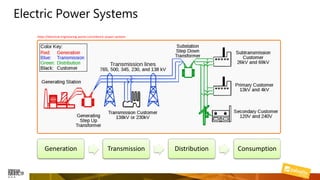
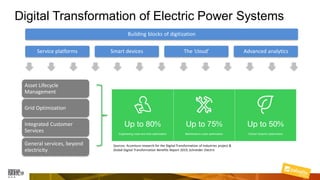
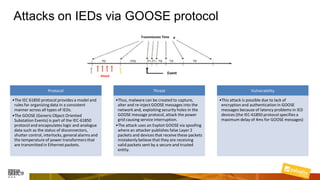
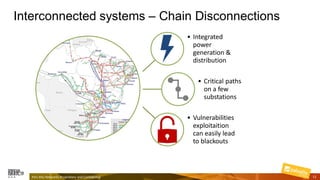
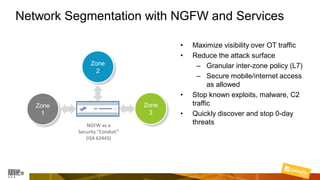
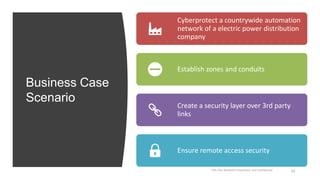
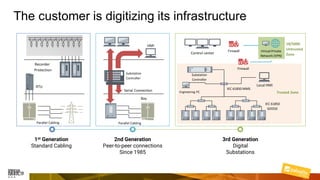
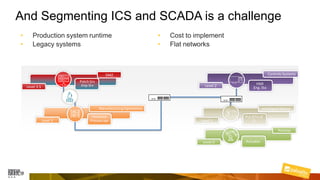
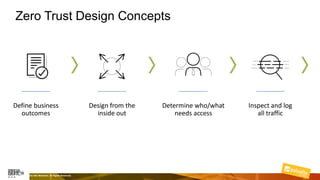
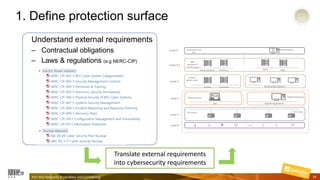
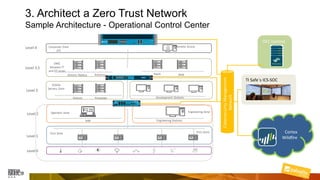
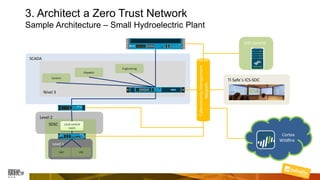
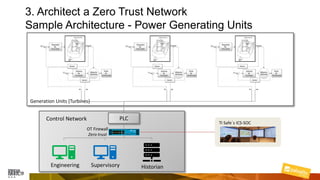
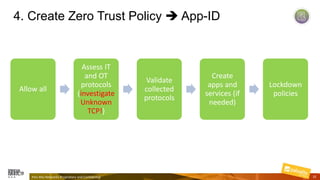
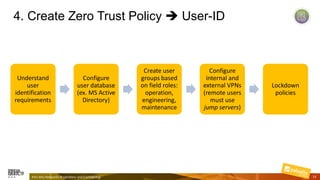
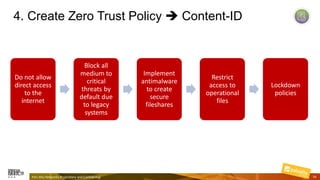
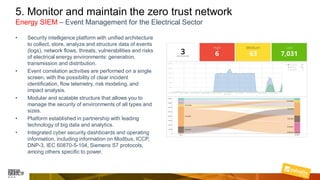
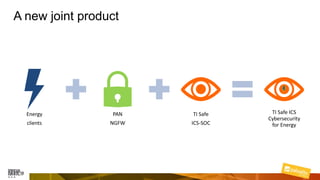
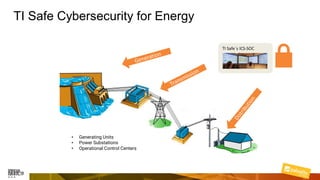
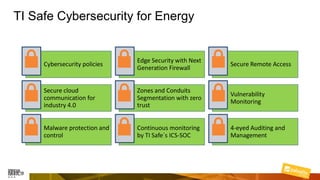
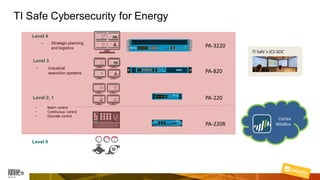
Marcelo Branquinho presented on protecting power distribution systems with zero trust cybersecurity. He discussed how digital transformation brings risks from increased connectivity and attacks on industrial control systems. Network segmentation with a zero trust model using firewalls as the network core was proposed. TI Safe and Palo Alto Networks developed a joint product called TI Safe Cybersecurity for Energy to implement zero trust for energy companies through next generation firewalls, remote access security, and continuous monitoring by TI Safe's industrial control system security operations center.