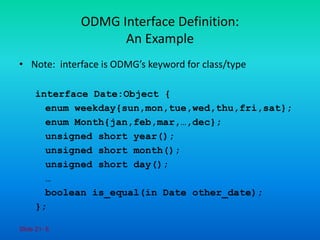
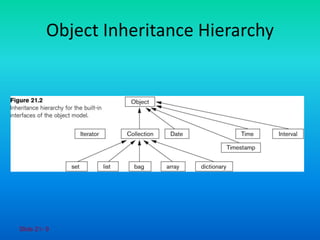
The document discusses the Object Data Management Group (ODMG) standards for object databases, highlighting key concepts such as object models, object definition language (ODL), and object query language (OQL). It outlines the characteristics of objects and literals within the ODMG framework, the definition and use of interfaces and classes, and the structure of collection types. Additionally, it addresses the use of object factories for generating objects and the principles of inheritance in class definitions.