1) The document discusses security and innovation in information technology and the future internet.
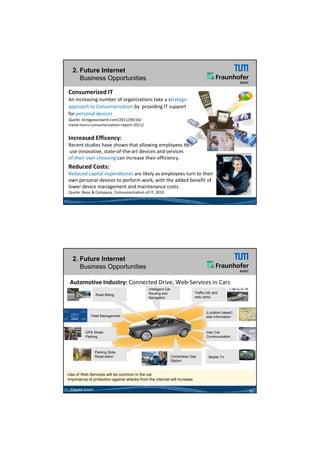
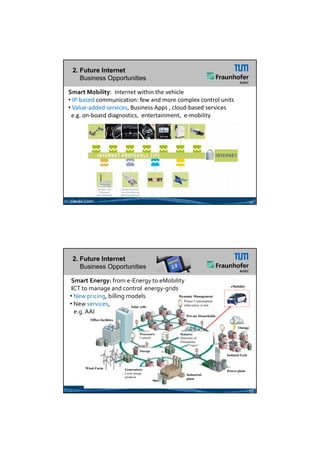
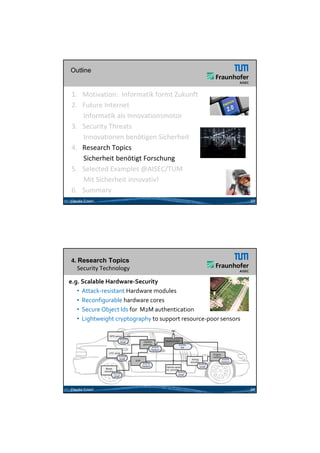
2) It outlines trends like cyber physical systems, cloud computing, and the internet of things that are driving new business opportunities but also increasing security threats.
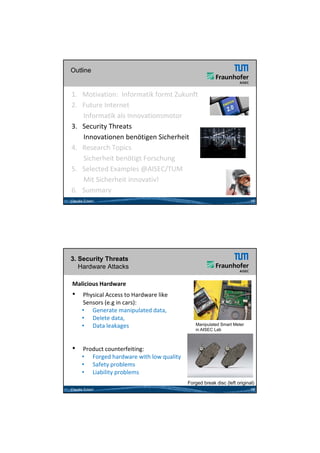
3) The author argues that appropriate security measures are urgently needed to address growing attack surfaces and security risks posed by many innovations.