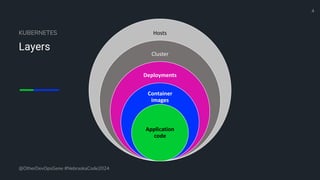
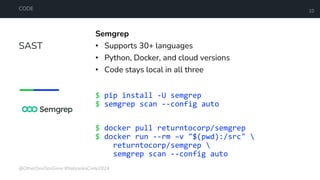
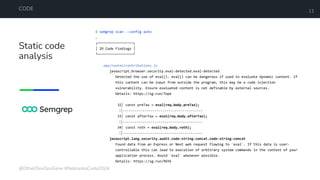
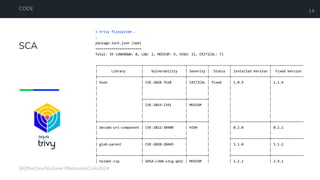
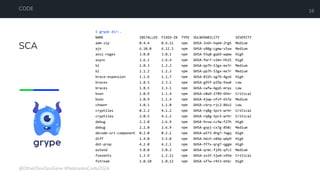
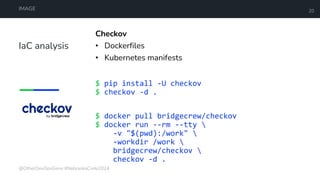
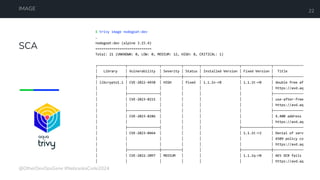
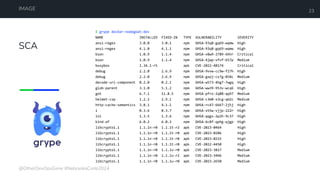
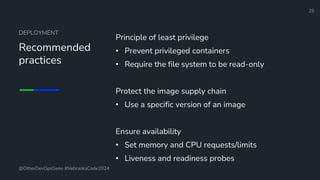
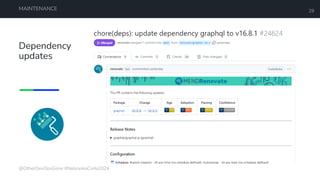
The document is a developer's guide focusing on Kubernetes security, detailing best practices such as implementing least privilege, threat modeling, and static application security testing. It discusses tools like Semgrep, Trivy, and Grype for scanning code and images for vulnerabilities, as well as the importance of automated builds and image supply chain security. Additionally, it emphasizes the significance of deployment best practices, including setting up proper resource limits and maintaining a secure deployment environment.