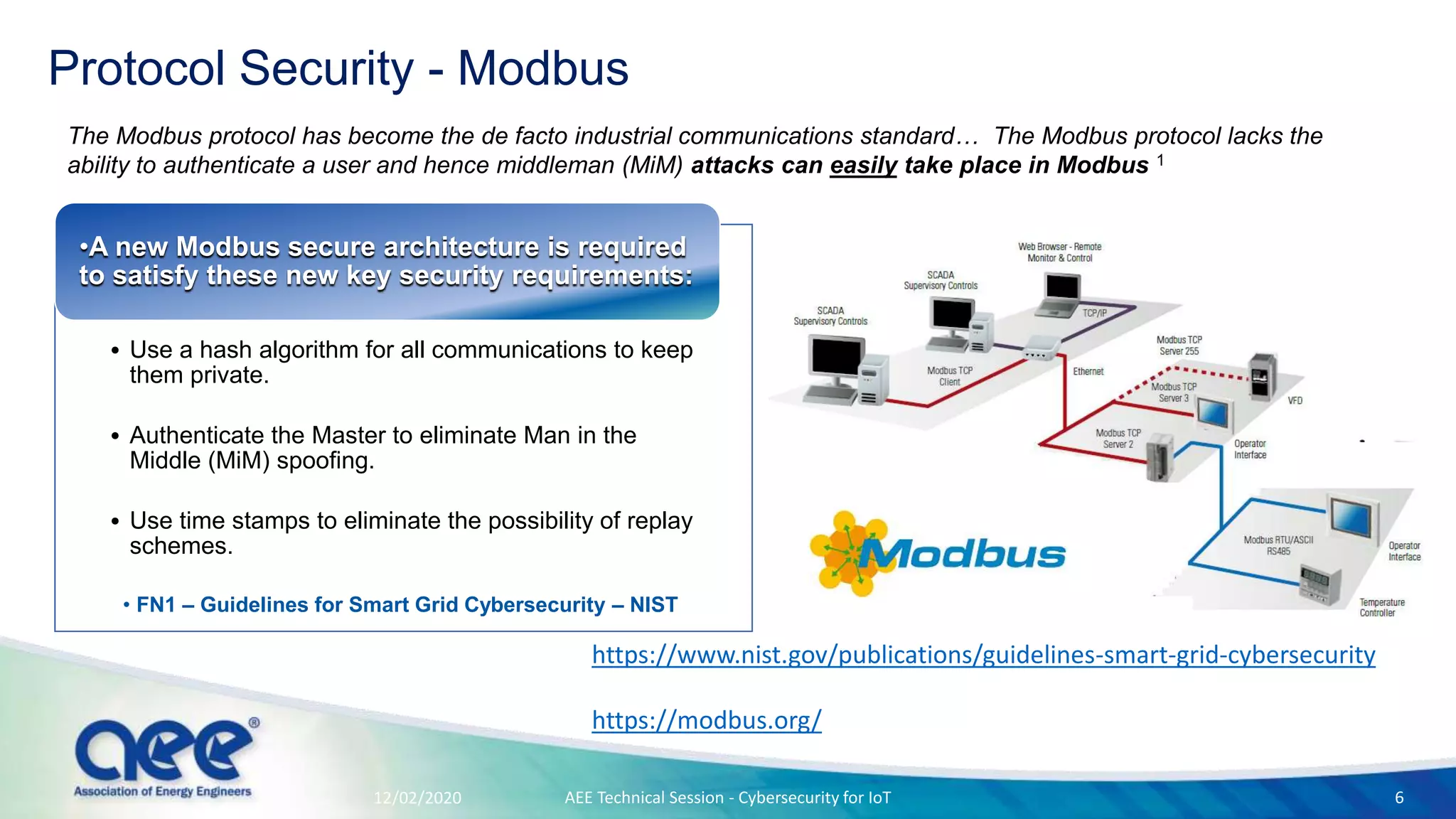
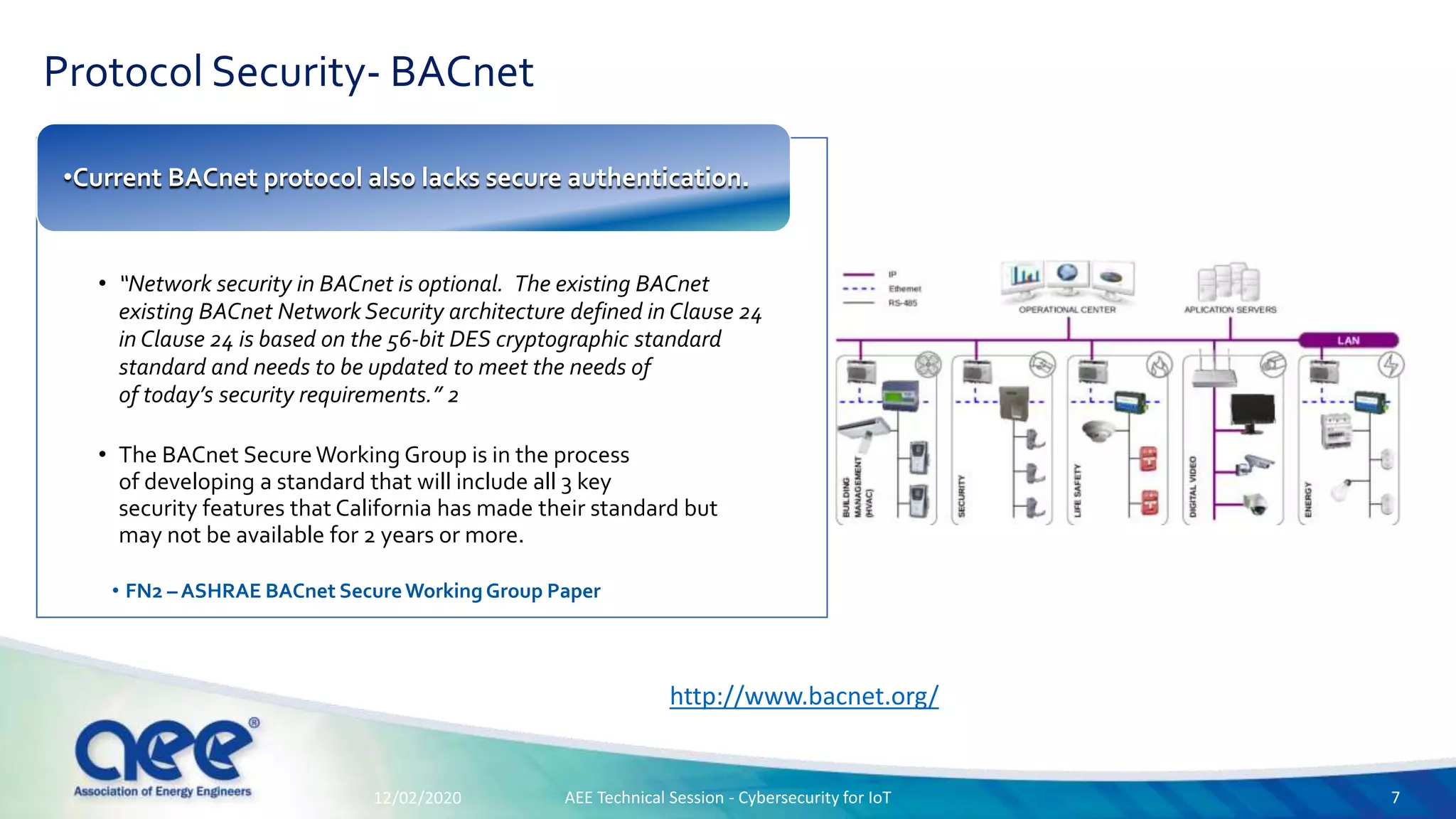
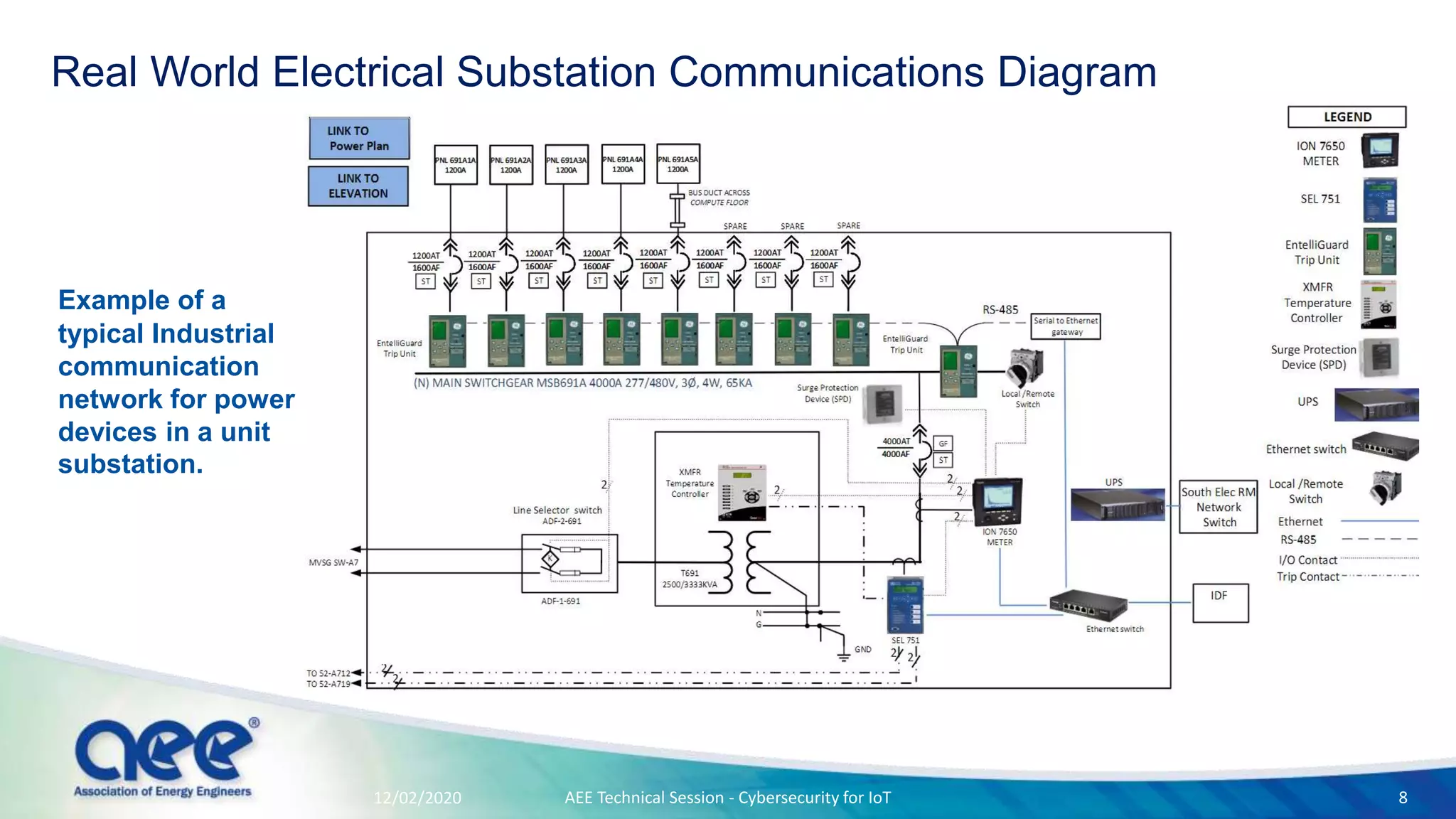
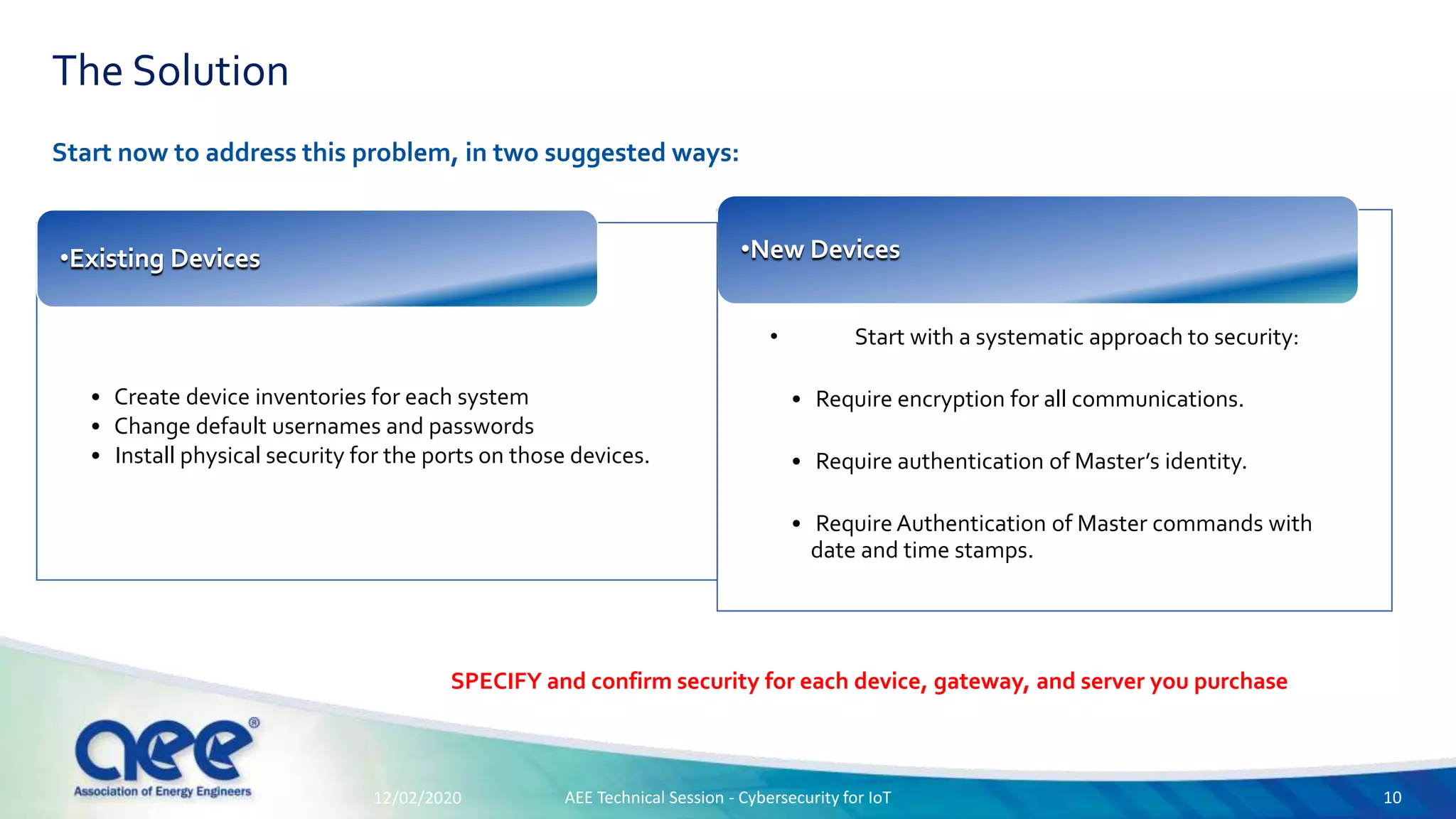
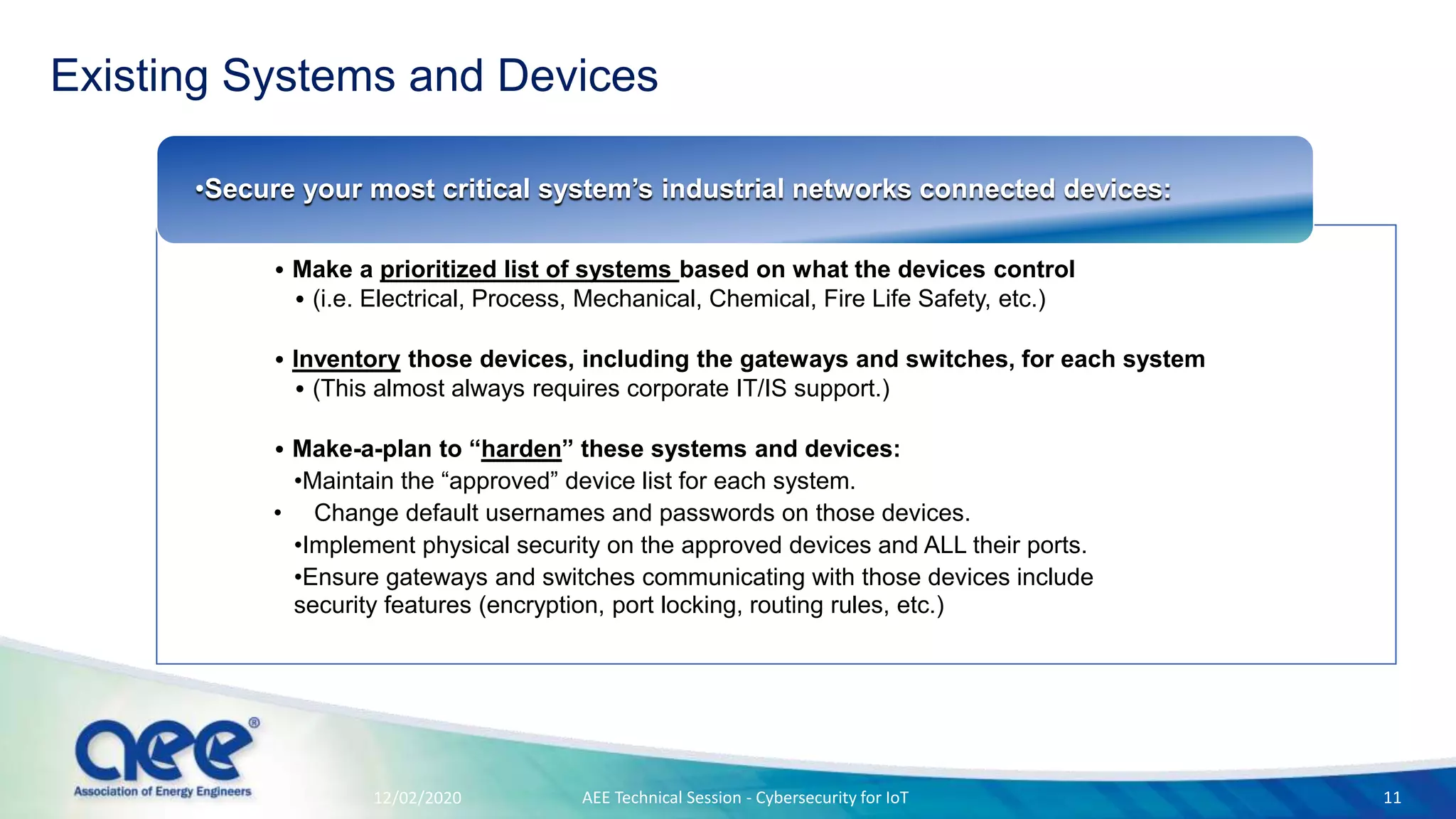
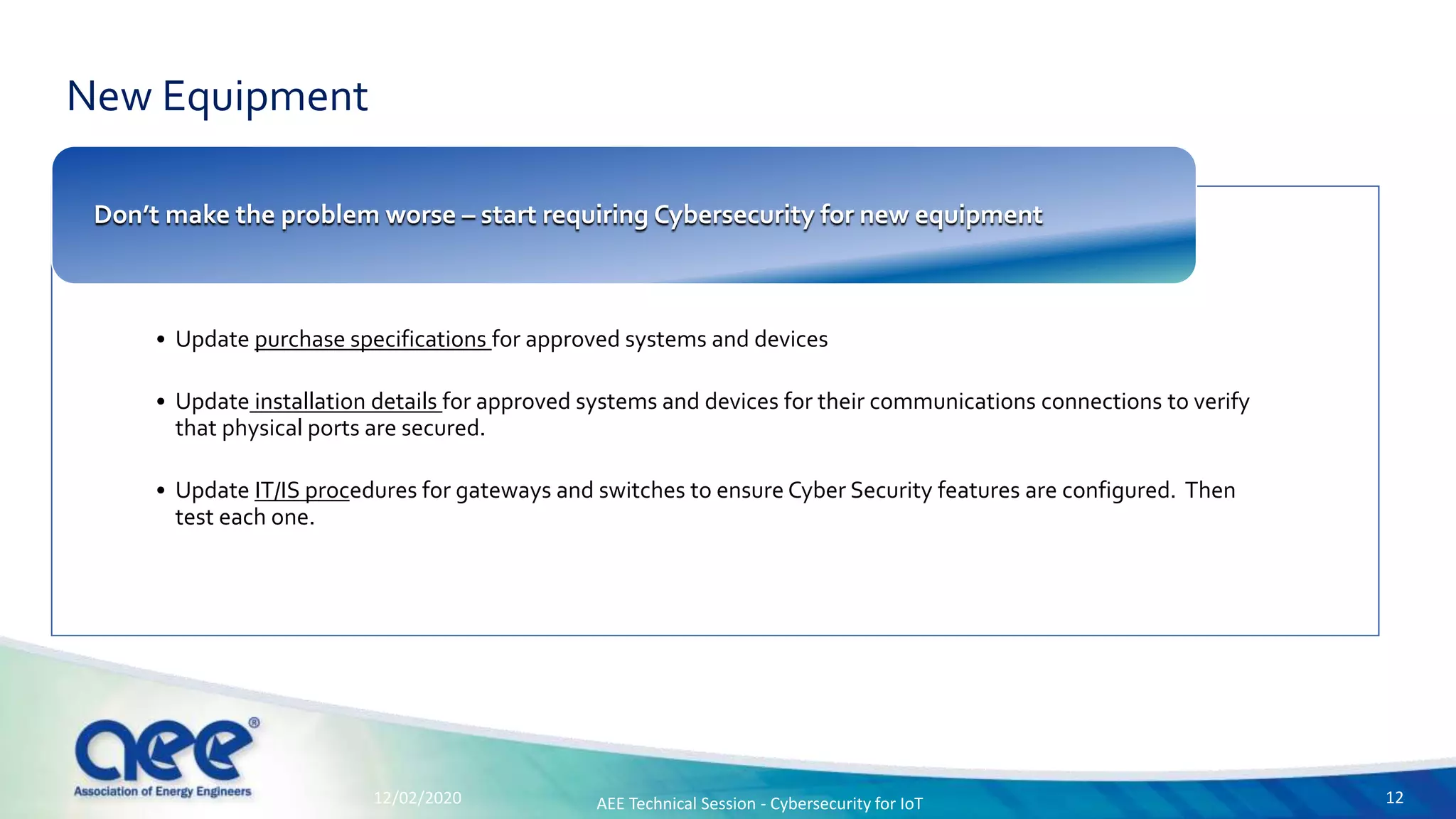
The document discusses cybersecurity challenges specific to IoT devices used in facility energy distribution, emphasizing the risks posed by such devices in controlling utilities. It highlights California's new regulations requiring robust security features for connected devices and outlines necessary steps for securing existing and new systems, including encryption and authentication measures. The conclusion stresses the urgency of engaging with cybersecurity issues now to protect industrial systems from potential threats.