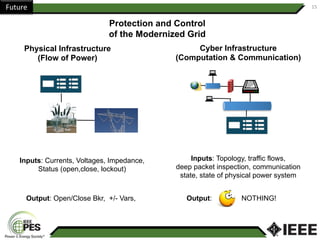
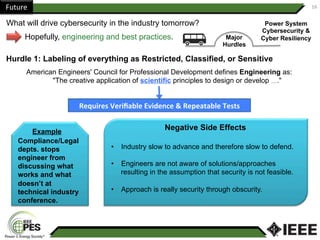
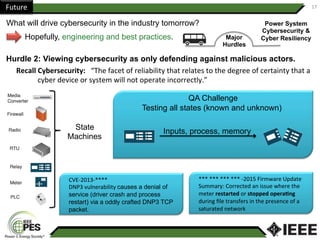
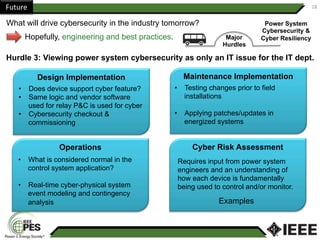
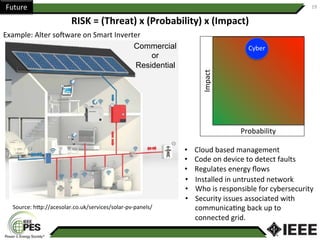
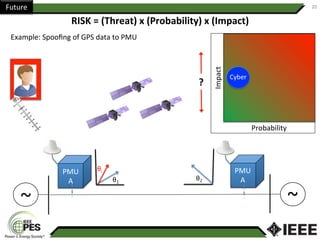
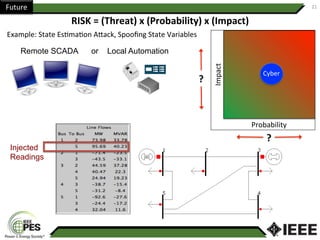
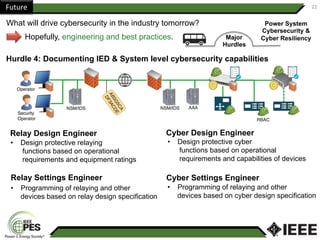
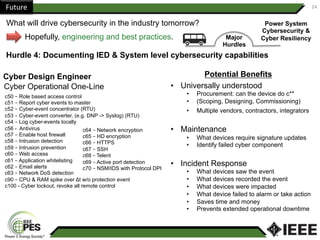
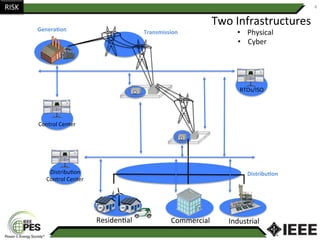
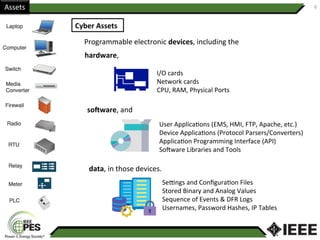
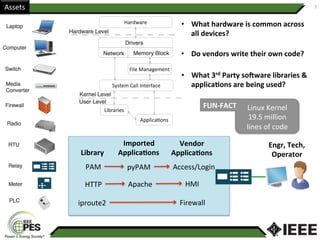
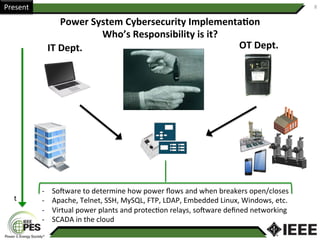
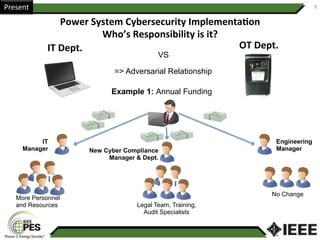
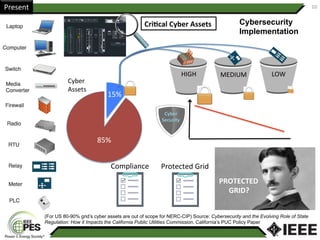
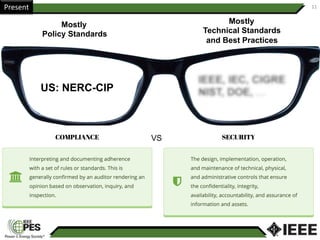
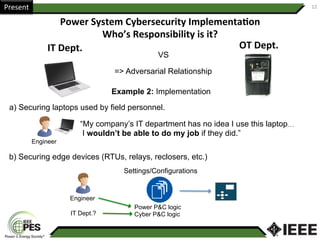
This document provides an overview of Nathan Wallace's background and experience in power engineering and cybersecurity. It discusses some of the challenges in implementing cybersecurity for power systems, including identifying critical cyber assets, determining responsibilities between IT and OT departments, and addressing compliance needs versus best practices. It also outlines major hurdles to improving cybersecurity such as overclassification of information, viewing it only as an IT issue or in defending only against threats. The document advocates for an engineering-based approach and standardization to help drive the field forward.


![13 Present
Cybersecurity
Design Implementation
Entity’s
1st Audit
v3 Audit
revealed over half
of the system’s
firewalls were
misconfigured.
• Typically the current approach is to use network firewalls and call it a day.
• Cybersecurity is an afterthought that ends up being “bolted on” only for compliance.
3 General Types of Firewall
Packet Filtering | ApplicaAon-Proxy Gateway | Stateful InspecAon
• Some can be bypassed by spoofing network layer data
• All are based on soXware
CVE-2016-**** The password-sync feature on [firewall vendor’s]
switches sets an SNMP community to the same string as the
administrator password, which allows remote attackers to obtain
sensitive information by sniffing network.](https://image.slidesharecdn.com/ieeepesgm2017panelnathanwallace-170804134539/85/IEEE-PES-GM-2017-Cybersecurity-Panel-Talk-13-320.jpg)