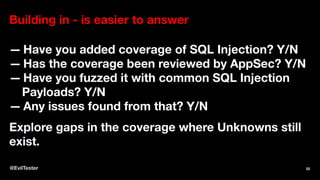
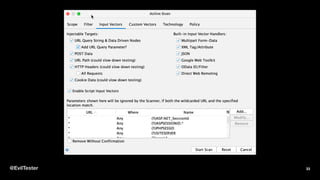
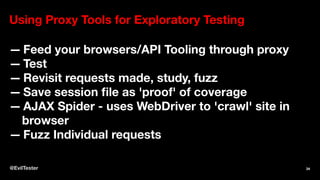
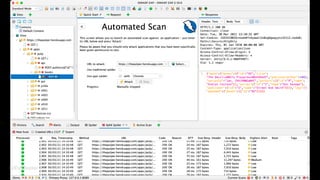
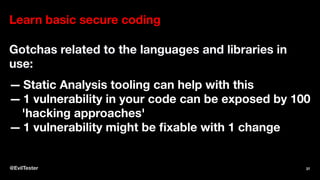
The document discusses enhancing security within testing and automation practices, emphasizing the overlap between security testing, exploratory testing, and automation skills. It provides resources for learning about vulnerabilities, suggests tools and techniques for integrating security testing, and highlights the importance of proactive measures in secure coding. Additionally, it stresses the need for addressing security concerns early in the development process without compromising testing efficiency.