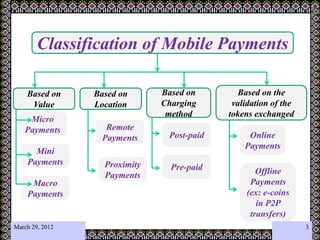
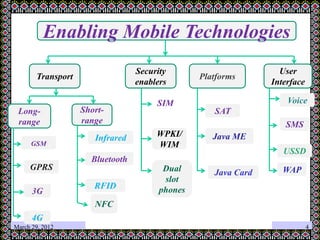
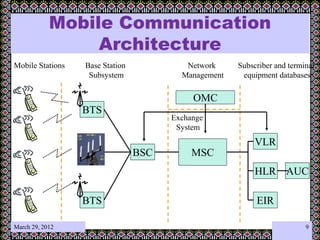
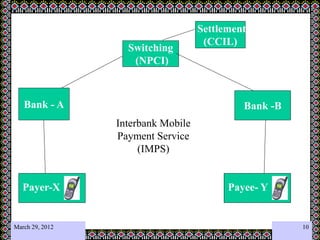
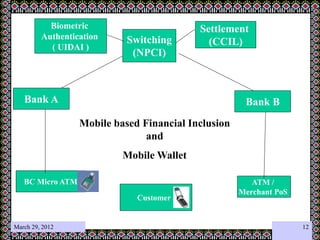
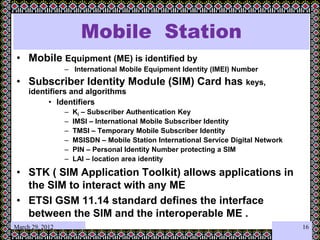
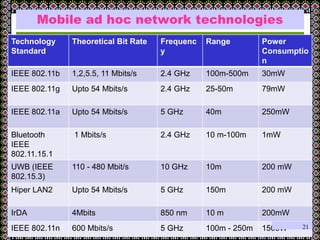
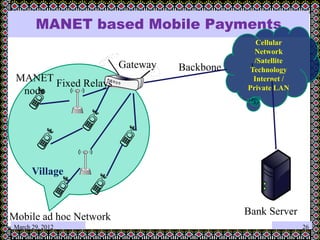
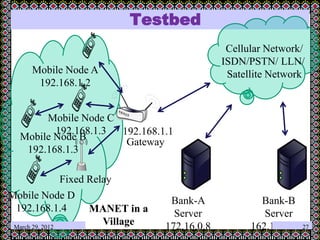
This document discusses technology challenges in mobile payments. It begins by classifying mobile payments based on value, charging method, location, and validation of tokens exchanged. It then discusses enabling mobile technologies like user interfaces, platforms, security, and transport layers. The document outlines several technology challenges including those at the device level, application level, communication level, user level, security level, standards level, and consolidation level. It provides examples of some of these challenges. Finally, it discusses some innovative mobile payment solutions developed in India and provides an overview of a mobile ad-hoc network ecosystem used to enable financial inclusion through mobile payments.