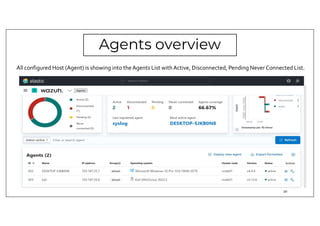
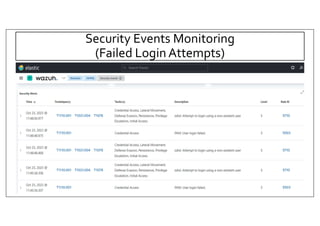
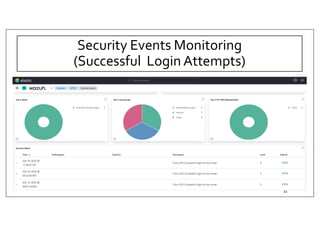
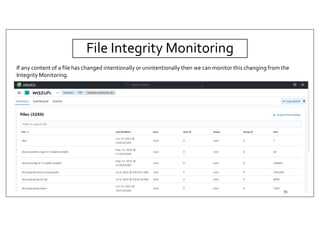
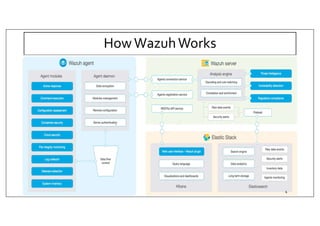
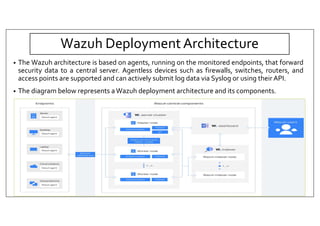
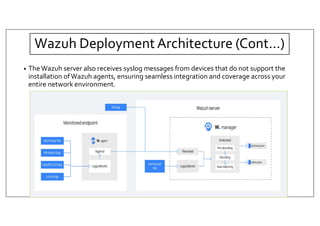
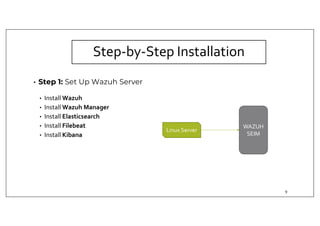
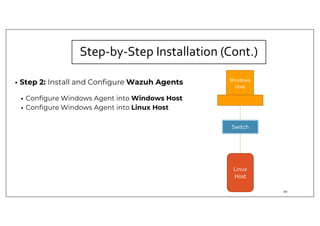
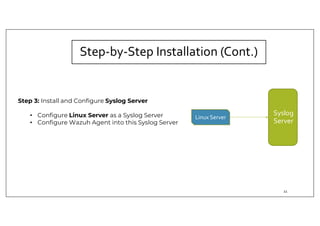
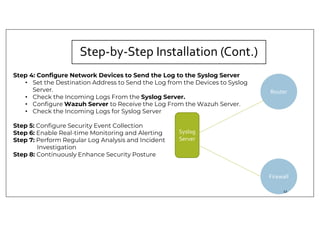
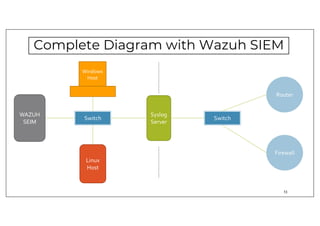
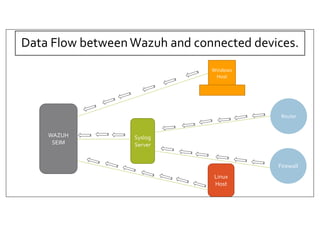
The document discusses deploying the Wazuh SIEM solution. It describes Wazuh's architecture with agents on endpoints sending security data to a central server. It provides a step-by-step process for installing Wazuh including setting up the server, installing and configuring agents, and integrating network devices via syslog. It also discusses customizing Wazuh through additional decoders and rules to monitor any log data and enhance detection capabilities.





![Adding new decoders and rules
• This example on how to create new decoders and rules.
The following log corresponds to a program called example:
Dec 25 20:45:02 MyHost example[12345]: User 'admin' logged from '192.168.1.100’
16](https://image.slidesharecdn.com/aplenarilyintegratedsiemsolutionanditsdeployment-231212044522-531f43f5/85/A-plenarily-integrated-SIEM-solution-and-it-s-Deployment-16-320.jpg)