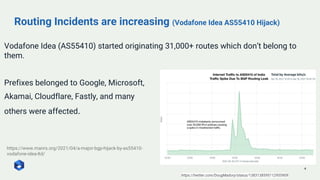
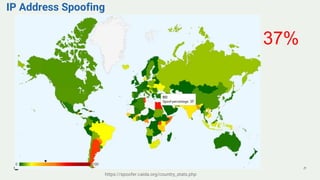
This document provides an overview of MANRS (Mutually Agreed Norms for Routing Security) for network operators in Bangladesh. It discusses key routing security issues like prefix hijacking and route leaks. It describes the four MANRS actions for network operators: filtering, anti-spoofing, coordination, and global validation. Filtering involves setting policies to accept only valid routing announcements. Anti-spoofing uses techniques like uRPF to prevent spoofed source IP addresses. Coordination means maintaining up-to-date contact details in databases. Global validation facilitates routing validation through tools like the IRR and RPKI. The document explains how these actions improve routing security and reliability. It also outlines MANRS' goals and