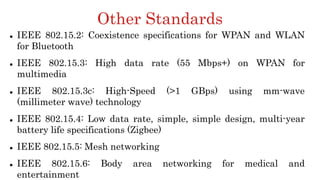
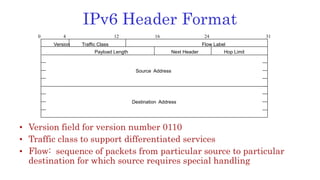
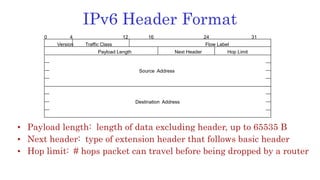
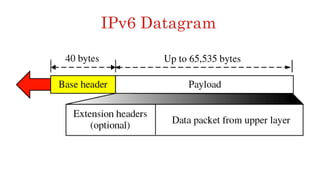
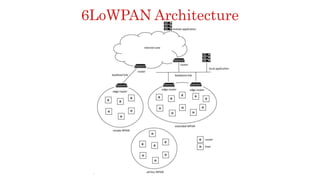
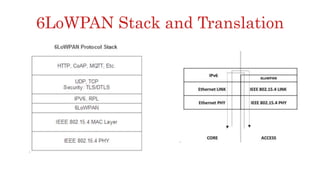
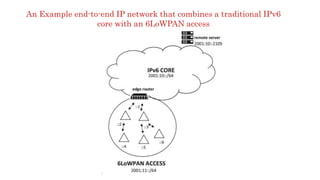
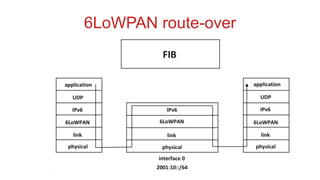
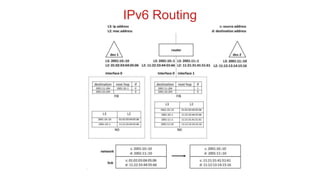
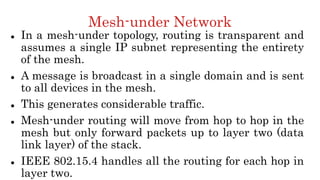
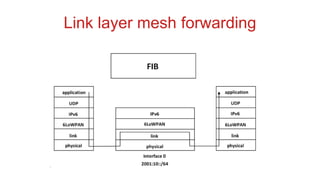
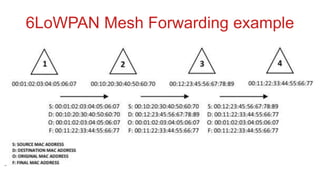
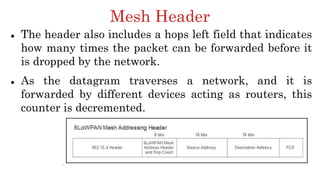
The document discusses 6LoWPAN (IPv6 over Low-Power Wireless Personal Area Networks), which allows IP networking for small, low-power devices. It describes how 6LoWPAN compresses IPv6 headers to reduce overhead and fragments packets to meet small MTU sizes. 6LoWPAN networks use an edge router to connect to the wider IP network and support two routing modes: route-over and mesh-under. The document also discusses related topics like CoAP, MQTT, and publish/subscribe messaging.