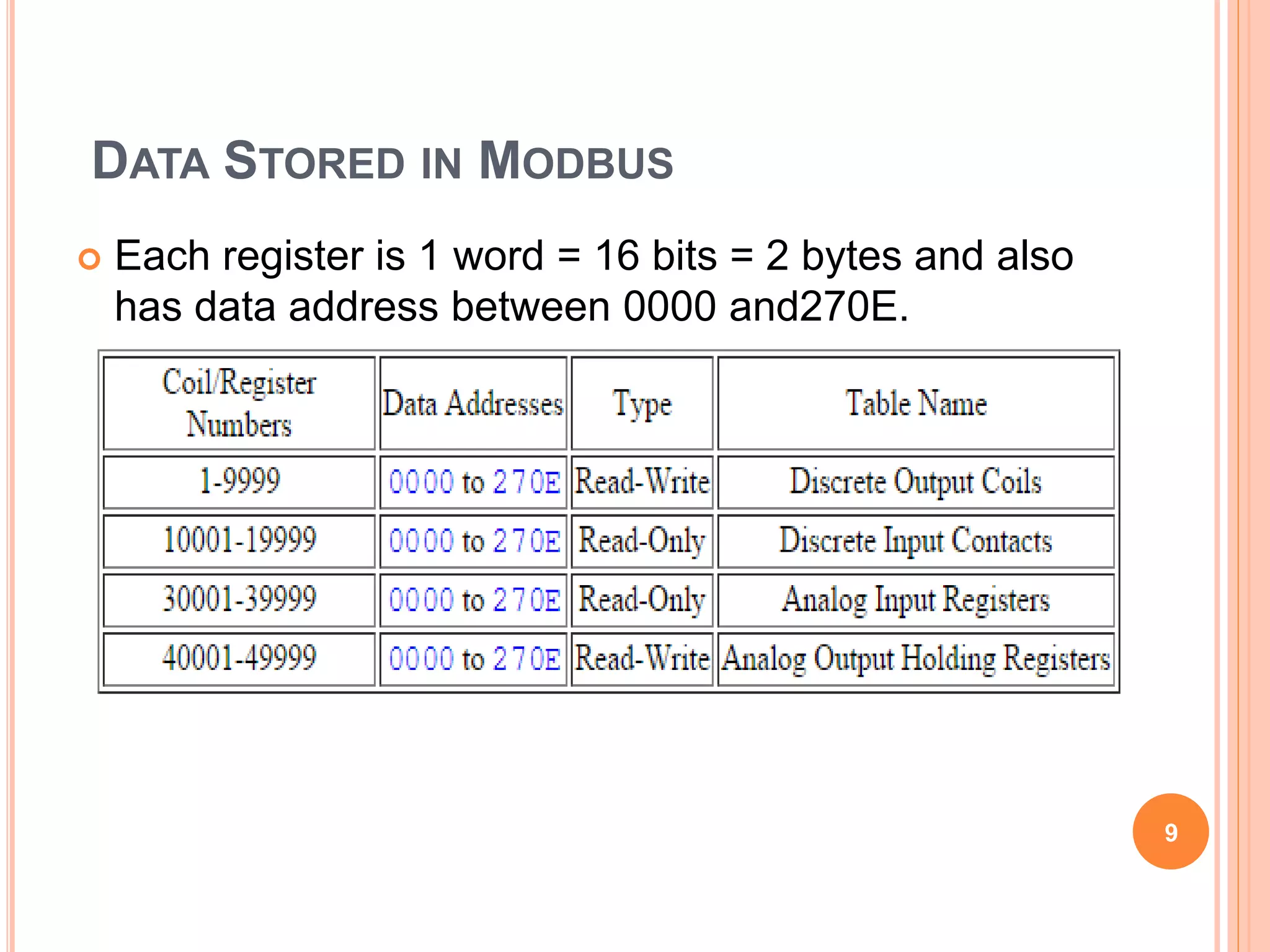
The document discusses two common industrial communication protocols: MODBUS and CANBUS. MODBUS uses a master-slave architecture and transmits data via MODBUS RTU, TCP/IP, or ASCII. It stores information in registers and coils that devices can read from and write to. CANBUS was developed for automotive applications to replace point-to-point wiring with a standardized serial bus. It uses dominant and recessive states to transmit data frames with identifiers, data, and CRC across a bus without a master. Both protocols are now widely used for industrial automation and embedded systems.