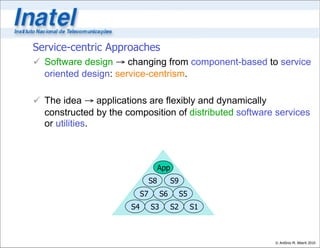
This document discusses the requirements and challenges for future network architectures. It covers several topics:
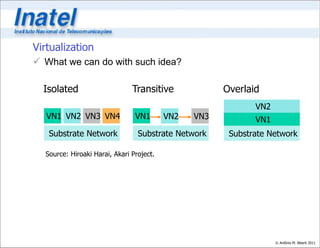
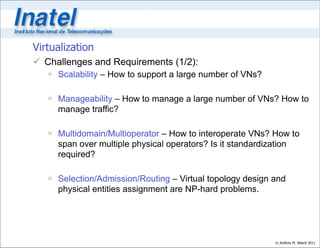
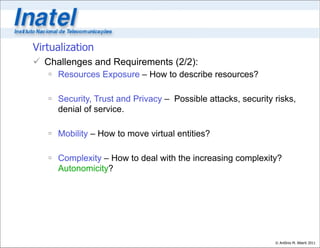
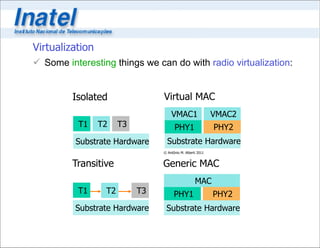
1. The integration of exponentially growing substrate resources like computing and storage with software through virtualization. This will allow multiple virtual networks to share the same physical substrate.
2. The rise of information-centric approaches and handling issues like identifier/locator splitting, mobility, semantics, and context as more "things" connect to the network.
3. Enabling autonomic and cognitive technologies to allow systems to self-manage and adapt as networks scale enormously in size and complexity.