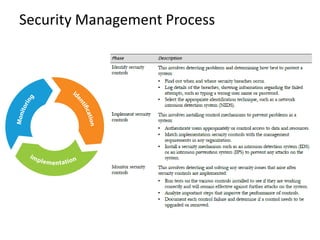
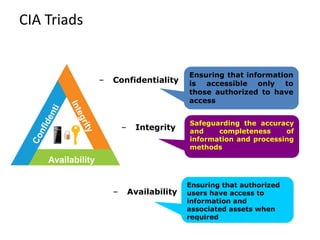
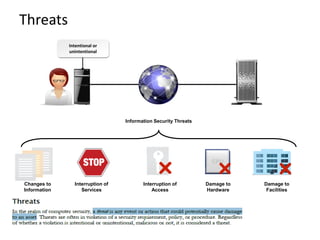
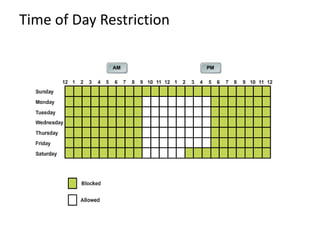
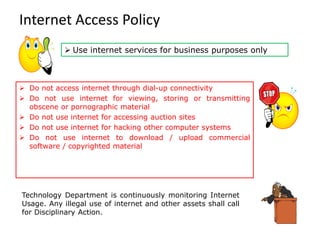
Information security involves protecting data and resources from unauthorized access, use, disclosure, disruption or destruction. It aims to ensure confidentiality, integrity and availability of information through methods like access control, encryption, monitoring and recovery planning. Key aspects of information security include defining security policies, identifying risks and threats, implementing controls like firewalls and access management, and promoting a security-aware culture through user training and responsibility.