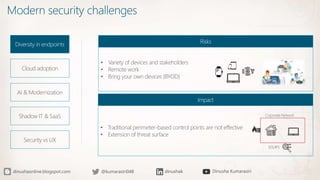
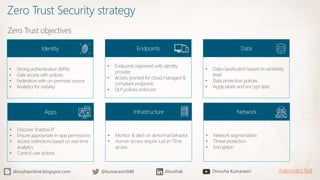
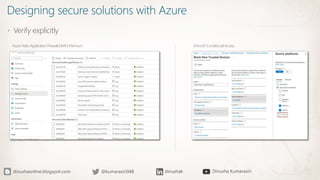
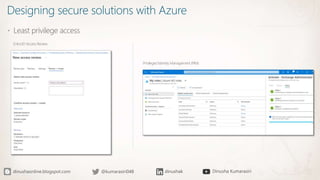
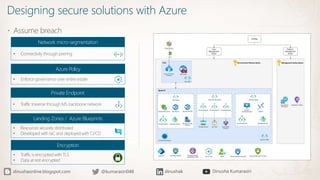
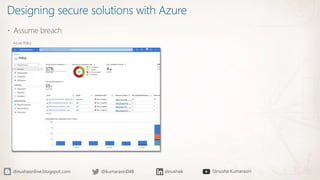
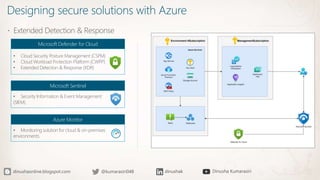
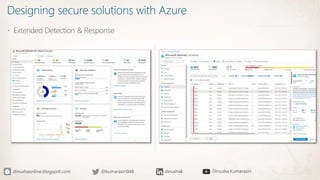
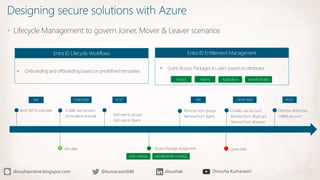
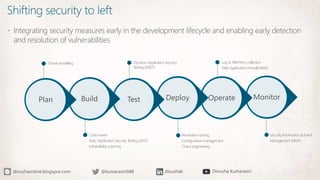
The document discusses the implementation of a Zero Trust security strategy using Azure, addressing modern security challenges such as diverse endpoints, cloud adoption, and sophisticated cyber attacks. It outlines key principles of Zero Trust, including strong authentication, least privilege access, and continuous monitoring to enhance security and reduce risks. Additionally, it emphasizes the importance of integrating security measures early in the development lifecycle and provides guidance on designing secure solutions with Azure tools.