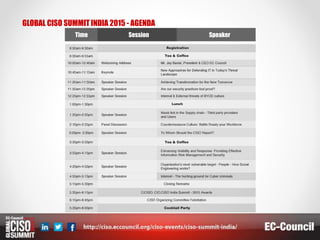
The document summarizes an upcoming EC-Council Global CISO Summit. It notes that the summit brings together CISOs from around the world to discuss real cybersecurity threats faced by nations, companies, and networks. The invite-only event will feature leaders implementing next-generation security technologies and strategies to address increasingly complex challenges. The summit aims to provide a forum for addressing the theme of "Agile Security in a Dynamic Threat Landscape." It is organized by EC-Council and an committee of cybersecurity experts from organizations including ICERT, Ernst & Young, PwicewaterhouseCoopers, Microsoft, and HDFC Bank.