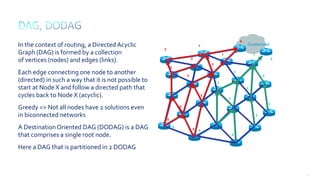
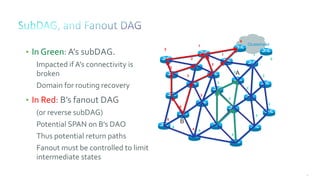
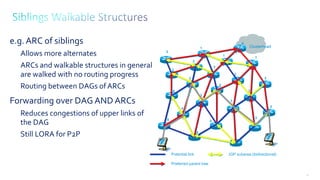
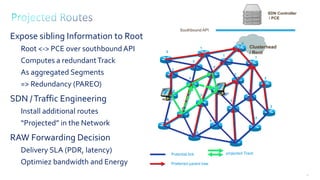
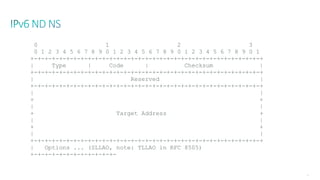
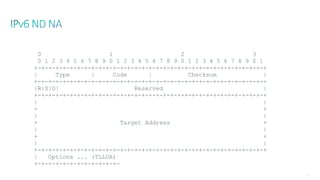
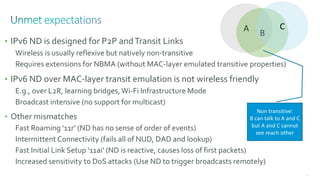
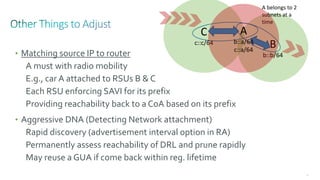
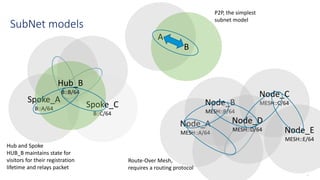
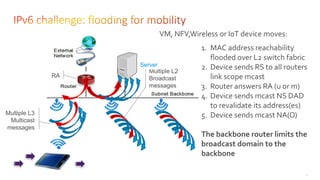
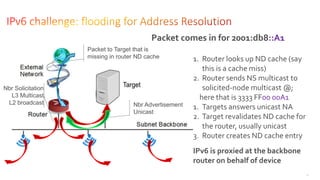
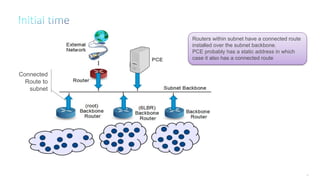
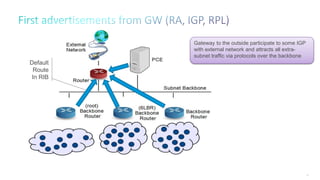
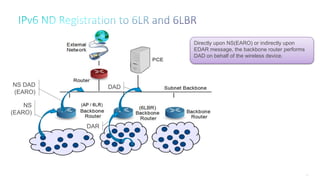
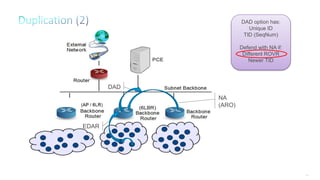
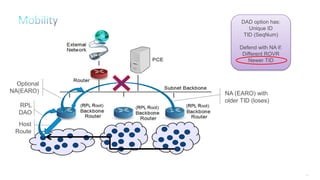
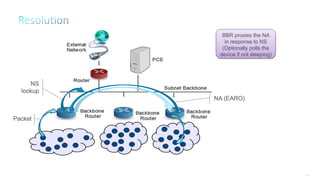
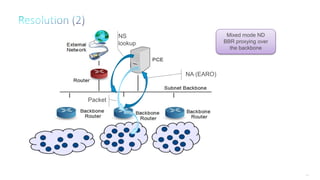
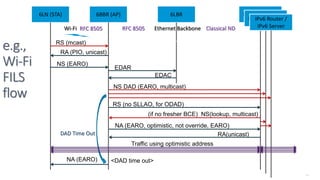
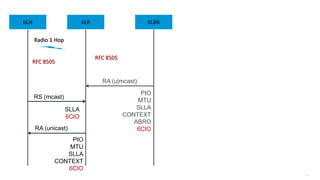
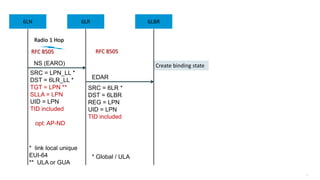
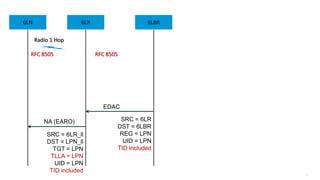
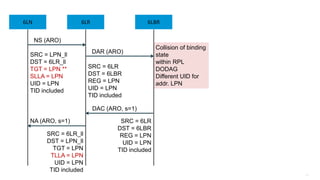
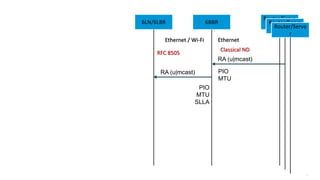
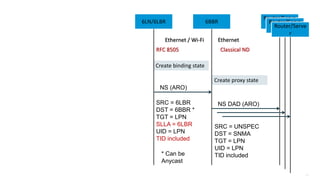
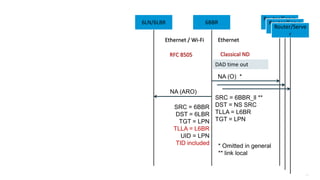
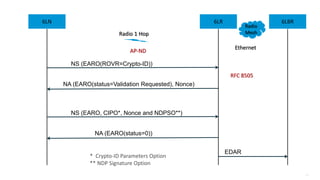
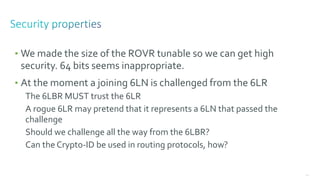
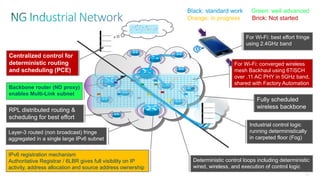
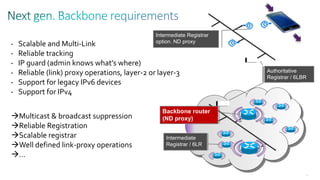
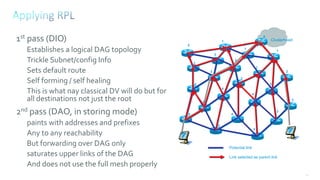
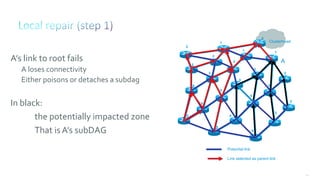
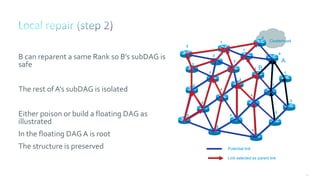
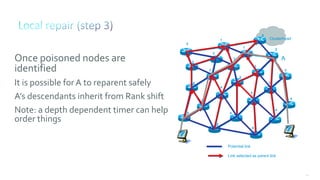
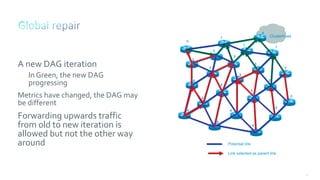
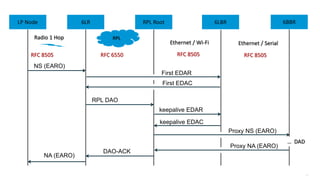
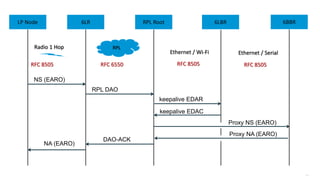
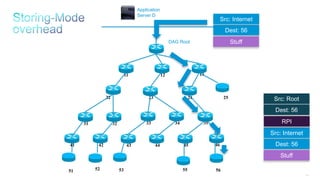
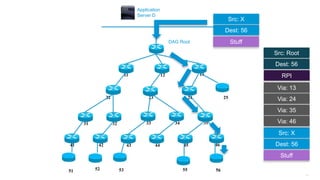
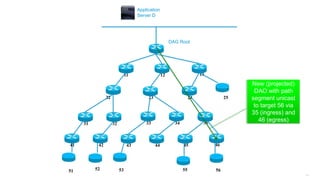
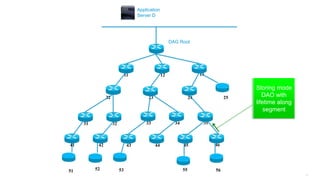
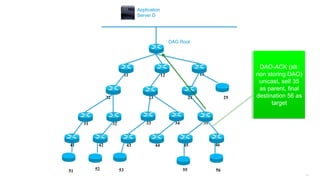
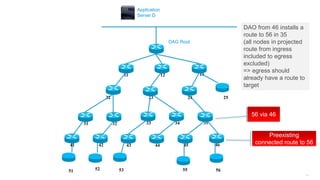
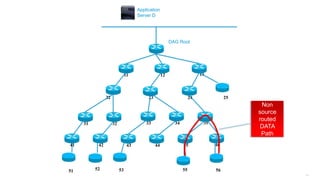
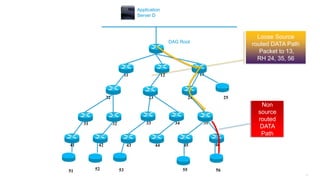
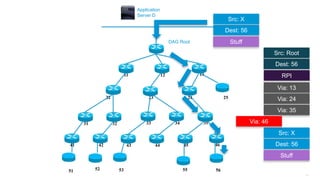
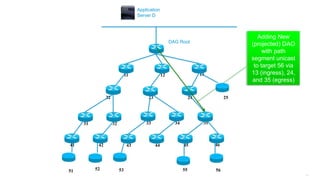
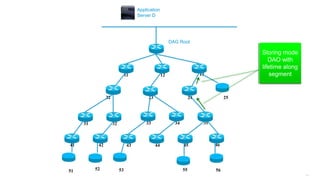
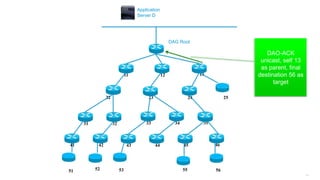
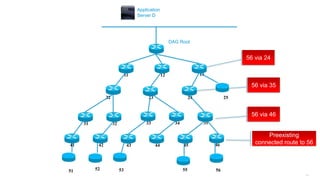
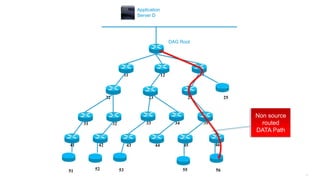
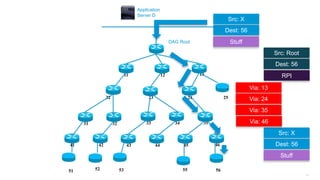
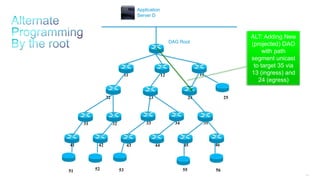
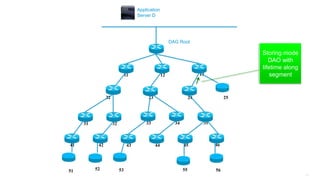
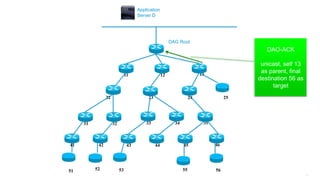
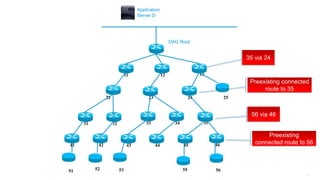
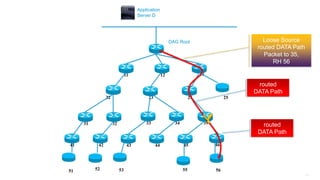
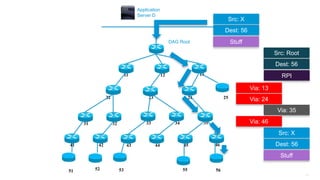
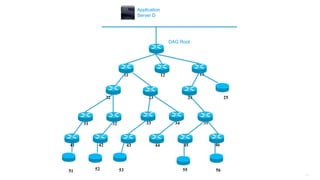
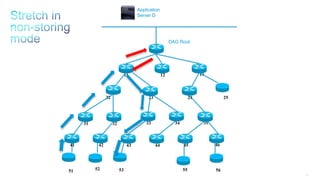
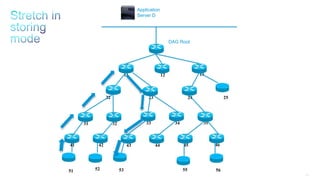
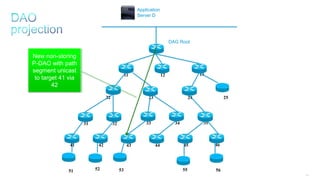
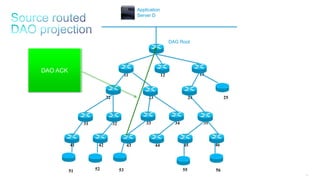
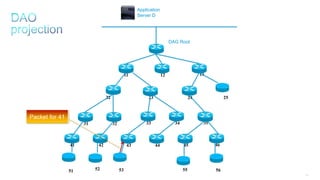
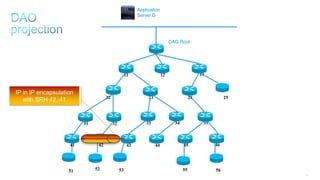
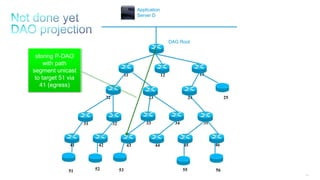
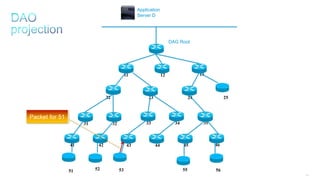
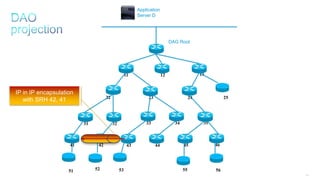
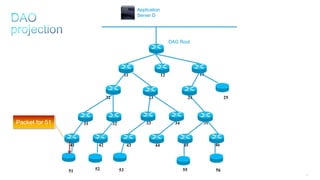
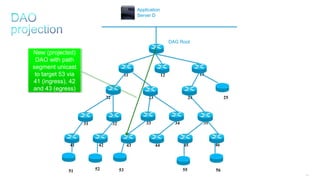
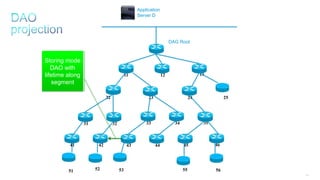
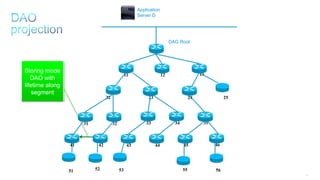
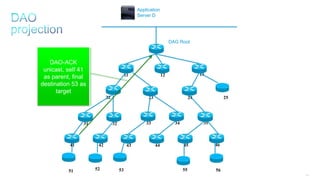
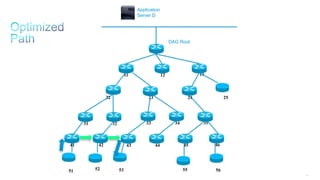
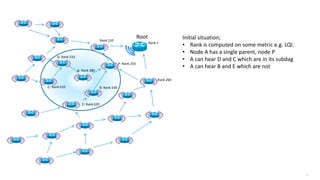
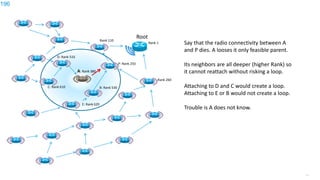
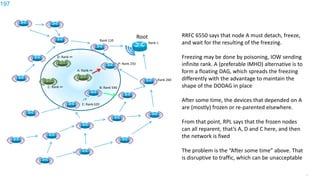
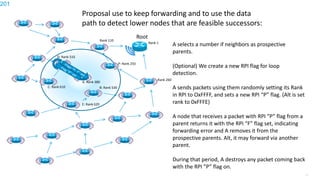
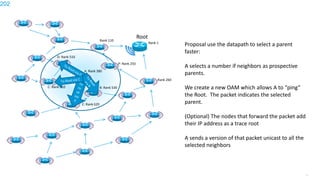
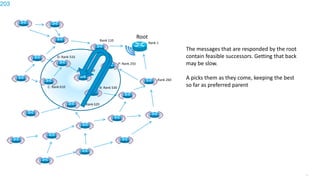
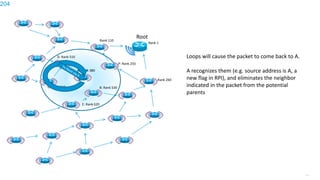
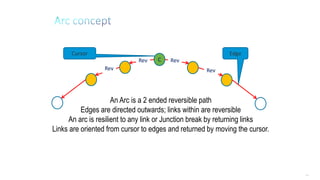
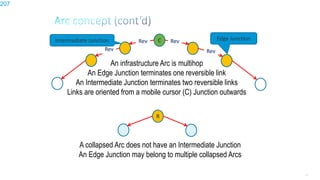
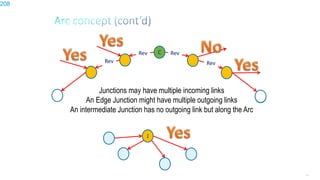
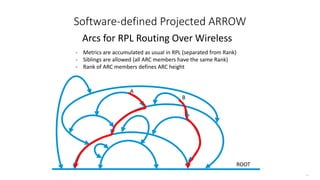
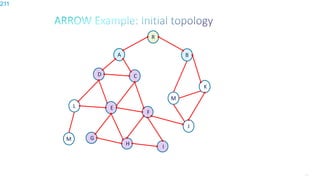
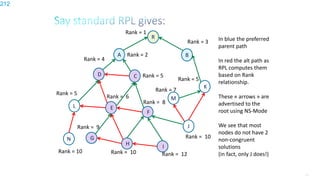
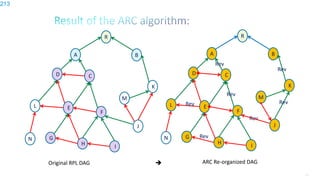
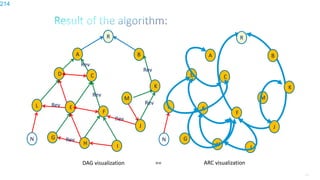
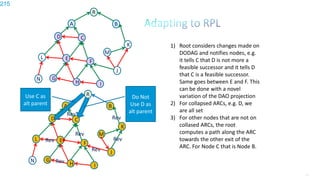
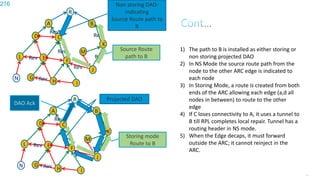
This document discusses several topics related to IPv6 and low power and lossy networks (LLNs):
1. It outlines the agenda for discussing IPv6 neighbor discovery for point-to-point and transit links, wireless neighbor discovery, RPL routing, and RPL extensions.
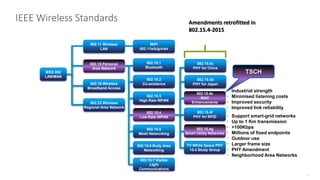
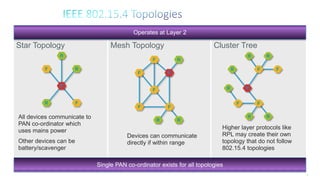
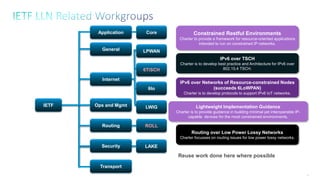
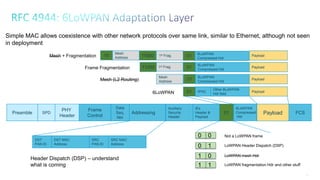
2. It notes that LLNs comprise billions of constrained devices interconnected by wireless links, and several standards groups are working on protocols for these networks, including 6LoWPAN, ROLL, and 6TiSCH at the IETF.
3. It argues that IPv6 is necessary for the Internet of Things given the tens of billions of additional smart objects that will be connected, and that the RIPE NCC has now