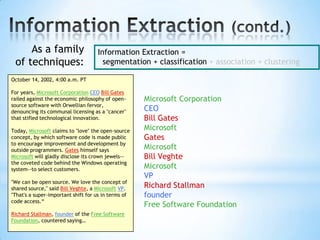
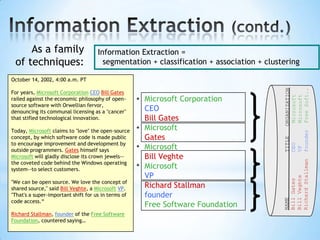
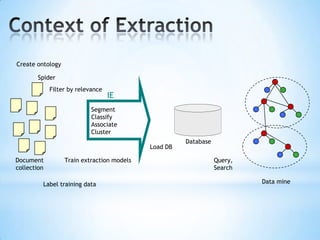
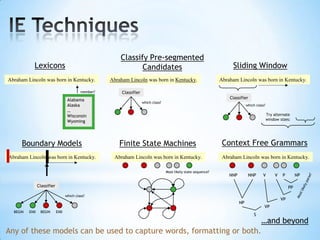
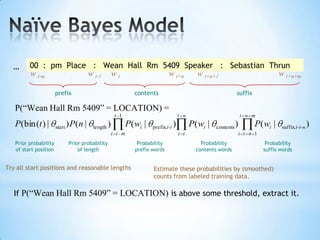
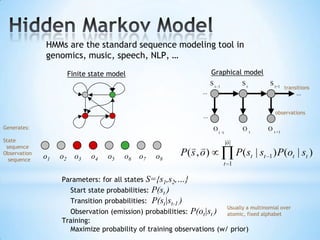
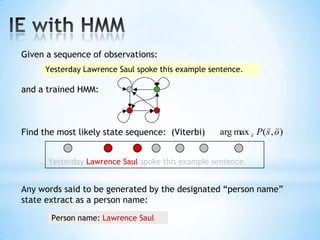
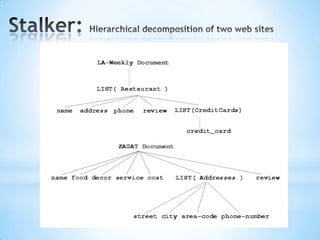
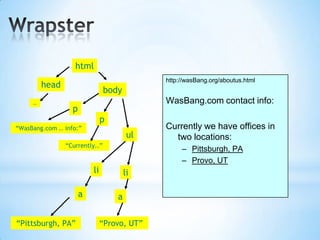
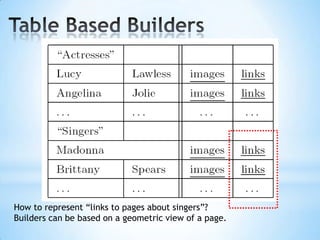
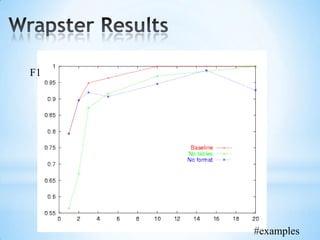
The document discusses the application of machine learning in developing domain-specific search engines, which focus on specific segments of online content to provide more relevant search results. It outlines the anatomy of a search engine, emphasizing the processes of web crawling, indexing, and searching, while also comparing vertical search engines to general web search engines. Additionally, the document touches on concepts of vertical search, information extraction, and the evolution of machine learning as an important discipline within artificial intelligence.