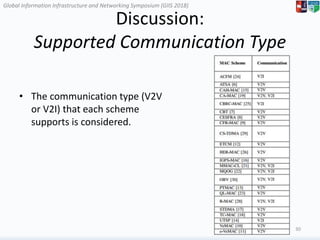
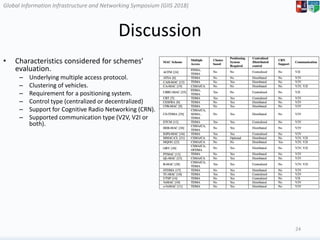
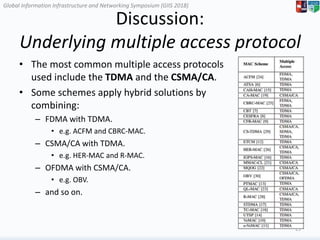
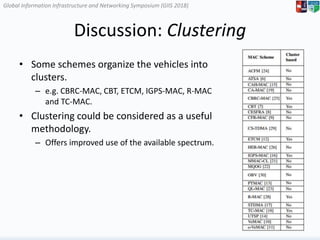
The document surveys medium access control (MAC) schemes applicable to 5G vehicular cloud computing (5G-VCC) systems, discussing various TDMA-based, CSMA/CA-based, and hybrid MAC schemes. It highlights the importance of advanced MAC algorithms for managing communication resources in a vehicular environment, which requires coordination between vehicles and roadside units. The paper also evaluates existing schemes based on their underlying access mechanisms, clustering methodologies, and control types.




![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
TDMA-based MAC schemes
• TDMA-based MAC schemes share the
medium in the field of time.
Adaptive TDMA Slot Assignment (ATSA)
[yang2013]
• Each vehicle selects a frame length, which is:
– reduced to improve channel utilization when
vehicle density becomes low,
– increased when vehicle density becomes high to
ensure that each vehicle can access the medium.
• Time slots are divided in two sets.
– Left and Right set.
• A slot management mechanism based on a
binary tree model is used.
– The vehicles on the left sub-tree can compete for
the Left time slots.
– The vehicles on the right sub-tree can compete
for the Right time slots.
• When a vehicle receives slot allocation
information from its neighbors, it discovers
which slots are in use.
– The remaining slots are available to compete for.
8](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-8-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
TDMA-based MAC schemes
Cluster Based TDMA (CBT) [sheu2014].
• It provides a mechanism for both intra-cluster and inter-
cluster communication.
– To minimize the packet collisions that could occur when two
clusters are moving in close places.
• In each cluster:
– The vehicles are timely synchronized using their GPS devices.
– One vehicle is elected as the Cluster Head (CH).
• A TDMA technique is used where each frame consists of N
time slots.
• The CH:
– Maintains a Slot Allocation Map (SAM) allocating time slots to
vehicles.
– Periodically broadcasts its SAM to its cluster's vehicles as well as
a beacon frame.
• The cluster remains in intra-cluster communication state if
beacon frames from CHs of other clusters are not received.
• If a beacon frame comes from an external CH.
– The two neighboring clusters' CHs exchange their SAMs in order
inter-cluster interference to be prevented.
• The CH that successfully sends first its SAM is considered as
the Winner.
– The other CH is considered as the Looser and must reschedule
its own SAM.
9](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-9-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
TDMA-based MAC schemes
Cross-layer Extended Sliding Frame
Reservation Aloha (CESFRA)
[rahman2014].
• It defines that safety information is
disseminated up to the third hop
neighboring vehicles.
– Without any routing scheme.
• The scheme divides each frame into N time
slots.
• All the vehicles are timely synchronized
using their GPS devices.
• When a vehicle has packets to transmit.
– Allocates an idle time slot.
– Starts transmitting its packets.
– The time slot is reserved by the vehicle in the
subsequent frames in order to transmit the
remaining packets.
10](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-10-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
TDMA-based MAC schemes
Collision Free Reservation MAC (CFR-MAC)
[zou2014].
• It considers the vehicles' traffic flows as well as
their velocities.
• Time slots are divided into two sets:
– The Left and the Right set.
• The Left set is assigned to vehicles that are moving
to the one direction.
• The Right set is assigned to vehicles moving to the
other.
• When multiple vehicles move on the same street
with different velocities.
– The interference levels are constantly changing.
• Leading on unpredictable changes in the medium
quality.
• CFR-MAC addresses this problem by dividing each
slots set into three subsets, while each subset is
associated to a specific velocity, namely:
– High velocity.
– Medium velocity.
– Low velocity.
• The interference levels inside each subset become
less variable and the medium quality more
resistant.
11](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-11-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
TDMA-based MAC schemes
Enhanced TDMA Cluster-based MAC
(ETCM) [shahin2016].
• The vehicles are organized into
clusters.
• A vehicle of each cluster is defined as
the CH.
• The CH applies a TDMA based method
to assign time slots to cluster's
vehicles.
12](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-12-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
TDMA-based MAC schemes
Prediction-based TDMA MAC (PTMAC)
[jiang2015].
• Its main operating principle is the packet
collisions prediction.
• PTMAC consists of three parts:
– Collision prediction.
• Data traffic and vehicles mobility
information is used in order potential
future data collisions to be predicted.
– Collision detection.
• It uses time slots information to detect
collisions that occurred in cases where
two vehicles transmit data using the
same time slot.
– Collision elimination.
• It reschedules the slots considering
information obtained from both collision
prediction and collision detection parts.
– In order the packet collisions to be
eliminated.
13](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-13-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
TDMA-based MAC schemes
Unified TDMA-Based Scheduling
Protocol (UTSP) [zhang2015].
• Centralized resource allocation
mechanism for V2I communication.
• The RSU:
– Collects information about:
• Channel state.
• Vehicles' velocities.
• Priorities of the vehicles' services.
– Uses a weighted function to compute
a score for each vehicle.
– Assigns TDMA time slots to each
vehicle according to its score.
14](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-14-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
TDMA-based MAC schemes
• Vehicular MAC (VeMAC) [omar2013].
• Similar to CBT and CFR-MAC schemes, two
vehicles' moving directions are considered.
– The Left and the Right direction.
• A set of time slots is assigned to vehicles
that move in each direction.
• Using these time slots, the vehicles of each
direction communicate with each other.
In [nguyen2014] the enhanced-VeMAC (e-
VeMAC) scheme is proposed.
– It is based on the insight of the one-hop
neighboring vehicles.
• To improve the performance of the VeMAC
scheme when parallel transmission occurs.
15](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-15-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
TDMA-based MAC schemes
• Other TDMA-based schemes include:
– The Cooperative ADHOC MAC (CAH-
MAC) [bharati2013].
– The Improved Generalized Prime
Sequence Based MAC (IGPS-MAC)
[zheng2014].
– The Self-organizing Time Division
Multiple Access (STDMA) [yu2013].
– The TDMA Cluster-based MAC (TC-
MAC) [almalag2012].
16](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-16-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
CSMA/CA-based MAC schemes
• The schemes of this category share the
medium by applying the CSMA/CA
operating principles.
Context Aware MAC (CA-MAC) [yi2014].
• It considers the network load status.
• Two parts:
– Reasoning part.
• Obtains the network load based on context
information.
• The network is characterized as congested, idle
or normal.
– Self-adaption part.
• Considers the obtained network load
• Dynamically adjusts the size of a Contention
Window, which is used for channel reservation
by the vehicles.
– If high network load is observed,
» the CW is incremented to reduce the
collisions probability.
– If low network load is observed
» the CW is decreased to avoid
unnecessary medium access delays.
– The CW will remain unchanged, if the Reasoning
part indicates that the network status is normal.
17](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-17-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
CSMA/CA-based MAC schemes
Multichannel MAC - Cross Layer
(MMAC-CL) [fazio2015].
• It aims to reduce the interference
between vehicles.
– Using two multichannel radio
interfaces per vehicle.
• Transmission channels are selected
considering a Signal to Interference
Ratio (SIR) evaluation.
– To minimize the cochannel
interference observed by the vehicles.
18](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-18-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
CSMA/CA-based MAC schemes
• Multichannel QoS Cognitive MAC
(MQOG) [el2012].
• It is multichannel scheme using:
– A CCH for control information
exchange.
– Multiple SCHs for data transmission.
• Each vehicle:
– Tracks its neighbors' communications
using a Channel Neighbor State Table
(CNST).
– Assesses the interference level in each
channel.
– Acquires the best SCH channel for data
transmission.
• Vehicles obtain information from the
CCH in order to update their CNST
tables.
19](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-19-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
CSMA/CA-based MAC schemes
• Q-Learning MAC (QL-MAC)
[wu2014].
• A Contention Window (CW) is
defined.
– The best CW size is evaluated
using a Q-Learning algorithm.
• A positive reward is awarded to
each vehicle when a data frame is
successfully transferred.
• A negative reward is given when a
data frame transmission is failed.
• The dynamic CW size adjustment:
– Reduces the packet collisions.
– Succeeds low medium access
delay.
20](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-20-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
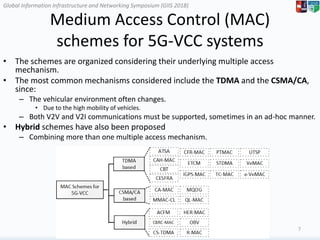
Hybrid MAC schemes
• Use more than one multiple access mechanisms.
• Adaptive Collision Free MAC (ACFM) [guo2012]
scheme combines both TDMA and FDMA.
• It implements a time slot reservation mechanism
located at each RSU.
• Each frame operates in a specific frequency and
contains 36 time slots that can be used for data
transmission and 1 slot that is called RSU Slot (RS).
• Each RSU maintains a Slot Assignment Cycle (SAC)
for the next 100ms of time, while each cycle can
contain from 1 and up to 5 frames according to the
vehicles density.
– If vehicles density is low, the RSU uses few frames in
order to avoid situations where a lot of slots remain
unused.
– If vehicles density is high, the RSU uses more frames
in order to support the increased needs for
resources.
21](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-21-320.jpg)
![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
Hybrid MAC schemes
• Cluster Based RSU Centric MAC
(CBRC-MAC) [zhang2013].
– Similar to ACFM scheme, it combines
both TDMA and FDMA for providing
multiple access to vehicles.
• CSMA-based Self-Organizing TDMA
(CS-TDMA) [zhang2014].
– Combines TDMA, CSMA/CA and SDMA to
support both safety and non-safety
applications.
• Some schemes combine TDMA with
CSMA/CA to accomplish the multiple
access:
– Hybrid Efficient and Reliable MAC (HER-
MAC) [dang2014].
– OFDMA-based MAC scheme for VANETs
(OBV) [bazzi2015].
– Risk-Aware MAC (R-MAC) [guo2013].
22](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-22-320.jpg)


![Global Information Infrastructure and Networking Symposium (GIIS 2018)Global Information Infrastructure and Networking Symposium (GIIS 2018)
Discussion:
Control type
• Distributed control distributes the
resource manipulation workload.
– It could be applied to 5G-VCC architectures:
• Considering the operating principles of the Fog
computing [mahmud2018].
• Centralized control simplifies the
manipulation of communication resources.
– It could be applied to 5G-VCC architectures:
• Using a Software Defined Network (SDN)
[li2018] controller.
• Which supervises the manipulation of the entire
system.
28](https://image.slidesharecdn.com/giis2018presentation-191212220431/85/A-Survey-on-Medium-Access-Control-Schemes-for-5G-Vehicular-Cloud-Computing-Systems-presentation-28-320.jpg)