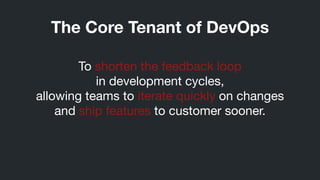
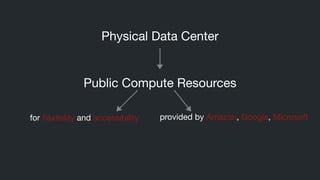
DevOps aims to shorten feedback loops and allow teams to quickly iterate on changes and ship features. However, continuously deploying changes also introduces security risks that must be monitored. SecDevOps seeks to address this by continually monitoring the security implications of operational changes, improving security response times while still allowing for continuous deployment. Implementing continuous security through a SecDevOps methodology is an important challenge that companies need to solve in order to fully benefit from DevOps practices.