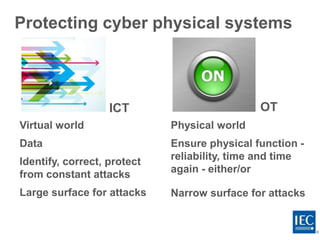
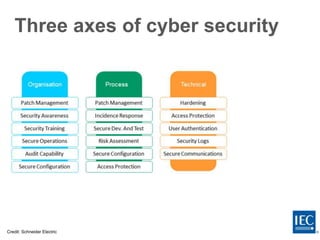
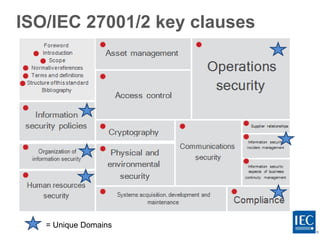
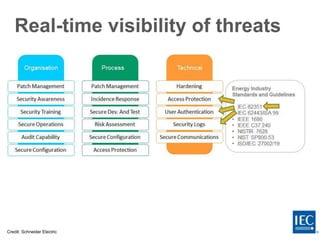
The document discusses several challenges around ensuring cybersecurity and resilience of critical infrastructure systems. As infrastructure becomes more digitally connected and complex, it faces increased cyber vulnerabilities. Regulators need to provide clear requirements and assign accountability, while utilities must accept responsibility and make necessary investments to update their infrastructure. International standards like those from the IEC provide common platforms to encourage cooperation on these issues. The goal is to implement a "defense-in-depth" architecture using standards and frameworks like ISO/IEC 27000 series and IEC 62443 for industrial control systems.